PwnedLabs Identify the AWS Account ID from a Public S3 bucket
Linux
ping -c 1 54.204.171.32
Nos damos cuenta que es un servidor Linux
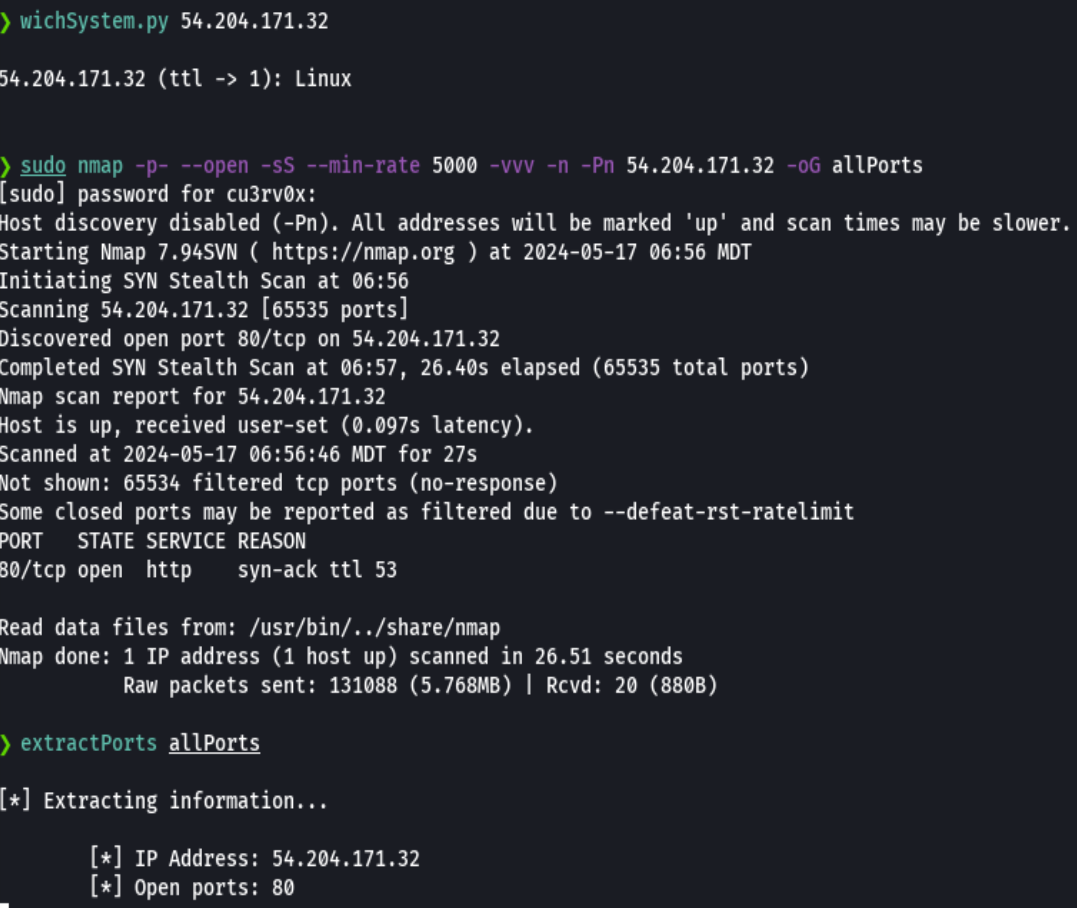
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 54.204.171.32 -oG allPorts
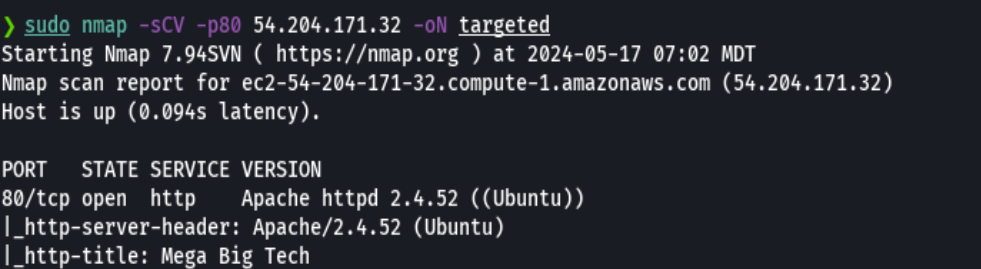
nmap -sCV -p80 54.204.171.32 -oN targeted
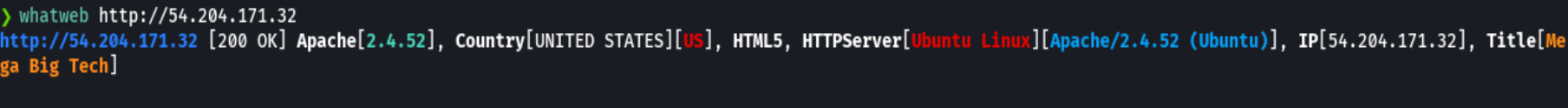
whatweb http://54.204.171.32
pip3 install s3-account-search
sudo ln -s /home/user/.local/bin/s3-account-search /usr/local/bin/s3-account-search
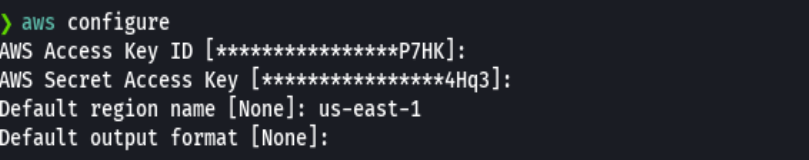
Hacemos como un whoami pero en aws
aws sts get-caller-identity
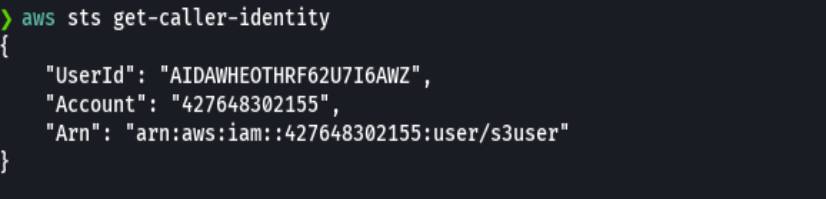
bc targeted -l rb
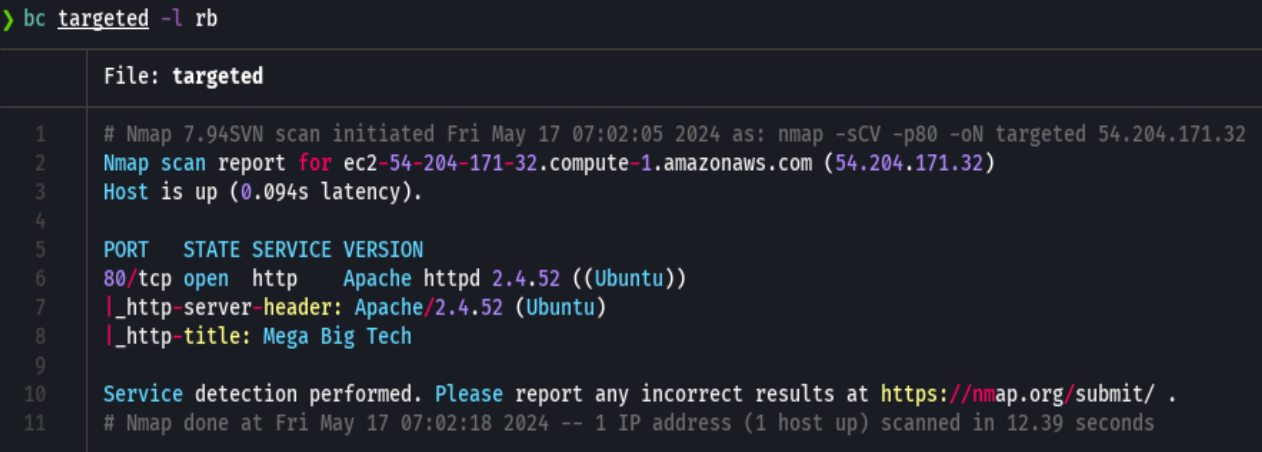
s3-account-serach arn:aws:iam::427648302155:role/LeakyBucket mega-big-tech
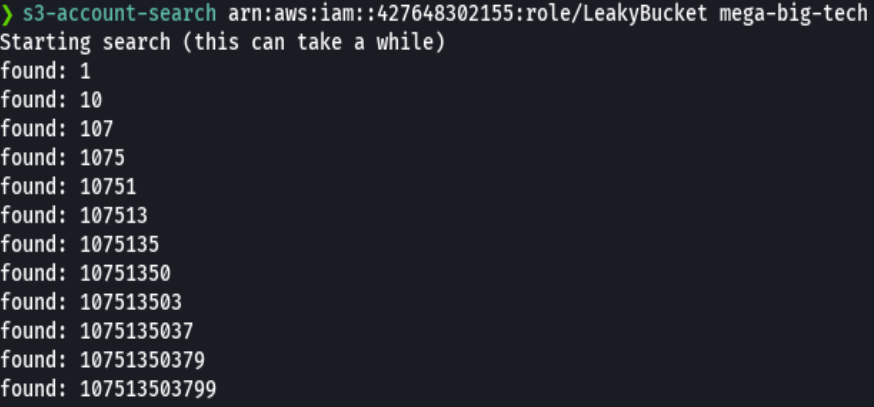
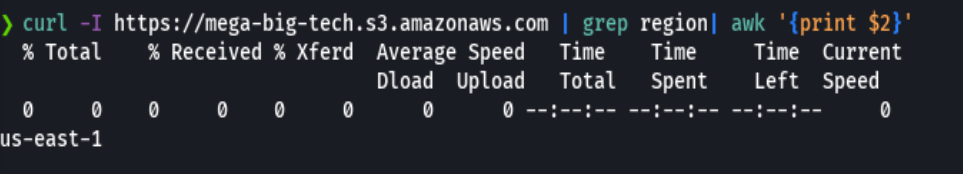
curl -I https://mega-big-tech.s3.amazonaws.com | grep region | awk '{print $2}'
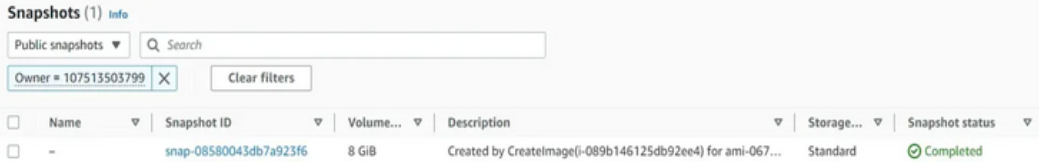
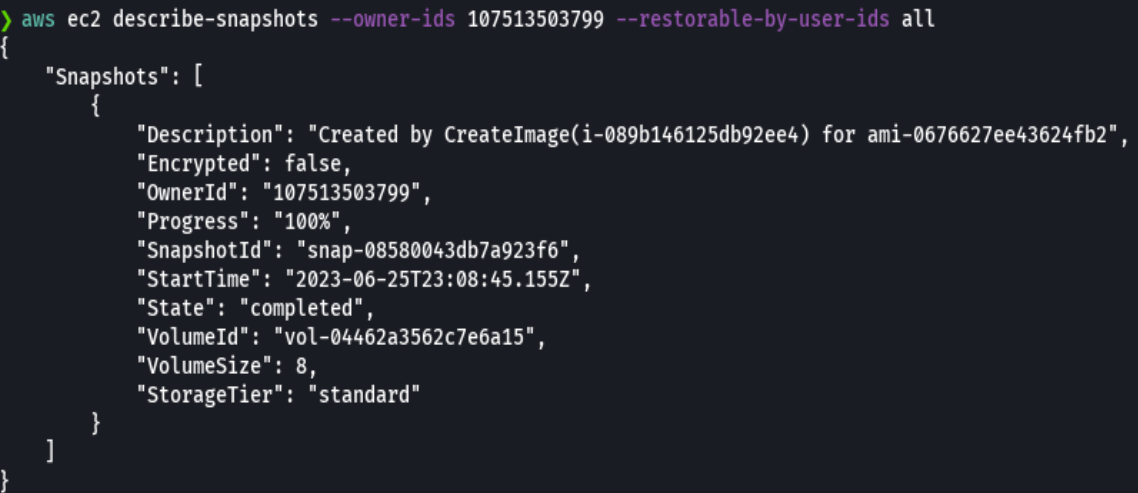
aws ec2 describe-snapshots --owner-ids 107513503799 --restorable-by-user-ids all