Blazorized
HTB Windows
nmap -A -p- -oA blazorized 10.10.11.22 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA blazorized 10.10.11.22
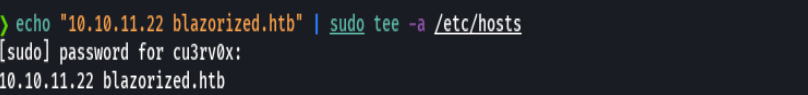
echo "10.10.11.22 blazorized.htb admin.blazorized.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA blazorized-udp 10.10.11.22
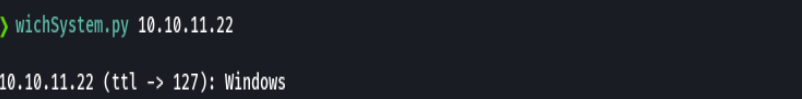
ping -c 1 10.10.11.22
nmap -p- --open -T5 -v -n 10.10.11.145
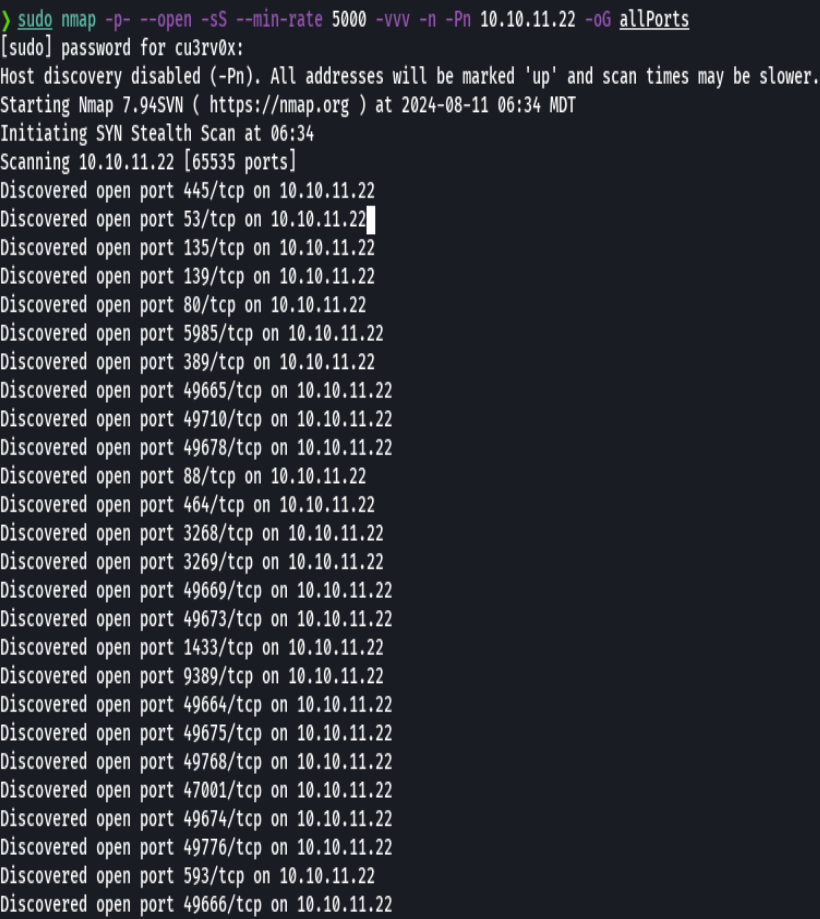
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.145 -oG allPorts
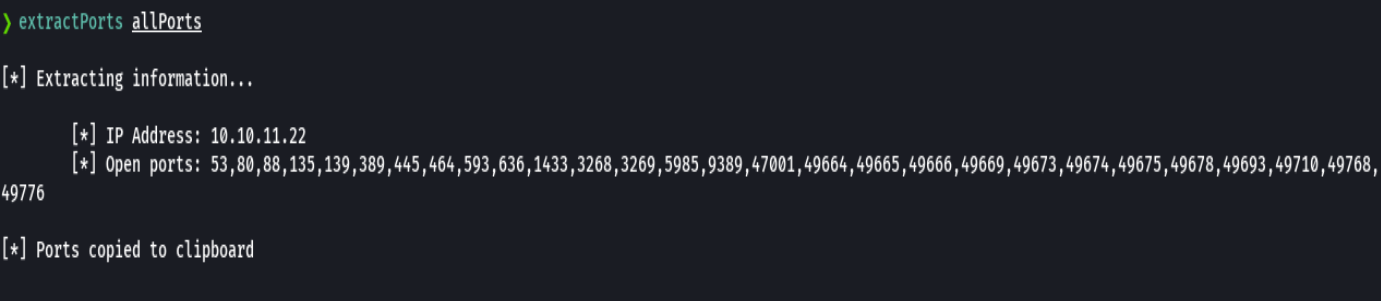
extractPorts allPorts
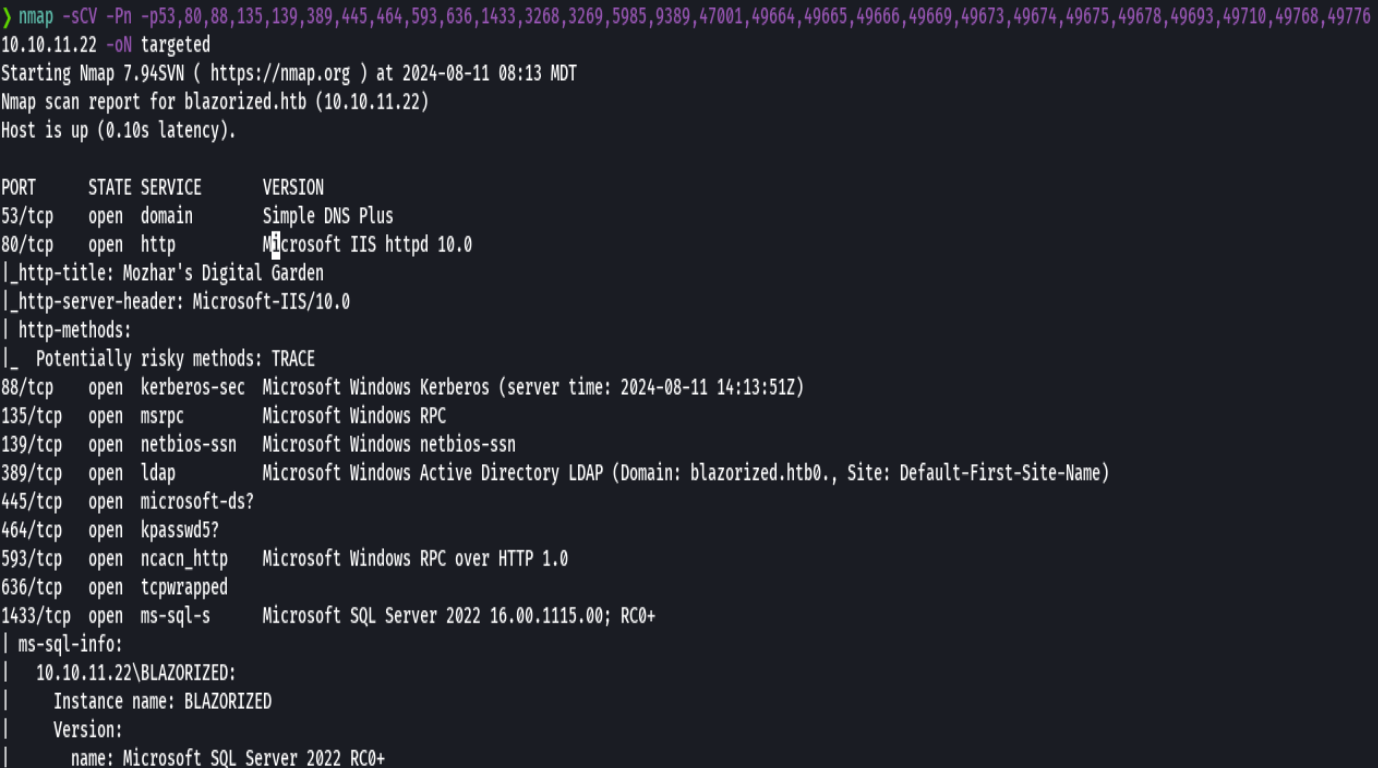
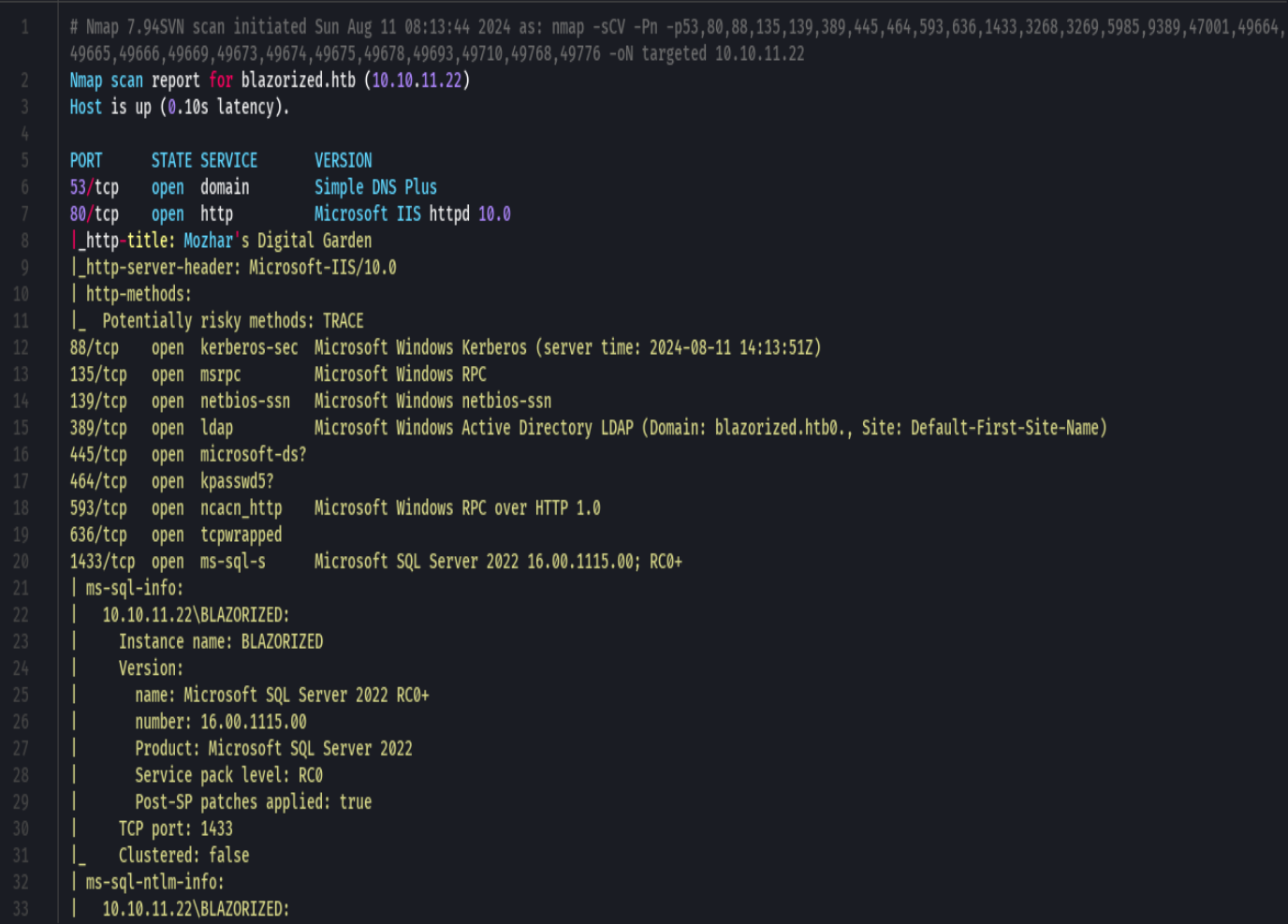
nmap -sCV -p53,80,88,135,139,389,445,464 10.10.11.22 -oN targeted
bc targeted -l rb
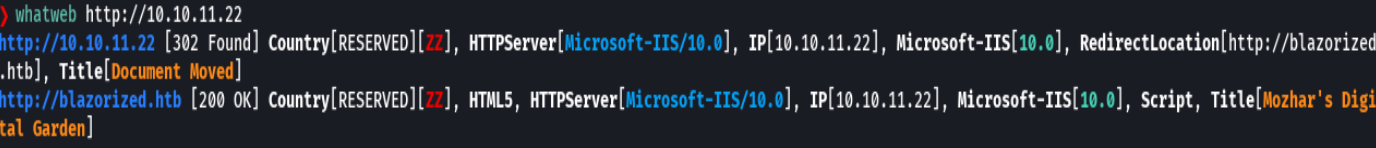
whatweb http://10.10.11.22
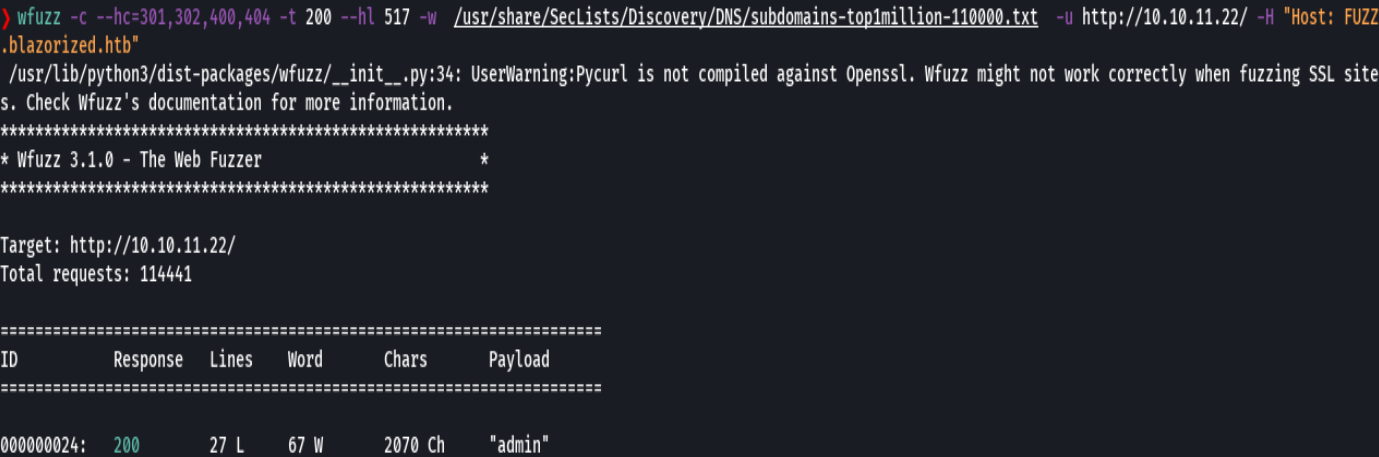
wfuzz -c --hc=302,404,403,400 -t 200 --hl 517 -w /usr/share/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -u http://10.10.11.22/ -H "Host: FUZZ.blazorized.htb"